OWASP Penetration Testing is a specialized type of security testing that focuses on attack vectors and vulnerabilities listed in OWASP Top 10. An organization’s security landscape is complex, and thus it is essential to test the organization’s security measures to ensure that they are working correctly.
OWASP’s (Open Web Application Security Project) compiled a list of the top 10 attacks named OWASP Top 10 for multiple technologies such as Web Applications, Cloud, Mobile Security, etc. The process of testing the top 10 security risks mentioned in OWASP top 10 is known as OWASP Penetration Testing.
What is OWASP Top 10?
The Open Web Application Security Project (OWASP) is a non-profit organization with a mission to make secure applications with free online educational content and community tools. Their mission is to make software security visible by providing all the tools, techniques, and mindsets to increase the application security of any software product.
OWASP was set up by cybersecurity enthusiast Mark Curphey on September 9, 2001, to control the rampant cyberattacks. In addition, they provide a bunch of free educational content on security testing and web application security and a variety of other resources for developers and IT professionals.
OWASP Top 10 is a standard awareness document for developers and web application security. The OWASP Top 10 does not address all possible vulnerabilities, but it accurately identifies the most common and critical web application security risks.
It focuses on the most common types of security risks web applications face, not all possible security risks. The OWASP Top 10 is a good standard of security expectations for new applications and a helpful security checklist for more mature applications.
Recent Trends in OWASP Top 10
After more than four years of research, the Open Web Application Security Project (OWASP) has released its latest list of the top 10 application security risks. Below mentioned are the new security risks that have been added to the updated list.
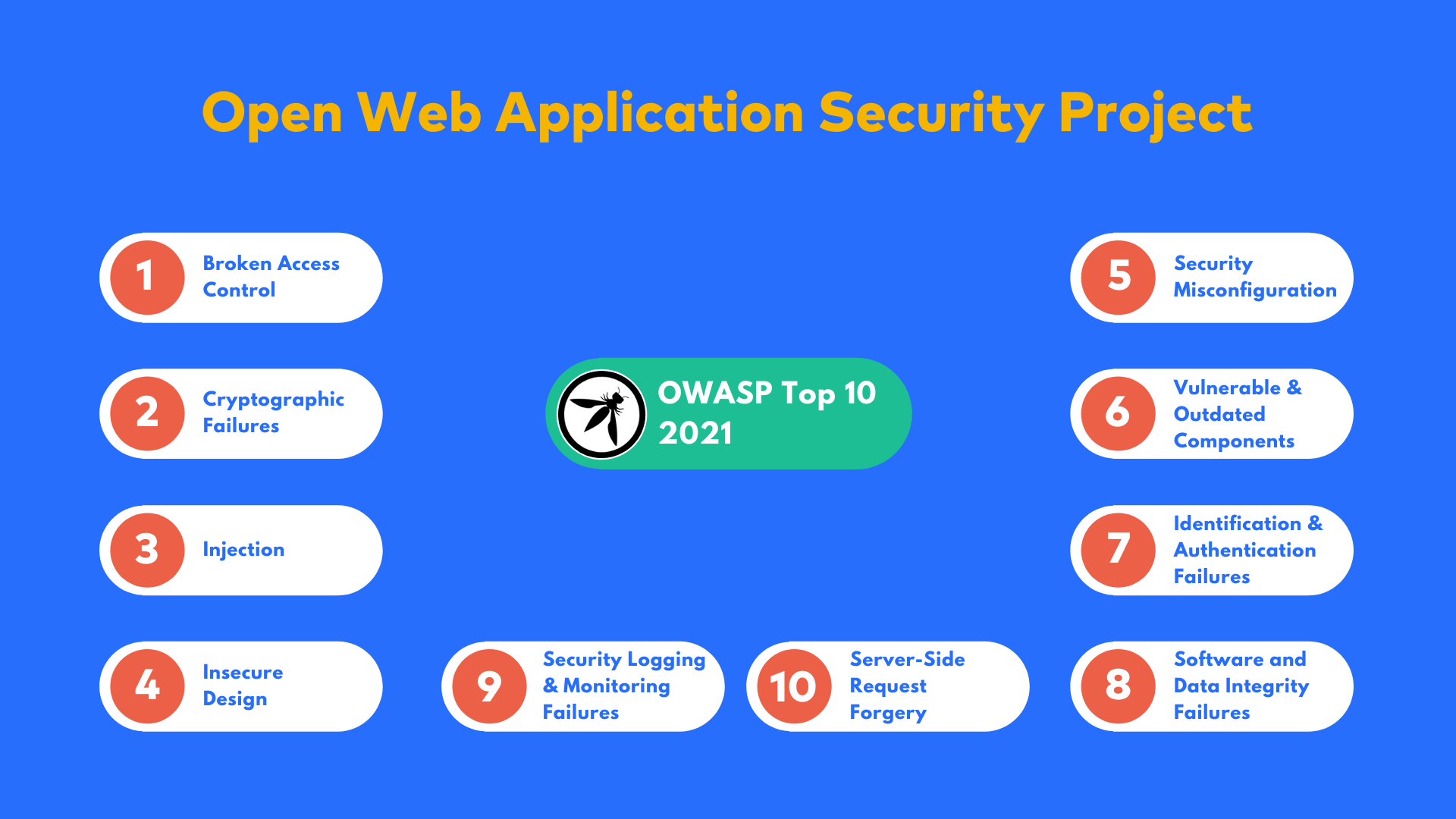
1. Insecure Design: Insecure design can also occur when a design checked for security vulnerabilities is not updated to account for known security vulnerabilities. Insecure design can occur at different levels of a given product.
2. Software and Data Integrity Failures: Data integrity is the state of being whole, authentic, and unbroken. There are many ways that software or data can fail to uphold integrity. Insecure deserialization, untrusted CDN’s, insecure CI/CD pipelines are how software fails to maintain the integrity of the data.
