An application security audit is a security service that assesses and tests the security of software. It is a collective term for various testing processes that examine the software for security vulnerabilities and weaknesses. This testing process can be outsourced or done in-house.
Application security audits aim to identify and classify risks and vulnerabilities in software to detect any security breaches that could result in a loss of information or damage to data.
Also Read: What is External Penetration Testing and How to Do It in 5 Easy Steps?
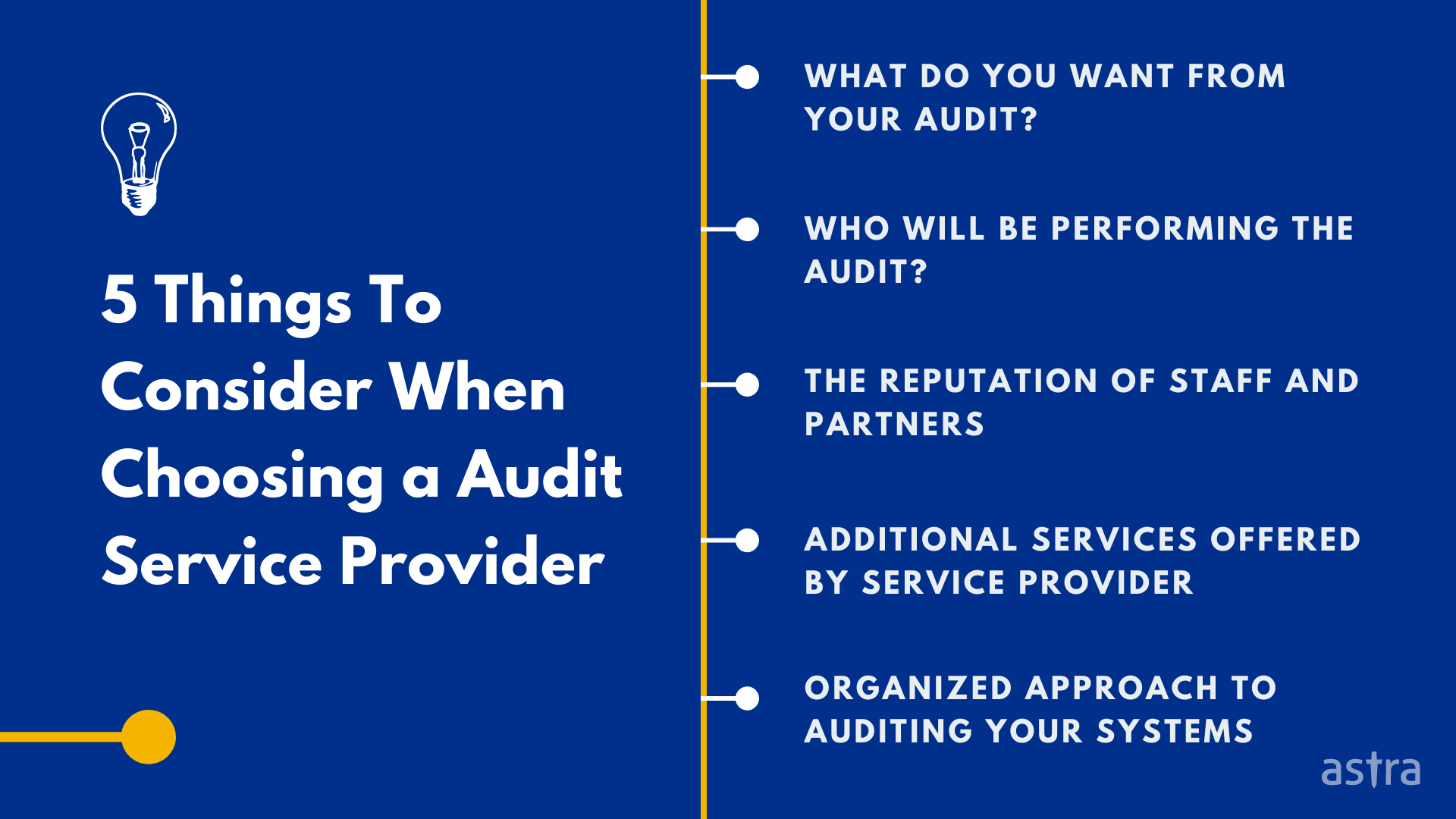
5 Things To Consider When Choosing An Application Security Audit Service
Any application security audit aims to find vulnerabilities in your application, document them, and then provide recommendations to help you fix them.
Hiring an application security audit service is critical to your application security program. It can be challenging to identify the right partner for your project. To help you with that, here are five things to consider when hiring an application security audit service provider.
1. What Do You Want From Your Audit?
Before you begin looking for an audit service, you need to ask yourself why you want one in the first place. Why do you want to audit your systems? What goals are you looking to achieve through this? While implementing an audit can be helpful in many ways, it also has specific uses. The most common type of audit is a compliance audit.
