Vulnerability assessment is a methodology that is manually carried out to identify, classify and prioritize vulnerabilities and security risks based on the severity they pose to the assets. This assesses if the assets can be accessed improperly, destroyed, or damaged.
To find and fix these issues, you’ll want to use a comprehensive vulnerability assessment methodology. This guide will walk you through the process of conducting a thorough vulnerability assessment and some other related aspects.
Vulnerability Assessment: The Definition
A vulnerability assessment is part of the security strategy of an organization that wants to identify security weaknesses in their systems and take immediate steps to fix them on time. In other words, it’s a way to find out where an organization’s digital assets are most vulnerable so that they can take steps to mitigate the risks.
The Difference Between Vulnerability Scanning and Vulnerability Assessment
Vulnerability scanning is an automated process that uncovers potential vulnerabilities in systems and software. It does not provide information on the impact and severity of the vulnerability or how they can be exploited using different exploitation techniques.
Whereas, vulnerability assessment methodology is a manual process that identifies, classifies, and prioritizes vulnerabilities in systems and software. It does provide information about the impact and severity of the vulnerability and how it can be exploited.
Vulnerability scanning is an important part of vulnerability assessment. However, it is not enough on its own. Vulnerability assessment also requires manual analysis to identify and prioritize vulnerabilities.
Why perform vulnerability assessment?
Vulnerability assessment is important because it helps organizations to:
- Understand where their digital assets are most vulnerable.
- Take steps to mitigate the risks.
- Prioritize vulnerabilities so they can be addressed accordingly.
Also Read: Top 7 Cyber Security Auditors for SaaS Companies
Types of Vulnerability Assessments
Typically, there are two types of vulnerability assessments:
- External vulnerability assessment
- Internal vulnerability assessment
External Vulnerability Assessment
An external vulnerability assessment methodology is conducted from the perspective of an outsider or attacker. It assesses an organization’s digital assets and systems that are accessible from the internet.
This type of assessment is critical for an organization to perform because it can provide you details about all the discovered vulnerabilities that can be exploited by hackers, if not fixed on time. It can also help organizations understand how well their systems and data are protected from external threats.
Internal Vulnerability Assessment
An internal vulnerability assessment methodology is conducted from the perspective of an insider or privileged user. It assesses an organization’s digital assets and systems that are accessible from within the network.
This type of assessment is important because it can identify vulnerabilities that can be exploited by malicious insiders. It can also help organizations understand how well their systems and data are protected from internal threats.
Also Read: What is Network Vulnerability Scanning? The Ultimate Guide
How Vulnerability Assessment and Risk Assessment is Related?
We can say that the Vulnerability assessment is kind of a subset of any organizations’ risk assessment process. A risk assessment process includes details on all potential risks to an organization, not just cyber risks. Cyber risks are a type of operational risk that can be assessed using vulnerability assessments.
Vulnerability assessments primarily focus on the identification and classification of technical vulnerabilities. Risk assessments take a more holistic approach that includes non-technical risks such as financial, reputational, and regulatory risks.
However, both vulnerability assessment and risk assessment aim to identify potential risks so they can be mitigated or managed. You can also say that the vulnerability assessment is a part of a vulnerability management program.
Vulnerability Assessment Methodology
There are many different ways to conduct a vulnerability assessment. The most important part is to ensure that the methodology used is proper for the organization and the assets being assessed.
Some common methods of conducting a vulnerability assessment include:
- Penetration testing
- Vulnerability scanning
- Manual analysis
- Risk management
Also Read: 5 Steps Approach to Penetration Testing Methodology | Top 5 Software Security Testing Tools in 2022 [Reviewed]
1. Penetration Testing
Penetration testing, also known as pen testing, is a type of security test that simulates an attack on a system or application. It is performed by ethical hackers to identify vulnerabilities using an offensive or active set of tools that typically acts as a perpetrator.
Pen tests can be conducted manually or automatically. Manual penetration tests are conducted by ethical hackers who attempt to exploit vulnerabilities in systems and applications. Automated penetration tests are conducted using software tools that simulate an attack.
2. Vulnerability Scanning
Vulnerability scanning is a type of automated test that scans for known vulnerabilities in systems and applications. Vulnerability scanners can be used to assess both internal and external systems.
Scanners use a database of known vulnerabilities, also called a vulnerability signature database. When a scanner identifies a potential vulnerability, it generates a vulnerability scanning report that includes information about the severity of the vulnerability and how it can be exploited.
3. Manual Analysis
Manual analysis is conducted by security analysts who manually review system code, configuration files, and log files to identify potential vulnerabilities. Manual analysis is often used in conjunction with automated tests such as penetration testing and vulnerability scanning.
4. Risk Management
Risk management is the process of knowing and mitigating risks to any organization’s IT or other internal systems. It is a proactive approach to security that helps organizations identify and reduce the impact of potential internal as well as external incoming and outgoing threats.
