Article Summary
It’s true – even the pandemic has not been able to slow down the terrifying rate at which more people are being hacked – in fact, since the world has had to move online, there have been more hacks. This means that everyone has to learn about good security practices to stay safe online. One such practice is to conduct regular security audits – read on to find out how you can do it yourself for your SaaS application.
SaaS security audits are growing more and more important by the day, as hackers are finding clever new ways to exploit websites and applications – especially those of small and medium businesses. Unfortunate as it is, such businesses are often an easy target for people with malicious intentions, as the security practices in such businesses are not paid much attention to, or ignored altogether.
What is a SaaS Security Audit?
To ensure that the data on your SaaS platform remains safe, secure, and private, you need to assess a few things about your organization’s security practices. This covers everything from your employees’ security habits to any vulnerabilities present in the software.
This whole process, after which you can identify vulnerable areas and begin to fix them, is known as a SaaS security audit. A good way to ensure that you are less likely to get hacked is to regularly conduct such audits.
How can you conduct a SaaS Security Audit?
There are a few things to do before you conduct an audit – namely, do some preliminary research about your platform, and make sure that your platform meets the SaaS Considerations. Then, you can follow these broad categories as convenient:
1. Make sure your employees are security smart
The security practices of your organization’s employees make a world of difference to your overall security. By ensuring that every person has their own accounts (follow the principle of least privilege to decide how to assign permissions), uses strong passwords that are regularly changed, and uses two-factor authentication.
Finding out how security-aware your team is a good foundation for a SaaS security audit. This can also help you decide whether you need to conduct specialized security awareness sessions for your employees.
2. Assessing your customers
Protecting your customers is essential. Making sure your customers are security-aware can ensure that they can deal with security incidents better. You can also enforce two-factor authentication to uphold security.
Assessing your customers’ awareness during a SaaS security audit would help paint a clearer picture of your security scenario.
Read Also: SaaS Security Assessment: Important Tips & 7 Best Practices
3. Making sure data is protected
Data is next, and it is one of the most critical components of a SaaS security audit. Data is usually in one of three different states, and each one of them has a different level of vulnerability and needs to be secured in a different manner.
1. Data at Rest
Data stored on your cloud is at rest, and this is a relatively secure state. Here, information is primarily protected by defenses such as firewalls and anti-virus programs. However, you would need additional layers of defense to protect sensitive data from intruders in the event of a hack.
Another good security practice is to store individual data elements in separate locations to decrease the likelihood of attackers gaining access to all information at once.
2. Data Being Used
Data that you’re currently using is more vulnerable than data at rest because, by definition, it must be accessible to those who need it. The more people and devices that have access to the data, the greater is the risk that it can be compromised. The key to securing data in use is to authenticate and control who has access to it. Make sure you can track and report any relevant activity which might mean that your data is in danger.
3. Data in Transit
Data is at its most vulnerable when it is in motion. Anyone with the right tools can intercept your data as it moves from source to destination. The best way to ensure that your data remains confidential is to transmit it through an encryption platform that integrates with your existing systems and workflows.
In addition to the above points, you might want to ensure the following too:
- Data is validated and sanitized upon entry: Data that has not been validated or sanitized can lead to a lot of dangerous attacks – most commonly, injection attacks. Make sure you check this during your audit.
- All data is encrypted: All data coming in and going out must be segregated meaningfully and encrypted separately and securely. The encryption keys must be handled carefully, too.
- Data is protected and has a well-tested recovery plan: Data security must be carefully monitored. Even in the case of data loss, you should have a great, foolproof Incident Response plan.
- There is a strict data retention policy: This is extremely important. This way, not only do you free up space you can use for your backups, but also makes your users feel more secure sharing their data with you. You can’t lose it if you don’t have it.
Read also: 8 SaaS Security Solutions You Can Count On
4. Following secure coding and secure software development life cycles
Your code is one of the most important facets of your security, so make sure to assess it during your SaaS security audit. Secure code definitely helps in taking your security to the next level. By shifting the security earlier to the development stage, you can easily detect potential vulnerabilities or weaknesses in your applications early in the life cycle, and build a secure application.
To effectively measure code quality, one needs to look at it under four different measures – reliability, efficiency, security, and maintainability. Following are some points you should keep in mind while conducting an evaluation of your code:
1. Reliability
- You need to ensure the protection of state in multi-threaded environments.
- Check for the safe use of inheritance and polymorphism.
- Analyse the resource bounds management and complex code.
- Look at how allocated resources and timeouts are being managed.
2. Efficiency
- Make sure the code complies with the best practices of Object-Oriented Programming.
- Check if the best database and SQL practices are being followed.
- Look for and evaluate expensive computations in loops.
- Analyze static connections versus connection pools.
- Ensure that the best garbage collection practices are being followed.
3. Security
- Check for the use of hard-coded credentials.
- Look for any buffer overflows.
- Also, look for missing initializations.
- Make sure all array indices are properly validated.
- Look for and ensure proper locking.
- Make sure there are no uncontrolled format strings.
Also Read: Security Audit Services: Importance, Types, Top 3 Companies | Security Audit Company and Services [Top rated]: How to Pick
4. Maintainability
- Make sure the code is well-structured.
- Analyse the cyclomatic complexity.
- Analyse the level of dynamic coding.
- Look for and control the over-parameterization of methods.
- Look for any hard coding of literals.
- Check and manage excessive component size.
