India is one of the fastest-growing digital markets in the world with close to 800 million internet users. It is home to the third-largest number of Internet users in the world, after the US and China. Eyeing the huge consumer base that India presented, Internet-based services flooded in India. Even the orthodoxical industries which functioned largely on manpower earlier joined the digital bandwagon in order to stay relevant in the changing times.
The ballooning Indian digital market also caught the eyes of cybercriminals. And as India moves further ahead on the path to digital transformation, threats to its different economic sectors rise simultaneously. So much so that, the average cost of a data breach rose by 7.9% to INR 119 million since 2017, a report by DSCI said.
Further, a presentation by the NITI AAYOG underlines the biggest victims of these data breaches as financial organizations, healthcare, public sector, and retail & accommodation, with most breaches (~24%) targeted at the financial sector.
Commenting on the dire situation of cyberattacks in India, National Cyber Security Coordinator Lt Gen (retd) Rajesh Pant said “cyberattacks have gone up manifold and every day, four lakh pieces of malware are found and 375 cyberattacks are witnessed”.
To put it simply, the situation is alarming.
The Indian government and stakeholders who were exploring ways to fight off the rising threat landscape, zeroed in on regulatory norms and guidelines for all services operating in India, putting a more stringent focus on BFSI (Banking, Financial sector & Insurance) and government sectors.
These stringent regulations forced organizations to take due cybersecurity steps to combat cyber attacks. This accelerated the demand for cybersecurity products, consulting, and security testing in India.
“It is estimated that the security testing services market in India would increase from USD 201 million in 2019 to USD 325 million by 2022, at a CAGR of 17.4%. Security testing services will comprise 23% of the services market share, as against 21% share in 2019.” reads the report by DSCI.
Whereas a Statista report foresees the cyber spend in India to cross USD 3000 million by 2022!
Further, security testing in India is expected to grow at the fastest rate with a predicted CAGR (Compound Annual Growth Rate) of 17.4% in 2022.
What is Security Testing in India?
Security testing encompasses the process of auditing and reviewing the current security posture of an organization to identify hidden security flaws and vulnerabilities in the system and recommending ways to patch them in order to achieve the most secured posture for the organization.
In other terms, security testing is a method to identify and rectify vulnerable points in a system (usually includes — website, mobile, IoT, network, etc.) in order to formulate an efficient & standardized security system for the organization.
Security testing is usually done by a certified security professional or service provider who, in layman’s terms, tries to hack your system or software to find security gaps and reports it so that the organization can work towards fixing those security gaps and make an informed decision in instituting the right security system for itself.
Security testing in India can have starkly different results with different types and methodologies of security testing. Depending on the requirement of a company’s specific needs and goals, security testing can follow different approaches like – White-Box security testing, Black-Box security testing, and Grey-Box security testing. The tests involved in security testing may also differ from organization to organization.
Take, for example, a financial institution that may also require payment gateway testing, whereas a telecom sector may stress more on network testing instead of payment gateways.
Common security testing goals that intersect with most organizations:
- To identify security bugs, missing security rules, configuration flaws, endpoint access, and other potential vulnerabilities in a system.
- To get security attested to comply with government mandates and regulatory bodies norms.
- To formulate an optimized security system for their organization and so on.
What Makes Astra the Best VAPT Solution?
- We’re the only company that combines automated & manual pentest to create a one-of-a-kind pentest platform
- The Astra Vulnerability Scanner Runs 8000+ tests to uncover every single vulnerability
- Vetted scans to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities
- Astra pentest detects business logic errors and payment gateway hacks
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

Types of Security Testing in India
Security testing is a broad term that encompasses different auditing & analyzing tools, testing methods, and type of tests. These types though come under the umbrella term ‘Security Testing’ can mean different things from what we normally understand as Security testing. They also deliver different results and have different end goals. The costs of these security testings vary as well.
Hence, it is very important to understand these terms in their correct sense and match them with your organization’s security testing requirements before making a choice.
Here are the main four security testing types:
1. Vulnerability Scanning / Assessment
Vulnerability scanning is largely an automated test and is the first kind of security testing. It involves security tools and scanners that run several tests and find out basic security issues such as outdated versions, misconfigurations, etc.
With the right tools and set up you can conduct vulnerability scanning yourself.
