Data Breaches are growing at a very high pace. It is time to take care of user sensitive data. Data is the life of any business: the more data, the better. But the more data you have, the more vulnerable you become to hackers and data breaches.
A data breach is the intentional or unintentional release of secure information to an untrusted environment. Data breaches can occur when a hacker breaches a company’s security measures or when an employee mistakenly (or purposefully) sends out sensitive information. Conducting software penetration testing regularly helps in securing data and avoiding data breaches.
What is Software Penetration Testing?
Software penetration testing is a method used to identify vulnerabilities in your software. This method is commonly used to test software security and is a very reliable way to check for security risks in the software. It is a simulated attack into the software that is conducted by professional security experts.
Software penetration testing is a type of test that is conducted to check the security of the application or software from malicious attacks. This testing is performed by a professional team consisting of a security tester and a report writer.
Software penetration testers are given an objective to test the security of a software. In some cases, they are given a checklist of what they should check during the test. The pentest report writer then analyzes the results of the pentest and creates a report. The pentest report is then sent to the client, and the client can then decide how and when to fix the vulnerabilities.

How can Software Penetration Testing add value to a company?
If you’re a business owner or a manager in a business that uses software in any way, then you should know that software penetration testing is a must. If you don’t have software penetration testing in your business, you’re leaving your organization vulnerable to cyber attacks, security breaches, and identity theft.
The purpose of software penetration testing is to help the business, and IT leadership identify vulnerabilities within their application. Software penetration testing is often the final step in identifying vulnerabilities within an environment and can be viewed as high-risk tests.
By utilizing an outside perspective, the penetration tester can test for vulnerabilities that might be overlooked by internal personnel. Although penetration testing can be a high-risk activity, it is highly recommended to perform penetration testing regularly. Penetration testing can be performed using automated penetration testing tools, manual techniques, or a combination of the two.
Also Read: Top 11 Penetration Testing Tools of 2022 [Reviewed] | Penetration Testing Quotes
Software Penetration Testing VS Software Testing VS Software Security Testing
Software testing involves analyzing a software product and its features to find bugs and other problems. Software testing is a key part of the software development process. Software testing is a method of verifying that a software product or application works as it should and meets its required quality standards.
There are different types of Software Testing:
- Unit Testing
- Integration Testing
- System Testing
- Acceptance Testing
- Regression Testing
- Security Testing
Security testing is a special type of software testing in which an application is tested for security vulnerabilities. Security testing is a critical component of software testing and should be an integral part of the SDLC and other testing processes. Security testing can be used to test applications for vulnerabilities and weaknesses that malicious users could exploit.
Security Testing is of 5 different types:
- Vulnerability Scanning
- Software Penetration Testing
- Risk Assessment
- Security Auditing
- Source Code Review
Software penetration testing (or pen-testing) is a manual or automated form of testing which attempts to discover vulnerabilities that an attacker could leverage to attack a software. Software penetration testing is a specialized form of security testing that attempts to discover and exploit weaknesses in software.
Related Read: SaaS Penetration Testing | Security Testing Software – 5 Things to Understand Before You Choose One
Different types of Software Penetration Testing
1. Mobile Application Penetration Testing
Mobile application penetration testing is a penetration testing process designed to test mobile applications’ security. In this method, a penetration tester is assigned to evaluate the security status of the mobile applications.
The mobile app penetration tester will test the applications to find out vulnerabilities in them and evaluate the potential risk to the organization if the hackers exploit the vulnerabilities.
Mobile application penetration testing involves many techniques, tools, and practices to find the vulnerabilities in mobile applications. These techniques, tools, and practices are applied to test various aspects of mobile applications like authentication, authorization, data leakage, code injection, etc.
2. Web Application Penetration Testing
Web application penetration testing is a process that assesses your web system for security vulnerabilities. Every organization should conduct web penetration testing to ensure that their information is safe and that unauthorized persons or employees can access no data or information.
Web application penetration testing is a security measure that should be carried out periodically to determine how vulnerable your system is to malicious attacks.
Also Read: Website Penetration Testing- A Complete Guide
3. Blockchain Penetration Testing
The blockchain is a distributed ledger that stores data across a network of computers rather than on one single secure server.
Blockchain penetration testing is a security assessment process done by ethical hackers or security professionals to test the security strength of the blockchain-based solution or application. Blockchain penetration testing helps enterprises identify the weak spots in the blockchain architecture, leverage the threat landscape and guide the security operations team to build an effective security strategy.
4. Cloud Penetration Testing
Cloud penetration testing is a process that is accomplished by using a combination of techniques, including penetration testing and attack simulations that are executed from a cloud environment towards a target that is hosted on a cloud platform.
