Android purpose-built application development is one of the most prominent choices for business owners and mobile app developers since Android is the world’s most popular mobile operating system.
Insecure Android applications pose a threat to the users’ privacy, security and lead to financial loss. With the increase in cyberattacks that target mobile applications, one of the best ways to improve the security of an android app is to perform android penetration testing.
This blog post will explain how vital android penetration is, how it helps companies be secure from hackers and cyber-criminals, and much more about android penetration testing in detail.
What is Android Penetration Testing?
Android penetration testing is a process of finding security vulnerabilities in an Android application by attacking it using various methods and tools. This systematic approach searches for weaknesses in an Android application, verifies its security and makes sure it abides by security policies.
The primary aim of android penetration testing is to find the vulnerabilities in the application and fix them before cybercriminals exploit the vulnerabilities. The security issues are mainly related to data theft, information leakage, etc. The android penetration testers generally do the android application penetration testing.
Why is Android Penetration Testing essential?
In today’s world, android apps are used for multiple reasons, such as mobile banking, shopping, sharing personal details, social networking, and entertainment. The android devices are prone to threats from various hacking techniques, such as buffer overflow, code injection, reverse engineering, malware, etc.
The identification and penetration testing of the vulnerabilities in the android applications to identify and resolve the weaknesses in the applications is referred to as Android penetration testing.
Some of the benefits of the android penetration testing are:
- Uncover security risks of android applications.
- Improve the efficiency of the application.
- Gaining customer trust
- Decrease cost of the data breach

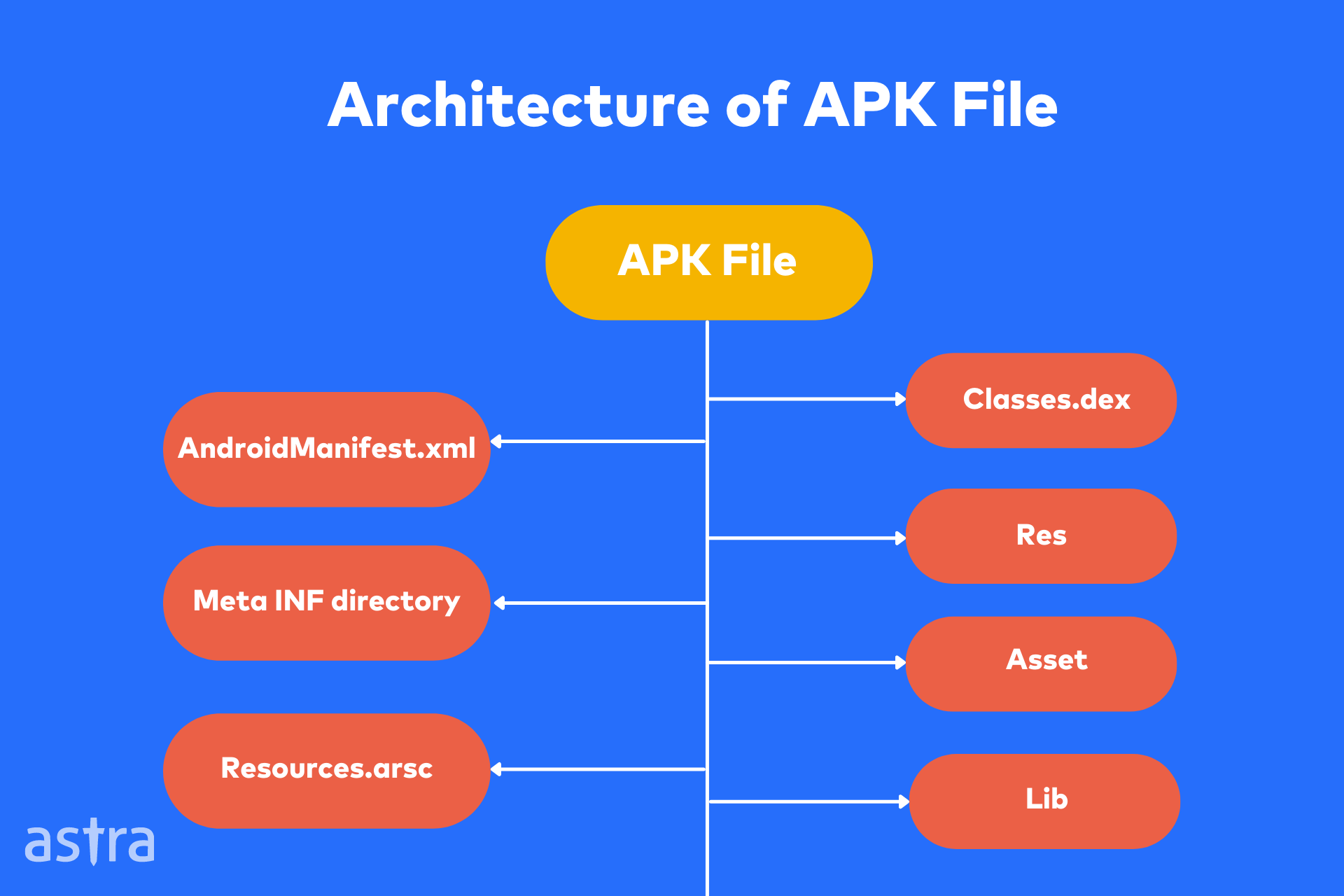
Understanding the Architecture of an Android App
An APK file is an archive file, and its primary use is to distribute the application’s binary files to the end-user. The APK file is a separate file from the Android operating system. Applications are installed on Android devices through the APK file, which is installed on the device’s system partition.
