Different types of penetration test methods are black-box, white-box, and grey-box penetration testing, or based on the assets tested i.e., networks, cloud, web, and mobile applications, APIs, and blockchain. They are employed to secure your assets this can be based on methodology i.e.
What Are The Different Types of Penetration Testing?
- Network Penetration Testing
- Mobile Penetration Testing
- Web Application Penetration Testing
- API Penetration Testing
- Cloud Penetration Testing
- Blockchain Penetration Testing
- Social Engineering Penetration Testing
What is Penetration Testing?
Penetration testing is the process of analyzing, detecting, and exploiting vulnerabilities within the security system of a web application, network, cloud, or API to assess the impact of a successful attack, mitigate the found vulnerabilities, and thus avoid breaches or exploitation by hackers.
Examples of penetration testing include mobile and web application penetration testing, API pentesting, cloud pentesting, and network penetration testing.
Types of Penetration Testing
1. Wireless Network Penetration Testing
Network penetration testing is a security audit by which you check the security of a network if you want to know about the technical details of the security audit.
In simple words, wireless penetration testing, or network security testing, is a method of evaluating a computer network’s vulnerability to intrusion. This vulnerability could be a flaw in a computer system or a malicious attack from a hacker. A penetration test simulates an attack from a malicious hacker to determine the network’s vulnerabilities and determine if an actual attack would be successful.
Who is it for?
Network pentests are ideal for networking companies that relay vast amounts of data, and cloud companies that rely on networks.
Why should you perform a network penetration test?
Network penetration testing is performed on the network infrastructure, also known as the backbone of the network. This type of testing finds holes in the network system that outside parties could exploit.
2. Mobile Penetration Testing
Mobile Application Penetration Testing is testing a mobile application for security vulnerabilities. The goal of penetration testing is to find weaknesses in mobile security and report them to the developers.
The scope of testing varies from functional testing to security testing. Penetration testing has evolved significantly as the number of mobile devices and users has grown, for example, android and iOS penetration testing.
Mobile application penetration testing is done to gain access to sensitive data or disrupt the app’s functionality.
Who needs mobile penetration testing?
Mobile pentests are highly advised for companies that develop mobile-based applications for games, payment, shopping, and more before they are released for public use. It should also be carried out after any major updates to the application.
Why should you perform a mobile pentest?
A mobile pentest should be performed since it provides credible evidence of vulnerabilities in a mobile application that can be resolved or mitigated before the application is released, making it less prone to glitches.
3. Web Application Penetration Testing
Web application penetration testing is a process of figuring out the possibility of a hacker or a group of hackers gaining access to your web application. It is done to expose your web application’s vulnerabilities and prevent data breaches, identity theft, financial loss, and other negative consequences.
The penetration tester usually tries to break the web application by looking for vulnerabilities such as SQL injection, cross-site scripting, and cross-site request forgery. The tester then identifies the vulnerabilities and checks if they can be used to gain access to information or control of the web app.
Who needs a web application penetration test?
Out of all pen testing types, web application penetration tests are the most commonly conducted and required type of pentest. It should be conducted by companies having any web assets.
Why should you perform a web application pentest?
Web application pentests should be conducted in order for the timely identification of any vulnerabilities that have risen in it to identify and mitigate them before they are exploited.
4. API Penetration Testing
An application programming interface (API) is a set of tools and standards that allow applications to communicate. APIs enable a developer to create a customized experience within a given app.
An API penetration test is a process of identifying vulnerabilities in an application programming interface (API). API penetration testing is a way of testing the attack surface of an application by simulating the actions of a malicious user
Who needs an API penetration test?
Businesses or companies that have products such as web applications or mobile applications having an API backend must regularly conduct API pentests to safeguard them from exposure or improper codes.
Why should you perform an API pentest?
API pentests can detect any security flaws within the code that can make the web or mobile application prone to a cyber attack.
5. Cloud Penetration Testing
Cloud penetration testing is a type of security testing that analyzes a cloud computing environment for vulnerabilities that hackers could exploit. Cloud pentest is a crucial component of a cloud security strategy because it can reveal potential weaknesses in cloud security controls.
