According to the recent IBM’s Cost of a Data Breach Report 2023, 45% of breaches are cloud-based, and 80% of companies have experienced at least one cloud security incident in the last year.
Moreover, with the global cloud computing market at $546.1 billion in 2022 and growing, adopting holistic cloud security practices has become critical.
This is where the importance of the AWS Security Audit comes in. An AWS security audit helps you discover all hidden vulnerabilities in your web system that can put your entire system at risk.
If you are wondering what an AWS security audit includes or where to get an AWS security audit from, look no further.
What is AWS?
AWS (Amazon Web Services) is Amazon’s implementation of the cloud computing concept. It offers around 175 fully-featured services from data centers globally and is currently a popular choice for cloud-based hosting in the industry. In simple words, AWS will let you host their computers (i.e servers) and thus allow you to:-
- Run Web and application server to host your dynamic websites.
- Securely store information on the cloud to access them over WAN.
- Host your database such as MySQL, PostgreSQL, etc on the cloud.
- Receive solutions for CDN or Content Delivery Network which can be troublesome to host on your network.
- Host SMTP, i.e., the mail server on cloud and send emails in bulk to your customers.
What is AWS Security Audit?
An AWS security audit is a comprehensive assessment of an organization’s AWS cloud environment to identify and mitigate security risks and vulnerabilities. It encompasses reviewing configurations, access controls, encryption, and compliance with AWS security best practices to ensure the protection of data and resources hosted on AWS.
The AWS cloud security audit can be divided into 2 categories:-
1. Security of Cloud
AWS manages the security of the cloud. This includes all the logic flaws or zero days that can be used to exploit the instance of the server. Security audit of the server is Amazon’s responsibility and you need not meddle with that.
2. Security in the Cloud
Security in the cloud is your responsibility. You can control the security of the instance by choosing what you decide to implement and how you do it. If you configure your web app securely, it can lead hackers to gain unauthorized access to the web app.
Why perform an AWS security audit?
Data Breach is the worst thing that can happen to a company. It ruins the customers’ trust in the firm forever. There are enough instances where such a hack brought a complete debacle for a business. But, besides the reputation loss, are there any other reasons you should be conducting an AWS security audit?
An AWS security audit is important for identifying and mitigating security risks, complying with regulatory requirements, and improving your security posture. It can help you identify unauthorized access to AWS resources, detect malicious activity in your AWS environment, and validate your security controls.
Hence, it’s crucial to do an AWS Security Audit while there is still time, at least once a year, or more often if you experience any changes to your AWS environment or if you are subject to specific compliance requirements.
In fact, for continued security, you should carry out the AWS security audits regularly. The recommended time is as follows:
- Reviewing System logs on a monthly basis.
- Checking the behavior of the hosted service for abnormalities or something suspicious every 4 to 6 months.
- Running a full scan to ensure no breach occurred any year.
There are many automated tools available to aid the process of the AWS security audit. However, using a manual enumeration is also recommended. The next segment will elaborate more on the manual AWS security audit and its pre-requisites.
What is covered in the AWS security audit?
An AWS security audit typically covers the following areas:
1. AWS Identity and Access Management (IAM):
This includes reviewing IAM users, groups, roles, and policies to ensure that they are configured correctly and that users and software have only the permissions they need.
2. AWS resources:
This includes analyzing all of your AWS resources, such as EC2 instances, S3 buckets, and RDS databases, to ensure that they are configured securely and that they are not vulnerable to known attacks.
3. AWS security services:
This includes looking into your use of AWS security services, such as AWS GuardDuty, AWS Inspector, and AWS CloudTrail, to ensure that they are configured and used correctly.
4. AWS network:
This includes evaluating your AWS network configuration to ensure that it is secure and that it is meeting your security requirements.
5. AWS logging and monitoring:
This includes reviewing your AWS logging and monitoring configuration to ensure that you are collecting the necessary data and that you can detect and respond to security incidents promptly.
In addition to these general areas, an AWS security audit may also cover specific areas of interest, such as compliance with specific regulatory requirements or the security of specific applications or systems.
AWS Security Audit 101
Step 1: Identity and Access Management
The first step is to identify the assets and instances of data stores, applications, and the data itself. Assets on the public cloud are categorized under in-house environments. In some cases, the situation can be less complex to inventory as AWS provides its visibility of the assets under the management.
