HIPAA Penetration testing refers to the scanning and exploitation of security system that needs to be HIPAA compliant to find any hidden vulnerabilities and risks. Doing HIPAA penetration testing helps organizations fix the areas of vulnerabilities found, thus maintaining compliance and avoiding hefty fines.
According to the Health Insurance Portability and Accountability Act (HIPAA), companies are required to carry out continued risk analysis through the means of penetration tests or vulnerability assessments which can be decided by the company.
Health Insurance Portability and Accountability Act is a regulatory standard set to protect people covered by health insurance and makes rules regarding the protection of personal health information storage.
HIPAA compliance is a must-have for any company, organization, hospital, or pharmaceutical as they make use of and store the confidential health information of scores of people.
This article will elucidate more on the HIPAA penetration testing requirements, steps, factors in choosing the right team, and finally the healthy solution for all your HIPAA compliance requirements.
HIPAA Penetration Testing Requirements
This section details the HIPAA penetration testing requirements that every healthcare organization needs to meet –
1. Risk Analysis
Risk analysis is the process of scanning and or analyzing an organization’s security system to identify vulnerabilities that could cause potential damage to the sensitive data stored by that organization. This can range from confidential patient health information to various results from tests.
HIPAA compliance requires risk analysis to be done continuously in order to ensure constant high-level protection from threats that look to access and exploit personal healthcare information.
However, it does not mention a specific type of risk analysis which leaves the decision of choosing between penetration tests and vulnerability assessments to the organization itself.
Regular HIPAA penetration tests are the best solution for this when compared to vulnerability assessments as they are more comprehensive and in-depth. This is because it scans for vulnerabilities and exploits the found vulnerabilities to assess the enormity of a potential hack using that vulnerability.
Penetration testing is applicable under HIPAA’s most important privacy rule as it helps determine the pathways that could be opted by hackers to gain access to protected health information (PHI).
2. Vulnerability Fixing
HIPAA compliance requires that once the risk assessment like healthcare penetration testing or vulnerability assessment is successfully completed, proper steps to remediate the vulnerabilities and areas of non-compliance be taken as soon as possible.
Not doing so can leave the security system exposed and vulnerable to a host of threats like a data breach, deletion, or theft. Once the HIPAA compliance penetration testing is done, a detailed report is generated that mentions the scope of testing, rules of engagement, and a list of vulnerabilities found with an executive summary.
The vulnerabilities listed will also have all their information including actionable risk scores for prioritization and remediation measures which can help in the immediate fixing of vulnerabilities.
3. Continuous Scanning
In order to maintain compliance and or achieve HIPAA compliance, continuous monitoring, scanning, and conducting HIPAA compliance penetration testing is a must to identify any new vulnerabilities that pose a threat to an organization’s online security.
The tools opted for HIPAA penetration testing must be fully integrated with the security system in order to provide automated continuous monitoring. It should also ensure that there will not be any false positives which could lead to unnecessary expenditure of resources like manpower, time, and expense.
