The way business organizations depend on decentralized connections along with the current rapidity of digital transformation has opened a lot of doors for cyber attackers. The cyber threat landscape has worsened over the last couple of years and 2024 is all set to pose critical security challenges.
Understanding and implementing penetration testing for web applications is a matter of extreme urgency given the circumstances, hence, it is a good idea to familiarize yourself with some effective web pen test tools.
The Top 14 Web Pentest Tools of 2024
Choosing the right tools and the most capable pentesting company makes the rest of the job way easier for organizations. We will discuss what pentesting is, how good web pentest tools can make a difference, and help you choose the right one for your business.
Top Features That Every Web Pentest Tools Should Have
Here are the top features offered by good web application penetration testing tools that you would need in your endeavor to be rid of any security vulnerabilities.
1. Vulnerability Scanning
The web app pentesting tool should have a comprehensive vulnerability scanner capable of scanning for a wide range of vulnerabilities from OWASP Top 10, and SANS 25, to any new vulnerabilities based on CVEs, bug bounty reports, and other trusty sources.
2. Detailed Reporting
A good pentesting tool is accompanied by better reporting without which it would be incomplete. Reports should have executive summaries, risk scores based on CVSS scores, and contextual data for easy prioritization and steps for remediation.
3. Vetted Scan Results
Automated vulnerability scans often generate false positives. The tool should have the support of expert pentesters who can vet and weed out any false positives from the scan results for a more effortless remediation experience for you.
4. Scan Behind Logins
The tool should be capable of scanning behind logins and have an extension for recording login information to do the same. This enables the tool to carry out authenticated scans based on different roles.
5. Deep Integrations
Modern web pentest tools should be capable of integrating with other CI/CD tools such as code repositories like Jenkins, GitHub, & GitLab, management and communication tools such as Jira & Slack among others.
6. Good Remediation Support
Another component of a good web pentest tool is good remediation support that helps customers mitigate the detected and identified vulnerabilities with ease.
Remediation support entails having contact with expert pen-testers and also being provided with step-by-step remediation measures for vulnerabilities.
7. Easy To Use Dashboard
The dashboard should be easy to use and navigate without presenting the customer with an overload of information. It should have options to download the report and view the scan results in real time.
Why Astra is the best in pentesting?
- We’re the only company that combines automated & manual pentest to create a one-of-a-kind pentest platform
- Vetted scans ensure zero false positives
- Our intelligent vulnerability scanner emulates hacker behavior & evolves with every pentest
- Astra’s scanner helps you shift left by integrating with your CI/CD
- Our platform helps you uncover, manage & fix vulnerabilities in one place
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

How to Choose The Best Web Pentest Tool
Here are some factors to consider when buying a web pentest tool.
1. Ease Of Use
The pentest tool should be easy to use, and navigate. The user interface should be user-intuitive with friendly workflows that do not hinder individual or team productivity.
2. Manual Pentesting
The pentest tool that offers the option for manual penetration testing by qualified pen testers is also a bonus since customers can opt for annual or bi-annual in-depth manual penetration testing to ensure the detection of all vulnerabilities.
3. Automated Vulnerability Scanning
Web pentest tools are often accompanied by automated vulnerability scanning which is ideal for conducting quick scans to detect vulnerabilities after a code addition or feature update.
4. Report Format
It is important to consider whether the pentest tool provides multiple report formats for you to choose from be it PDF or XLS. The report should also be detailed, have an easy executive summary, and should be customized keeping the reader in mind.
5. Reduced False Positives
Ensure that the pentest tool provides very low or no false positives. It is resolvable if the tool provides manual vetting of the scan results to weed out any false positives that may pop up.
6. Customer Support
The web pentest tool under consideration should also come with good customer service that is available 24*7 be it through chats, emails, calls, or through the dashboard.
7. Reliability & Experience
Ensure that the company is known for its reliability and experience in the field of web pen-testing with a good number of years of experience. This can be confirmed by going through reputed review sites such as Gartner, G2, and others to know more about their customers’ experiences.
