The size of your business does play a role in pulling a hacker’s attention. But if you think that your website is too small to attract any malicious actors, think again. Hackers have a wide range of motivations, from financial gains to personal vendetta. Some just do it for fun, some are very serious about it.
Your company could be a victim of a mass cyber attack just by appearing on the radar of a hacker. On average, a website is visited by malicious bots in search of exploitable vulnerabilities more than 2000 times a week. A vulnerability scanning report helps you spot the vulnerabilities extant in your systems, and figure out how much damage they can cause and how you can fix them.
To avoid being on a hacker’s radar you must cleanse your application, website, IT network, and devices of vulnerabilities and keep doing that every now and then. The vulnerability scanning report allows you to prioritize the vulnerabilities that need urgent fixing based on the risk they pose to your IT infrastructure and your by extension your business.
What is vulnerability scanning?
A vulnerability scanner is an automated software tool that is commonly used to detect security weaknesses and exploitable vulnerabilities in your website, web app, IT network, or devices. It is an automated tool that helps you discover anomalies in your systems in reference to a vulnerability database. After that, the scanner produces a vulnerability scanning report that documents all the issues found during the scan along with some recommendations on how one could get rid of them. The following section gives you five important pieces of information about a vulnerability report.
Why is Astra Vulnerability Scanner the Best Scanner?
- Runs 8000+ tests with weekly updated scanner rules
- Scans behind the login page
- Scan results are vetted by security experts to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities from one place.
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Integrates with Slack and Jira for better workflow management
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

What is a Vulnerability Scanning Report?
A vulnerability scanning report is a document which records all findings after a vulnerability scan has taken its course. This document helps you understand what the vulnerabilities are, how they can impact your organization, possible fixes, etc.
The report includes a detailed analysis of the vulnerabilities including severity scores and recommendations for remediation.
Reading a Vulnerability Scanning Report
We will break down a vulnerability scanning report into its different components later in the article. Right now, let us discuss how you should read a vulnerability scanning report.
Every report has an executive summary that talks about the overall security health of your organization according to the tests performed. It gives you an overview of the issues present and helps you conceptualize the security posture of your organization without going much deeper into the details of individual vulnerabilities.
The aforementioned part, along with the list of vulnerabilities with their corresponding severity scores helps the management prioritize vulnerabilities and assign them to developers.
It can be difficult even for IT professionals to read and make sense of vulnerability scanning reports unless they have a security acumen. Then again, it is very important to understand and act on the report as it helps you fix the vulnerabilities.
Hence, you want a vulnerability scanning report that includes video POCs helping developers reproduce and fix vulnerabilities. It also helps if you have steady assistance from security experts while remediating the issues.
Also Read: What is Network Vulnerability Scanning? The Ultimate Guide
What is Included in a Detailed Vulnerability Scanning Report?
A detailed vulnerability scanning report helps you attain the true picture of your web app’s security posture. It has two primary purposes – helping you prioritize critical vulnerabilities, and assisting you in fixing the said issues. The following are different components that a vulnerability scanning report should have.
1. Executive summary
This is intended to give you an overview of the vulnerability situation without delving deep into the details.
Firstly, it should establish the purpose and the scope of the testing. It helps if the report has graphical representations of the vulnerabilities found according to their type as well as their severity.
Next comes the list of vulnerabilities where you can view the CVSS score of each vulnerability along with their categorization in terms of low, medium, high, and critical severity. This part also comes with the current status of the vulnerabilities.
2. Details of the vulnerabilities discovered
This is where things start getting pretty technical. In this part, each vulnerability is explained. Here, you learn what a specific vulnerability is, and how it can impact your website as well as your business, its status, and CVSS score. It also includes suggestions to fix the issue.
The recommendation for remediation maybe just a one-line comment or a detailed step-by-step guide to reproduce and solve the issue.
3. Scan details
A vulnerability scan comprises hundreds of test cases and a wide range of manual and automated scan types. The vulnerability scanning report needs to document each test case along with its category, typical severity, scan type, etc. The test cases are different for web apps, android apps, iOS apps, and blockchain-based apps.
Apart from the PDF report which includes the aforementioned segments, there can also be video POCs to help developers reproduce certain issues.
Download Sample Penetration Testing Report (VAPT Report)
How a Vulnerability Scanning Report aids Your Security Efforts
The impact of an actionable vulnerability scan report is quite simple.
- It identifies the vulnerabilities that pose a threat to your organization.
- Tells you how severe each of those vulnerabilities is so that you can prioritize the most dangerous ones.
- Gives you suggestions and guidance for fixing the vulnerabilities.