Steps In HIPAA Penetration Testing
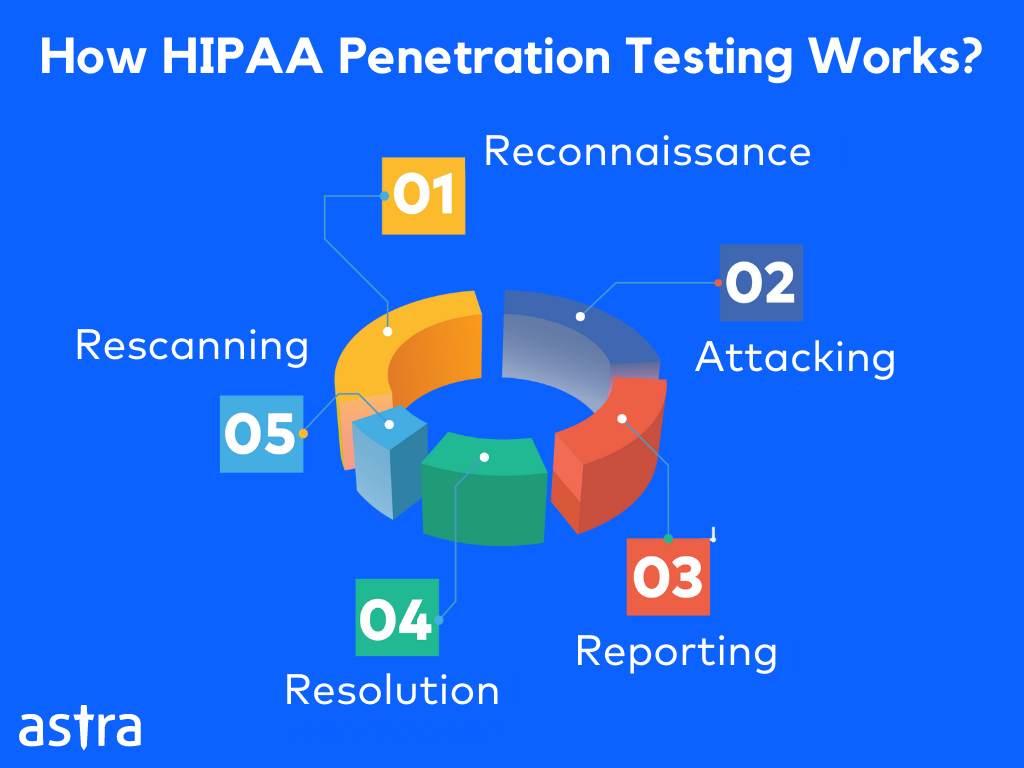
1. Reconnaissance
Reconnaissance refers to the researching phase of the pentest where the pentesting teams aim to find all the information they can about the target that is publicly available. This is done after scoping where all the assets are to be tested, and the reasons and the limits are discussed so as to avoid any legal troubles and scope creeps.
There are two types of reconnaissance, active and passive reconnaissance:
- Active reconnaissance refers to finding information about the target through thorough interaction with it. This type of surveillance requires prior permission from the target.
- Passive reconnaissance refers to finding information without any interaction from the actual target but through online resources that are publicly available like websites for example.
2. Attacking
This is the phase where the information from the reconnaissance is scanned and tested to find different vulnerabilities which are identified based on a vulnerability database of known CVEs, as well from OWASP Top 10 and SANs 25.
Vulnerabilities can also be found using an automated comprehensive vulnerability scanner the results of which can be vetted with a manual pentest to avoid any false positives.
3. Reporting
Once the penetration testing is done a detailed report is generated with an executive summary. It also includes information on the scope of the test, rules of engagement, methods employed, and lastly, a list of the vulnerabilities found.
Each vulnerability is explained in detail with its CVSS scores, its impact on the security system, and actionable risk scores for prioritization and remediation measures. Some companies offer additional assistance through POC videos and customer assistance.
4. Resolution
Once the target organization obtains the detailed report upon the scan completion of its assets and its security, it is used to rectify and remedy the vulnerabilities found. This helps avoid any breaches and threats to security.
5. Rescanning
This is the last step in the pentesting procedure to safeguard the fixes made to the security of an organization’s assets. The security system is rescanned once the fixes are made to find any additional or new vulnerabilities that could have arisen from the patching.
Once this step is complete and zero vulnerabilities have been detected, the organization’s online security can be said to be completely safe.
Choosing The Right HIPAA Pentesting Team- Factors
1. Reputation
Ensure that the company you opt for to achieve your HIPAA penetration testing requirements has a good reputation and experience within the field. This can be vetted with the help of reviews and comparisons available online as well as through interaction with existing or previous customers to know their thoughts.
