The regulations around data protection and privacy have continuously evolved to control the practices related to data collection and usage and alleviate the risk of data exposition. Cybersecurity auditors play a central role in the entire scheme of things and will be this article’s focal point.
What is a Cyber Security Auditor?
A cyber security auditor is a person with the necessary qualifications who can perform the following activities for an organization or a company:
- Systematically analyze their security infrastructure with customized audits.
- Provide detailed reports about current security infrastructure.
- Provide a list of improvements to enhance and modify the security for better asset safety.
Top 6 CyberSecurity Auditors
What is a cyber security audit?
A cyber security audit is a thorough examination of an organization’s security posture – its IT infrastructure, security protocols, software development practices, existing security measures like firewalls, etc.
There can be multiple angles to a security audit. You can hire a security testing company to examine your existing security strength and determine how you’d fare against an attempted hack. You can purchase a vulnerability scanning tool to run external scans to find vulnerabilities and security loopholes in your systems.
Or, you can find a more comprehensive solution like Astra’s Pentest Platform that brings the best of both to the table (we will talk more about this approach later).
Once you have gotten the security audit done, polished out the rough edges in your security policies, and filled the gaps in your defense, you can go for a compliance audit.
Yes, cyber security audits and compliance audits are often used interchangeably but there are marked differences. We will talk about that too.
Read also: Penetration testing compliance: An easy-to-follow guide
Why security audits are necessary for the survival of a SaaS business?
As a SaaS business you build a solution, add something to the digital world, create a thing of beauty and satisfaction, and people who believe in your vision, pay you to align themselves with you. You get signups overnight from across the world while sleeping.
But sleep evades you as you worry about cyber attacks that can cause a denial of service, burn a hole in the bank, expose your customers’ data, and create havoc out of a tiny loophole in your security. Cyber security auditors bring you peace of mind that you need to scale among other things.
Read also: Checklist for SaaS Application Security – Developers & Agencies
Building trust among clients
It’s important for your clients to feel safe when they share their data with you – they need to know you are compliant with industry standards and taking good care of your software assets against malicious actors.
Keeping security practices up to date
The cyber threat landscape is changing every week. There were 50 new vulnerabilities every day in 2021. You need to twist and tweak your security practices to stay ahead of the curve. Security audits are the best way to determine the correct course of action.
Being compliance ready
Security audits do not make you compliant with security regulations but they definitely prepare you for the compliance audits. For instance, with Astra’s compliance reporting feature you can identify the vulnerabilities that block certain compliances and focus on remediating those on priority.
Saving big money
Cyber security endeavors are often looked at as expenditures whereas they should be perceived as investments. The average cost of a data breach in 2021 was to the tune of $4 million. That includes the business you lose post the event, the cost of fixing, the cost of circulating the updates, and the penalties payable.
When you have cyber security auditors conduct regular audits and fix the vulnerabilities periodically, you safeguard yourself from loss and actually unlock the confidence to scale.
Also Read: 10 Best Cyber Security Audit Companies [Features and Services Explained]
What should you look for in a cybersecurity audit provider?
Security audits can be difficult, time-consuming, and expensive. Nevertheless, with the right security audit partner things can be really breezy.
Some cyber security companies have really figured it out. With them, you will have an easy onboarding, there will be absolute transparency, you will be able to monitor vulnerabilities in real-time, and you will be able to scale the process with ease.
A combination of manual and automated security testing
When we talk about the combination of manual and automated testing, we’re not necessarily saying that you should opt for the month-long manual tests. There is a better option.
You should look for companies that come with a solid automated tool and a team of security experts that can validate the results shown by the automated tool as well as look for things that it might have missed.
Authenticated scanning
A vulnerability scanner is pretty pointless if it cannot scan behind logged-in pages. The challenge faced by most scanners is that they have to be authenticated manually whenever a session runs out. Some have figured out a way around it too. Look for companies that offer seamless scanning behind the login.
An interactive platform to manage and monitor the processes
You need an interactive dashboard that lets you manage the vulnerabilities, assign them to team members, monitor and update their status, and even get help from security experts. A lot of companies try to offer you this experience, but only a few succeed.
An actionable report
A long, complicated, and boring vulnerability report is worse than the vulnerability itself because you are not going to use the report and yet you have paid a bunch of money for it.
You need a report that is nicely composed for all the stakeholders (executives and developers alike). It should help you prioritize the critical vulnerabilities, and also point you in the right direction in terms of remediation. It should trigger action instead of slowing things down with jargon.