Check out the architecture of a decompiled APK file mentioned below:
What is OWASP Mobile Application Security Project?
The Open Web Application Security Project (OWASP) has been a global charitable organization working to make the web a safer place.
The OWASP Mobile Security Project includes a list of the top ten security risks that mobile applications face today. Each of the top ten mobile security risks is ranked by its threat level and further investigated. Let’s understand each one of these in detail.

M1: Improper Platform Usage
Improper Platform Usage involves the misuse of an operating system feature or a failure to use platform security controls properly. This is a risk that is very important to identify because it can have a significant impact on your data or devices.
This may include Android intents, platform permissions, the Keychain, or other security controls that are part of the platform.
- Vulnerability Impact: Impact can vary in severity resulting from manipulation of content within the application or even complete security compromise of the Android app.
- Prevention: The server side of the application must be well-equipped with the best coding practices like cryptographic encryption and good security configuration.
M2: Insecure Data Storage
Insecure data storage refers to the lack of sufficient security or the presence of security gaps within the Android application data storage.
Data of Android applications are stored in various locations like servers, mobile devices, and cloud storage. All of these locations are susceptible to attacks by hackers.
- Vulnerability Impact: Impact can vary from partial or complete loss of data to extraction of sensitive application data. This can result in damage to the reputation of businesses.
- Prevention: To protect the data from these attacks, the data needs to be stored securely, safeguarded with encryption and strict access control measures.
M3: Insecure Communication
Insecure communication is sending sensitive data over non-secure channels which can be intercepted and copied by anyone who has access to this channel, which is everyone on the same network.
This is very common in public WiFi access points and you should always assume that your data is being intercepted when using one.
- Vulnerability Impact: Impact includes exposure of sensitive data, and compromising of network and data servers. From a business perspective, it can cause reputational damage from data theft, fraud, or privacy violation.
- Prevention: It can be prevented by encrypting data in transit using TLS/SSL protocols, using strong cipher keys for encryption, and applying an additional layer of encryption before secure transmission.
M4: Insecure Authentication
Insecure authentication is a vulnerability where there are faults in the mechanism used to prove a user’s identity to a system. Weak authentication measures are one of the root causes of many security risks.
Attack vectors such as authentication bypass, information disclosure via debug messages, and session invalidation are typical examples of insecure authentication.
- Vulnerability Impact: Having insecure authentication can tarnish a company’s reputation due to the possibility of data theft, manipulation, or damage.
- Prevention: Use client-side data encryption and constant and device-specific authentication.
M5: Insufficient Cryptography
Insufficient cryptography refers to having any weak points or gaps in cryptographic implementation through which an adversary can access sensitive information.
While cryptography is a fundamental part of any app that stores user data, there is a common misconception that cryptography can solve all security problems. Cryptography is just a tool that helps to protect the data from attackers.
- Vulnerability Impact: This can result in unauthorized access and subsequent retrieval of sensitive information like intellectual property.
- Prevention: Avoid storing sensitive information on insecure devices like mobile phones, and apply appropriate standardized cryptographic measures.
