NIST stands for the National Institute of Standards and Technology. NIST is a non-regulatory agency of the US Department of Commerce with a mission to promote industrial innovation and industrial competitiveness.
NIST has a long-standing tradition of working with industry. The relationship between NIST and industry is a partnership – a partnership that is based on a mutual commitment to serve the public interest.
Importance of NIST Security Audit
NIST security audit plays a major role in protecting the nation’s critical information systems. The agency provides the security standards that government agencies, private companies, and other organizations rely on to protect their IT systems.
The NIST has released the NIST Cybersecurity Framework (CSF), which provides a way for organizations to evaluate their cybersecurity capabilities. The CSF is the first step to improving security at the agency level, which will lead to improvements in cybersecurity throughout the nation.
Here are some benefits of performing a NIST security audit:
1) Keeping the customer’s data safe and secure from cyber-attacks
2) Having an edge over the market with a better reputation and customer trust.
3) Protecting company data and network
4) Getting in line for government projects or contracts.
5) Saving the data breach cost
We’ve termed NCF but what exactly is that? Let’s understand the NIST cybersecurity framework(NCF)
What is the NIST cybersecurity framework?
The National Institute of Standards and Technologies Cyber Security Framework (NIST CSF) is a set of standards to help companies improve their overall cybersecurity posture.
The NIST Cybersecurity Framework is a voluntary set of standards, developed by the National Institute of Standards and Technology (NIST), for improving an organization’s overall cybersecurity posture.
NIST cybersecurity framework helps to identify the various cyber risks that may cause harm to your company’s infrastructure and data. With these guidelines, companies can set up plans to identify, manage, and monitor their risks in a more comprehensive manner. The framework also helps to identify different control mechanisms that can be implemented to mitigate these risks.
The NIST cybersecurity framework is designed to identify and reduce cyber risks across critical infrastructure sectors, including those that are not covered by existing regulations such as the Health Insurance Portability and Accountability Act (HIPAA) and Payment Card Industry Data Security Standard (PCI DSS). The framework is to be used as a voluntary and collaborative tool and applies to all organizations and industries.
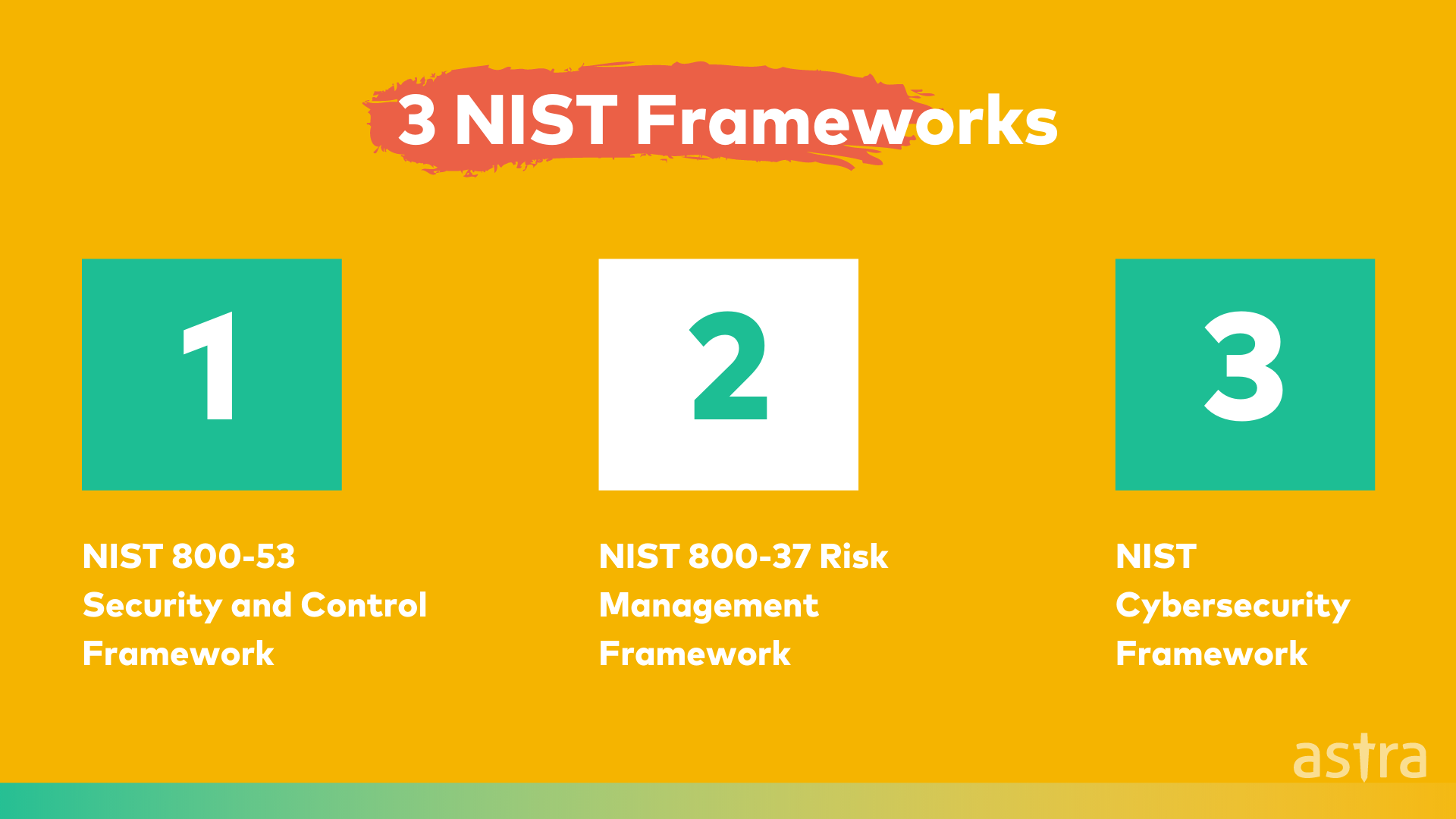
Understanding 3 NIST Frameworks
1) NIST 800-53 Security and Control Framework
The NIST 800-53 security control framework is a set of information security controls used to evaluate the effectiveness of security controls in protecting the confidentiality, integrity, and availability of federal information systems.