However, the results of vulnerability scanning are not very deep-seated. So if you’re looking to test your application in the most thorough form, doing vulnerability scanning for your application or system is just scratching the surface. That said, you can always make it a part of the more intense security testing.
Related Guide – How to conduct Website Penetration testing | 11 Top Penetration Testing Tools/Software of 2022
Vulnerability Assessment, although entails the same process, is usually used as a base-setter for holistic penetration testing. One key difference between vulnerability scanning and vulnerability assessment is that the latter can also include manual work, which is normally missing in scanning.
2. Penetration Testing
Penetration testing is the process of uncovering potential security risks in a system by trying to bypass security rules imitating a hacker’s approach. It is usually a manual, intricate, and slow process as compared to instant vulnerability scanning. A penetration test can take days or even weeks to complete and covers every aspect of the application as defined and agreed upon by the pen-tester and the stakeholder. The results of penetration testing are more detailed and reported in a way that the owner can take remediation steps based on that.
3. Red Team testing
Red Team testing is somewhat similar to penetration testing. It also reveals the hidden vulnerabilities in an application in a simulated attack and can take days to complete. The main difference between penetration testing and Red Team testing lies in the fact that Red Team testings are not always holistic. That is, they may not test every aspect of an application for issues. Rather, they focus on one end goal and try to penetrate into the application to achieve that. The results of a Red Team testing are not very detailed and actionable.
4. Purple Team testing
Purple team testing is a balanced test between the exploit and defense. It is conducted with a goal to build a security guard for the vulnerable areas the red team testing highlights. Since it is an amalgamation of Red and Blue team testing, hence the name Purple. A purple team testing is more fruitful compared to a Red team testing because it also includes a call to action or remediation to be taken at the end.
Also Read: Security Audit Company and Services [Top rated]: How to Pick | API Penetration Testing: What You Need to Know
Tests and methodology
As we already discussed, methodologies and tests may differ while performing security testing depending on the specific requirements of an organization and application. We tried to segregate the tests according to the type of application and here they are:
Tests for Websites/Web Applications
- Static & dynamic code analysis
- Server infrastructure testing & DevOps
- Tests to identify the loopholes in the business logic
- Authorization checks for user access (UAC)
- Manual & automated application scanning
For e-commerce websites, tests around payment gateways can also be included.
Related Guide- Online Website Security Testing | Top 5 Software Security Testing Tools in 2022 [Reviewed]
Tests for Mobile Applications
- Proxy interception to analyze the incoming & outgoing packets of the app
- Source code analysis
- Data storage and encryption
- Identify application’s data store (at rest, in transit or on display) and sensitivity
- Tests on different user roles, access points, etc.
Related Guide – Mobile Application Security Testing
Tests for API Security
- Tests to identify data leakage
- Unauthorized access check
- Fuzzy input check
- Tests for common vulnerabilities, parameter tampering, etc.
- Data validation testing
- Access permissions check
- IDOR (Insecure Direct Object Reference) check
Related Guide – API Security Audit
Tests for Cloud Infrastructure
- Configuration review of the environment
- Reviewing Identity and Access Management (IAM) users, groups and roles
- Managing the access control on the cloud EC2, SNS, RDS
- Security configuration review
- Reviewing other AWS policies for: S3 Bucket SQS queue KMS keys
- Reviewing data protection & encryption
Also Read: Cloud Security Audit: Everything You Need to Know |
Tests for Network Devices – Firewall/Routers/Printers
- Check if all the endpoints of devices are protected with authentication
- Security policies & architecture review
- Do authorization checks for user access (UAC)
- Network data review
- Evaluate the policies for remote access, etc.
- Reviewing network strengths against common attacks
Related Guide – Network Penetration Testing
Security certificates in demand and how to get them
To oversee secure operations on the online platform, regulatory bodies have been constructed. These authoritative bodies have put in effect rules and guidelines for companies to follow. Some rules are more strict than others. Also, not all rules are applicable to all industries. There are rules that apply to the healthcare sector and then there are others that are applicable to the financial sector. Compliance also varies according to geographical locations. For instance, the European continent follows data privacy rules in the form of GDPR, whereas America falls under the compliance of CCPA.