3. Server-Side Request Forgery: SSRF (Server-Side Request Forgery) is a vulnerability when an application makes a request to an unauthenticated, remote host and does not validate the request correctly. Any website that allows external requests to be made to other hosts based on user input is vulnerable to SSRF.
| S No. | OWASP 2017 | OWASP 2021 |
|---|---|---|
| A01 | Injection | Broken Access Control |
| A02 | Broken Authentication | Cryptographic Failures |
| A03 | Sensitive Data Exposure | Injection |
| A04 | XML External Entities (XXE) | Insecure Design |
| A05 | Broken Access Control | Security Misconfiguration |
| A06 | Security Misconfiguration | Vulnerable and Outdated Components |
| A07 | Cross-Site Scripting (XSS) | Identification and Authentication Failures |
| A08 | Insecure Deserialization | Software and Data Integrity Failures |
| A09 | Using Components with Known Vulnerabilities | Security Logging and Monitoring Failures |
| A10 | Insufficient Logging & Monitoring | Server-Side Request Forgery |
Basics Of Pentesting
In order to undergo OWASP Penetration Testing, let’s first understand what penetration testing is. A penetration test is a method of evaluating a computer system or network to identify vulnerabilities that a malicious attacker could exploit.
Security experts carry out penetration testing to identify vulnerabilities in the target software or system. Penetration testing is an integral part of a more extensive information security process to ensure proper risk management, compliance, and systems administration.
A penetration test is an excellent way to determine the extent of the damage a hacker can cause. Penetration testing can be done at any point in time to find vulnerabilities in the system. Penetration testing can help to ensure that an organization’s security measures are working correctly.
Understanding OWASP Top 10 in-depth
As mentioned, OWASP updated the list of vulnerabilities recently (in 2021). Let’s understand them in-depth one by one:
1. Broken Access Control
Broken Access Control vulnerabilities are among the most common security bugs found in web applications. Broken Access Control vulnerabilities, also known as missing authorization, occur when an application does not correctly check for authorization or does not check for authorization at all. This allows users to view or edit protected data they should not be able to view or edit.