Some of the major points to keep in mind during asset identification are:-
- Remove all keys for the root account
- Do not use the root account for any automation or daily task
- Implement 2FA authentication for the root
- Allow only limited permissions to the service accounts
- Allow the usage of only one key per user
- Ensure all users have only one active access key
- Change all ssh and PGP keys regularly
- Remove all unused security accounts
Step 2: Enable Logical Access Control
Once you have identified all the assets that are being managed, it’s time to manage the access control on the cloud.
Logical Access Control is the process of assigning what type of actions can be performed on the resource (read, write, execute, etc) and by whom. The major part of this step involves controlling access to AWS resources, users, and processes.
The access to the AWS resources can be controlled through the AWS account or individual Identify and Access Management (IAM) user accounts.
The major portion of this step focuses on identifying how users and permissions are set up for the service in AWS. It is essential to ensure that the management of the credentials associated with the AWS accounts is well-secured.
Step 3: Secure S3
In simple words, the S3 is essentially a cloud folder commonly called a “Bucket”. It is a storage server that supplies you robust such as region exceptions, versioning, access logging, encryption and access control.
The factors that determine the security of the S3 bucket are as follows:-
- Permissions for HTTP methods such as LIST, GET, PUT, DELETE, etc should only be allowed for specified users.
- The bucket should have versioning enabled.
- The bucket should have logging enabled.
Step 4: Optimize Database Services
The database is something that is used in most of the web services. Thus, it is crucial for you to make sure that your database follows the security standards. A single flaw in your service in the cloud can cause you a data breach.
The Amazon Relational Database Service (RDS) makes it easy to set up the database in just a few clicks. Additionally, consider keeping in mind the following key points during the AWS security audit:-
- Back up your data regularly.
- The backup retention time should be set to more than a week.
- Use of the Multi-AZ deployment method is recommended.
- Instance storage should have some encryption enabled.
- Allow access to only a few specified IP addresses.
- The Database snapshots should not be publicly accessible.
Step 5: Employ Vulnerability Scanners
Once you have finished securing your service in the cloud according to the security standards, running a vulnerability scanner is recommended. This will show you if you have any missing assets or CVE.
Popular vulnerability scanners such as CloudSploit can help you with the process.
Most hackers can gain access to your AWS instance by hiding themselves in unused regions to avoid detection. This is where CloudSploit can cover for you. It scans every public region of the AWS instance, including the ones you don’t actively use.
AWS Security Audit Provider – Astra
Astra is a cybersecurity company that provides protection and tests for security vulnerabilities in your Website and Infrastructure. Astra’s hacker-style security testing offers real-world attacks to the website and thus, ensures no security vulnerability is exploited in the wild.
We provide an in-depth AWS security audit under our VAPT program. VAPT by Astra includes a thorough audit of static code & dynamic code, business logic errors, payment security flaws, price manipulation testing, network misconfigurations, tests for known CVEs, insecure roles and permissions, and so much more.
From the time you sign up to the completion of the audit, it’s a smooth process and can be visualized in the following picture:
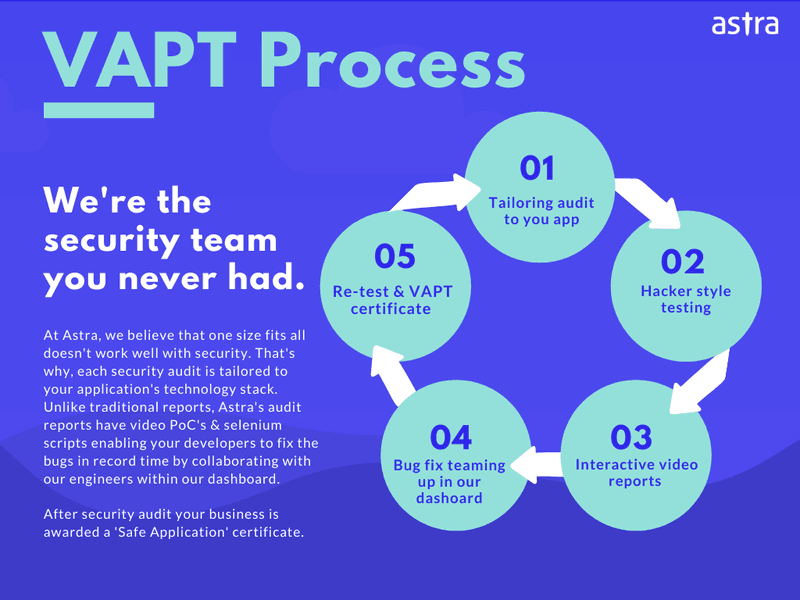
Moreover, the security expert team of Astra makes sure that no damage is made to the website or your infrastructure during the audit. Astra also ensures that no security bug or vulnerability in your website goes unseen.
