A responsible mobile app development practice compels you to rethink the security of your app as you build it. But, mobile application security tests are easier said than done. This is why we have put together this mobile security testing guide to help you out.
According to a survey, over 98% of mobile apps are not secure! This is due to one major fallacy in their app development practice which pushes mobile security testing to the end of the development cycle. Or worse, abandon it altogether.
With this blog post, you will learn about – some astonishing mobile app hacking stats, the common security risks to mobile apps, the basics of mobile application security testing, and steps to carry out end-to-end mobile app security testing. With a mention of automated tools.
What Is Mobile Application Security Testing?
Mobile application security testing refers to analyzing mobile applications for potential flaws through hacker-style testing. This is done before the production of the app to ensure zero errors in the implementation. Security testing of mobile applications is done for applications on various platforms like iOS, Android, and even Windows.
One can use or make a mobile application security testing checklist to be well-prepared for iOS or Android application security testing. The security of mobile applications can be tested at two stages.
- One during the initial development phase and throughout development.
- Towards the end stage of development or the application’s final build.
Why Is Mobile App Security Testing Important?
Mobile app security testing is vital for the following reasons:
- Detection of Vulnerabilities: Timely detection of vulnerabilities ensures that flawed application susceptible to malicious attacks isn’t released by the developers.
- Elimination of Vulnerabilities: Eliminating the detected vulnerabilities ensures that a well-secured application is released and customer data will remain safe.
- Maintain Compliance: Mobile applications are strictly required to maintain compliance since many such applications deal with payments and customers’ personal information thus making compliance with various security standards crucial.
- Free of Security Risks: Mobile application security testing successfully secures one’s application against any risks that could result in data breaches, theft, or loss of confidential information.
Types Of Mobile Apps
- Web apps: Normal web applications built-in HTML and accessed from your mobile.
- Native apps: Specifically built for a particular OS and use OS-specific features.
- Hybrid apps: Similar to native apps but behave like web apps leveraging the benefits of both types.
Criteria For Mobile Application Security Testing
1. Analyzing threat and modeling
The first step is to produce and analyze any potential threat. This is done by checking the parameters as mentioned below:
- While downloading an app, if it stores any logs within the app store including credentials or account information, there might be a chance of a data leak.
- If apps store user credentials, the developers need to analyze any potential threat to the user data.
- Users need to scrutinize the data shown on an app, as the attackers can exploit this data by hijacking sessions or snooping.
- Apps can quickly send and receive data thanks to high-speed internet connectivity. Attackers can capture this data, to avoid this, all transmitted data can be encrypted.
- Interconnection with other apps or third-party services needs to be secured. Any vulnerability in the structure can endanger all services of the app.
2. Analyzing Mobile Application vulnerabilities
During vulnerability analysis, you need to check the app for any security gaps, the responsiveness of the security defenses, and whether they can counter any attack in real time. Before jumping into this stage, ensure that there is a list of vulnerabilities to check and a format to capture all findings.
A complete vulnerability analysis consists of checking components at a broader level, including the network, operating system of the phone, and hardware.
Mobile apps hacking statistics
A study by App Annie shows that mobile app downloads reached 204 billion in 2019 and the worldwide app store consumer spending increased to $120 billion.