Penetration testing can be performed manually, by a human tester, or automatically by a security tool or a tool integrated with a CI/CD pipeline. Cloud penetration testing aims to identify vulnerabilities in the cloud infrastructure and determine the effectiveness of controls implemented to protect the infrastructure.
Who needs a cloud penetration test?
Cloud penetration tests are required by companies that provide cloud services such as AWS, Google Cloud Platform, and Azure and cloud security services. Since cloud employers opt for a shared responsibility model, it is on the cloud customers to ensure and enhance their cloud security measures.
Why should you perform a cloud pentest?
Cloud pentests should be performed in order to detect any vulnerabilities within the platform, data storage, and or network that is used for data transfers.
6. Blockchain Penetration Testing
Blockchain is a distributed database that maintains a continuously growing list of ordered records called blocks. Each block contains a timestamp and a link to a previous block. Blockchain databases are spread across a network of computers.
Blockchain penetration testing assesses the security of a blockchain network, application, or smart contract. It’s the process of testing for known and unknown vulnerabilities in a blockchain network, application, or smart contract.
Blockchain penetration testing is used to determine whether the solution can withstand attacks that are performed to compromise the network’s security. Blockchain penetration testing aims to uncover vulnerabilities and security loopholes and identify misconfiguration errors in the solution.
Who needs a blockchain pentest?
Blockchain pentests are essential for companies that deal with blockchain solutions, networks, applications, and in cases of smart contracts too.
Why should you perform a blockchain penetration test?
A blockchain penetration test should be performed on a regular basis to avoid any security issues and help improve the security quality of the code before and after its implementation.
7. Social Engineering Penetration Testing
Social engineering penetration testing involves testing the security of a company’s employees to identify vulnerabilities that could be exploited by an attacker. This type of testing involves creating scenarios in which an attacker tries to trick an employee into giving them access to sensitive information or systems.