The goal of the cloud penetration testing is to test the security of a cloud environment, gain access to a system that is hosted on a cloud platform, identify vulnerabilities that are related to the security of the cloud environment, and recommend actions that may help to mitigate the vulnerabilities that were identified.
Also Read: What is Automated Penetration Testing? Difference between Automatic & Manual Pentesting Software
How is Software Penetration Testing performed?
Software Penetration Testing is performed in 5 different steps. Each step has its purpose and is performed to reveal different information about the target. Let’s understand each one of them in detail.
1. Pre-Engagement Analysis
One of the most important parts of a penetration test is actually before the penetration test begins. It’s the pre-engagement analysis. Many clients don’t even think about this, but it is one of the most important parts of the penetration test. The reason why this phase is important is because this is when you can talk about the scope of the test, the time frame, the budget, the objectives, the tools and the penetration testing methodology, etc.
Are you unable to access your website? Is your website experiencing hacking issues? Find out in 15 seconds.
2. Information Gathering
Information gathering is the cornerstone of any penetration test. Information gathering is the reconnaissance phase of the penetration test. The penetration tester must gather as much information as possible about the target.
Many information-gathering techniques are passive, which means they do not require interaction with the target. Passive techniques range from using search engines to social engineering.
3. Vulnerability Assessment
Vulnerability assessment is a part of penetration testing that focuses on finding and confirming security vulnerabilities in the target environment. Vulnerability assessment itself is a process and not a single test.
Vulnerability assessments may include a variety of testing and scanning activities. The specific activities included in a given assessment will vary based on the nature of the target and the scope of the assessment.
4. Exploitation
Exploitation is the final phase of an attack. It is the phase where the attacker exploits the security gaps of the target software to gain access to the data. During the exploitation phase, the attacker uses exploits to gain access to the software.
Exploits are scripts used to exploit security gaps. The exploitation phase is the most important phase of an attack as it will determine the attacker’s success or failure.
5. Reporting
The Reporting Phase is a part of penetration testing. In the reporting phase, the penetration tester will have to document all the vulnerabilities they have found and provide a list of recommendations to the management.
In the reporting phase, the pentester will have to demonstrate the vulnerabilities they have found and the control measures to deal with the vulnerabilities. The report should include the following details:
