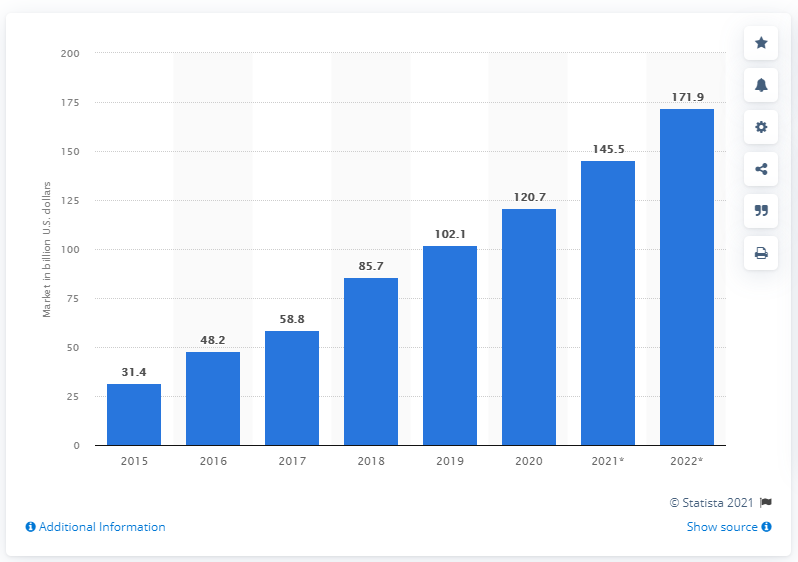
Software-as-a-service, colloquially known as SaaS, is a subscription-based cloud service model. The easy scalability, fast implementation, low cost of SaaS have soared it to popularity. The onset of the Pandemic in 2019 further fuelled the growth of SaaS. As per Statista, SaaS solutions are to capture a market cap of over 171 billion US dollars by 2022. It has almost tripled since 2017!
The crazy expansion of the SaaS model across industries is both amazing and scary at the same time. Undoubtedly, SaaS has simplified operations for a ton of businesses out there, but cyber threats still lurk for SaaS. Further, data security & privacy rules, and other compliances like – HIPAA, ISO/IEC-27001, SOC 1, SOC 2, etc. – encourage SaaS to take solid action in securing their product & the surrounding infrastructure. For healthcare & finance industries, these laws have even more stringent implications.
These compliances generally require you to go through external SaaS penetration testing. SaaS penetration testing helps you to test your product, infrastructure, assets, and other connected systems for security flaws & vulnerabilities.
Let’s understand what else does SaaS penetration testing encompass and how to choose the right SaaS penetration testing service for your business.
Know About: Penetration Testing Quote | Security Testing Software – 5 Things to Understand Before You Choose One
What is SaaS penetration testing?
Though SaaS simplifies operations for others, they themselves operate on quite a complex infrastructure. A SaaS solution has much going on behind the scenes than what meets the eye. There are web interfaces, network, cloud, APIs, third-party integrations, base code, user roles, and several other inter-connected systems that make a SaaS solution what it is.
Maintaining & securing these SaaS components enterprise-wide is no easy task. Vulnerabilities creep up in one form or another. This is where SaaS penetration testing helps.
SaaS penetration testing is an in-depth evaluation of all components of a SaaS business to highlight & fix hidden security vulnerabilities in them. It also helps SaaS owners review the present security of their product, bridge existing security gaps, and identify improvement areas, while there still is time.
Also Read: API Penetration Testing: What You Need To Know
How SaaS penetration testing helps your business?
Extending services to many other companies, SaaS shoulders the responsibility to keep associated companies from fatal security risks. If not for moral reasons, SaaS owners are also bound under strict compliances to keep their environment safe before they can sell. This is a huge catalyst for SaaS business owners in seeking SaaS penetration testing.
However, a penetration test can help your business in other ways as well. A thorough SaaS pentest helps you with:
- Vulnerability Detection: It helps you detect & fix vulnerabilities in all systems & networks
- Security Planning: It enables you to chalk out a working security plan with the test results to improve your technical environment
- Compliance Requirements: It helps you meet compliance requirements like HIPAA, SOC2, ISO-27001, GDPR, and so on.