6 best cybersecurity auditors from around the world
Here’s a detailed discussion of some of the top cyber security auditors. This should help you find the right fit for your business.
Astra Security
The security experts and engineers at Astra Security have built an excellent security solution for SaaS businesses. They cover both the defensive and offensive security needs of a company in the modern cyber threat landscape with their website protection product and the pentest platform.
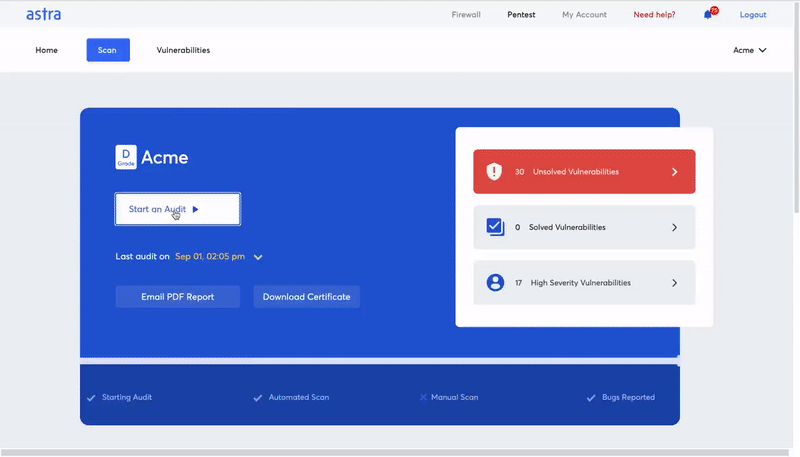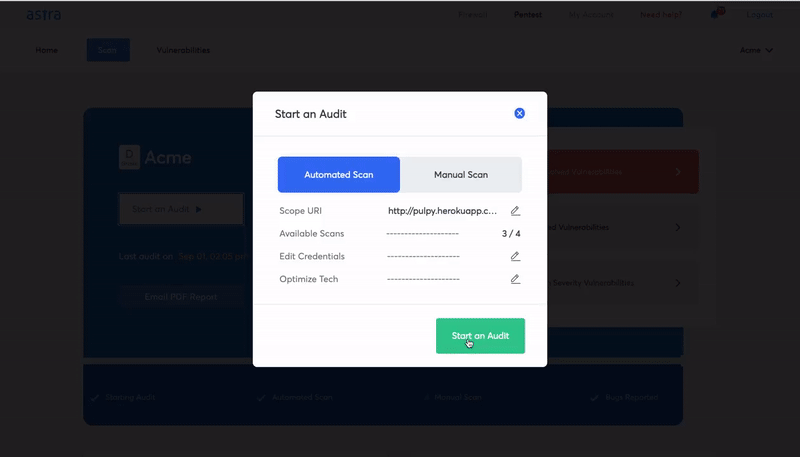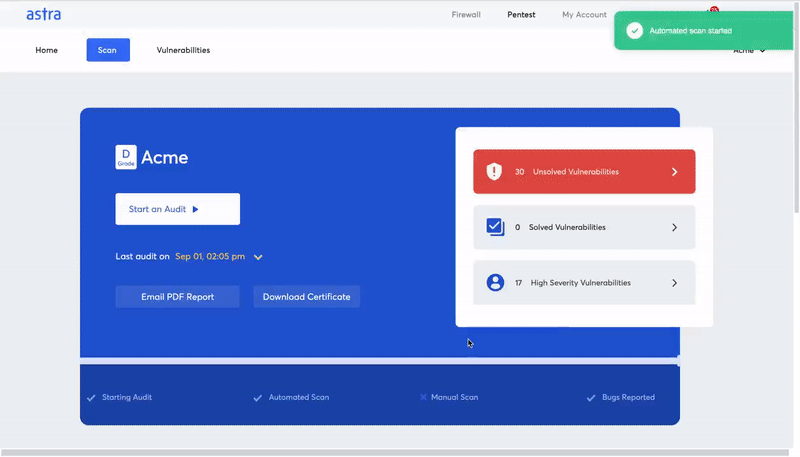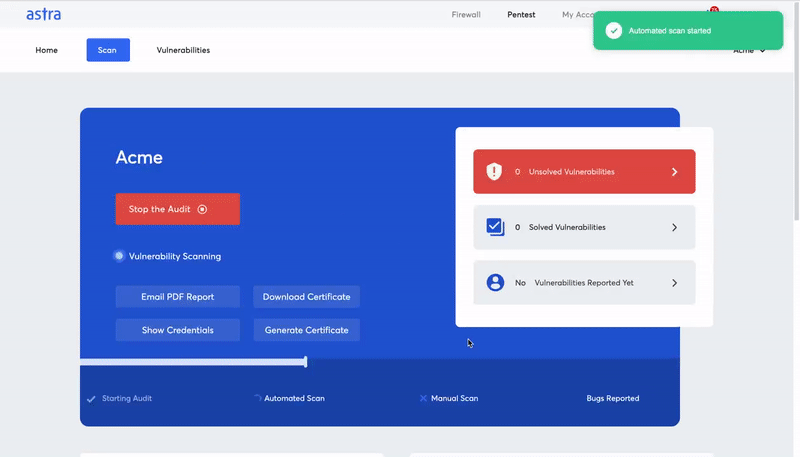
The pentest dashboard
Astra’s pentest platform comes with an interactive dashboard that lets you manage and monitor all vulnerabilities as they are found.