1. The number of vulnerabilities found in each category
2. An action plan to address each of them
3. The technical and business impact of these vulnerabilities and their potential impact
4. The time required to fix the vulnerabilities
Learn more about Penetration Testing Phases
3 Approaches to Perform Software Penetration Testing
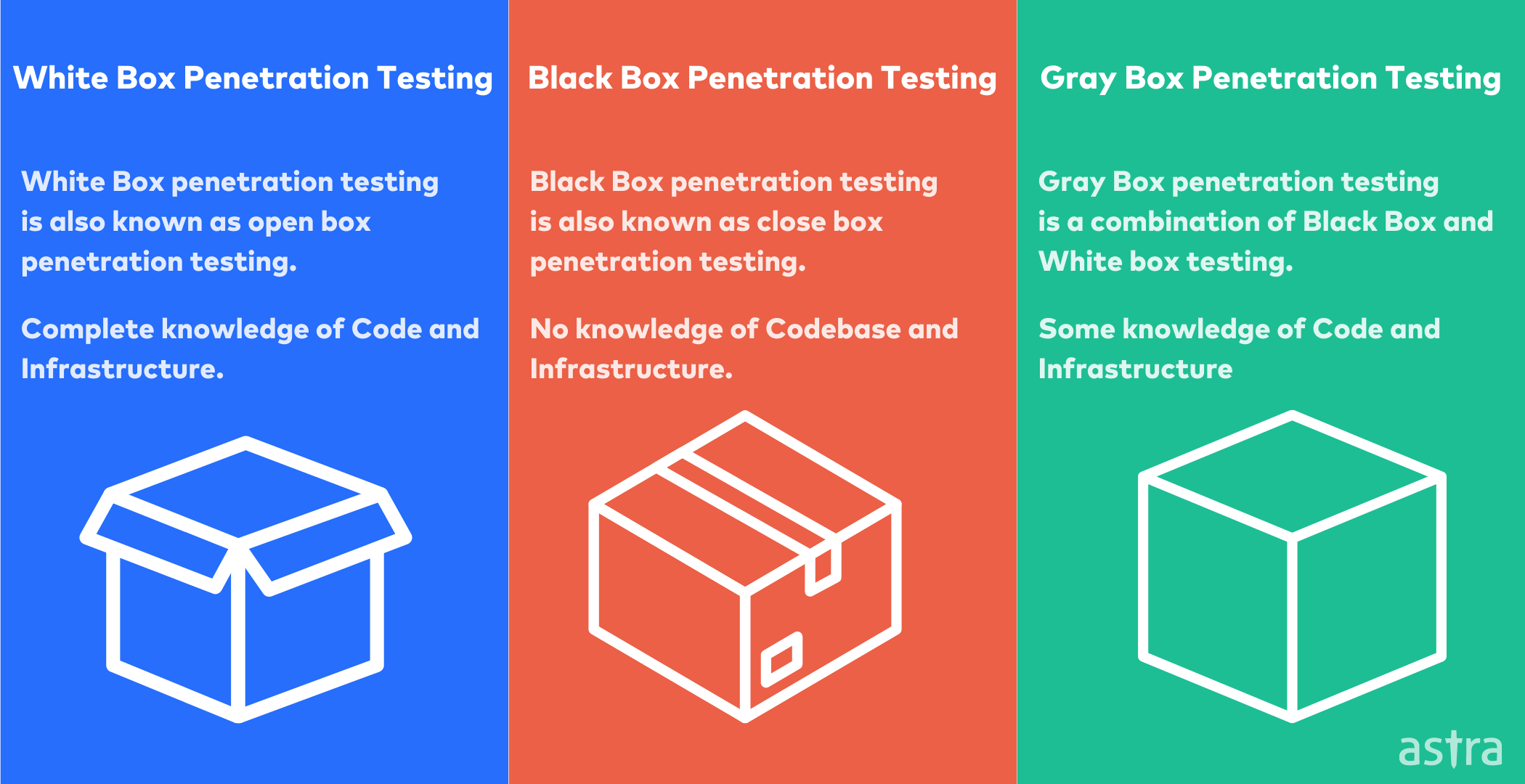
1. White Box Testing
White Box Testing is the testing of internal structures or workings of a software application. White box testing is usually done by developers or testers who have detailed knowledge of the internal structures or workings of the application. This type of testing usually occurs in the development phase of the software development lifecycle.
2. Black Box Testing
Black box tests are done without knowing or understanding the internal mechanism of the software. Black box testing is the most widely used testing method. The tester does not know the software and designs the test as an uninformed attacker. Black box testing focuses on the functionality of the software. It is usually done at the requirements or specification level.
3. Gray Box Testing
Gray Box Penetration Testing is a method of pen-testing that attempts to combine the best of both the Black Box and White Box methodologies. In gray box penetration tester, the tester has some knowledge of the code and infrastructure but not a complete understanding.
Three common tools used for Software Penetration Testing
1. OWASP ZAP: OWASP ZAP is an open-source security tool for finding vulnerabilities in your web applications. It is designed to be used by people with a wide range of security experience. As such, it is ideal for developers and functional testers who are new to penetration testing.
2. Vega: Vega is a free and open-source web security scanner and testing platform to test the security of web applications. Vega can help you to find security issues and vulnerabilities related to the application. It’s a web application security scanner that can be used to audit web applications.
3. sqlmap: sqlmap is an open-source penetration testing tool that automates the process of detecting and exploiting SQL injection vulnerabilities. It comes with a powerful detection engine, many niche features and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
Also Read: Top 5 Software Security Testing Tools You Should Know About | Top 6 Web Pentest Tools You Should Not Miss
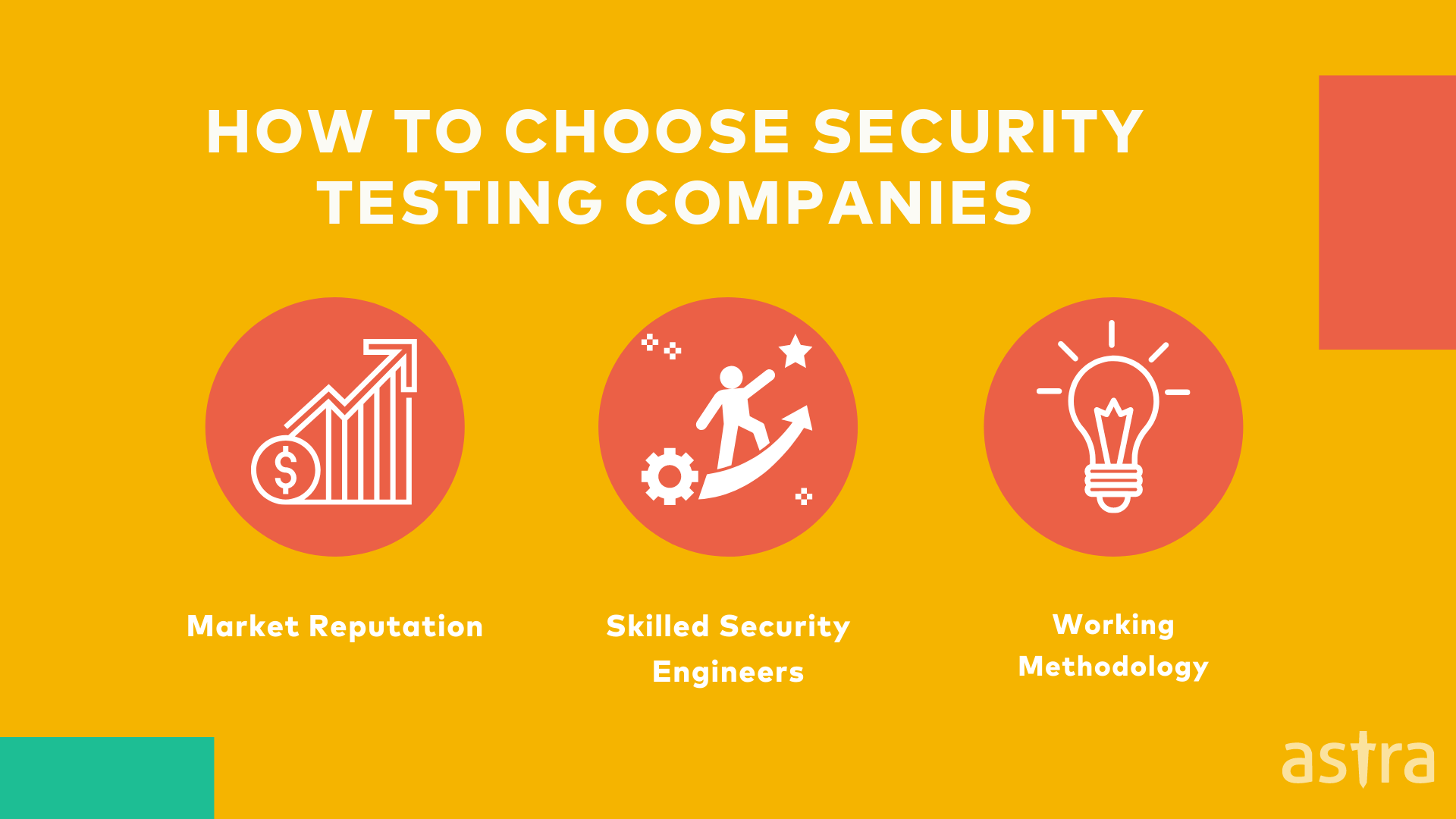
3 Things to check to choose a Software Penetration Testing Vendor
Penetration tests are important, but it is even more important who carries them out. This is where a Penetration Testing Vendor comes into the picture. Because choosing a Penetration Testing Vendor can be a daunting task, we have gathered a few pointers to help you make the right decision.