8. Budget
Lastly, keep your budget in mind while narrowing down the list of web pen-testing tools under consideration. Ensure that the pentest tool’s pricing is within your budget and if it’s not, consider whether it offers a multitude of features you need, to explain the increased expenditure. Compare our Pricing here.
The Top Web Penetration Testing Tools in the Market
By now you have formed a general idea about the different kinds of tools generally used by Penetration Testers. Now let us learn about the best web services pentest tools. The tools we list down here are all loaded with great capabilities, however, you have to choose the right ones according to your needs. If you have doubts, you can always talk to the experts.
1. Astra Pentest
Astra Security has been driven by the urge to simplify web application security for users. Astra’s Pentest has taken this philosophy home. This web application penetration testing tool comes with great advantages. For instance, you can integrate CI/CD tools with Astra’s pentest suite, so whenever there is a code update, it launches an automated scan.
Moreover, you can integrate it with say, Jira or Slack, which means you can assign pentest and remediation-related tasks to your team members without them having access to the suite. Of course, the pentest suite itself allows you to connect with developers and security experts. It is like having an in-house security team, without actually having one.
Features –
- Platform: Online
- Scanner Capacity: Unlimited continuous scans
- Manual pentest: Available for web app, mobile app, APIs, and cloud infrastructures
- Accuracy: Zero false positives
- Vulnerability management: Comes with dynamic vulnerability management dashboard
- Compliance: Helps you stay compliant with PCI-DSS, HIPAA, ISO27001, and SOC2
- Price: Starts at $199/month
Some of these features might overlap with offerings from other website pentesting tools, and that is where Astra’s relationship management, support, and goodwill come into play. They have secured companies like Ford, Gillette, and GoDaddy with their security testing tools. You cannot miss them while looking for the best.
Pros
- Can be integrated into the CI/CD pipeline.
- Ensure zero false positives through thorough manual vetting of scan results.
- Helps with cloud vulnerability management.
- Provide round-the-clock customer support.
Cons
- Does not provide a free trial.
- More scope for integrations.
2. NMAP
NMAP is short for Network Mapper. It is an open-source web application pentest tool that helps you map a network by scanning ports, discovering operating systems, and creating an inventory of devices and the services running on them.
It sends differently structured packets for different transport layer protocols which return with IP addresses and other information.
Features –
- Scanner Capacity: Usually scans the 1000 most popular ports of each network protocol
- Manual pentest: NMap is actively used for network mapping and port scanning. These are parts of the manual pentest effort.
- Accuracy: Occasionally shows false positives and faulty insights
- Vulnerability management: No
- Compliance: Indirectly relates to compliance reporting
- Price: Free
You can use the tool for a large network with thousands of devices and ports.
Pros
- Shows open ports, running serves, and other critical facets of a network
- Freely available.
- Usable for large and small networks alike
Cons
- The user interface can be improved.
- Might show different results each time.
So, how does NMAP actually help in security audits?
Well, when security auditors use NMAP to create an inventory of devices and to discover operating systems and applications running on a host network, they can also scan and find out their vulnerabilities to specific security threats.
For instance, if a certain version of an application is declared vulnerable, the network administrator can scan the network to find whether it’s running that version of the application and patch it up if needed.
3. WireShark
WireShark is one of the most famous open-source penetration testing tools for web applications that you can use for protocol analysis. It allows you to monitor network activities at a microscopic level. It is a growing platform with thousands of developers contributing from across the world.
Features
- Scanner Capacity: Captures live packet data from a network interface
- Manual pentest: Useful tool for pentesting
- Accuracy: Fairly accurate
- Vulnerability management: No
- Compliance: Indirectly relates to compliance reporting
- Price: Free
WireShark is the industry standard for protocol analysis in many different sectors. If you know what you are doing, it is a great tool to use.
Pros
- Easy to install
- Freely available
Cons
- Can be difficult for beginners to navigate.
- Could improve its user interface.
4. Metasploit
Metasploit is a Ruby-based open-source framework, used by both ethical hackers and malicious actors to probe systematic vulnerabilities on networks and servers. The Metasploit framework also contains portions of fuzzing, anti-forensic, and evasion tools.