The NIST 800-53 security control framework can be used as a template for implementing security controls, as a checklist against which to measure security controls, as a baseline for continuous monitoring activities, as a set of required security controls, or as a basis for tailoring.
2) NIST 800-37 Risk Management Framework
The NIST 800-37 Risk Management Framework is a step-by-step process for assessing risk and implementing countermeasures to reduce risk to an acceptable level. The NIST 800-37 Risk Management Framework is applicable to all organizations, regardless of size, type, or complexity.
The NIST 800-37 is a standard that is used in the federal government to ensure that they are compliant with security standards. This process is a great way for any organization to manage the risk of their information system.
3) NIST Cybersecurity Framework
The National Institute of Standards and Technology (NIST) released the NIST Cybersecurity Framework to help organizations manage cybersecurity risks. The Framework is a set of standards and best practices that organizations can use as they develop strategies for managing cybersecurity risk.
Organizations that use the Framework can develop and implement an effective cybersecurity risk management program that enables the organization to protect its operations and assets; satisfy its missions and business functions, and manage cybersecurity risk effectively.
Role of Vulnerability Assessment in NIST Security Audit
NIST (National Institute of Standards and Technology) is one of the leading government agencies that are responsible for providing comprehensive information security standards. According to the NIST, vulnerability scanning of systems and devices needs to be conducted to ensure that systems are safe and secure.
The National Institute of Standards and Technology (NIST) has identified the importance of vulnerability assessment as a key component of Information Security Audit. Information systems can be vulnerable to a number of threats, including viruses, intrusions, improper configurations, misuses, malicious software, or accidental loss of data, vulnerability assessment is required.
Organizations are responsible for assessing the security of their IT systems on a regular basis. It is important to have a vulnerability assessment program in place so organizations can identify weaknesses in their security.
A vulnerability assessment is a way to evaluate the security of a system, network, or application. Vulnerability assessments are commonly used to determine what security controls are in place to protect the system or application. They are also used to measure the level of risk associated with the system, network, or application.
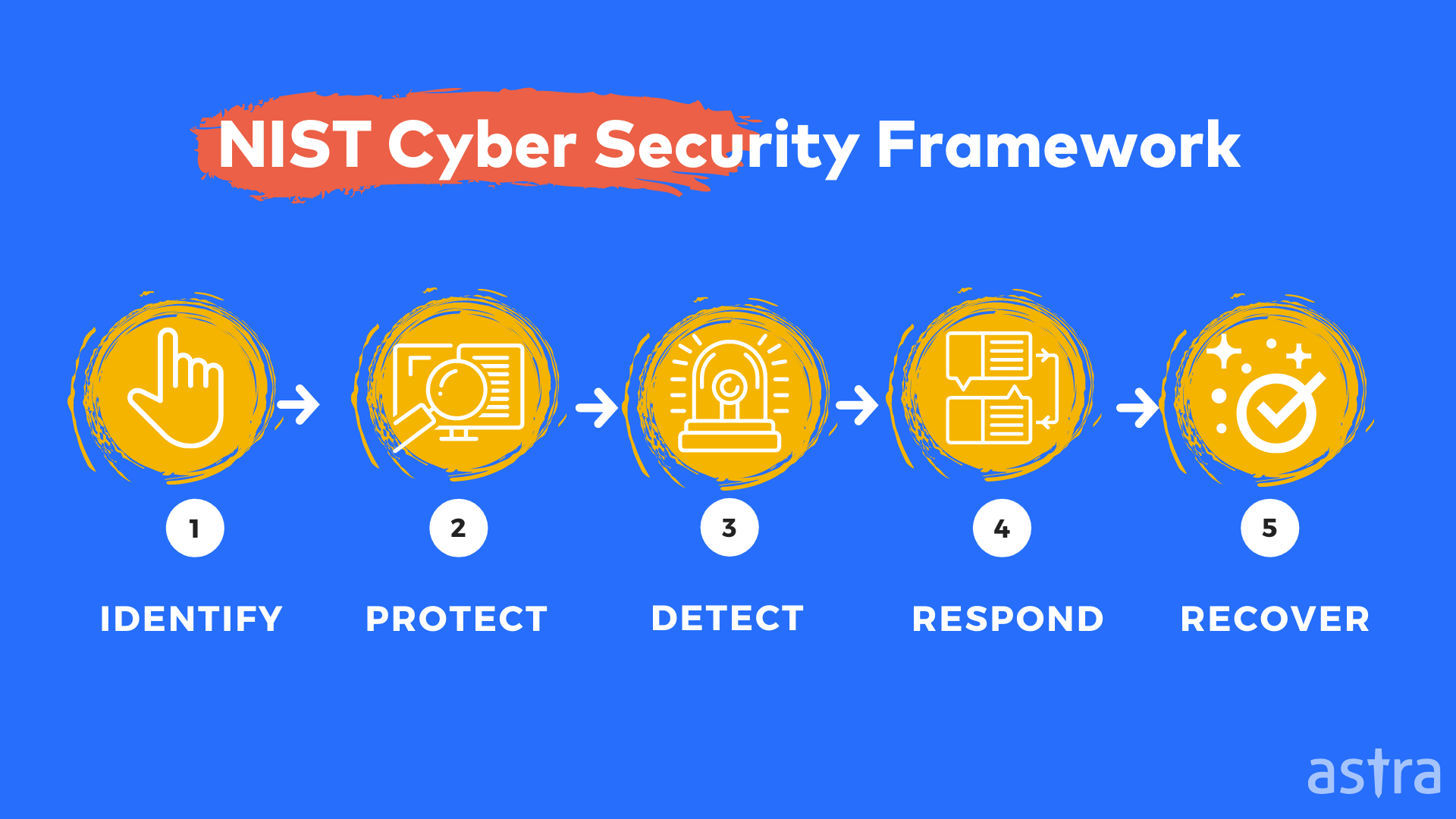
5 Functions of the NIST Cybersecurity Framework (NIST CSF)?
The NIST Cybersecurity Framework (CSF) was released in 2014 by the Department of Commerce’s National Institute of Standards and Technology (NIST).
The framework describes five functions that are core elements of an organization’s cybersecurity program. Each function consists of categories that comprise 23 subcategories listing requirements and controls.
The five functions are:
1. Identify