The easier it is for you and your developers to read and make sense of the report the sooner the issues will be fixed, thus restoring the security health of your organization.
How to Pick the Right Vulnerability Scanning Tool?
You need a scanner that comes with a robust interface for you to use, conducts tests according to relevant security standards, and conducts enough of them. And finally, a scanner that produces an actionable report.
Apart from these typical features, you can look for additional features such as
- Scan behind login
- Compliance reporting
- Human support
- Integration with CI/CD platforms.
Also Read: Top 6 Web Pentest Tools You Should Not Miss in 2022
Types of Vulnerability Scanners
1. Network-Based Scanners
As the name would suggest, a network-based vulnerability scanner is used to search an entire network with all the devices, and applications running on it, for vulnerabilities. The scanner creates an inventory of all the network assets and the vulnerabilities in each of them.
2. Host-Based Scanners
Host-based scanners are used for scanning servers and workstations. They are also used to check the security configurations and patch history of a server or workstation.
3. Wireless Scanners
Wireless scanners are used to identify unauthorized access points in a network. It is also used to find inconsistencies in security configurations.
4. Application Scanners
Application scanners are used to scan websites and applications for common security vulnerabilities. We will be talking about these scanners at length.
What are Internal and External Vulnerability Scanners?
When talking about vulnerability scanners and reports, one ought to talk about internal and external scans. When you think about protecting your website or business, you worry about the internet-facing assets and how those can be meddled with from the outside. That is where external scanning comes in.
External vulnerability scanning looks for loopholes in your firewall and other external security measures in place to block threats from the internet.
However, threats can originate from within the firewall too. A malicious file that was downloaded by mistake, or weak passwords used by employees can pose just as critical a threat. Add design-related issues with these and you have got quite a handful of vulnerabilities that need to be identified with an internal vulnerability scanner.
Why are Vulnerability Scans Necessary?
As we have discussed earlier, your system is being scanned for vulnerabilities quite frequently by malicious actors. They are looking for unpatched issues, outdated plugins, broken access controls, lack of input validation, or some other chink in your security that they would exploit and cause harm.
Hence, it would be in your best interest to find vulnerabilities existing in your web app or network, before the bad guys do. Let us list down some benefits of frequent vulnerability scans to help you understand their importance better.