- Software Penetration Testing vendors should have highly skilled security engineers to perform the testing.
- Make sure the vendor has a good reputation in the market.
- Understand what methodology the vendor will be using and how they will be dealing with sensitive data.
- Check the vendor’s pricing and how it will help reduce the cost of a data breach.
Why do companies trust Astra for Software Penetration Testing?
No one wants to realize how easily hackers can gain access to their software, but you can’t afford to have a security breach as a company. Hacking is a growing problem, and many companies are aware of the potential risks. Luckily, there are many ways to prevent a security breach, and one of the best ways is to hire a penetration testing company.
Astra provides a complete service for pen testing that is trusted by many small and big companies to conduct secure software testing services for their products and applications. Astra performs Software Penetration Testing to ensure that the applications and software are secure and compliant with the security standards and regulations.

Conclusion
Software penetration testing is one of the best ways to get a clear idea about the security of your application. It is a process through which the security of your software can be measured. The main aim of penetration testing is to evaluate the software’s security by trying to penetrate the software with the use of vulnerabilities. Many companies trust Astra for Software Penetration Testing to ensure they have security software to fight against hackers. Why don’t you? Get in touch with us today to make sure your software is free from security vulnerabilities.
FAQ’s
1. What is Software Penetration Testing?
Software penetration testing is a type of security testing that focuses on finding security vulnerabilities in the software or application in a way a hacker would try to attack it from outside.
2. How much does an average software pentest cost?
The pentest pricing varies as per the range of the pentest and a few other metrics. That said, most penetration testing pricing comes between $500 to $10,000 for a single scan for a website or mobile application.
3. What is the timeline for Software Penetration Testing?
Although the timeline of the pentest is based on the scope, on average, software pentest takes around 7-10 days. Vulnerabilities start showing up in Astra’s pentest dashboard from the second day of the scan.
4. Why choose Astra for software penetration testing?
Astra is the security team you never had. Astra is trusted by those whom you trust. Astra is a team of skilled and professional security engineers who perform extensive manual pentest on top of machine learning-driven automated scans.

















which are the best software penetration testing tools apart from sql, owasp and vega?
Hey Monika, apart from the mentioned tools, others like Astra’s Pentest Suite, Burp Suite, Nikto, and Metasploit are some of the best software penetration testing tools.