2. Cryptographic Failures
Encrypting sensitive data is a necessary step that needs to be performed in every development process. The aim of implementing cryptographic measures is to make sure that the data is protected. Some common issues that fall under cryptographic failures are:
- Using HTTP to transmit sensitive data
- Hard-Coded sensitive data such as API Keys
- Weak Encryption being used
- Improper key management
- Missing Key Rotation mechanisms
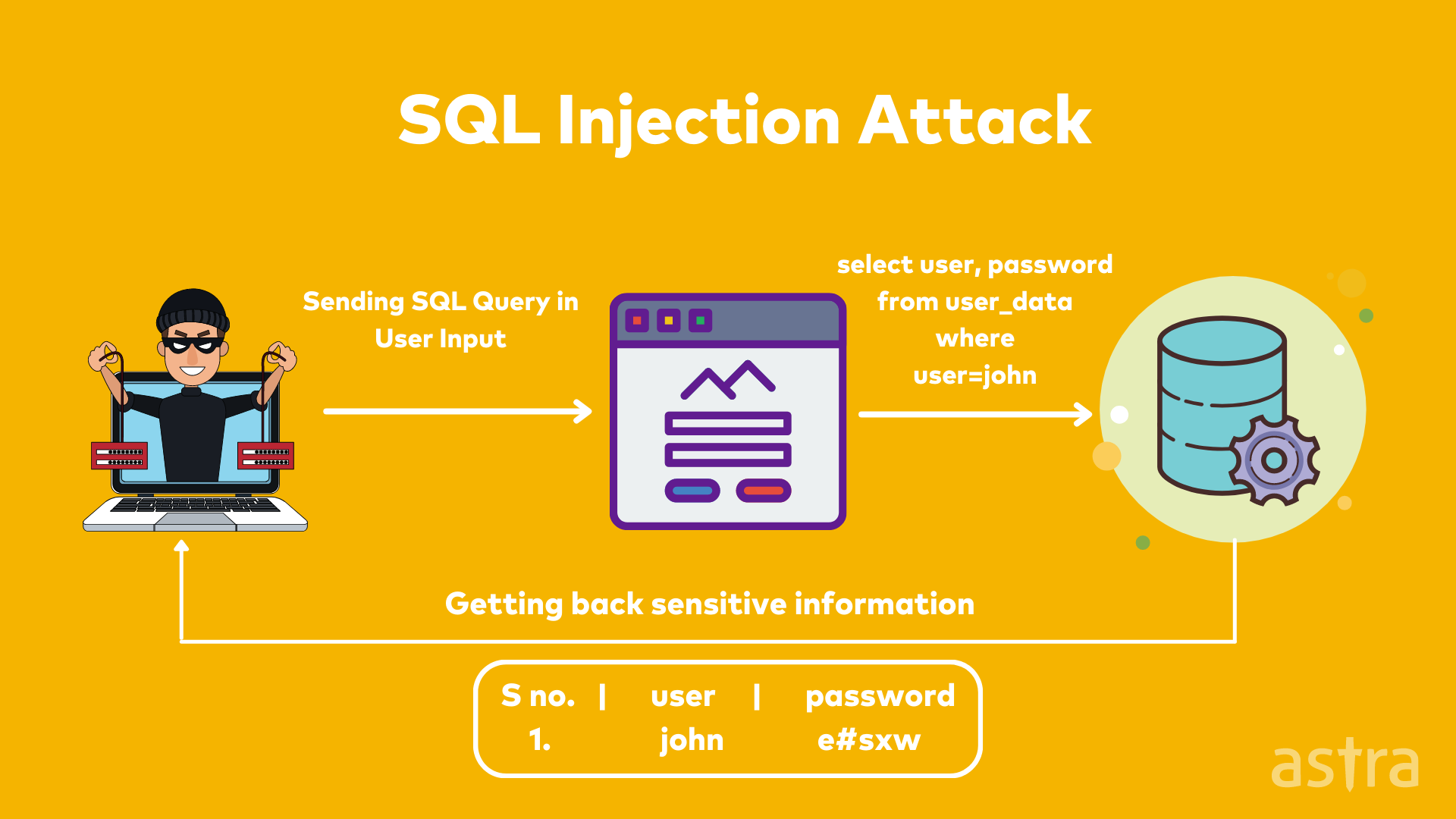
3. Injection
Injection attacks are a common type of attack. They happen when a user enters a malicious payload to a website’s input field. This payload is then processed by the website and executed as a malicious script written by the hacker. The malicious script is what performs the actual damage to the website’s server and its data. There are several different types of injection attacks. All of them involve a malicious payload. The payload is entered via a form field, URL, or API (Application Programming Interface).