It provides you with easily consumable graphs and tables to make it easier for you to prioritize security vulnerabilities. You can use the same dashboard to assign vulnerabilities to team members and collaborate with security experts.
Integration
Astra’s pentest integrates with your CI/CD pipeline. It allows you to conduct continuous automated testing. You no longer need to move to the dashboard to run a scan, you can set up the pentest suite to run scans automatically whenever you push new code into production.
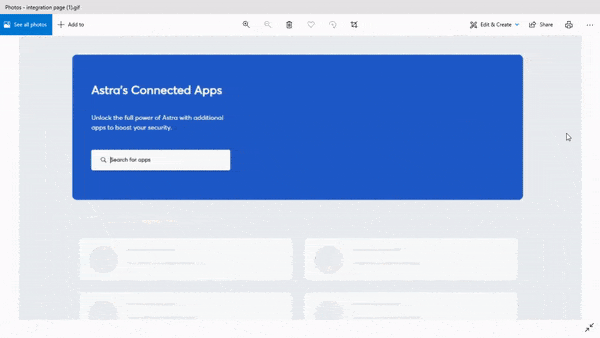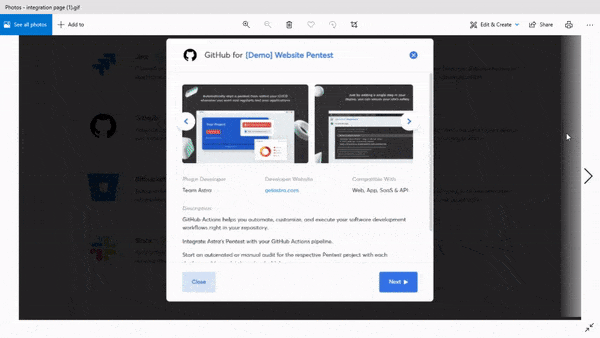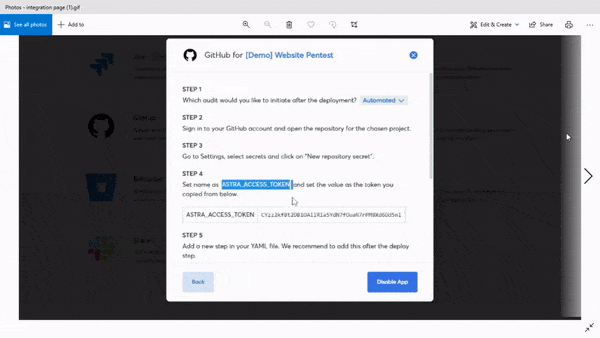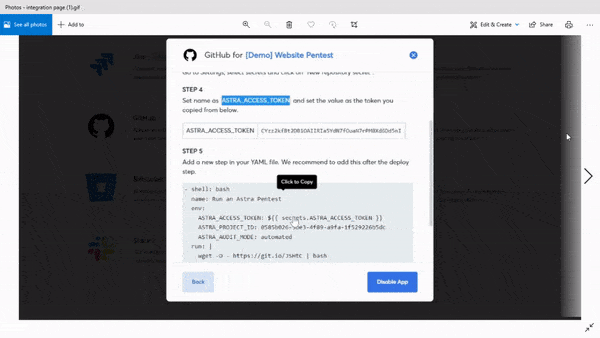
On top of that, you can integrate the pentest tool with workflow management tools like Jira and Slack. It allows you to assign vulnerabilities to team members without so much as leaving your daily mediums of communication.