M6: Insecure Authorization
Authorization is a process that ensures that only authorized individuals who are allowed to access the data are performing the access operation. Many mobile applications have improper authorization implemented due to which low-level users can access information of any highly privileged user.
- Vulnerability Impact: Results in data theft, damage, and tarnish company image.
- Prevention: Proper verification and authentication of users, their roles, and permissions from the backend.
M7: Client Code Quality
Poor quality of the client code can result in many security flaws in a mobile application, but the most common ones are SQL Injection, Cross-Site Scripting, and Buffer Overflows.
Application code quality is an essential factor in ensuring the quality of the final product. As a developer, you should have several goals for your application.
- Vulnerability Impact: Issues with code quality can result in poor code execution resulting in gaps in functionality and security causing data loss, or theft.
- Prevention: Maintain standardized coding practices agreed upon by everyone involved, ensure good code documentation, and validate incoming data.
M8: Code Tampering
Code tampering is a process in which hackers exploit the existing source code of an application by modifying it with malicious payloads.
The issue is usually found in mobile apps that are downloaded from third-party app stores. These app stores are not associated with the official mobile application developers and usually distribute pirated apps.
- Vulnerability Impact: This can lead to business disruption, financial loss, and loss of intellectual property.
- Prevention: It can be prevented through the detection of changes in code during the run-time of applications.
M9: Reverse Engineering
Reverse Engineering is a process to decompile the mobile application to understand the application logic. Code obfuscation is done to prevent attackers from reading the application code and understanding the logic.
- Vulnerability Impact: Attackers can reveal information about backend servers, and cryptographic keys used, to perform attacks and steal intellectual property.
- Prevention: Applications and their codes can be made difficult to read logically through code obfuscation by creating a source code that is difficult to decompile.
M10: Extraneous Functionality
Bad actors such as cyber-criminals or hackers try to understand the mobile application’s extraneous functionality. The main goal is to understand and explore hidden functionalities of the backend framework.
- Vulnerability Impact: Exposure of backend functionalities, execution of unauthorized high-privilege actions, data theft, or damage.
- Prevention: Continuous source code reviews should be conducted.
Stages of the Android App Penetration Testing Methodology
- Scoping And Discovery
Android application penetration testing begins with setting a thorough scope of assets to be scanned and tested. This has to be done keeping in mind the layout and the data flow of the application.
- Assessment and Evaluation
The pentester monitors and assesses the application and its functionality before and after installation looking for vulnerabilities, entry points, and security gaps.
Static and dynamic analysis, inter-application communication, and reverse engineering are some of the assessment techniques used.
- Exploitation
The vulnerabilities discovered and evaluated for impact are then exploited using various techniques to try and gain access to the application.
Malicious payloads, and publicly available exploits are used to try and further the exploit and the access it provides.
- Reporting
Once the exploitation is complete, a report containing all the information on the vulnerabilities discovered, tests carried out and its impact on the application is detailed. Steps for remediation are also provided while the vulnerabilities are categorized according to their severity.
- Remediation
The vulnerability report plays a crucial role in allowing development teams to fix the issues detected in the Android application during the pentest. Following this a rescan is conducted to check the efficacy of the patches made.
Best Practices for Android Penetration Testing
1. Observe the security framework of the Android application
The security framework in use for each application will vary from the other and therefore it is highly recommended for the pentester to gain a thorough understanding of the same.
This allows for a solid pentesting plan to be created assessing all the necessary aspects of the application.
2. Know about the application structure and layout
This refers to having an in-depth knowledge of how the application works, how it manages data in the backend, its interaction with other services, and user requests.
3. Choose relevant pentesting tools
Tools opted for pentesting the Android application must be capable of carrying out extensive tests for the same to detect vulnerabilities.
For Android application pentesting the preferred methodology of testing is black-box where the tester is not aware of anything about the application.
Focus Areas for android penetration testing
1. Data Storage
Testing for data storage in an Android application is an integral part of Android penetration testing. These tests should include:
- Checking for Hardcoded credentials
- Sensitive data exposure such as API keys or tokens
- Encryption and Weak cryptography
2. Application-level communication
Communication of applications with other applications and with the application’s servers can lead to critical security issues if the communication between can is not done via a secure channel. Hackers use man-in-the-middle attacks to intercept the communication between mobile applications and servers.
3. Debug and Error messages
While developing an android application, developers use different kinds of error or debug messages to understand different application-level errors. These error messages are usually left even after production.