4. Insecure Design
Insecure design refers to a variety of security issues and not a single issue. The cause of insecure design is the same as the cause of insecure coding, which is a lack of knowledge and awareness of security vulnerabilities. Most of the time, security is not taken as a serious issue and is not included in the list of requirements for software development.
5. Security Misconfiguration
Security Misconfiguration moved from #6 in OWASP Top 10 – 2013 to #5 in the updated OWASP Top 10 – 2021t. Security Misconfiguration is a broad range of vulnerabilities such as:
- Default Credentials being used
- Server version disclosure
- Missing security headers such as X-Frame-Options
6. Vulnerable and Outdated Components
The most common issue in most web applications is using components with known vulnerabilities and out-of-date components. Usually, the issue is not due to a lack of knowledge but due to difficulty in the version migration.
Components like jQuery, Bootstrap, Angular JS, etc., are the most vulnerable components. These are the most used components in web applications. They are also viral components for hackers; vulnerabilities are more common in them due to their popularity.
7. Identification and Authentication Failures
Identification and Authentication Failures were previously known as Broken Authentication and have moved from #2 to #7. Common Weakness Enumerations(CWE’s) have also been added to this. Some common vulnerabilities that fall under Identification and Authentication Failures are:
- Missing Brute Force protection
- Weak password policy
- Missing or weak multi-factor authentication
- Improper session management
8. Software and Data Integrity Failures
Data integrity failures are still widespread in software engineering. It isn’t easy to maintain data integrity of your data if you are not careful with your code. Data integrity failures lead to security flaws. Insecure deserialization, untrusted CDN’s, insecure CI/CD pipelines are how software fails to maintain the integrity of the data.
9. Security Logging and Monitoring Failures
Log monitoring is a crucial part of any security program. It is one of the most crucial areas of log management that helps companies detect and analyze security events in near real-time. Yet, in 40% of organizations, log management systems cannot detect and analyze security events in near real-time. The reason is that log monitoring is often insufficiently customized and managed.
10. Server-Side Request Forgery
Server-side request forgery (SSRF) is a vulnerability when an application makes a request to an unauthenticated, remote host and does not validate the request correctly. In essence, the application is tricked into requesting a host that it thinks is local but is remote.
This type of vulnerability is dangerous because the software running on the remote host is not authenticated, meaning that it may have been compromised or configured to execute malicious code.
Why is OWASP Penetration Testing important?
OWASP penetration testing is an integral part of any security program. It helps the organization find and patch security risks before hackers exploit them. OWASP penetration testing is a systematic approach that identifies vulnerabilities in an application’s design, code, and supporting systems (such as network, hardware, and hosted services) and determines how an attacker can infiltrate the application.
Penetration testing and other security practices, such as risk analysis and source code review can help you build and maintain a secure enterprise.
Three benefits of performing OWASP Penetration Testing
- OWASP Top 10 is a list of the most common security vulnerabilities. OWASP penetration testing focuses on that list and helps companies uncover security risks.
- OWASP Penetration testing is also helpful in discovering and documenting vulnerabilities, which can help system administrators prioritize their efforts at securing the system.
- OWASP penetration testing can help you achieve common security standards such as HIPPA, PCI DSS, SOC2.
5 Best practices to avoid vulnerabilities
1. Implement Proper Multi-Factor Authentication
Multi-factor authentication is a security measure that requires you to provide more than one form of identification before accessing a system or service. A multi-factor authentication scheme can be a password, pin or fingerprint.