When a vulnerability is found or fixed, the tool can send an update to a designated Slack contact or group. It’s just neat.
Contextual collaboration
The security experts from Astra engage in contextual collaboration – they discuss steps for remediation or reproduction of a vulnerability by referring to shared resources and documents. It speeds up the process of fixing vulnerabilities for your developers.
Optimizable for different frameworks
The security audit process is made easier if the security testing tool you are using works well with your development environment. Astra lets you adjust the tool to work for your framework with a few clicks. Astra’s pentest platform is also optimized for single-page apps.
Scan behind the login with Astra’s login recorder
We have already talked about the difficulty of reauthenticating the scanner every time a session runs out while scanning behind the login page. Astra has created a solution for this in the login recorder. You fill up some information to authenticate the scanner once and never worry about authentication. You can learn more about it here.
Compliance specific scans
Astra’s pentest platform allows you to identify vulnerabilities that are blocking specific compliance. It helps you accelerate the process of reaching compliance readiness.
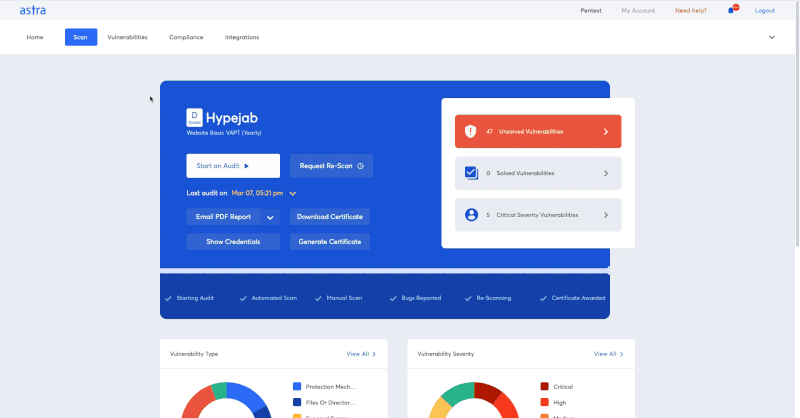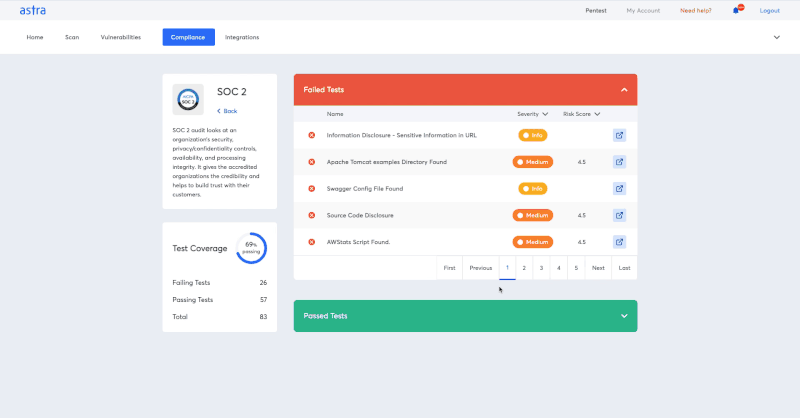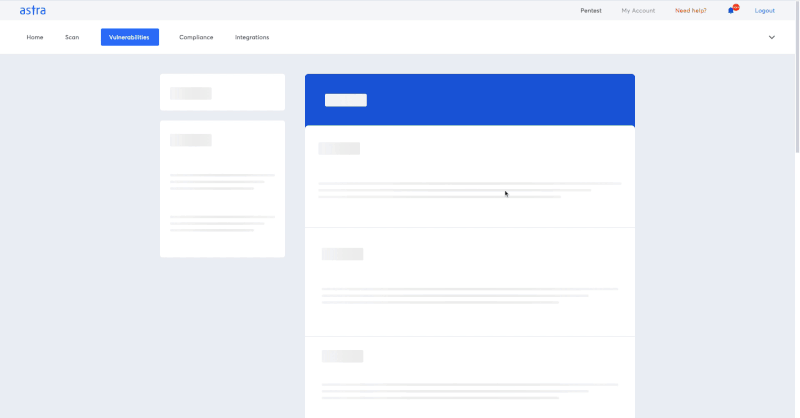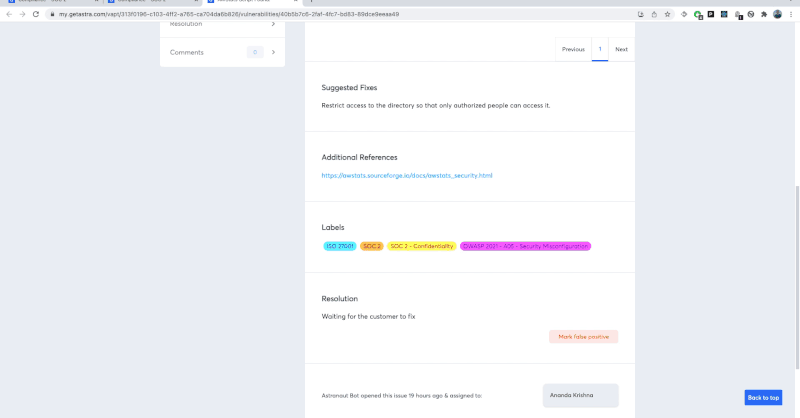
On top of all these Astra has a powerful scanner that conducts 8000+ tests and gets updated rules every week. It has a team of expert pentesters who can help you if you need it. It offers a boatload of features at a very reasonable price.