It is easy to install and can work on a wide range of platforms regardless of the languages they run on. The popularity and the wide availability of Metasploit among professional hackers make it an important tool for Penetration Testers as well.
Features
- Scanner Capacity: N/A
- Manual pentest: Metasploit contains an assortment of tools that can be used for pentesting
- Accuracy: N/A
- Vulnerability management: No
- Compliance: Indirectly relates to compliance reporting
- Price: Free
The framework also includes listeners, encoders, post-exploitation code, and whatnot. In the right pair of hands, Metasploit can be a really powerful tool for Pentesting.
Pros
- Includes nearly 1677 exploits.
- Freely available online pentest tool.
- Easy to use.
Cons
- Not beginner-friendly.
- Initial navigation can be difficult.
5. Burp Suite
Burp Suite is a set of penetration testing tools by Portswigger Web Security. It is used by ethical hackers, pen-testers, and security engineers. It is like a one-stop shop for bug bounty hunters and security researchers.
Features:
- Scanner Capacity: Web applications
- Manual pentest: Yes
- Accuracy: False positives possible
- Vulnerability management: No
- Compliance: PCI-DSS, OWASP Top 10, HIPAA, GDPR
- Price: $449/per user/per year
Burp Suite has both a free community edition and a commercial edition.
Pros
- Provides advanced automated pentesting services.
- Provides step-by-step advice for every vulnerability found.
- Can crawl through complex targets with ease based on URLs and content.
Cons
- Advanced solutions are commercialized and can be expensive.
- Does not provide expert customer service and assistance.
6. Nessus

Nessus is a vulnerability scanner by Tenable. It has been used by security professionals for vulnerability assessment since 1998. Their aim is to make vulnerability assessments simple and remediations quick. You can deploy it on a variety of platforms.
Features
- Scanner Capacity: Web applications
- Manual pentest: No
- Accuracy: False positives possible
- Vulnerability management: Yes (Additional Cost)
- Compliance: HIPAA, ISO, NIST, PCI-DSS
- Price: Starts at $4,236.20/year
Now that you have had exposure to the best Penetration Testing Tools, let us circle back to the top of our list.
Pros
- Helps find missing patches that are critical to maintaining security.
- Point-in-time analysis of security system.
- Helps achieve compliance with the scans.
Cons
- Advanced support is only available upon additional payment.
- Takes time to complete scans.
- Can be an expensive solution.
7. Cobalt

Cobalt is another provider of penetration testing as a service. They connect your organization with the global community of vetted penetration testers whose pentesting skills are suitable for your tech stack.
Cobalt’s SaaS platform helps you gather real-time insights so that your teams can get on with the remediation quickly. It helps you with web app pentesting, mobile app pentesting, cloud scanning, and API pentesting.
Features
- Scanner Capacity: Web and mobile applications, APIs, Networks, and Cloud
- Manual pentest: Yes
- Accuracy: False positives possible
- Vulnerability management: Yes
- Compliance: SOC2, PCI-DSS, HIPAA, CREST
- Price: Quote on request
Pros
- Impressive existing clientele including Nissan and Vodafone.
- 14-day trial period.