Hackers use these error messages to understand the flow of the application and hidden functionalities of the application.
4. Authentication & Authorization
Authentication and authorization are key areas to test while performing Android penetration testing. These tests should include:
- Session related security issues
- Storage of session token
- Authentication checks on sensitive endpoints
- Improper access controls
5. Code Obfuscation
The process of obscuring code to conceal its purpose is known as code obfuscation. Obfuscation leads to a code that is difficult to reverse engineer. Obfuscation is used as a method of protecting intellectual property as well as for anti-tampering.
Obfuscation is done by adding meaningless symbols (such as variable names like $i), changing the order of operations (i.e. changing the order of mathematical operations), or by using different languages (for example, by using a hexadecimal or other representations)
5 Secure Coding Practices for Android Developers
1. Communication over HTTPs
Communicating over HTTPs is standard practice for any business or company. The only problem with using HTTPs is that it isn’t an option everyone can use. It requires modification to your current infrastructure while it also requires you to re-enroll into your SSL certificate. Non-users state cost as a reason for not implementing it, however, HTTPs can improve one’s business structure and secure coding practices.
2. Encrypting sensitive data
Data encryption is the process of changing information to make it unreadable without secret information or a key known only to authorized parties so that unauthorized parties cannot read it.
Data encryption can be used to protect data traveling between two computers over the Internet, or it can be used to protect data stored on a hard drive. Data encryption can be used to protect data from being manipulated by malicious programs and is locked up with access availability for authorized parties alone.
3. Ask for credentials before showing sensitive information
Secure Android applications use data masking and password or biometric-based authentication to show or display sensitive data such as API Keys.
4. Use common error messages
As discussed earlier, error messages can lead to the discovery of hidden functionalities of the application. To avoid these security risks, developers should use common error messages and remove the debug errors or logs once the app is live.
5. Check the validity of external data sources
External storage can be used to store data that are used by your application such as a list of the most recent documents opened, or data that your application uses to do its work, like a database containing a list of customers.
The issue here is that you have to make sure that the data stored in external storage hasn’t been corrupted or modified by anyone else.
Top 3 open source tools for Android penetration testing
Android penetration testing is done via a various number of tools but let’s check the top Android 3rd party penetration testing tools that are usually used:
- MobSF: MobSF is an automated, all-in-one mobile application (Android/iOS/Windows) pen-testing, malware analysis, and security assessment framework capable of performing static and dynamic analysis.
- Frida: Frida is a dynamic instrumentation toolkit that is used by developers, reverse-engineers, and security researchers
- Apktool: Apktool is used for reverse engineering/decompiling any apk file. Using various Linux commands, android penetration testers find sensitive data.
Also Read: 11 Best Penetration Testing Tools & Platforms of 2022
What is Astra’s Android Pentest Suite?
Astra’s pentest suite is a complete solution to all your security needs. Astra makes it easy to perform controlled attacks on android devices with an easy-to-use interface and a streamlined workflow.
At Astra, we understand your needs and keep them as our top priority while performing any penetration test. With new features like login recorder, and the GitLab integration, Astra is pretty unparalleled on the feature front.
Checkout Astra’s Security Audit Checklist for Mobile Applications
Conclusion
In a nutshell, there are many reasons why you should be thinking about penetration testing your Android apps. Whether you’re a startup that’s just getting off the ground or a large corporation, the need for penetration testing on Android applications is accurate, and it’s here to stay.
FAQs
1. What is the timeline for Android pentesting?
It takes no more than 7-10 days to complete android penetration testing. The vulnerabilities start showing up in Astra’s pentest dashboard from the 3rd day so that you can get a head start with the remediation. The timeline may vary with the pentest scope.
2. How much does android penetration testing cost?
The cost of Android penetration testing with Astra’s Pentest suite ranges between $349 and $1499 per scan depending on the plan and the number of scans you opt for.
3. What makes Astra your best choice for Android pentesting?
1250+ tests, adherence to global security standards, intuitive dashboard with dynamic visualization of vulnerabilities and their severity, security audit with simultaneous remediation assistance, multiple rescans, these are the features that give Astra an edge over all competitors.
4. Do I also get rescans after a vulnerability is fixed?
Yes, you get 2-3 rescans depending on the plan you are on. You can use the rescans within a period of 30 days from initial scan completion even after a vulnerability is fixed.
















