AWS cloud security controls are measures doled out by the cloud service provider to keep their infrastructure and their client data safe and secure from harm’s way. Deploying AWS security best practices for cloud and tools help organisations and the service provider stay compliant with a host of security standards, as well as keep their security measures up to date.
This article will detail the risks faced by AWS, the best practices and tools for well-rounded security.
What Is AWS Cloud Security?
AWS Cloud Security is a feature offered by AWS to protect your applications along with the data stored and transmitted by it. AWS makes use of the shared responsibility model for security. This means that security for the cloud infrastructure is managed by AWS while the customers are responsible for their own applications and data.
Why is AWS Security important?
AWS cloud security is important because:
- AWS cloud security helps you comply with the shared responsibility model, which means that AWS manages the security of the cloud infrastructure, while you are responsible for the security of your workloads and data.
- AWS cloud security provides you with a range of services and features, such as encryption, key management, identity and access management, detection and response, network and application protection, and compliance, to help you implement your organisation’s security policies.
- It enables you to enhance your security posture and streamline your security operations across your entire AWS environment by continuously identifying and prioritizing security risks.
- It also allows you to move fast and stay secure by confidently integrating and automating security into every part of your organisation. By automating this, you can spend your time on the highest value tasks, reduce human error, and scale security best practices across the organisation.
- It gives you a comprehensive view of your compliance status and continuously monitors your environment using automated compliance checks.
How does AWS cloud security work?
AWS cloud security works by following the shared responsibility model, which means that AWS manages the security of the cloud infrastructure, while you are responsible for the security of your workloads and data. AWS provides you with a range of services and features to help you implement your organisation’s security policies, such as encryption, key management, identity and access management, detection and response, network and application protection, and compliance. The shared responsibility model can help relieve the your operational burden as AWS operates, manages and controls the components from the host operating system and virtualisation layer down to the physical security of the facilities in which the service operates.
You assumes responsibility and management of the guest operating system (including updates and security patches), other associated application software as well as the configuration of the AWS provided security group firewall. You should carefully consider the services they choose as their responsibilities vary depending on the services used, the integration of those services into their IT environment, and applicable laws and regulation. The nature of this shared responsibility also provides the flexibility and customer control that permits the deployment.
AWS Cloud Security Best Practices
AWS cloud security best practices are those steps that enhance the available security within the AWS cloud when taken. These solutions include:
1. Cloud Security Controls
Place critical importance on implementing good AWS cloud controls to enforce good security strategies. Cloud security controls vital to security within the platform include identity and access management, multi-factor authentication measures, and regular changes to access keys.
It is also important to place strong passwords that have varying cases and characters along with continuously reviewing the access keys and passwords.
2. Data Encryption
Encryption is quite important to keep data that is stored and transmitted in the cloud secure from malicious attacks. It is also a security mandate for some regulatory standards without which there would be an issue of non-compliance.
AWS offers a key management service (KMS) that gives one centralized control over the encryption keys in place. Having data encryption in place ensures that there is an effective security barrier in place against attackers.
Also Read: A Complete Guide to Cloud Security Testing
3. Data Backup
This is yet another important feature to make use of since if any unmitigated disaster or breach occurs, organizations can get up and running again with a short recovery period owing to the data backups in place.
AWS Backup is an easy automated way to back up and secures your data from unforeseeable acts that could be natural or manmade. Adding multi-factor authentication to this system will enhance security by limiting the number of individuals who can access and modify the data stored.
4. Native Cloud Security
Opt for cloud-based security solutions rather than traditional solutions for security since they aren’t entirely equipped to deal with a cloud model. When choosing an AWS security solution for your organization’s data and application, ensure that they can be integrated into your organization’s development pipeline seamlessly.
They should also have experience providing security solutions to cloud-based organizations such as yours and should be able to detect external threats and vulnerabilities to the applications and sensitive information on the cloud.
5. Secure Access
Securing access to your organization’s applications and data with AWS security in the cloud is crucial to maintaining safety. This can be done by implementing authentication and authorization measures such as multifaceted authentication and implementing role-based access control.
Making use of strong passwords which should be changed often and, deleting access for inactive accounts are other measures that can help secure access to confidential data within the cloud environment.
6. AWS Compliance
Make use of AWS compliance programs to better understand the controls available for AWS security in the cloud to maintain security and compliance. Tools by Amazon like AWS Artifact can help in checking for the compliances your company needs to be compliant and check for areas that don’t meet compliance for the resolution.
7. IR Plan
Place an elaborate threat and incident response plan so that in the case of emergencies, no time is lost in placing the backup processes and workflows that were planned out well in advance. This ensures that fewer systems and workflows are impacted with far less collateral damage than a company without a good incident response plan would face.
8. Continuous Monitoring
Continuously monitoring one’s AWS cloud assets can ensure the quick detection of any new vulnerabilities or risks that can result in a breach or theft. Such vulnerabilities can then be patched immediately to safeguard the AWS infrastructure thus drastically reducing the chances of a successful attack.