- Accelerated find to fix cycles
Cons
- The retest often takes too much time
- Complex pricing structure
- Reported false positives
8. Probely
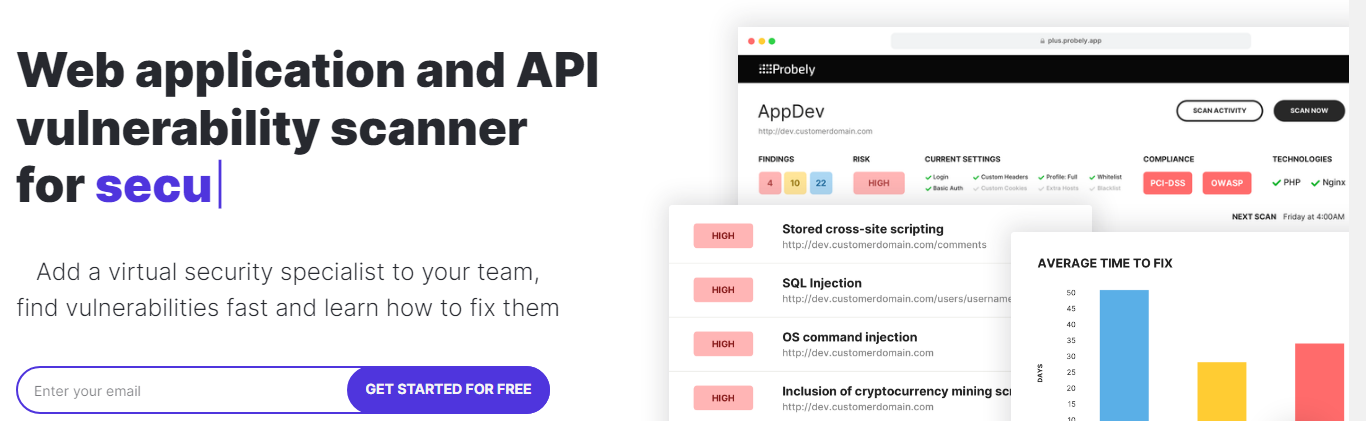
Probely is designed for web application scanning and API scanning. They say, using Probely is like adding a virtual specialist to your team. We will let you be the judge after you look at the features.
Probely automatically prioritizes vulnerabilities based on the risk of the vulnerabilities and provides proof of legitimacy for each issue.
Features
- Scanner Capacity: Web applications, APIs
- Manual pentest: No
- Accuracy: False positives possible
- Vulnerability management: Yes
- Compliance: HIPAA, PCI-DSS, GDPR, & OWASP TOP10
- Price: Starts at $98/month – Pro Plan
Pros
- Simple to use with continuous scanning.
- Wide range of tests.
- Good customer support.
Cons
- Could have better integrations.
- Custom vulnerability scoring does not align with general scoring.
9. Rapid7
As a vulnerability assessment service provider, Rapid7 is another tool for web pentesting that has a range of services dedicated to web application security. They configure the scans, schedule them, validate the findings, and remove false positives.
They optimize the vulnerability scans based on your compliance requirements. These things apart, Rapid7 also provides business logic testing that is otherwise impossible with a vulnerability scanner.
Features
- Scanner Capacity: Cloud and Web Applications
- Manual pentest: Yes
- Accuracy: False positives possible
- Vulnerability management: Yes
- Compliance: CIS, ISO 27001
- Price: Starts at $175/app/month
Pros
- Simple and easy-to-navigate interface.
- Capable of finding hidden vulnerabilities
- Great and easy-to-understand reports.
Cons
- Customer support can be improved.
- Removal of scanned devices must be done manually.
10. Indusface WAS
Indusface WAS combines automated scanning and manual pentesting to help you detect all OWASP top 10 vulnerabilities and business logic errors. Much like Astra, Indusface also promises zero false positives and provides remediation assistance.
The scanner built by Indusface is focused on scanning single-page applications and it offers intelligent crawling. It offers you unlimited scans and detects application vulnerabilities validated by OWASP and WASC.
Features
- Scanner Capacity: Web and mobile applications, APIs
- Manual pentest: Yes
- Accuracy: Zero false positives
- Vulnerability management: Yes
- Compliance: PCI-DSS, ISO 27001
- Price: Starts at $ 59/app/month – Advance plan
Pros
- Assured zero false positives through zero-day protection.
- Helps achieve compliance with regulations like PCI-DSS and ISO 27001.
- Vulnerability detection is not limited to OWASP Top 10.
- It has an executive dashboard that provides necessary information.
Cons
- Not available for mobile applications.
- Reports are difficult to understand.
11. Veracode
Veracode is a dynamic solution and one of the best tools for web application pentesting that helps in the analysis of web apps to find vulnerabilities. It has the capacity to run thousands of tests with a less than 1% false positive assurance rate.
Features
- Scanner Capacity: Web applications
- Manual Pentest: Yes
- Accuracy: False positives possible
- Vulnerability Management: Yes
- Compliance: NIST, PCI, OWASP, HIPAA, GDPR
- Price: Quote upon request
Pros
- Offers quick penetration testing services.