- Confidence & Trust: It Instills great confidence in you as the owner and trust in your customers & partners.
What to expect from SaaS penetration testing?
Many SaaS solution owners understand the objectives of SaaS penetration testing, but only vaguely. When you don’t have a clear vision of your requirements, you may fall for the wrong test. Or have wrong anticipations about the outcomes.
To avoid that, you must understand what SaaS penetration testing can do for you and what it can’t.
SaaS penetration testing can:
- Help you find & fix vulnerabilities in your technical arrangements. Typically via application & infrastructure testing. It tests web apps, cloud, source code, third-party integrations, devices, APIs, firewalls, etc.
- Increases awareness of your security processes and arrangements
- Helps you meet rules & regulations.
SaaS penetration testing can’t:
- Look into security issues emanating from lack of security education & awareness in the organization
- Fix vulnerabilities. Usually security engineers report vulnerabilities with steps to remediation, however, they don’t fix those vulnerabilities themselves
- test external services/APIs your business uses unless explicitly mentioned
- perform DDoS or stress testing on the applications since a lot of cloud providers like AWS forbid that.
Also Read: 11 Best Penetration Testing Tools & Platforms of 2022 | Third-Party Penetration Testing And Why You Should Consider It
What to look for in a penetration testing solution for your SaaS?
When looking for a SaaS penetration testing service, look for transparency, viability, time frame, methodology, trust & security. You can also ask informed questions about the process, frequency of testing, type of support provided, certifications, customers, and case studies before you engage with the penetration testing team.