Here we are only mentioning the certificates which are in demand across the world:
Also Read: 10 Best Cyber Security Audit Companies [Features and Services Explained]
Download and Verify VAPT certificate
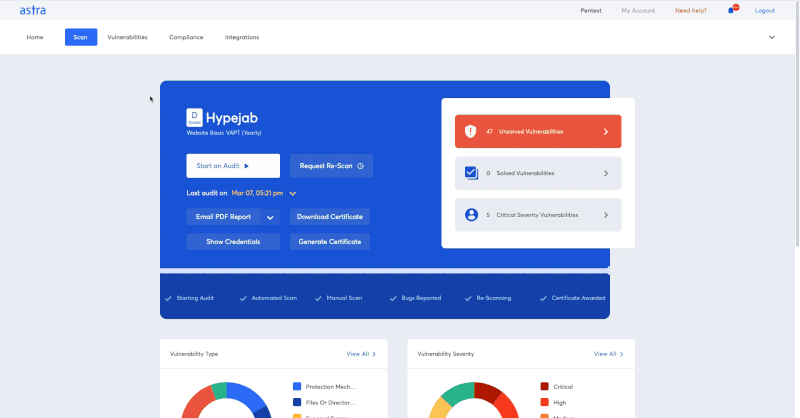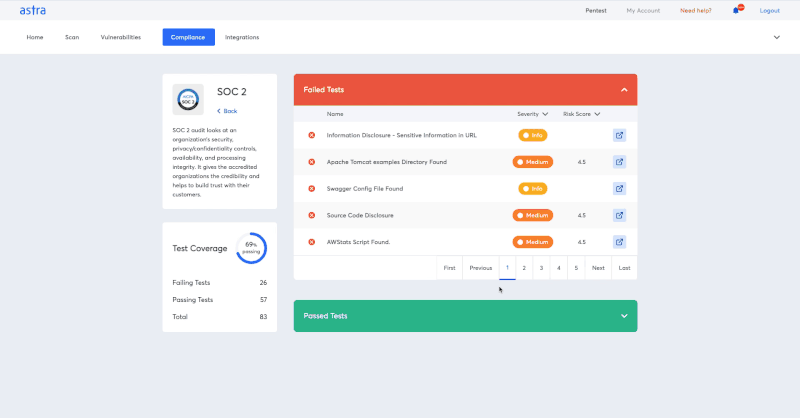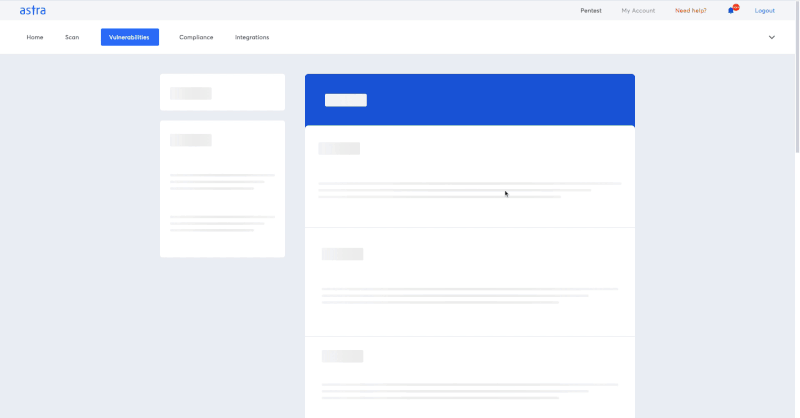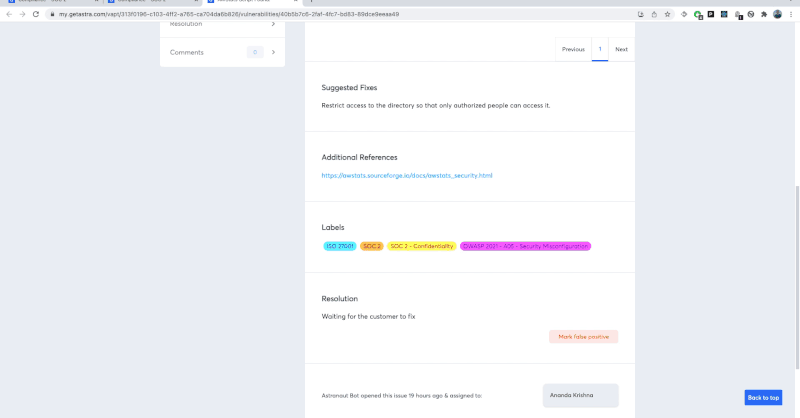
A VAPT certificate attests to the fact that your application has been tested and rectified. Any trustworthy VAPT service provider can certify your organization with a VAPT certificate. It can also help you achieve certain data privacy compliance and help build customer trust while using your secured applications. You can directly download and verify your VAPT certificate within Astra’s Security Scan dashboard itself. Check out what Astra’s VAPT certificate looks like:
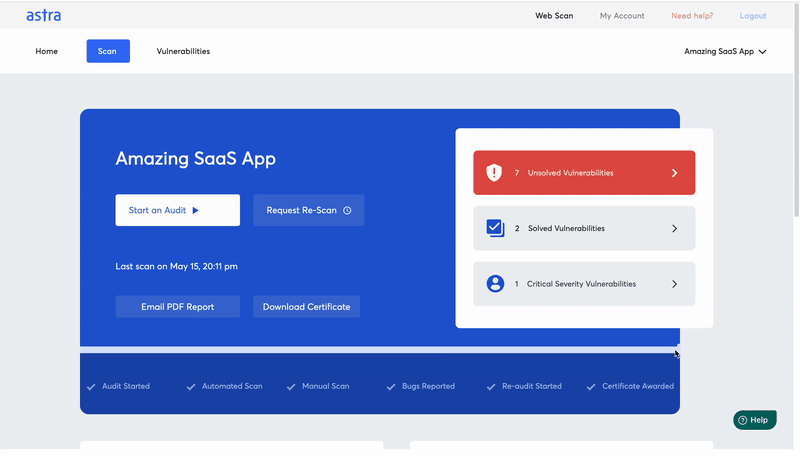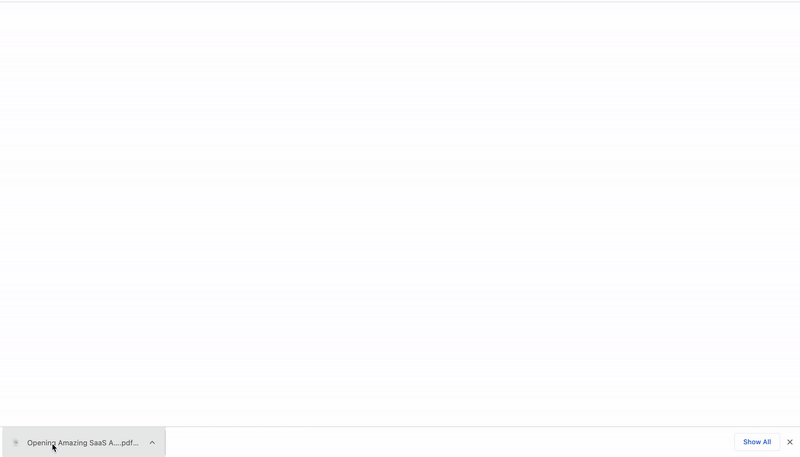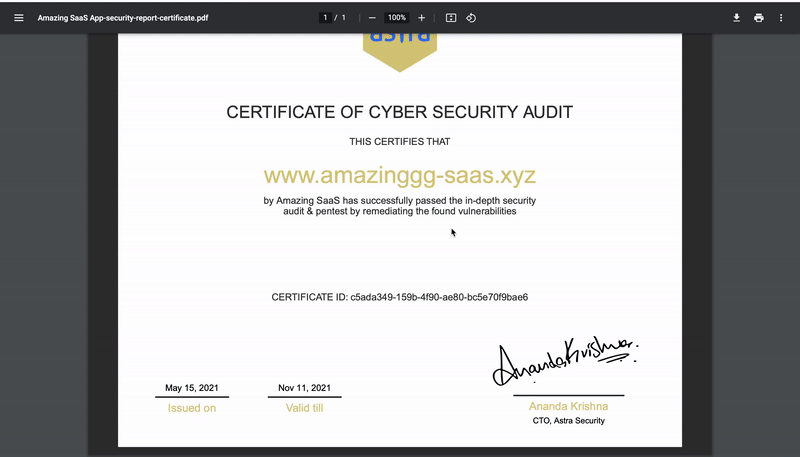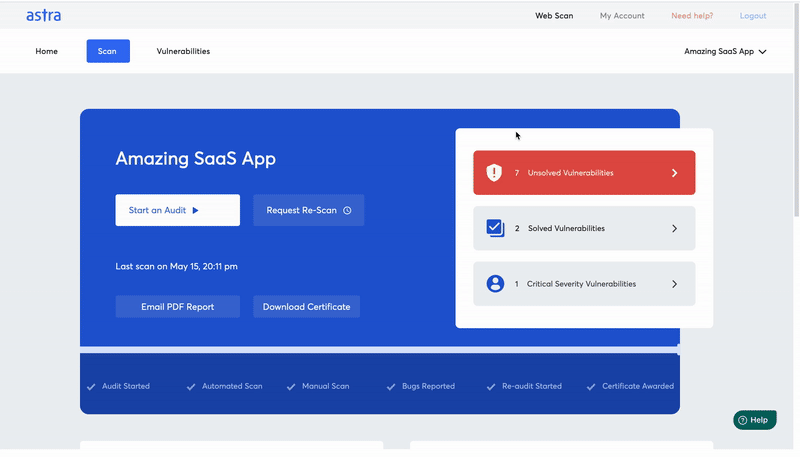
Safe to host certificate:
Safe to host certificate is an X.509 certificate that assures security between the client and service communications. Mainly hosting companies need to acquire a ‘Safe to host’ certificate. You can get ‘Safe to host’ certified by submitting a formal request to the Certificate Authority (CA). Credible security service companies like Astra Security can also issue ‘Safe to host’ certificates to hosting companies after conducting a VAPT.
HIPAA