- Extremely comprehensive reports.
- Remediation assistance is provided.
Cons
- Zero false positives are not assured.
- Could improve its user interface
- Can be difficult for beginners.
However, with Veracode, false positives are likely to rise. Along with this, it is also known to be difficult for beginners with much need for improvement in its user interface.
12. OpenVAS
OpenVAS is an open-source penetration testing software that is comprehensive and powerful. It is supported and updated constantly with the help of expert pentesters all around the world thus making it up to date.
Features
- Scanner Capacity: Web applications, network protocols
- Manual Pentest: No
- Accuracy: False positives possible
- Vulnerability Management: No
- Compliance: No
- Price: Free
This tool can be difficult for beginners. It is also prone to missing basic vulnerabilities and may result in false positives.
Pros
- Automated vulnerability scanning is quick and efficient
- Freely available network vulnerability scanning tool.
- Constantly updated
- Scans for improper file access, XSS injections.
Cons
- Could be difficult for beginners to make use of.
- Automated causes false positives to appear.
13. Acunetix
This is software that provides vulnerability assessments and automated penetration tests provided by Invicti. Acunetix helps reduce vulnerabilities across various kinds of web applications.
It also allows the scanning of multiple environments as well as the prioritization of vulnerabilities.
Features
- Scanner Capacity: Web applications
- Manual Pentest: No
- Accuracy: False positives possible
- Vulnerability Management: Yes
- Compliance: OWASP, ISO 27001, PCI-DSS, NIST
- Price: Quote on Request
Pros
- Time release of updates
- Can find a wide array of vulnerabilities.
- Agile testing with detailed reports
Cons
- Does not provide expert remediation assistance with professionals.
- Does not ensure zero false positives.
- Pricing is not mentioned.
- Dated user interface with scope for improvement.
14. Breachlock

Breachlock offers Penetration Testing as a Service or PTaaS. It is a SaaS platform that allows you to request a pentest and after the penetration test is conducted you can avail of monthly scans through the same SaaS platform.
Breachlock has a team of ethical hackers who conduct AI-augmented web app pentest to give you a comprehensive picture of your security posture and certify you for having conducted a pentest.
Features
- Scanner Capacity: Web and mobile applications, Network, APIs, cloud.
- Manual Pentest: Yes
- Accuracy: False positives possible.
- Vulnerability Management: Yes
- Compliance: PCI DSS, HIPAA, SOC 2, ISO 27001, GDPR
- Price: Quote on request
Pros
- Continuous addition of risk checks
- Scalable vulnerability management solution
- Manual and automated testing options
- Helps in the identification of grey areas in the codes
Cons
- Product support could be improved
- Documentation can be confusing
What is Penetration Testing?
Penetration Testing is an offensive security exercise where security engineers simulate a controlled hack of your systems, find vulnerabilities, exploit them, and tell you how to fix them. At the end of a penetration test, you receive a pentest report that documents all the vulnerabilities your systems have along with the risk attached to each of them. The report also contains guidelines to reproduce and remediate the vulnerabilities.
How is a Pentest different from a Vulnerability Assessment?
You must have noticed that vulnerability assessment and penetration testing are coupled in the same phrase: VAPT. Sure, both VA and PT are examples of security testing procedures but there is no reason to think they are the same thing.
Vulnerability assessment is an automated process where a system is scanned for known vulnerabilities and the found vulnerabilities are assigned risk scores according to the common vulnerability scoring system (CVSS). It is usually a very quick procedure.
Penetration testing takes it up a notch and exploits certain vulnerabilities to learn more about them. It involves automated as well as manual processes. Vulnerability assessment is a part of the penetration testing process.
Why do you need Penetration Testing?
- To get a comprehensive understanding of the security posture.
- Gain tangible insight into the risk posed by each vulnerability.
- Get thorough and efficient guidance for remediation of the issues.
- Connect vulnerability remediation with business outcomes.
- Test your current security measures against a potent threat.
- Comply with relevant security standards.