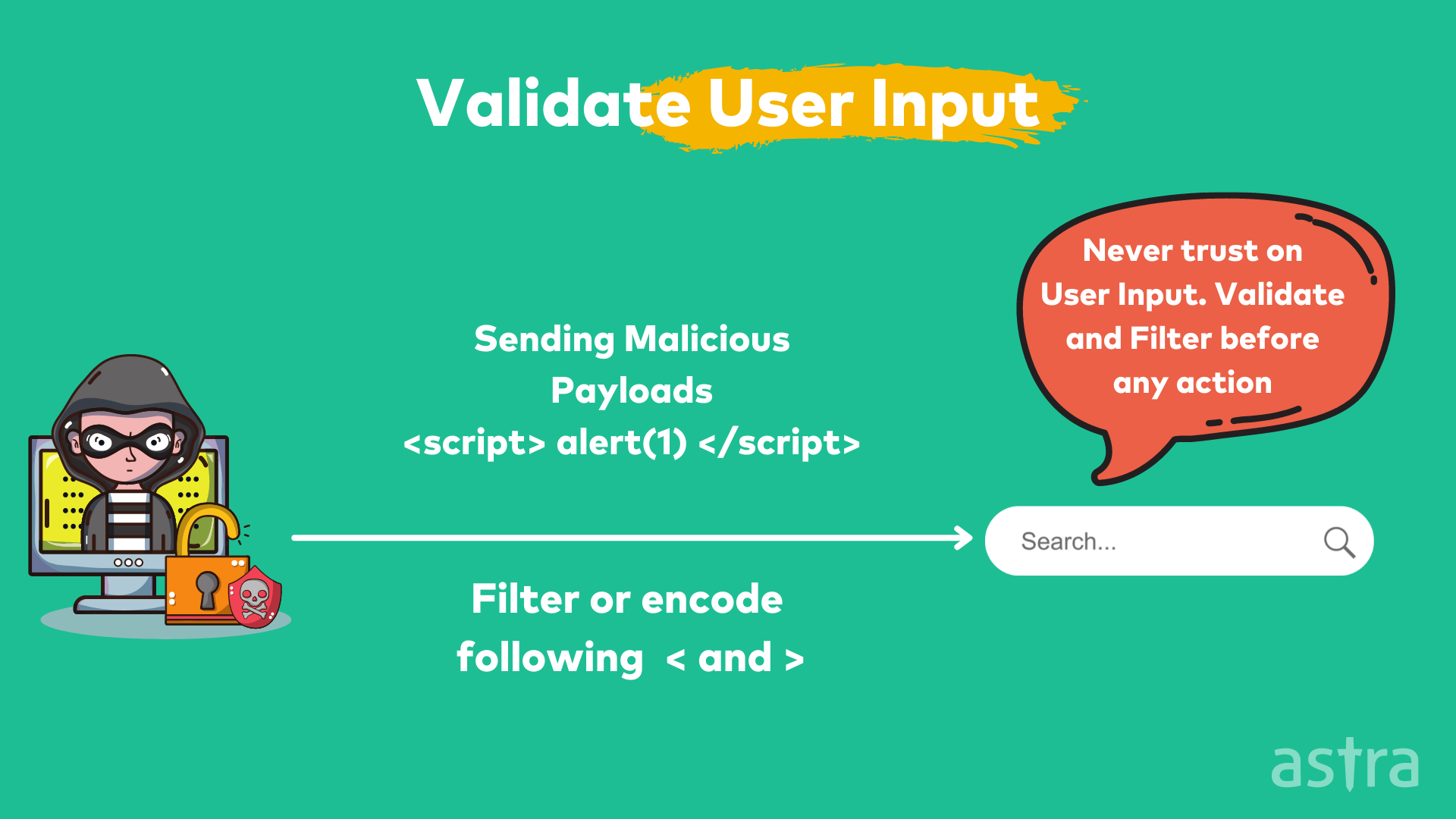
2. Validate user input
Input validation is the first and foremost step to securing your application from malicious attacks. It can be defined as a process of checking and testing an input provided by the user or the application to make sure that it does not pose any security or integrity issues. This can be done by validating the input data’s type, format, length, range, consistency, etc. Input Validation can be broadly classified into two categories:
- Client-side Validation
- Server-side Validation
3. Implement Cryptography
Cryptography is the practice and study of techniques for secure communication. Cryptography protects sensitive information, such as information used in credit card transactions from being accessed by an attacker.