Also Read: Top 5 Cloud Vulnerability Scanners & Choosing the Right One
6 AWS Cloud Security Mistakes To Avoid
Every cloud service security out there, including the AWS cloud security, is occasionally plagued by certain forms of risks. Such areas of vulnerability can affect its performance and holistic security. Some of the top AWS cloud security risks have been explained further to help better understand the threat they pose.
1. Poor Identity and Access Management
Identity and access management refer to the efficient management of individuals who can access certain data and those who can’t. This is done by granting authorization and then access to specific individuals.
However, in some cases, poor IAM can lead to the wrong individuals being granted access to sensitive information. This is where proper authorization and authentication play a crucial role since they can help prevent unauthorized access.
This is especially concerning when access is still available to previous and inactive employees. Lack of role-based access is yet another reason for such a risk to arise.
2. Understanding Liability
AWS has a shared responsibility model. This means that the security of the AWS platform is covered by AWS but the responsibility for securing the applications and data falls on the customer organizations themselves.
Understanding this concept is crucial in having a clear-cut understanding of who the liability falls under in case there’s a mishap in security procedures that lead to a data breach. Users have to deal with access control, login monitoring and more as this falls under the domain of their application and data’s safety.
3. Improper Data Encryption
AWS provides its customers with an easy and cost-effective way to store their data through S3 buckets which are formally known as Simple Storage Service. Customers can create these buckets from any point in the world and store their data in them.
However, the issue lies in the fact that these private buckets of information can easily be made public by anyone who has an AWS account. This can lead to huge amounts of data being lost or stolen for personal gain.
4. Non- Compliance
Non-compliance is a major issue that can lead to heft penalties and even criminal charges. Compliance with specific regulatory standards is compulsory for organizations in every sector.
Compliances like HIPAA, PCI-DSS, SOC2, ISO 27001, and GDPR ensure that the best security measures are followed by companies in various industries according to global standards. Non-compliance with such standards means that the organizations aren’t reliable and don’t follow the highest standards of data protection and security.
5. AMIs Made Public
AMIs are Amazon Machine Images that contain all the information required to start a cloud-based storage system. This can include operating systems, data from applications, and more.
AWS accounts can be accessed and shared making AMIs an extremely vulnerable component of a company’s cloud presence. Such an accident could mean a company’s entire online operational infrastructure could be revealed, making this a costly vulnerability.
You may like to read: Cloud Penetration Testing: A Complete Guide | 5 Best Cloud Security Companies: Features Offered And Factors To Consider
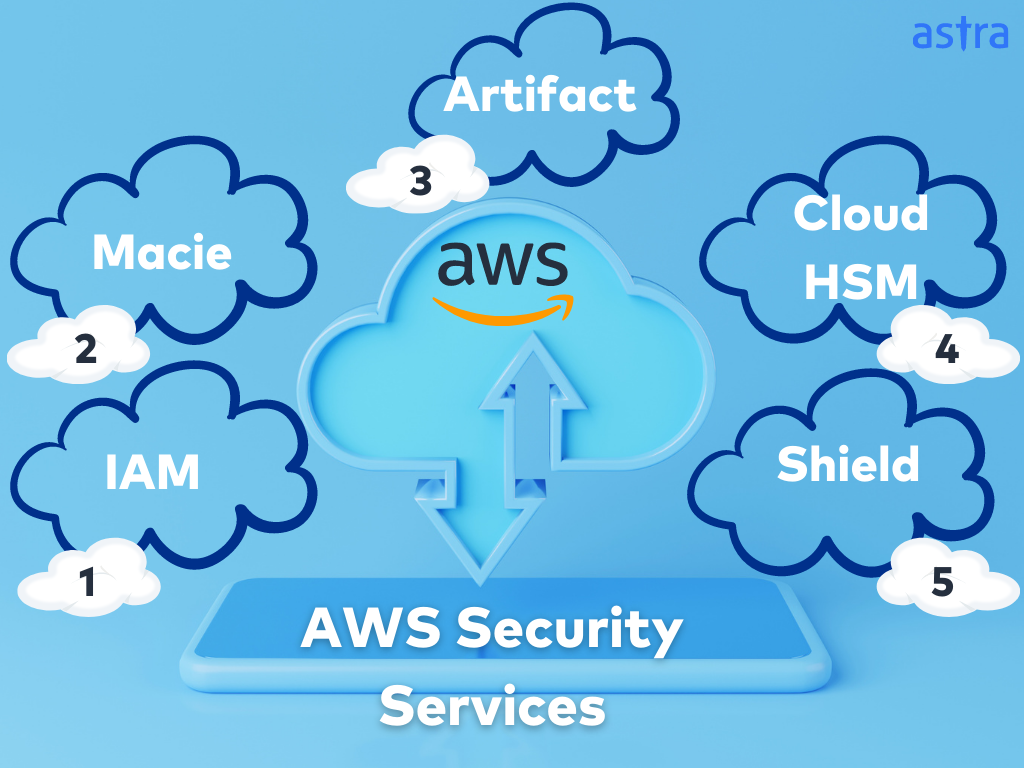
Important AWS Cloud Security Services
This section lists some of the important security services provided by AWS to help customers analyze various aspects of their cloud usage. They include:
1. AWS Identity And Access Management
This service allows one to define and set parameters for access with specific credentials, and to scale the privileges as and when required. It allows you to fine-tune the access and authorization allowing you to decide which individuals, groups, or roles can access certain information.