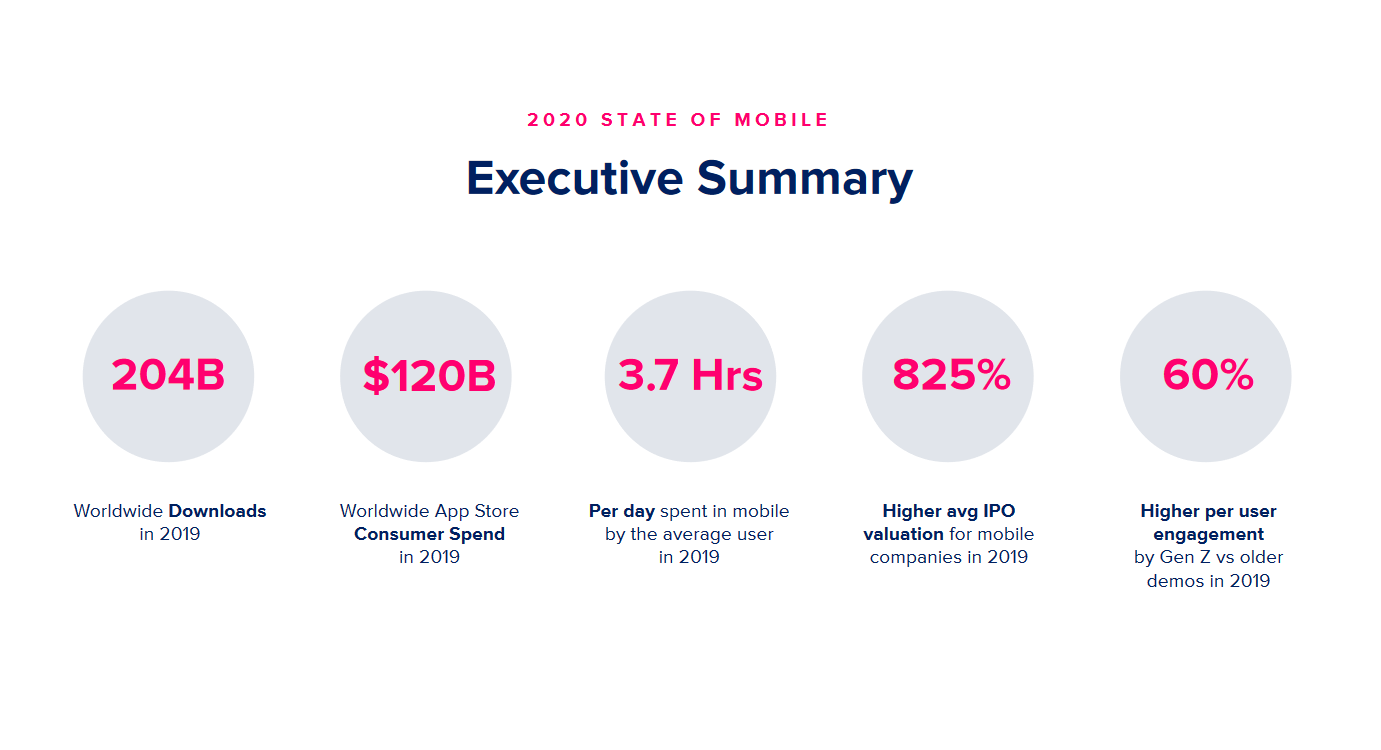
Although the popularity of mobile apps is quite evident, risks related to the security of mobile applications have also risen. Here are a few security stats for mobile apps:
- 1 out of 36 devices is compromised by a mobile app security threat.
- Nearly 10,000 rogue apps are responsible for 28% of all attacks (in 2018). (Source: RSA’s recent report)
- 71% of fraud transactions came from mobile apps and mobile browsers (in 2018).
Understanding Mobile App Security Issues: Android vs iOS
Although it wouldn’t be entirely true to say that app developers are shoddy about security, it can’t be ruled out either. The fact that so many apps are getting hacked increasingly has something to do with the poor security infrastructure of these apps.
Now, the apps on Android are a bit differently developed and distributed than their iOS counterparts. This means the security issues in both these platforms differ too.
Mobile app security issues in Android:
Mobile app hacking stats show that Android apps are more badly hit than iTunes. One major reason behind this is Android’s open-source environment meaning, anyone is free to use or change Android’s source code for app development. The major reasons behind this are:
- Android’s open-source environment allows anyone to use or change Android source code for app development.
- The lack of a strict screening process by Android OS for apps leads to an increased number of vulnerable mobile applications.
Such issues can be detected with ease by using tools that provide Android app security testing. Major security issues in an Android app include:
- MITM (Man-in-the-Middle Attacks)
- Cryptojacking
- Malvertising
- Phishing and Social engineering
- Component related threats
- Permissions based issues
- Rooting
Mobile app security issues in iOS:
iOS apps are less vulnerable than Android apps because of their closed development environment. Also, Apple follows a meticulous screening process for their apps. That said iOS apps are not free from security risks entirely.
Market share analysis tells us that iOS operating system is more frequently used by the affluent divide, making it a hot target for hackers. Despite the security measures, there have been instances where iOS apps, devices, and other data were hacked. Major security issues found in an ios app include:
- Storing data locally on the device
- Jailbreaking
- Phishing and Social Engineering
- Allowing 301 Redirects
- Stolen certificates to host apps
Besides security risks emanating from the basic structure and build of the two operating systems, there are other common mobile app security issues faced by Mobile apps regardless.