Social engineering penetration testing is important for companies that want to ensure that their employees are aware of the risks of social engineering attacks and can identify and prevent them.
Social engineering pentesting should be performed by companies looking to get an outside POV of their security systems and their functioning.
Social engineering pentesting helps identify problems in security measures, be it physical or virtual such as lack of awareness in employees regarding best security practices, security gaps, and more.

What Are The Different Approaches To Penetration Testing?
The penetration test is a fundamental good practice for checking the security of a system. If the penetration test is done correctly, the weaknesses of the system will be revealed. Penetration testers follow 3 different approaches to conduct the different types of pen tests:
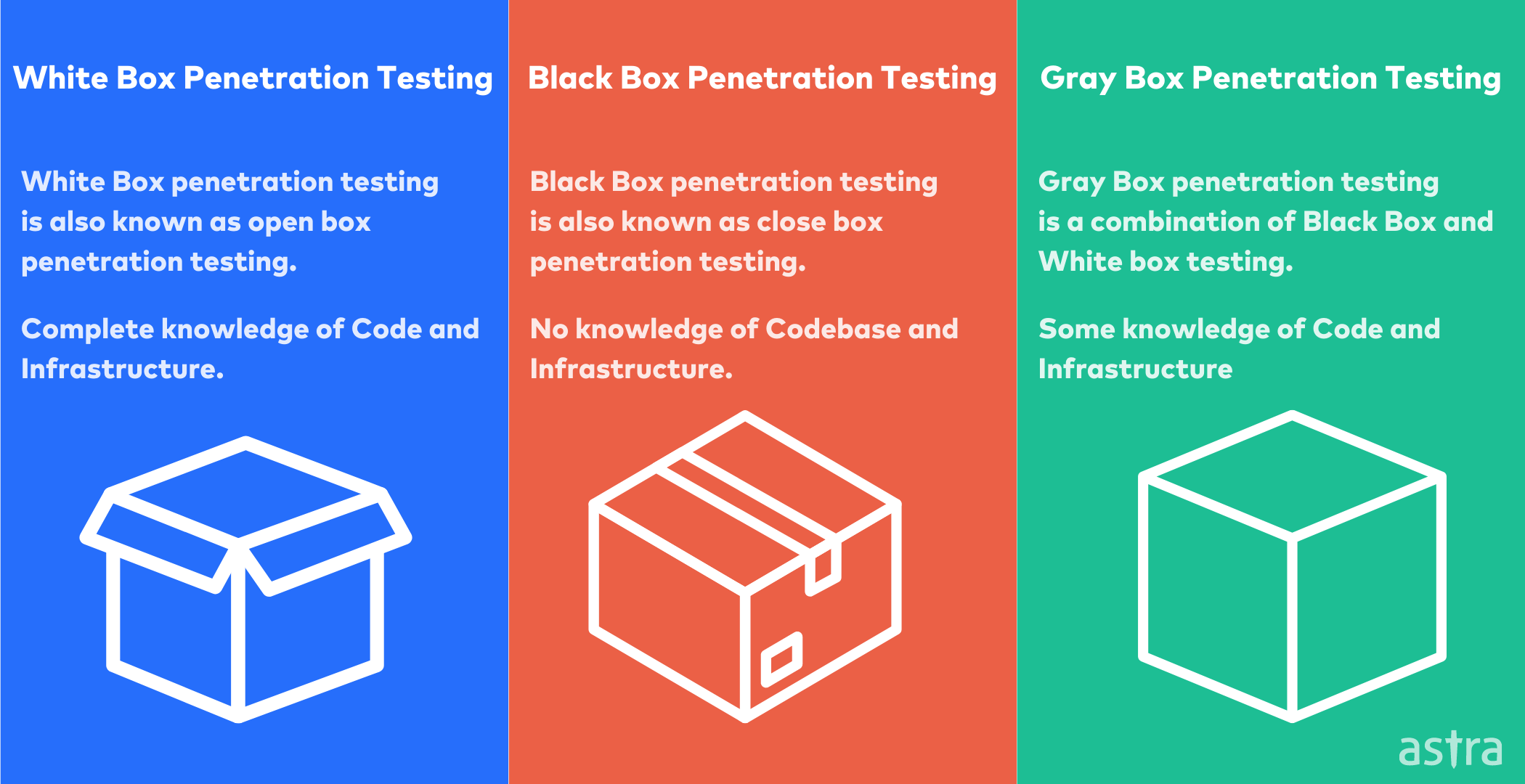
1. Black Box Testing
Black box testing is a method of evaluating the security of an application or system. The penetration tester has no information about the system, not even the operating system or application type. The tester must use the same tools and techniques that a hacker would use to attack the system.
Black box penetration testing is the most challenging type of penetration test to perform. It requires a high level of skill and often accesses the same resources that the attacker would have available. Black box penetration testing is the best way to test the overall security of a system.
2. White Box Testing
White box pen testing is a method of penetration testing where the tester has complete knowledge of the source code and environment. White box testing is based on how the program works, not by exploiting any vulnerabilities in the code.
White box testing focuses on understanding how the application works, then attempt to break into the application through knowledge of the source code. This is the opposite of black-box testing, where the tester does not access the source code.
3. Gray Box Testing
Gray Box testing is an approach to penetration testing. The tester has partial knowledge of the target environment in network diagrams, network documentation, or partial access to the internal network. The tester has limited but more than just an outside understanding of the target environment.
Gray box testing is typically done in the early stages of a program to assess what types of vulnerabilities could be present and how much information an attacker could potentially receive.