5. Ensure that applications are deployed safely
Another great place to audit is the platform used to deploy your application. Established SaaS vendors like Amazon and Google go to great lengths to ensure security, and you can also come up with a checklist to make sure that appropriate safety measures are taken and safety standards are followed.
6. Ensure compliance with standards
Make sure your application complies with well-known security standards. You may make a checklist of all the compliances and check and test them accordingly – this may even help set a procedure for conducting your SaaS security audit.
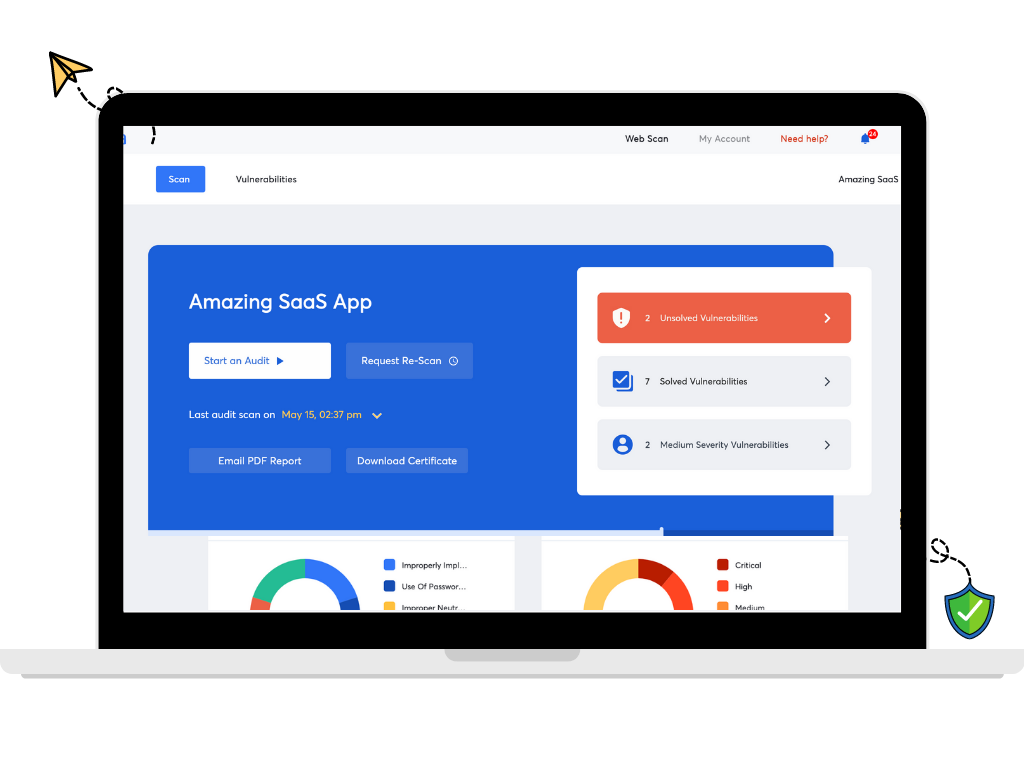
You can also get a professional security team to conduct a security audit. Astra Security’s engineers quickly audit your application and also help your development team patch them. At the end of the process, you are issued a safe-to-host certificate that you can proudly display. After all, such a secure application does call for some bragging!
Also Read- SaaS Penetration Testing | 10 Best Cyber Security Audit Companies [Features and Services Explained]
7. Invest in security resources
Whether in-house or external professionals like Astra Security to conduct your SaaS security audits, investing in security teams is always a good idea (not just hassle-free), and it is one of the only tried-and-true methods to make sure you never get hacked.
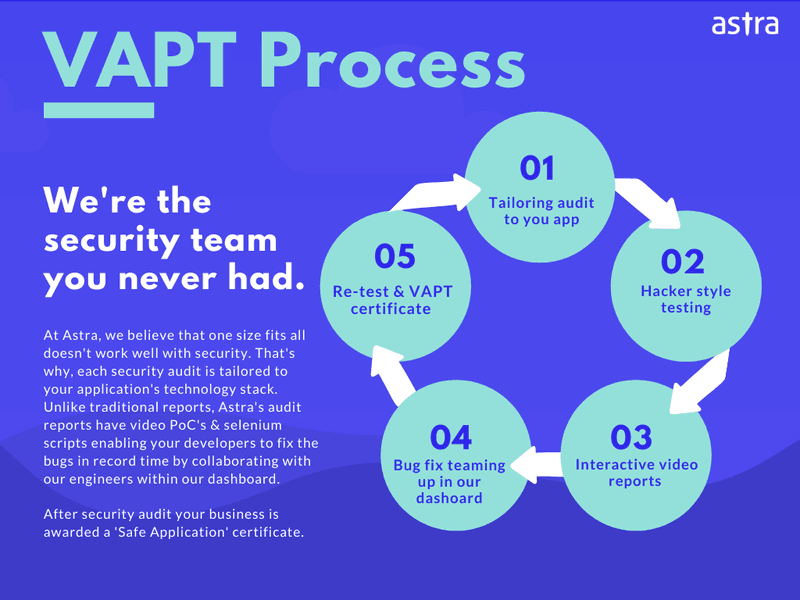
SaaS Security Audit: Conclusion
A SaaS security audit is essential to protect your application from hackers. You can conduct it yourself in the 7-step procedure given in the article, but for a truly hassle-free experience, it is recommended that you get Astra Security – with round-the-clock professional support, you can rest easy knowing you’re in good hands.
