Besides these fundamental questions, you should also look for a penetration testing service that provides you with:
- Easy reporting & management of vulnerabilities
- Detailed penetration testing report
- Fixing advice
- Re-test, etc.
Related Article: How to Conduct a SaaS Security Audit in 7 Easy Steps | Why Firewall Penetration Testing is Essential to Your Security Strategy
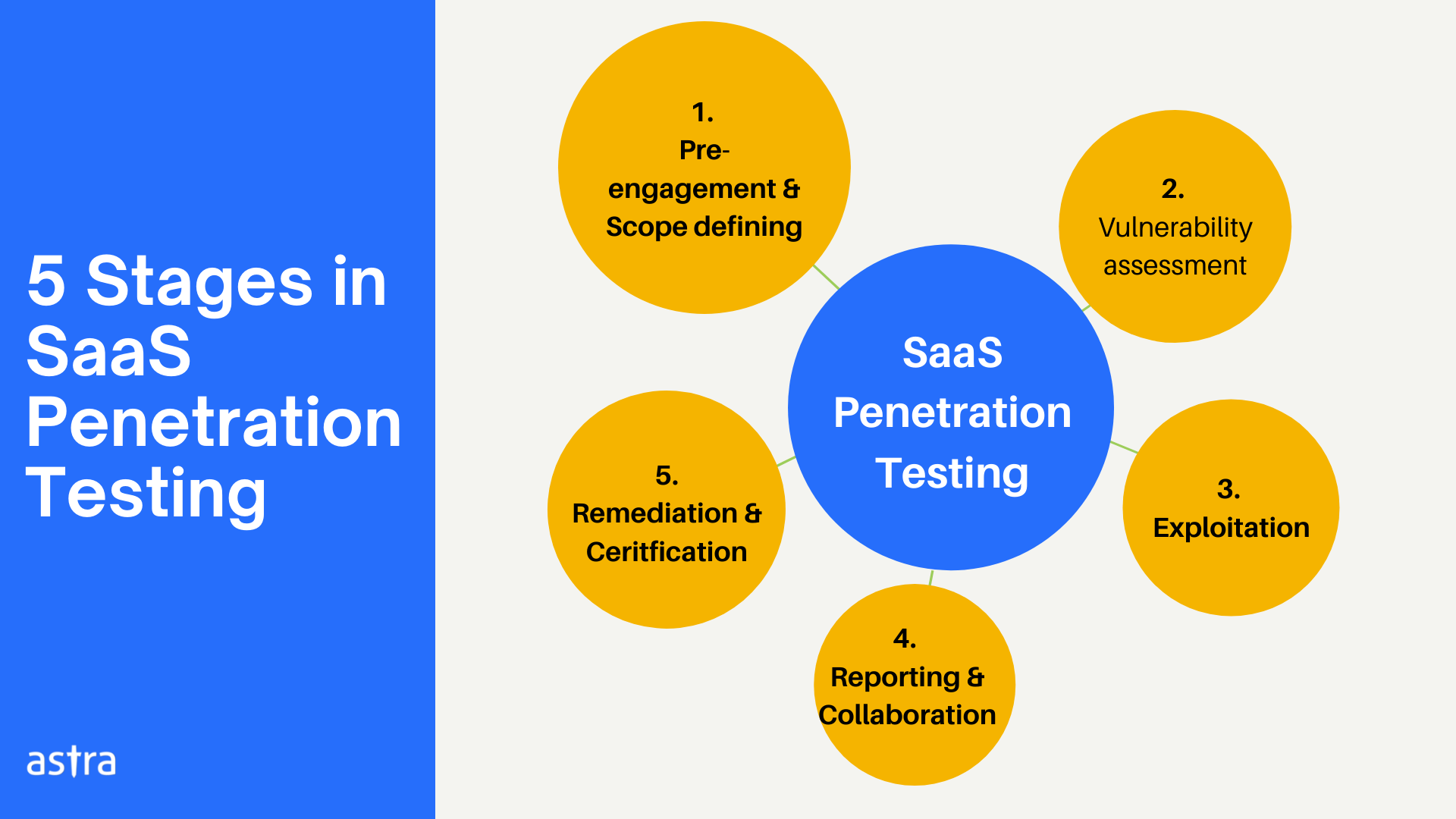
5 Stages in SaaS penetration testing
SaaS penetration testing stages can be broken down into these 5 stages:
Also Read: Top 5 Software Security Testing Tools in 2022 [Reviewed]
1. Pre-engagement & mapping scope
This is the first stage in a SaaS pentest.
For the saas owner getting a pentest, this is the stage:
- To ask out queries about the engagement
- Communicate their objectives and the perceived outcomes
- Share their compliance and other requirements
- And, inform about the basic scope of the test.
From a security engineer’s perspective, this is the stage:
- To pan out the depth and breadth of the testing according to the scope
- Discuss methodology and testing details
- Clear any false notions about the testing and set the right expectations
- Communicate the time frame and details required from the client
- Propose costs of the engagement
Note: In the case of SaaS, the scope is usually massive. Including – the application, various user roles, cloud infra, APIs, integrations of the SaaS with other platforms, email services, payment gateways, etc. This could influence the costs of the engagement.