- Stay aware of your security posture.
- Stay informed about your standing regarding relevant security compliance regulations.
- Protect your website from being hacked into.
- Protect sensitive information belonging to both you and your customers.
- Get a competitive edge by being secured and certified.
A data breach cost $4.24 million on average in 2021 and 60% of small and midsize businesses failed to bounce back after being hacked.
So, the bottom line is pretty straightforward. Your website is likely to have some vulnerability or the other, and you risk losing a lot of money and reputation if you ignore them.
Read also: What, Why, and How of Vulnerability Scanning
Vulnerability Scanning with Astra’s Pentest
Software development is a continuous process. With each updated version of a web app, new vulnerabilities creep in. Hence, security needs to be a continuous process too and it needs to be simple.
Astra Security has built the most elegant solution for scanning web apps, mobile apps, and networks for potential vulnerabilities (with over 3000 test cases). Astra’s Vulnerability Scanner is a part of their comprehensive offering called Astra Pentest Suite.
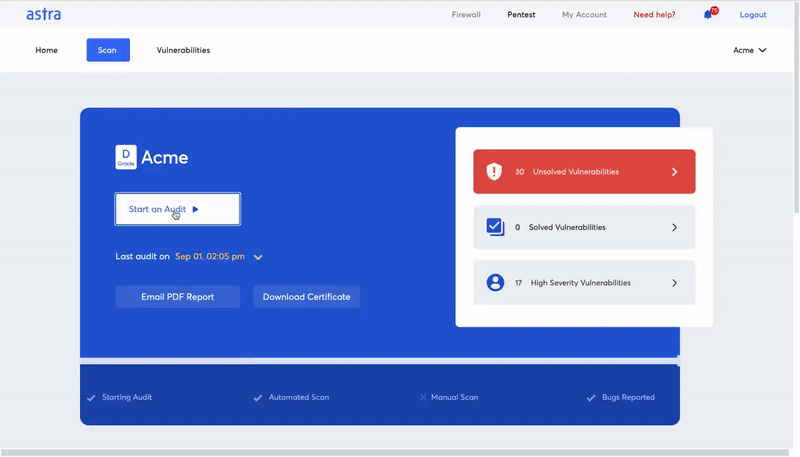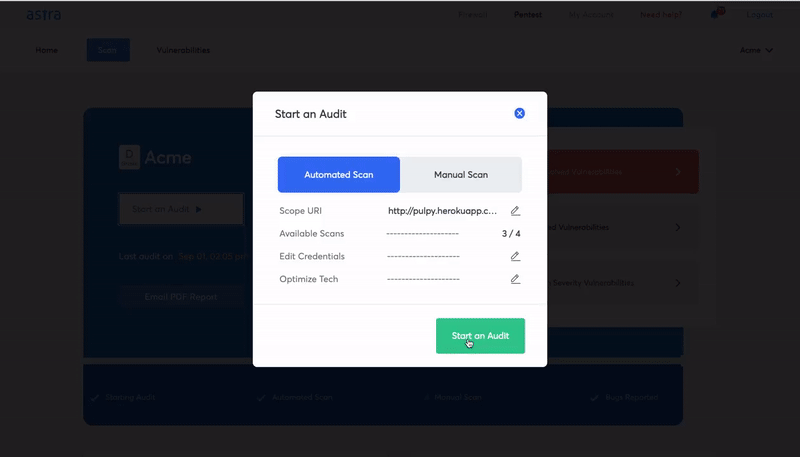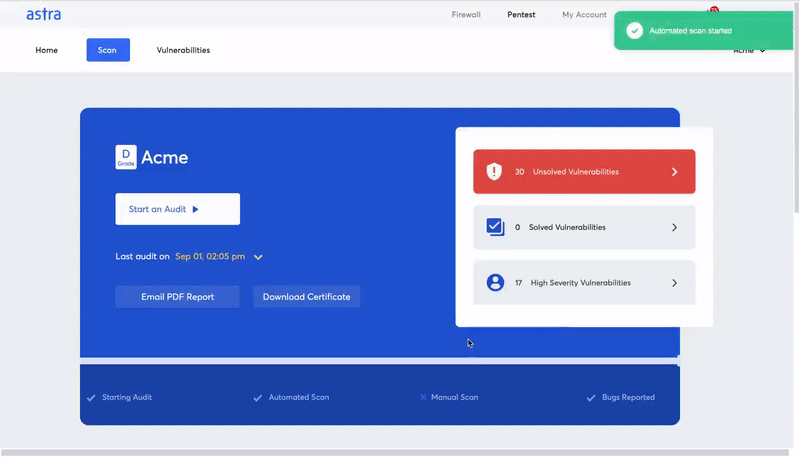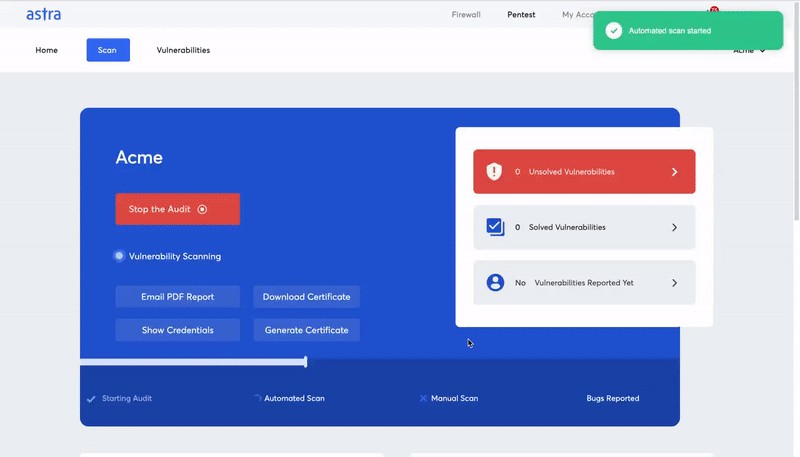
Here are some unique features of Astra Pentest Suite:
- Scan behind login: Astra’s login recorder extension allows the automated scanner to scan behind logged-in pages.
- Zero false positives: When vulnerabilities are detected, security engineers manually ensure that each one of the reported vulnerabilities is genuine.
- Compliance reporting: The pentest compliance feature shows you the compliance regulations you meet or fail to meet with reference to the vulnerabilities found during a scan.
- CI/CD integration: You no longer have to go to the pentest dashboard to run a vulnerability scan after each product update. You can automate the scan after each update by integrating the pentest suite with CI/CD platforms.
- Detailed report with video POCs: The vulnerability scanning report by Astra Security is as detailed and comprehensible as it gets. You get easy access to security experts if the remediation process hits a roadblock.
Conclusion
A vulnerability scan without an actionable vulnerability scanning report is quite useless. A sample vulnerability scanning report is one of the first things you should see and review before choosing a vulnerability scanning tool. It always helps if you have some help from security experts while reading a vulnerability report. Communication is the key when it comes to acting effectively based on the results of a vulnerability scanning report.
