Risk management includes four steps:
- Identify – Identify potential risks to the organization
- Assess – Assess the likelihood and impact of each risk
- Mitigate – Mitigate the risks with controls such as security policies and procedures
- Monitor – Monitor the effectiveness of controls
Read Also: A 10-Point Vulnerability Assessment Checklist to Secure Your Business
Type of Tools for Conducting Vulnerability Assessment
There are many different types of vulnerability assessment tools available. Some common tools include:
- Port scanners
- Web app scanners
- Database scanners
- Configuration auditors
- Log analysis tools
Port Scanners
A port scanner is a type of tool that scans for open ports on systems and applications. Port scanners are used to identify which services are running on a system and what type of access they have.
Web Application Scanners
A web application scanner is a type of tool that scans for vulnerabilities, security loopholes, and misconfiguration errors in web applications. Web application scanners can be used to assess both internal and external systems.
Also Read- IoT Security Testing | Top 6 Web Pentest Tools You Should Not Miss in 2022
Database Scanners
A database scanner is a type of tool that scans for vulnerabilities in databases. Database scanners can be used to assess both internal and external systems.
Configuration Auditors
A configuration auditor is a type of tool that audits the configuration of systems and applications. Configuration auditors can be used to assess both internal and external systems.
Log Analysis Tools
A log analysis tool is a type of tool that analyses log files to identify potential vulnerabilities. Log analysis tools can be used to assess both internal and external systems.
Also Read: 11 Top Penetration Testing Tools of 2022 [Reviewed]
Vulnerability Assessment Solution by Astra
We at Astra provide a comprehensive offering to deal with all your needs regarding the vulnerability assessment and penetration testing for your applications, networks, cloud infrastructures, APIs and more.
Astra’s Pentest Suite is specifically designed to perform a thorough vulnerability analysis of your systems by conducting a set of test cases (over 8000+). The suite also offers continuous vulnerability scanning that helps you secure your system during real time hacks and cyberattacks.
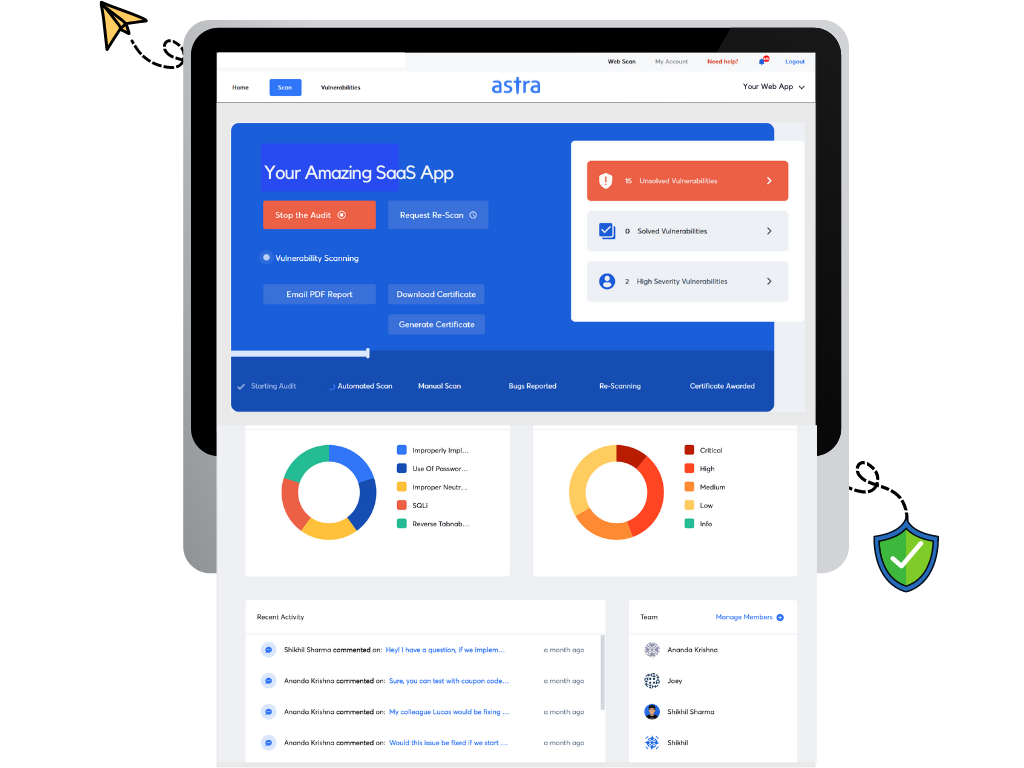
Here are some key features of Astra’s Pentest Suite:
- Automated Vulnerability Scanners with scan behind login pages feature.
- Automated and Manual Penetration Testing.
- Centralized dashboard for vulnerability management services.
- Detailed analysis for discovered vulnerabilities with a risk score, impact, severity and more.
- Collaborative dashboard to connect your dev teams with security engineers at Astra.
- A separate dashboard for Compliance test cases. (for SOC2, ISO27001, HIPAA, PCI-DSS, GDPR and more)
- CI/CD pipeline integration.
- Industry recognized Pentest Certificate after every successful scan.
And more…
Conclusion
Vulnerability assessment is an important part of any security program. There are many different methods of conducting a vulnerability assessment, and the most important part is to ensure that the methodology used is appropriate for the organization and the assets being assessed.
