2. Vulnerability Assessment
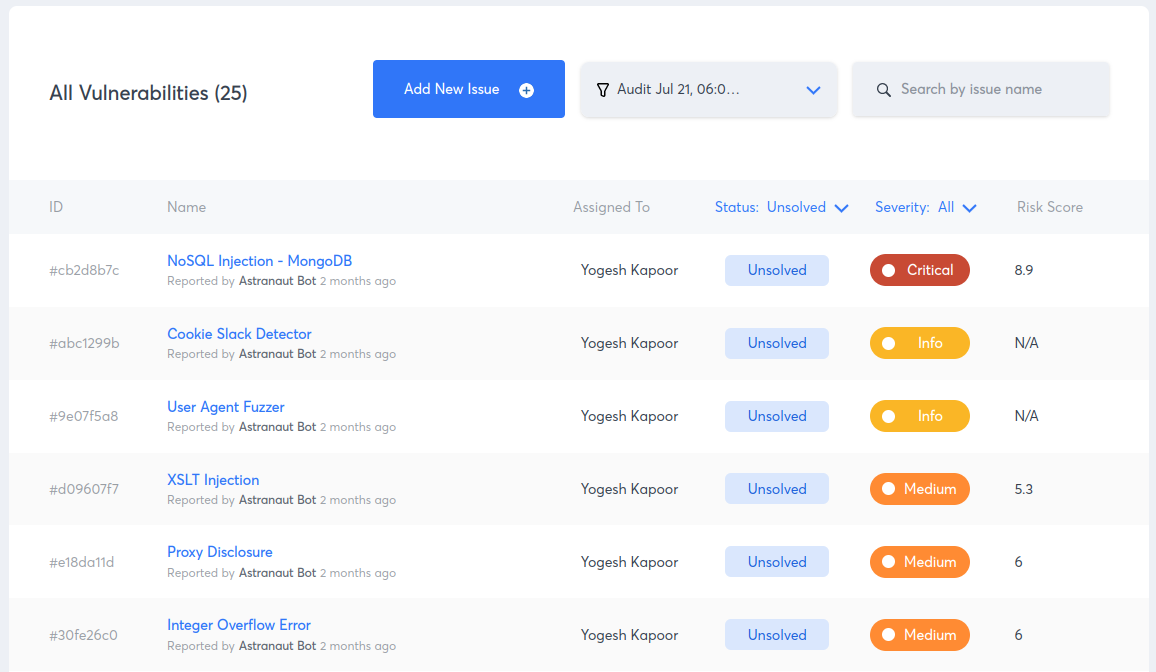
After signing the agreement, the testing starts with Vulnerability Assessments. This is where the tester scans the whole infrastructure for security vulnerabilities. This is largely an automated process, nonetheless, extremely crucial. The results of the vulnerability assessment direct the rest of the testing.
For example, see the following vulnerability assessment conducted by Astra’s Pentest Scanner:
Read Also: SaaS Security Assessment: Important Tips & 7 Best Practices
3. Exploitation
The vulnerabilities identified in the above step will be exploited in this stage to gauge their impact on the system.
This is a very detailed step and is beyond the scope of this article. If you wish to know more about the process, we’ve covered them in our blogs here:
- What, Why, and How of Penetration Testing
- How to Conduct A Web Application Penetration Testing?
- What is Network Penetration Testing & How to Perform It?
- A Complete Guide on Cloud Penetration Testing
4. Reporting & Collaboration
The next step in SaaS penetration testing is to document the found vulnerabilities. Along with the identified vulnerabilities, the tester should also report their impact, the steps to reproduce, and the steps to fix for the respective vulnerability.
At Astra, we go the extra mile to also provide details like potential monetary loss of a vulnerability, CVSS score, Automated calculated risk score, PoCs, and selenium scripts along with the traditional information.
Given the complex arrangement of a SaaS, a continual two-way collaboration becomes even more so necessary. A bumpy communication can hamper the performance of the testing and the remediation. If you’re collaborating over email or support, make sure queries are quickly replied to.