2. Certifications
Ensure that the compliance penetration testing provider opted by you is compliant with all the standard regulations and rules that they need to follow. Also, make sure that pentesters within the company also have the right experience and certifications that can make your pentesting and compliance journey a breeze.
3. Detailed Reporting
Make sure that the reports provided by the pentesting company are detailed and with easy-to-follow steps as well as POC videos to help ease the remediation process. Added bonus is they provide a feature of collaboration between the pentesters and the development team.
4. Budget
Make sure that the pentest services you opt for are well within your budget and have options to customize and tailor the penetration test to your specific requirements.
The Healthy Solution – Astra Pentest
1. Compliance-Specific Scans
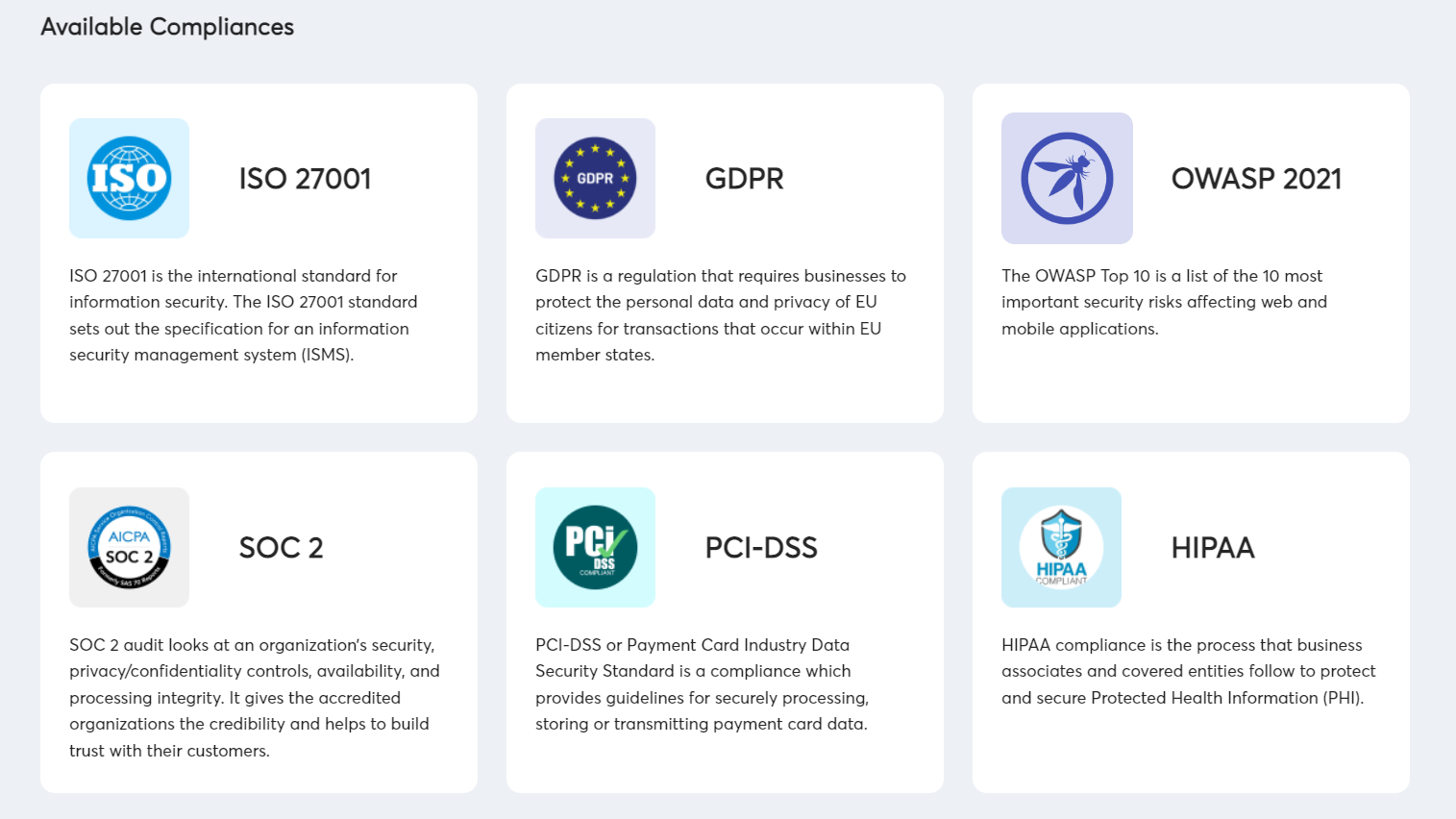
Astra provides compliance-specific scans with its very own dashboard and personalized compliance reports. This is available for various regulatory standards like HIPAA, GDPR, PCI-DSS, SOC 2, and ISO 27001.