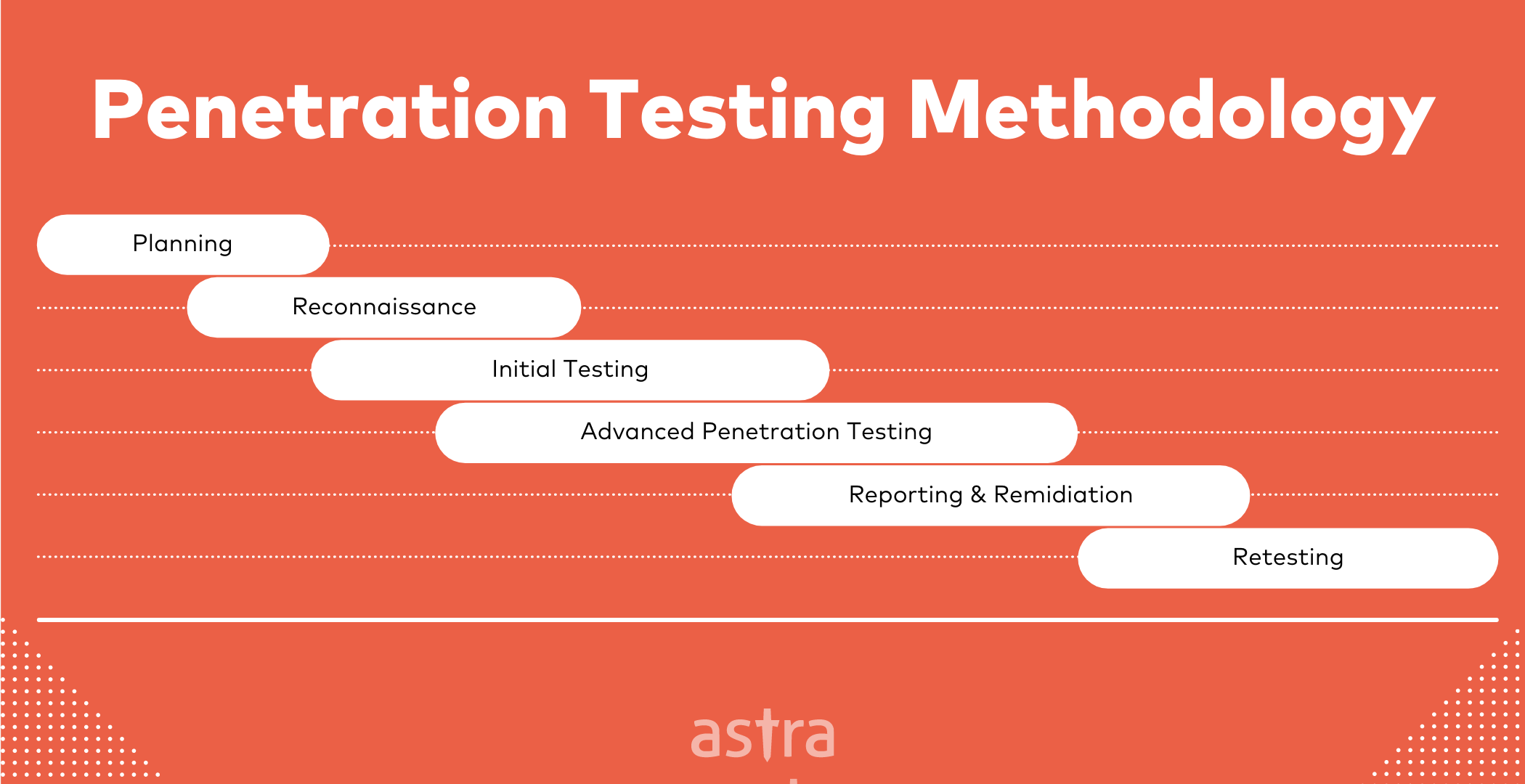
Why is Penetration Testing performed?
These days, everyone needs to be worried about cybersecurity. Just about anyone can be hacked, and there are many cybersecurity threats. Unlike traditional threats, like natural disasters, you can’t predict when you might be hacked. So, it’s helpful to be prepared, which is why performing regular pentests is essential.
Let’s understand 4 common reasons why penetration testing is essential:
1. Uncover Security Risks
Penetration testing is a security evaluation technique used to identify vulnerabilities in a computer system, network, or web application. These identified vulnerabilities are patched before a hacker or cyber-criminals can find and exploit them.