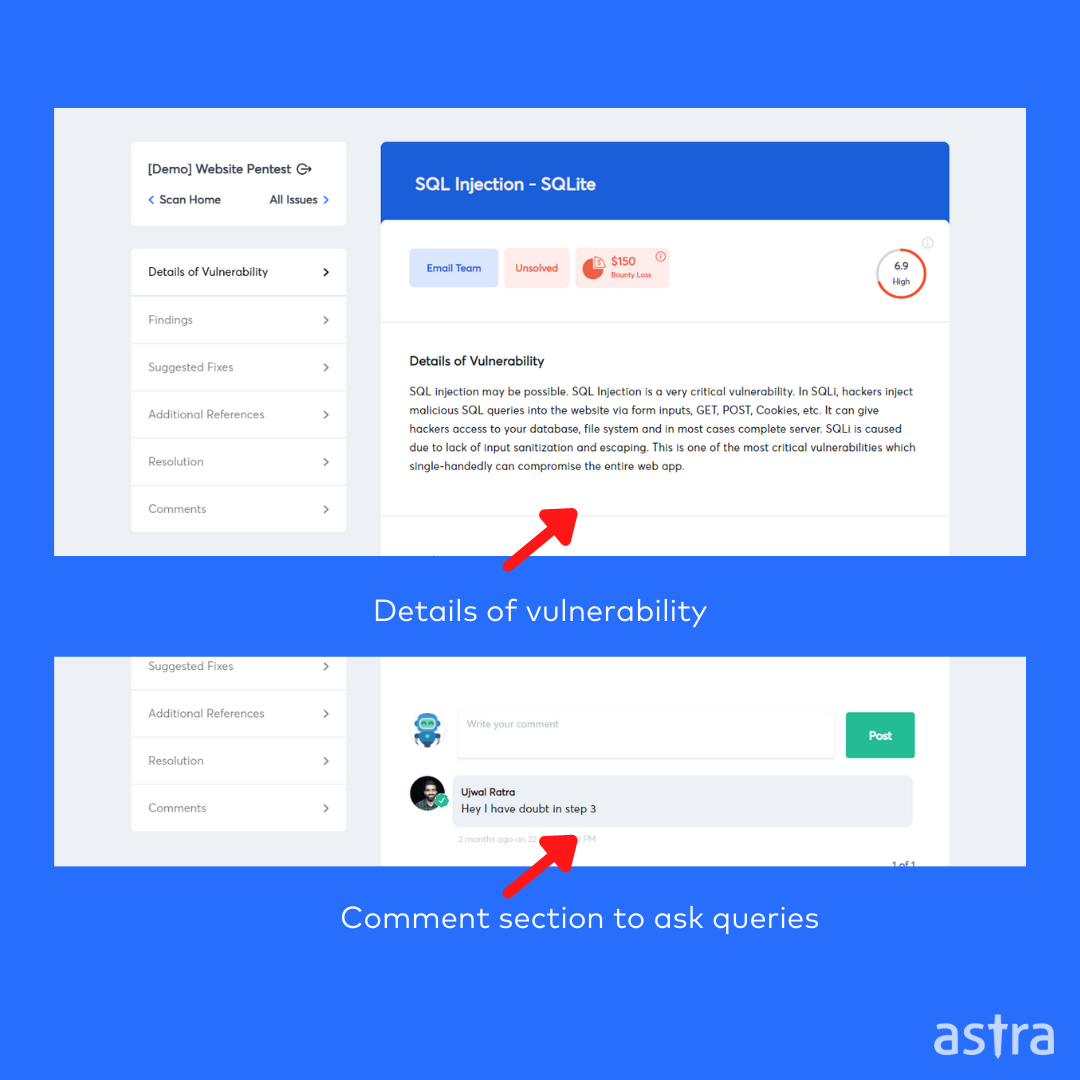
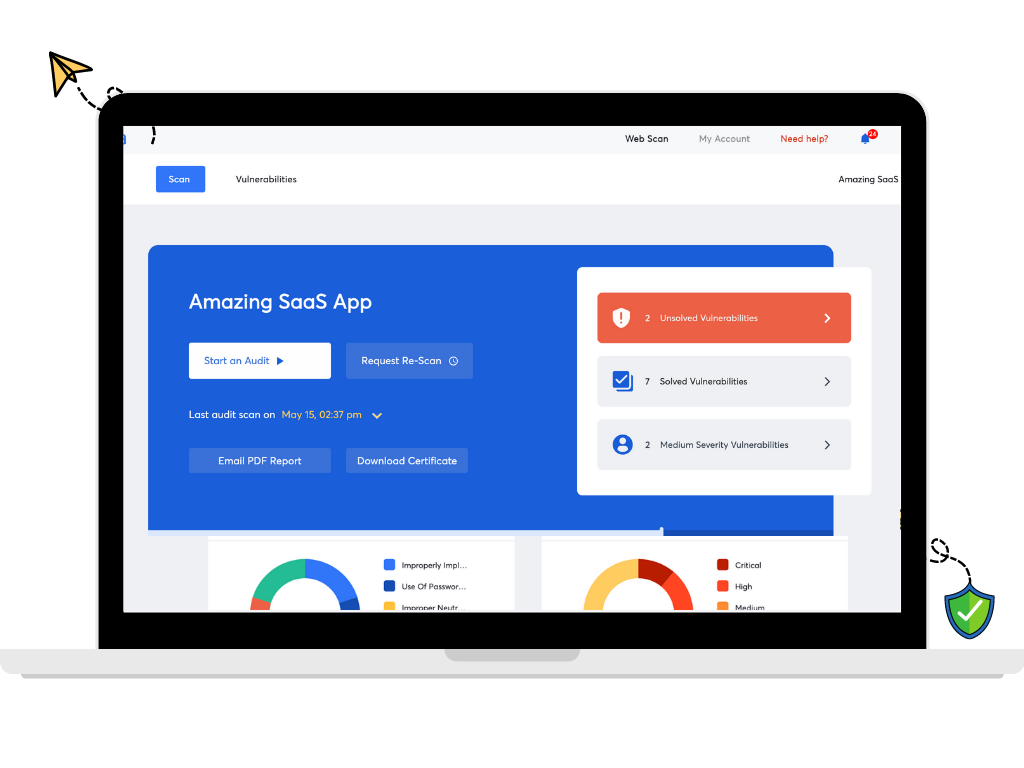
An alternative way to collaborate is to collaborate over vulnerability management dashboards. It simplifies the whole process and cuts the remediation time for all the people involved. Here’s how collaboration works in Astra’s Pentest dashboard:
5. Remediation & Certification
Remediation & Certification is the last leg of SaaS penetration testing. Remediation here refers to the client fixing the reported vulnerabilities as per the steps to fix shared by the tester.
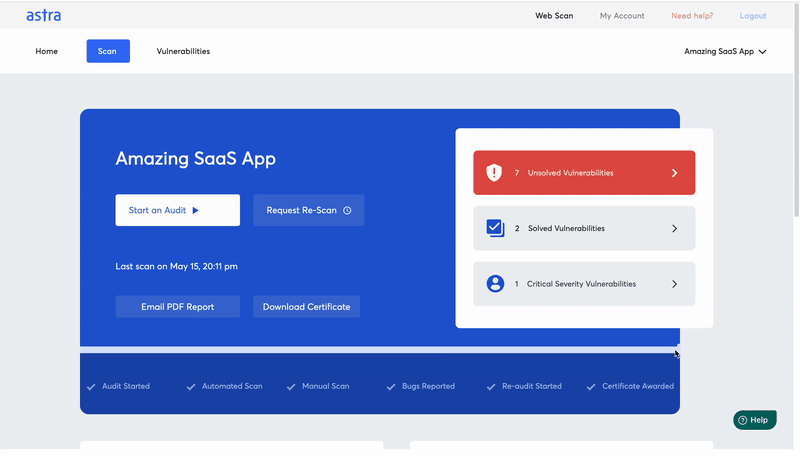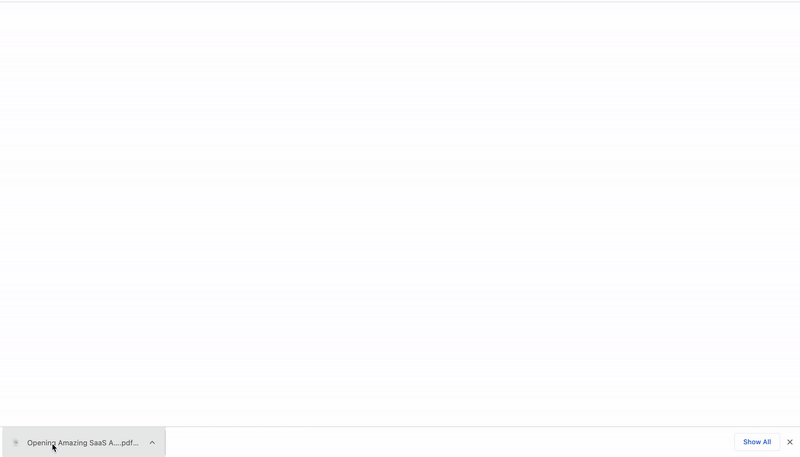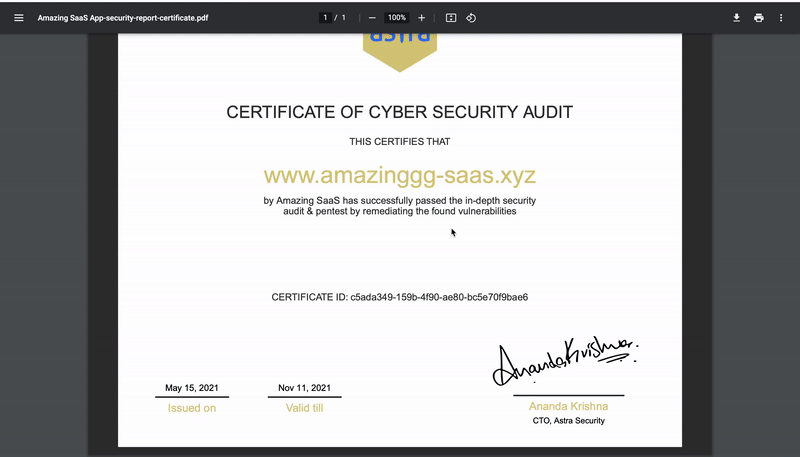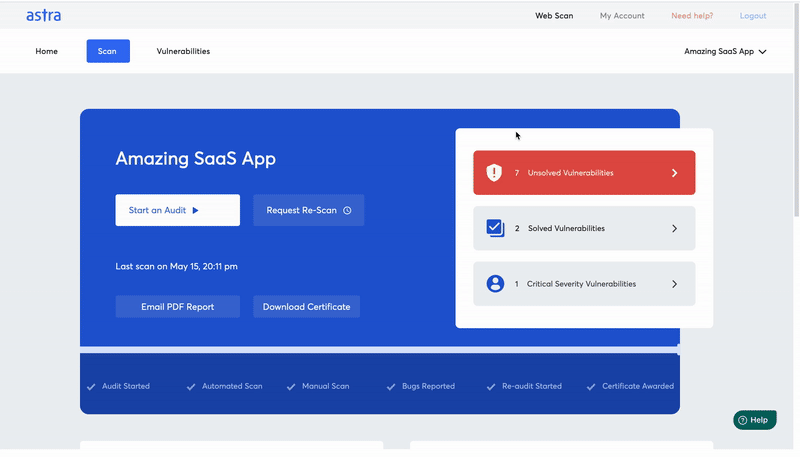