Further, with our collaborative VAPT dashboard, you can see vulnerabilities reported live and communicate directly with the security expert working on the audit.
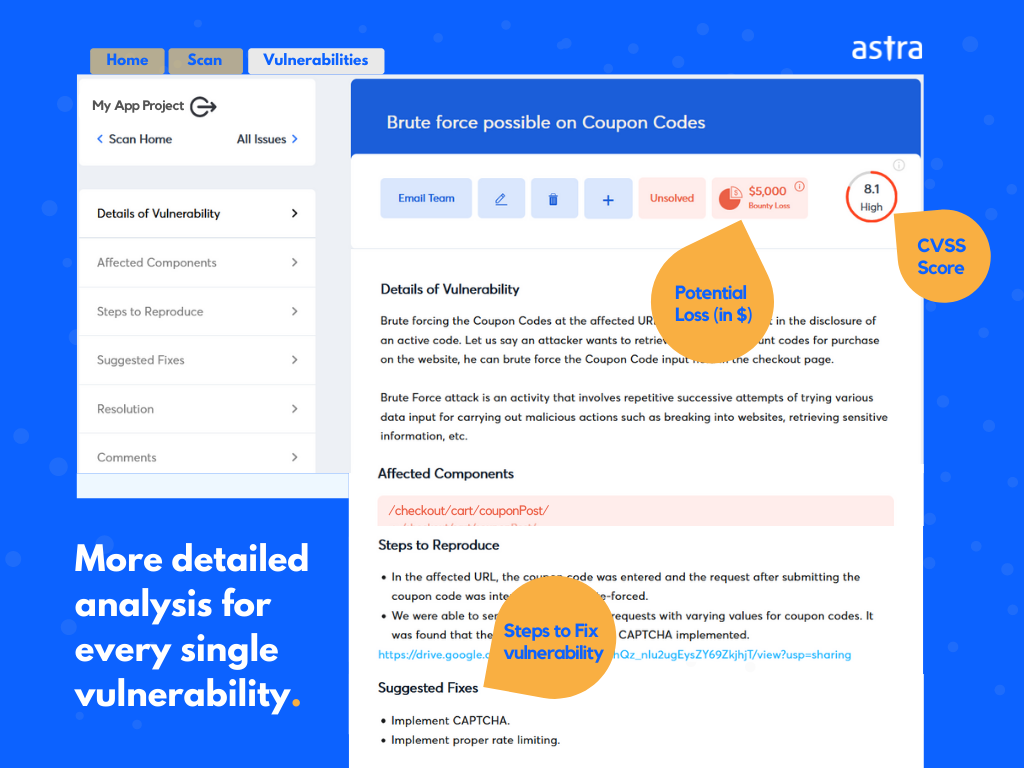
Our experts not only report the vulnerabilities but also provide remediation methods to fix them. Not only this, Astra engineers are known to go the extra mile, so they also assist you/your developer in patching the vulnerabilities and are quick to do a re-scan for you to ensure everything is in place.
Our round-the-clock AI-powered chatbots and human support help us provide you with end-to-end security services.
Conclusion
AWS offers various security measures for the security of the cloud. However, the security in the cloud depends entirely on you. Therefore, performing an AWS security audit becomes important for your business. The sooner you know your security vulnerabilities the sooner you can fix it and protect your website from hackers.

FAQs
How do I conduct an AWS audit?
To conduct an AWS audit, start by reviewing your AWS configurations, permissions, and access controls. Use AWS tools like AWS Config and IAM to assess compliance with best practices, identify vulnerabilities, and monitor for suspicious activities. Collaborate with security experts and leverage third-party auditing tools for a comprehensive evaluation of your cloud.
Which AWS service is used for auditing?
The AWS service used for auditing is AWS Audit Manager. It is a cloud-based audit service that helps you automate the collection and analysis of audit evidence to meet your compliance requirements. AWS Audit Manager provides pre-built and custom audit frameworks that you can use to assess your AWS environment against a variety of standards
