2. Compliance and Regulations
These days, it’s almost impossible for businesses to avoid the acronym PCI. Not only is it a widely used acronym, but it also stands for something vital: Payment Card Industry Data Security Standard. Most compliances such as PCI DSS, SOC2 Type I, Type II have an essential requirement of performing a proper pentest.
3. Customer Trust
Having a good business idea, a well-designed product, and a clear marketing strategy in the internet age is no longer enough. To survive in the market, a company must protect its customers and their data from cybercriminals who can use it to steal confidential information.
4. Save the cost of a data breach
A minor Data Breach can cost millions of dollars, and this can only be prevented by keeping your infrastructure and your application secure by conducting regular pentests and awareness training.
4 things to consider while getting a penetration testing contract
A penetration testing contract is an agreement between the client and the penetration tester, who performs the right type of penetration tests on the desired application or network. Penetration Testing is a sensitive process. When testing, there are many steps to take so that the actual product or application is not affected during this process.
Below mentioned are 4 things to keep in mind while getting a penetration testing contract:
1. Make sure you have a proper plan & scope
It’s essential to have a proper plan to perform penetration. This pentest plan is handed over to the team of penetration testers before conducting a pentest. The strategy usually includes what time the automation scanner is allowed, how much load testing is permitted, which all hosts can scan, etc.
2. Data security
There’s a high chance that you don’t want the penetration testers to look into the sensitive data of your customers or clients. A proper data security policy helps you with this. Data security policy contains information regarding sensitive data testing, how to test the databases, what to do if sensitive information is disclosed etc.
3. Vendor’s Reputation
When it comes to the services of a pen testing company, its reputation is of great importance. It is a guarantee of a successful result of a penetration test of a business. A good rating of a pen testing company guarantees high-quality services and professionalism in the field. The rating of a company can be easily checked online via various discussion forums.
4. Skilled and Trained Penetration Testers
The pen testers are an essential part of the pen test team. They are the ones who analyze the vulnerabilities, assess the risks, and carry out the attacks. The pen testers must have firsthand knowledge of the vulnerabilities being tested, so they must have the skills and expertise necessary to carry out the attacks. When selecting a pen test provider, it is beneficial to find a provider who hires trained and experienced pen testers.
Why Astra’s pentest suite is a perfect fit?
One of the best ways to conduct penetration testing is outsourcing this task to an experienced penetration testing company. Astra is a team of highly skilled security engineers whose only job is to keep your application secure from attackers. Astra Security offers different penetration testing services such as:
- Cloud Penetration Testing ( AWS, GCP, and Azure )
- Blockchain & Smart Contract Penetration Testing
- Mobile Penetration Testing ( Android, iOS, and PWA )
- Network Penetration Testing
- Web Application Penetration Testing
- API Security Testing
We at Astra understand how vital your and your customers’ data is. Astra’s automated scanners come with more than 2600+ tests which keep not only your but your customer’s or client’s data secure too.
Penetration Testing at Astra is not limited to automated Scanners; skilled and trained security professionals manually test applications to ensure no security risk is left untouched.
FAQs
1. What is penetration testing and its types?
Penetration testing refers to the process of evaluating a system’s security posture by finding and exploiting vulnerabilities present in the said system. Penetration tests are categorized into three types – white box pentesting, grey box pentesting, and black box pentesting.
2. What Is The Primary Purpose Of Penetration Testing?
The primary object of a penetration test is to identify critical vulnerabilities and understand their impact and cure.
This post is part of a series on penetration testing, you can also check out other articles below.
Chapter 1. What is Penetration Testing
Chapter 2. Different Types of Penetration Testing?
Chapter 3. Top 5 Penetration Testing Methodology to Follow in 2024
Chapter 4. Ten Best Penetration Testing Companies and Providers
Chapter 5. Best Penetration Testing Tools Pros Use – Top List
Chapter 6. A Super Easy Guide on Penetration Testing Compliance
Chapter 7. Average Penetration Testing Cost in 2024
Chapter 8. Penetration Testing Services – Top Rated
Chapter 9. Penetration Testing Report