Testbytes
Testbytes is a security services company that offers a variety of information security-related services including web application scanning and security audits. Their security auditing team consists of security experts, network experts, programmers, and business analysts.
Testbytes has a proven audit methodology. They help you reduce downtime during the security audit and increase operational efficiency. Testbytes serves a number of industries including banking, e-commerce, and healthcare.
Proofpoint
Proofpoint focuses on detecting and preventing user-based security risks. These can include email-based threats, phishing attacks, social engineering attacks, etc. Proofpoint offers a host of products around digital security awareness, cloud security, email protection, and compliance.
The company helps you create sustainable and transparent digital security practices so as to make it easier for you to achieve compliance with security regulations.
They also offer on-call personal assistance regarding security. The focus of this company is mostly on defensive measures but it can help a good deal with your security assessment needs as well.
HackerOne

HackerOne brings the strengths of expert hackers to your side of the table. You get to tap into insights offered by actual hackers and prepare your systems for a real-time hack situation.
HackerOne focuses on application security, vulnerability management, attack resistance management, and cloud security. Their products HackerOne Bounty and HackerOne Assessments could be suitable for your security testing needs.
Intruder
Intruder is a dedicated application vulnerability scanning tool. It offers attack surface monitoring, compliance reporting, and continuous vulnerability scanning features.
Intruder creates detailed vulnerability scanning reports that help you with fixing the loopholes in your security and preparing for the compliance audits.
Their features include internal and external vulnerability scanning, cloud security scanning, and continuous pentesting. Intruder brings a manual pentest offering to the table for a higher price point.
Qualys

Qualys is a great tool for cloud security management and incident response. The cloud platform by Qualys is an asset monitoring tool that gives you 2-second visibility on all your IT assets deployed on the cloud. On top of that, it also has vulnerability management and surface monitoring programs.
Qualys also helps you with compliance with their vendor-risk management and data availability solutions.
Bottomline
Cyber security auditors are crucial for your digital well-being if you are a SaaS company. Threats can emerge from a lot of different angles – from internal errors, vulnerable plugins, or a third-party vendor that has been infected.
Your best bet is to stay prepared and the only way to do that is by conducting regular audits. A cybersecurity audit partner like Astra Security can add a lot of value to your security endeavors and help you build a more secure and trustworthy business.
FAQs
What is the timeline for a security audit?
If you are looking for a comprehensive security audit including the manual pentest component, it can take between 7-14 days depending on the auditor.
Does passing a cyber security audit guarantee compliance?
No, it doesn’t. A cyber security audit helps you identify areas in your security posture that need attention – vulnerabilities, outdated software, open network ports, unclear policies, etc. It gives you the chance to fix these issues before appearing for a compliance audit.
How much does a security audit cost?
Depending on the size of your company and the nature of your business, a security audit may cost anything between $5000 and $30000.
How often should I conduct security audits?
It’s ideal to conduct two security audits a year while nurturing a system of consistent monitoring around the year.
![6 Top CyberSecurity Auditors for SaaS Companies in 2024 [Reviewed]](https://cdn-blog.getastra.com/2022/08/Featured-Images-33.png)