Penetration testing allows an organization to understand its security posture – how it would fare against an actual attack. It is a necessary procedure for specific industries where a pentest certificate is essential for compliance. In order for you to conduct a penetration test successfully, it is very important to form an idea about different types of web pentest tools.
Different types of tools used by pentesters
The process of Pen testing is generally divided into five steps. The Pentest starts with planning, followed by scan, infiltration, escalation, and analysis. Each of these steps requires certain kinds of tools. We will look into different types of tools a Pentester needs to be equipped with.
Port Scanners
You can use a port scanner to send a packet to specific ports to uncover security vulnerabilities. Ports are virtual points where network connections start or end and each port is associated with a different process. Port scanners are used to identify open ports in a network that are treated as vulnerabilities.
Vulnerability Scanners
A vulnerability scanner is an automated tool that you use to create an inventory of all IT assets and then test them for known vulnerabilities. A security professional can use the report generated by a vulnerability scanner to identify security loopholes and categorize them by severity.
Network Sniffers
Network sniffers can monitor network traffic and information. It can be used by blackhats to ‘sniff’ traffic to steal passwords or other information. Network administrators can use it to find vulnerabilities and ensure a secure environment.
Intercept Proxy
An intercepting proxy sits between the client-side browser and the internet. It allows you to monitor and alter responses and requests by intercepting the connection. It is a very important tool for web-application vulnerability assessment.
Password Cracker
Just as the name suggests, a password cracker is used to crack passwords. There are several different password cracking techniques like brute force, dictionary attacks, combined dictionary attacks, Rainbow table attacks, etc. These techniques are used by both attackers and pen-testers.
What Are The Top Penetration Testing Techniques?
The top penetration testing techniques include:
Black Box Pentesting
Black-box penetration testing is a technique of testing where the pentester does not have any prior information about the target that is to be exploited.
Since the testers don’t have any information about the target, it is the closest simulation to a real attack. The tester has no information regarding the source codes, or internal software information like structure and application design.
White Box Pentesting
White Box Penetration Testing is a technique in which the internal structure and function of a system or network are known to the penetration tester.
White Box testing is often used to pentest internal networks and systems of a company.
Gray Box Pentesting
Gray box penetration testing is a type of penetration testing in which the pentesters have partial knowledge of the network and infrastructure of the system they are testing.
It is a combination of black-box and white-box pentesting where a solid understanding of the system is required and it is often used in more controlled environments.
Why Astra Pentest Is An Easy First Choice
Simplicity, speed, and convenience put Astra right at the top of the list of web pentest tools. If you consider the intuitive dashboard, integrations, ease of use, and the success this company has had over the last couple of years, you realize, that it does not get any better. And yet, the researchers and engineers at Astra are on a relentless quest to make it better. Take the latest login recorder extension, for example, it makes authentication for scan behind login pages completely hassle-free for users.

From creating a game plan for the pentest, to remediating the issues, the security engineers at Astra ensure you get what’s best for your business. They have an outstanding track record when it comes to working with your developers and helping them solve the detected issues. The publicly verifiable certificate that you get helps your organization build trust.
To Conclude
Making the right call at the right time is what puts you ahead of your peers and this fact holds when it comes to security testing. It is impossible for you to know when a critical vulnerability will blow up in the face of your business operations. It is better to prepare and prevent than to react to a disaster. It starts with choosing the right web pentest tools and ends with you achieving a ‘safe to do business’ certificate.
FAQs
How much time does it take to complete a Pentest?
It may take 4-10 days to complete a penetration test depending upon the scope of the test. The rescans after fixing the vulnerabilities may take half the time taken by the initial test.
How much does a pentest for web applications cost?
The cost of penetration testing for web applications is between $99 and $399 per month depending on the scope of the test and the number of scans.
Do I get free rescans after the vulnerabilities are fixed?
Yes, you get up to three rescans based on the plan you are on. You can avail of these rescan within 30 days of the initial scan completion.
![Web Pentest Tools [Top 14]: Types and Easy First Choice](https://cdn-blog.getastra.com/2022/02/Copy-of-Featured-Images-39.png)