2. Protect
3. Detect
4. Respond
5. Recover
The CSF’s core includes the five functions described above and the key categories and subcategories. Each function has its own set of implementation tiers, which describe how to organize and report on the categories and subcategories. Profiles and tailoring guidance provide support for implementing the CSF. Profiles are tailored to specific sectors, organizations, or domains.
For the individual or agency that is new to cybersecurity, the framework serves as a guideline to provide a better understanding of cybersecurity risks, along with potential solutions. The framework is also what many organizations will use to create a holistic cybersecurity program. The framework is sorted into three levels of increasing rigor: pillars, objectives, and functions.
Astra’s Compliance Friendly Pentest [NIST Security Audit]
Compliance is a necessity for most companies. Whether it is to stay in good graces with the government, maintain a healthy reputation, or just to prove that you are doing what you can to protect your customers, meeting compliance standards is vital.
When it comes to penetration testing or vulnerability scanning, penetration testing should be compliant with all the security standards. To get the best penetration testing services, you need to search for the best company offering the same. Astra is a renowned company that provides reliable pentest services. At Astra, the pentest services are always compliant with all kinds of audits including the NIST. Astra offers a comprehensive security audit based on the NIST frameworks.
Benefits of using Astra’s Compliance Friendly Pentest:
- Automated Scanner with more than 8000+ tests to keep your application safe.
- Manual scanning along with a scanner to make sure no security risk is left.
- Easy, accessible reports that you can interpret at a glance with the dashboard.
- Get detailed steps on bug fixing tailored to your issues and know exactly how to reproduce vulnerabilities with video Proof of Concepts (PoCs).
- Why keep your security status private? Showcase Astra’s Publicly verifiable certificate.
- A post-penetration test, Astra shows a potential loss in $$$ for each vulnerability, making it easier for everyone to understand the impact.
- For each vulnerability, Astra gives an intelligently calculated risk score.

Conclusion
Cyber attacks are becoming a bigger threat every day, and a lot of the time, organizations don’t even know they’ve been compromised. NIST security audits are a great way for businesses to eliminate all the guesswork and prevent cyber attacks from happening in the first place. NIST security audits are a complex and time-consuming process but Astra is here to help. Get in touch with us and let us take care of your security.
FAQs
1. What is an NIST audit?
NIST stands for National Institute of Standards and Technology. It is a nonregulatory agency of the US Department of Commerce. NIST audit refers to a security audit that follows the compliance regulations formed by NIST.
2. What is the NIST CSF audit?
CSF stands for Cyber Security Framework created by NIST. A CSF audit helps businesses and agencies evaluate their cyber security capabilities.
