Next, the security team tests the implemented fixes and issues a certificate to the SaaS, if everything is alright. A sample penetration testing certificate by Astra Security is shown below.
Fun fact: You can also make the Astra Pentest certificate publicly verifiable so that your clients and partners can verify it. Helps in establish transparency & trust for your business 🙂
Related Read: 5 SaaS Security Certifications to Wrap Your Head Around
SaaS pentesting by Astra Security
Astra Security offers a thorough yet hassle-free SaaS penetration testing service with:
- Over 8000+ tests – manual & automated
- An intuitive pentest dashboard
- Real-time vulnerability reporting, management & collaboration for each vulnerability
- An on-demand vulnerability scanner (scan your application at your will)
- Direct collaboration with security experts
- Detailed reports
- Pentest certificate, and more
Check out Astra’s SaaS Pentest for more information.
Conclusion
SaaS solutions are clusters of complex systems & functions. Given the massive adoption of cloud-based saas solutions, paying attention to the associated cybersecurity risks to these services has become more than necessary. SaaS penetration testing helps you identify underlying security vulnerabilities in your saas solution. Asking the right questions while choosing a saas penetration testing service can save you from unpleasant and non-intended outcomes. It also sets the correct expectations for you and the pentester.
At Astra, we have helped hundreds of SaaS businesses successfully find and fix critical vulnerabilities in their SaaS infrastructure. We can help you in making your SaaS business more secure. Let’s talk?
