The features offered by AWS IAM include
- AWS Single Sign-On
- Manage permissions for single accounts
- Manage single account roles
2. AWS Macie
AWS Macie is a data protection service offered by AWS to customers. It makes use of machine learning, evaluations, and pattern recognition to identify the sensitive data in your S3 bucket and its accessibility.
Macie can easily detect changes to a bucket, as well as detect multiple larges files of data including personal information like PII and PHI. It also functions to scan and evaluate one’s S3 environment for security purposes.
Also Read: How to Conduct a Cloud Security Assessment: A 5-Step Process
3. AWS Artifact
AWS Artifact helps customers maintain compliance with data privacy and protection standards in place to ensure the safety of sensitive data stored on the cloud. The service helps you understand what sort of regulatory standards are applicable to the data stored by you and provides reports on how to maintain compliance with them. Reports are generally available for SOC, PCI-DSS, GDPR, and more.
4. AWS CloudHSM
CloudHSM (Hardware Security Module) provided by AWS is a hardware security service that aims to provide easy generation of encryption keys for use on the AWS cloud platform.
It also allows you to shift your encryption keys to other commercial, standards-compliant HSMs if the configurations set by you allow it. It automates time-taking tasks like hardware provisioning, patching, and availabilities.
5. AWS Shield
AWS Shield is one of the AWS security services that provide protection to the infrastructure such as network connections. It provides protection against DDoS attacks thus securing the applications running on the AWS cloud.
AWS Shield is of two types: Standard and Advanced. Standard Shield protects against basic threats like common network DDoS attacks. Advanced Shield goes above and beyond the standard services by also providing identification and prevention of large-scale DDoS attacks, integration, and closely monitored visibility of attacks.
Related Read: AWS Penetration Testing: A DIY Guide for Beginners
Best AWS Cloud Security Tools
| S. No. | Features | Astra Security | Prowler | ScoutSuite |
|---|---|---|---|---|
| 1. | Availability | Paid | Open-source | Open-source and Paid |
| 2. | Cloud Platforms | AWS, GCP and Azure | AWS | AWS, GCP, Azure and Oracle |
| 3. | Services | Vulnerability Scanning and Pentesting | AWS Security Assessment and Auditing | Security Auditing |
1. Astra Security
This commercial tool can carry out compliance and vulnerability scans comprehensively listing out the areas that are non-compliant or vulnerable according to their CVSS scores for quick remediation.
Automated vulnerability scans
Astra’s vulnerability scanner is capable of conducting more than 3000 tests to detect vulnerabilities that matched an extensive vulnerability database which includes OWASP Top Ten, SANS 25, known CVEs, and more.
Easy compliance checks
Continuous compliance scans ensure that compliance is maintained with industry-specific standards like HIPAA, PCI-DSS, GDPR, and SOC 2.
Intuitive Dashboard
Astra Pentest dashboard is unique in that it is entirely CXO-friendly and allows seamless collaboration between team members and pentesters for easy vulnerability fixing.
Manual Pentest
Astra’s comprehensive manual pentest can detect business logic errors, and conduct scans behind logins.
Zero False Positives
Astra’s Pentest team assures zero false positives in the report through thorough vetting after the automated scans.
Actionable Reports
It provides extensively detailed reports as well POC videos to help organizations patch the vulnerabilities found quickly.
Gap Analysis
Astra also conducts a gap analysis of an organization’s security systems to find the gaps in security and performance that can be improved on.
Publicly Verifiable Certificate
Provision of publicly verifiable certificate upon completion of security analysis and remediation which enhances the company’s reliability and trustworthiness.
Also Read: Cloud Security Scanner: Top Features, & the Best Solution
2. Prowler
Prowler is open-source third-party software known for assessing the AWS cloud security best practices and defenses. This audit tool has a great compliance and configuration scanner which focuses on areas like networking and identity management whilst checking for compliance statuses with regulatory standards like HIPAA and GDPR.
3. ScoutSuite
Similar to Prowler, this well-capable auditing tool provides security posture assessment for not just AWS cloud services but also for platforms like GCP, and Azure as well. It works by aggregating all data automatically and carrying out an audit based on a decided set of rules.
Conclusion
This article has given a detailed view of what AWS security of the cloud looks like, the most common risks that threaten an AWS environment as well as the important security services provided by AWS. Aside from increasing awareness of AWS risks and services, the article also scopes out the best practices to conduct for enhanced AWS security. Lastly, it mentions some great tools for you to use and keep your organization safe from harm in the cloud.
FAQs
How to implement security in AWS?
Security in AWS can be implemented by following these measures:
1. Securing access through MFA and strong passwords.
2. Having regular data backups and strong data encryption in place.
How secure is AWS?
AWS cloud services comply with most of the regulatory standards around the globe including HIPAA, NIST, GDPR, and PCI-DSS.
What are the risks associated with AWS?
The most common risks associated with AWS are improper understanding of liability, weak IAM, and data encryption.
