Customers can choose the compliance they want to scan for, once the scans begin, vulnerabilities and areas of non-compliance detected are displayed on the dashboard in real-time with all the information regarding it as well as steps to achieve that area of compliance.
2. Continuous Penetration Testing
Astra is capable of providing continuous pentests to assess an organization’s security posture on a regular basis. Based on the initial scope and the needs of the target organization, Astra deploys its automated scanner or enlists its own pentesting team to find the security flaws of the organization.
3. Comprehensive Vulnerability Scanner
Astra’s automated scanner is capable of conducting more than 3000 tests to find hidden vulnerabilities. It can also carry out scans behind logins, as well as detect any business logic errors that may be affecting an organization’s revenue.
This extensive vulnerability scanner can detect vulnerabilities based on known CVEs, OWASP Top 10, and SANs 25 and is constantly updated to find newer vulnerabilities. It follows various frameworks like NIST and OWASP to ensure smooth scans for its customers.
4. Penetration Testing Certificate
Astra goes a step further compared to all other pentesting providers by providing the customers with a pentest certificate upon the completion of a successful pentest, followed by resolution of found vulnerabilities, and lastly, a rescan to ensure that there are no new vulnerabilities.
This certificate is publicly verifiable and can be put on one’s website to boost sales and promote a security-conscious approach.
5. Detailed Report
Detailed reports given out by Astra are truly helpful for organizations in terms of remediation and documentation. It gives a detailed account of the scope, engagement rules, and methodologies.
But most importantly, it lists out the vulnerabilities found with a dedicated section for each vulnerability explaining their CVSS scores, actionable risk values to indicate which vulnerabilities are critical, information found through exploitation, its impact on the security system, and remediation measures to patch it.
6. 24*7 Customer Support
Astra boasts 24*7 customer support through email, chats, and even calls if necessary with the help of the expert pentesters on the team. The dashboard also provides a comment option for each vulnerability for immediate doubt clearance.
Conclusion
With compliance becoming a norm to adhere with drastic effects of non-compliance ranging from hefty fines to penalties and even criminal charges, it is no wonder compliance-based pentesting is gaining popularity.
HIPAA penetration testing is set to address and find the areas of non-compliance within any healthcare organization to safeguard it from threats and risks associated with vulnerabilities and non-compliance.
Astra’s Pentest is truly the one-stop destination for all your HIPAA penetration testing requirements with its compliance-specific scans, dashboard, and compliance reporting. Ensure the health of your organization today by teaming up with Astra!
FAQs
Is pentesting compulsory for HIPAA compliance?
According to HIPAA, organizations need to do risk analyses regularly to avoid and or identify and rectify any areas of non-compliance. This can be done with either penetration tests or vulnerability assessments.
What is the purpose of HIPAA?
The Health Insurance Portability and Accountability Act is designed to protect people covered by health insurance and also to secure their protected health information from any breaches and or theft.
What is protected by HIPAA’s Privacy rule?
HIPAA’s privacy rule protects all protected health information stored or transmitted through electronic, media, or paper.
