Even though cryptography has been used for thousands of years, it is still a vital part of data security today. Cryptography is the art of creating codes and ciphers that make messages unreadable by anyone except those intended. It is a way to store and transmit information securely.
4. Manage Access Controls
Managing access controls properly is an integral part of an application. Privilege Escalation is a type of security risk in which a low-privileged user can access user resources with privileges that originate due to missing or improper access controls in the applications and managing these privileges properly can help prevent this risk.
5. Proper error handling
Error handling and logging are two of the most important things to remember when creating development tools. Error handling is the ability for code to anticipate error situations and provide the best possible outcome.
Logging is the ability for error handling to keep track of these errors either through a log file or in memory. When creating development tools, error handling and logging are the most important things to remember.
The list of secure coding practices is not limited to the techniques mentioned above. Check out Astra’s Ultimate Secure Coding Checklist to get rid of security risks.
Checkout Astra’s Amazing Secure Coding Checklist
What Is OWASP Penetration Testing Kit?
OWASP penetration testing kit is a browser designed to simplify the day-to-day application security process.
The browser provides in-depth information about OWASP security testing like the technology stack, WAFs, crawled links, and authentication flows.
Other services this extension provides include a cookie editor, SCA scans, integrated swagger.io, and even a Selenium integration.
Installations are available for Firefox, Chrome, and MS Edge.
OWASP Penetration Checklist
This OWASP testing guide has been released by OWASP to promote consistency among internal penetration testing and the services provided by external vendors.
The list doesn’t describe the methods to be used for testing, however, it does specify the various targets that ought to be tested.
It can be used as an RFP template, Benchmarks, and OWASP web security testing guide.
OWASP web security testing guide provides a comprehensive guide for the testing of web applications and services.
The website security testing guide was created by the collaborative efforts of numerous cybersecurity professionals and volunteers.
How much does an average Pentest cost?
The cost of a penetration test is a fixed value. The cost depends on a lot of factors such as:
- Size of Organization
- Approach to perform pentest
- Scope of pentest
- Experience of Pentest vendor
- Time to perform pentest
- And much more!
Penetration testing pricing varies on a case-by-case basis, but you can expect the cost to fall in the range of $2,000 to $20,000.
Why choose Astra for OWASP Penetration Testing?
If you search for an OWASP penetration testing service provider, you will find that the options seem endless. There are many reputable penetration testing companies that you can choose from, but choosing the right one for your needs may not be easy.
You need to have complete coverage of the code, the security of the network, and even of the organization’s employees. You need to have a full scope of services that tells you precisely what is being done, how it is being done, and why.
With Astra, you get all of this. Astra offers various penetration testing solutions, including OWASP penetration testing at pocket-friendly pricing. All you need to do is get in touch with an Astra-naut, and we’ll take it from here.
Conclusion
OWASP penetration testing is to make sure that security flaws are not present in the applications. OWASP penetration testing will check for the vulnerabilities present in the application. At Astra, We believe that it is our job to help businesses create secure applications. When it comes to application security, companies need to know that their applications are secure and secure enough.
FAQs
1. What is the timeline for OWASP-based pentest?
The initial scan for OWASP penetration testing takes 7-10 days for web or mobile applications, and 4-5 days for cloud infrastructures. Vulnerabilities start showing up in Astra’s pentest dashboard from the second day of the scan. The time-line may vary slightly depending on the scope of the pentest.
2. How much does penetration testing cost?
The cost for penetration testing ranges between $99 and $399 per month for web apps.
3. Why choose Astra Pentest?
8000+ tests, adherence to OWASP top 10 testing methodology, intuitive dashboard with dynamic visualization of vulnerabilities and their severity, security audit with simultaneous remediation assistance, multiple rescans, these are the features that give Astra an edge over all competitors.
4. Do I also get rescans after a vulnerability is fixed?
Yes, you get 2-3 rescans depending on the plan you are on. You can use the rescans within a period of 30 days from initial scan completion even after a vulnerability is fixed.
