Top 10 Mobile App Security Issues By OWASP
According to a list issued by OWASP in 2016, the top 10 mobile app security issues are:
- Improper Platform Usage
- Insecure Data Storage
- Insecure Communication
- Insecure Authentication
- Insufficient Cryptography
- Insecure Authorization
- Client Code Quality
- Code Tampering
- Reverse Engineering
- Extraneous Functionality
Development Fall-Outs In Mobile Application Protection
Several other mobile application protection issues in Android and iOS stem from poor development practices and maintenance. Here’s what developers have been doing wrong while building an app:
- Not securing components of their apps
- Ignoring insecure interprocess communication
- Not thinking about secure data storage
- Not using universal links
- Overlooking configuration flaws (Configuration flaws include disclosure of sensitive information in error messages, fingerprinting in HTTP headers, and TRACE availability.)
- Not testing their code in every development stage and on runtime
- Not planning for caching & logging Vulnerabilities
- Not patching your code fast enough
Mobile Application Security Testing as a Solution
The best way to prevent any mobile app security issues is to hack your application yourself.
Security testing in mobile applications is the best way to accomplish that. Ideally, mobile application security testing should be conducted before you launch your app for public use, however, if you have missed doing that, the next best time to do security testing is today.
Mobile application security testing consists of two processes — Vulnerability Assessment (VA) and Penetration Testing (PT) — usually performed in tandem:
- Vulnerability assessment: involves the evaluation of the application’s infrastructure and security mechanism to detect possible vulnerabilities & loopholes in the app.
- Penetration testing: As the name suggests, it involves exploiting the vulnerabilities found in the VA to assess the scope of a possible hack via that vulnerability.
In simpler words, VA lists the vulnerabilities and PT provides a clear picture of their severity.
How To Perform Mobile Application Security Testing
1. Define the goal of the security audit
Security audits are vast and multi-purpose. Hence before you begin with the process know your number one reason why you are doing the audit. What is it that you hope to find or correct? Will there be actions at the end of the process.
Once all this is answered, make a list of priority security areas you need to assess first. Then, as you go on and cover these areas, you can always add new ones. The goal of mobile application security testing can be any of the following things:
- To check if there’s a security mechanism in place
- To confirm a management control framework exists
- To check if there are right configurations set
- To check if the application has been tested in each stage and with different test cases
- To check all communication between a user and the application and application and server is encrypted
- To detect and manage all threats and risks to the app
- To check proper authentication process is implemented
- To check session and cookies are properly handled
- To confirm security requirements are met in contract management
- To check the secure data storing process is implemented
High on priority security areas in a mobile app shall include:
- App permissions
- Configurations
- Authentication and Authorization
- Session and cookies
- Data storage
2. Threat analysis and modelling
Threat analysis is a process to identify potential threats in a system. Threat analysis & modeling has four components:
- App architecture
- App resources
- Third-party interaction
- Threat agents
While evaluating your mobile app for vulnerabilities, being pessimist is the key. Think of all the components and functionalities that could allow a hacker in. Since you already have a list of high-priority areas, start with them first.
List down all potential security risks in them. For an even precise result, develop test cases (usually a permutation of different app functions, operating systems, versions, user roles, permissions, and so on) and analyze your app for those.
To quicken the process of threat analysis and modeling for your mobile app you can use these automated tools:
- Android Debug Bridge: Android Debug Bridge (ADB) is a command-line tool that is used to assess and debug mobile apps. ADB is a client-server program consisting of three components: Client, Daemon, and Server. ADB is a great security testing tool, however, it is limited to the Android OS, which brings us to the next tool. ADB is available in the Android SDK Platform-Tools package. However, you can also download ADB with the SDK Manager or directly from here.
- Mobile Security Framework (MobSF): Mobile Security Framework (MobSF) is an automated security testing framework for Android, iOS, and Windows platforms. It performs static and dynamic analysis for mobile app security testing. Follow this guide to install MobSF.
- iMAS: iMAS (iOS Mobile Application Security) is an iOS security testing framework to find out vulnerabilities in an iOS mobile application. iMAS works great in detecting vulnerabilities related to security controls, CWE, system Passcode, jailbreak, debugger/run-time, flash storage, and keychain.