This is conducted to ensure that your systems are compliant with applicable regulations. Another type of audit is a security audit. This audit looks at the security posture of your systems — i.e., how strong the defenses are against the threats they are likely to face.
Why Astra is the best in pentesting?
- We’re the only company that combines automated & manual pentest to create a one-of-a-kind pentest platform
- Vetted scans ensure zero false positives
- Our intelligent vulnerability scanner emulates hacker behavior & evolves with every pentest
- Astra’s scanner helps you shift left by integrating with your CI/CD
- Our platform helps you uncover, manage & fix vulnerabilities in one place
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

2. Who Will Be Performing the Audit?
To properly evaluate an audit’s quality, you should get a good idea of who is performing it. Is it a third-party service provider? Is it one of your in-house staff?
Some audits are conducted by third-party auditors, while others are performed by one of your office’s staff. Regardless of who is conducting the audit, it’s important to note that the audit’s quality will depend on these auditors’ quality.
When choosing who will be conducting your audit, you also need to consider any time constraints they’re working under. What are their experience levels, what resources do they have available, etc.?
3. The Reputation of Staff and Partners
One of the most important things you can learn from a service provider/contractor is the reputation of their staff and partners. It’s essential to find a business consultant with a good reputation. Reputable auditing firms and third-party services will have a solid online presence.
You can use this to learn more about the auditors and their experience levels. If you don’t already have a list of top security auditing companies to cover, feel free to use this list.
4. Additional Services Offered by the Service Provider
Security service providers aren’t just auditors. They may offer a broad range of services, from infrastructure scanning to malware cleanup. It’s a good idea to ask your business consultants about any additional services they offer.
Do they have particular expertise that you can use? Are there any additional services you can use now but might benefit from being implemented in the future?
It can be helpful to learn more about the auditing services offered by your service provider. These services can be helpful in several ways. For example, they can help you with your compliance.
5. Organized Approach to Auditing Your Systems
To create a comprehensive plan to bring your application security up to par, it helps to consult with a service provider to understand how things will work.
They can provide several different perspectives and help you better view the entire picture. If your security auditors are working with your internal teams, it can help your teams understand how to improve their security posture.
It’s also helpful to meet with more than one service provider if you want to get a better idea of each security auditor’s approach. This can help you make an informed decision about which security auditors you want to work with.
Also Read: Security Audit Company and Services [Top rated]: How to Pick

Why is Application Security Audit Important?
The importance of application security audits (AST) is increasing rapidly nowadays due to the increasing number of cyber attacks and malware attacks. The application security audit guarantees high quality and efficiency in the application software.
The application security audit helps to detect the vulnerabilities that the hackers can exploit to steal the data or perform other malicious activities.
In addition, the application security audit helps to detect the risks of the business and helps the business improve its security posture.
3 Best Practices to Avoid Vulnerabilities
Security threats are ever-changing, and even the most reliable network can be vulnerable. It’s therefore essential to always be on the lookout for new threats and ensure that you comply with industry best practices for security.
Here are three things that can help you avoid security vulnerabilities on your website.
1. Never Rely on User Input
Some of the most common security vulnerabilities are in inputs such as search queries, registration forms, and comments. These inputs are often used in conjunction with SQL injection attacks and cross-site scripting. Both exploits un-validated user input and can be avoided by escaping malicious payloads and sanitizing the user input.
2. Use a Strong WAF
Web application firewalls (WAF) can significantly help fight against hackers and security vulnerabilities. A WAF can help you detect and prevent several vulnerabilities such as XSS, SQLi, DoS, and much more
3. Perform Regular Pentest/Audits
One of the best things you can do is to know how to perform regular security audits/pentests. For every website and application, you should perform a security audit regularly. It’s great to do if you want to improve your website.
Why Choose Astra for Application Security Audit Service?
Astra is one of the leading application security audit service providers, which has helped many companies to protect their business-critical applications.
Astra’s application security audit services help you audit applications critical to your business. Our dedicated team of application security experts will audit your application and provide you with a detailed report that will help you fix all the vulnerabilities and keep your applications secure.
Check out Astra’s Sample Report to know more.
Conclusion
Whether you are a start-up or a Fortune 500 company, application security testing (AST) is a fundamental part of the software development & QA processes. A single security hole can potentially lead to an entire system being compromised.
We hope this article has provided valuable information on application security testing. Please contact us if you have any questions or concerns on AST or are interested in learning more.
Thank you for reading, and we hope to hear from you soon!
FAQs
1. What is an application security audit?
Application security audit is the process of assessing the security of an application or system. It includes assessing the security of the code, applications, infrastructure, and data.
2. What are the types of application security audit?
Application security audits can be performed manually or using automated tools. Manual audits are usually conducted by security experts who manually review the code and architecture of the application. Automated audits are typically conducted using static analysis tools that analyze the code without executing it.
3. Why is application security audit essential?
Application security audits are an essential part of any organization’s security program. They help identify risks and vulnerabilities and recommend controls to mitigate them.