3. Exploitation
Threat analysis is work half-done. By now, you know what are the possible vulnerabilities threatening your app and the test case it is occurring with. Now, all you need to do is to estimate the scope of these vulnerabilities. By scope, I mean the penetration of these vulnerabilities in causing damage to your app. In other words, the severity of the vulnerabilities.
The tools you can use for this are:
- QARK (Quick Android Review Kit): Developed by LinkedIN, QARK is an automated Android pen-testing tool. You can scan all components of your mobile app to detect any misconfigurations and threats. QARK also highlights issues in your Android version.
To install QARK, use the following command:
~ git clone https://github.com/linkedin/qark
~ cd qark
~ pip install -r requirements.txt
~ pip install . --user # --user is only needed if not using a virtualenv
Follow this detailed guide on how to use QARK for Mobile application security testing.
- Zed Attack Proxy (ZAP): ZAP is a free security testing tool used by thousands of pen-testers around the globe. ZAP is developed by OWASP and is one of the most preferred tools for manual security testing.
To download ZAP for Linux OS, use this link.
- Mitmproxy: Mitmproxy is a free and open-source tool to identify MITM (Man-in-the-Middle) vulnerabilities in a mobile app. It is an HTTP proxy that can be used to intercept, inspect, modify and replay web traffic such as HTTP/1, HTTP/2, WebSockets, or any other SSL/TLS-protected protocols in a mobile app. mitmproxy is a great way to exploit client-server communications of your mobile app and identify the underlying vulnerabilities.
Also Read: 11 Best Penetration Testing Tools & Platforms of 2022 | Top 5 Software Security Testing Tools in 2022 [Reviewed]
4. Remediation
So far, you have set a definitive goal for the audit, analyzed your app and it’s supporting infrastructure for vulnerabilities, exploited vulnerabilities to determine their criticalness. By the end of the previous step, you should have a list of vulnerabilities segregated according to their severity.
In this step, you fix the vulnerabilities, focusing first on the critical ones.
Too complex for you? Get Astra Security
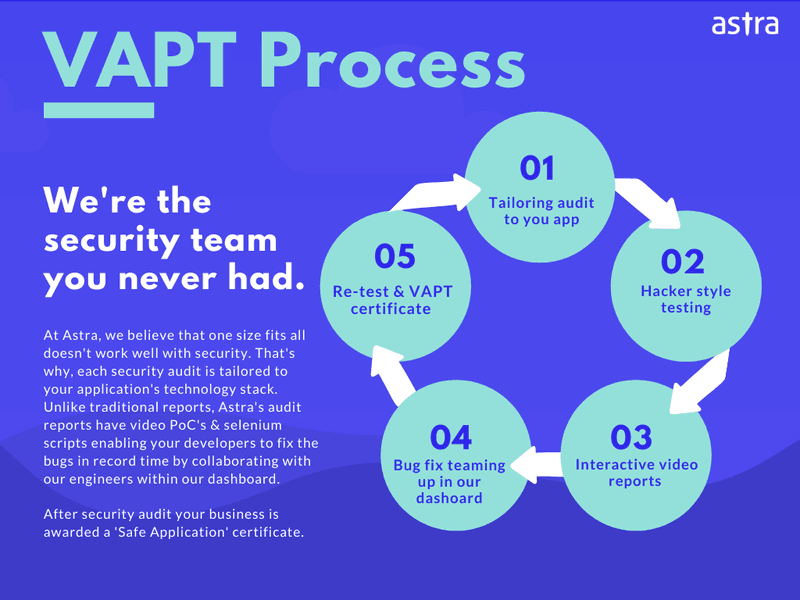
If the above process sounds too much of work, you can totally trade it for an easier yet more thorough option. I am talking about taking a professional mobile app security audit. At Astra Security, we regularly help app developers to secure their apps by finding vulnerabilities in their apps.
Here’s how Astra’s VAPT work:
Security tips for safe mobile app development
Lastly, after you have tested your solution for security risks, it is time you protect it too. Besides patching and updating your mobile application regularly, there are other security practices you can undertake. Follow this exhaustive guide on 10 security tips for your mobile app development to learn more.
