HIPAA stands for Health Insurance Portability and Accountability Act. HIPAA is a 1996 American Act that binds the US healthcare sector to follow secure data security & passage procedures to help battle the prevalent cybercrime in the sector. To become HIPAA certified, a healthcare facility needs to undergo security testing to fortify itself from vulnerabilities.
CERT-IN Certificate
CERT-IN (Indian Computer Emergency Response Team) is an Indian government body that falls under the Indian Ministry of Electronics and Information Technology. It is a nodal agency whose job is to handle cybersecurity incidents, issue alerts & advisories, and collect data & analyze cyber incidents. You can proclaim a CERT-IN certificate by getting security testing from a CERT-empanelled security service provider.
PCI-DSS
The Payment Card Industry Data Security Standard is another compliance that is meant for any organization that processes or interacts with credit card data. More details about the PCI-DSS compliance are given here.
GDPR
GDPR, General Data Protection & Regulation Act 2016, is a European Union regulation that requires businesses to protect the personal data and privacy of EU citizens. Any business that operates in the EU member states or has a European consumer base comes under GDPR compliance. GDPR protects the privacy of personal data like an individual’s IP address, cookie data, location, RFID tags, biometrics, political opinions, PII, health and genetic data, financial data, and so on.
GDPR implementation is unique to each organization. To become GDPR compliant understand the regulatory framework and understand how that applies to your business and act accordingly.
Astra Security is a GDPR-compliant company and helps other businesses comply with GDPR with its ready-to-use cookie consent bar.
ISO27001
ISO27001 (formerly known as ISO/IEC 27001) is an international standard on how to manage security with the information security management system (ISMS) framework. An ISMS framework consists of a certain set of policies and procedures which is followed by an organization in their information risk management processes.
The ISO 27001 compliance standard has a special clause for vulnerability assessment and penetration testing. This clause also helps while defining the scope of VAPT for the ISO27001 compliance. We at Astra Security follow this standard and perform assessments accordingly. Astra VAPT dashboard displays vulnerability discoveries, fixing recommendations, and a final report that you can send to your ISO auditors for achieving compliance.
Besides these, there are a few other compliances such as RBI ISMS policy for banking, NBFCs & fintech companies, SEBI ISMS policy for brokers & other registered share transfer agents, SOC, and so on.
Cost & Timeline of a Security testing in India
Cost
A rough estimate for security testing in India will lie in the range of INR 35,000 to INR 2,00,000. Since security testing depends on a number of other things like scope, no. of applications, APIs, etc., the cost is subject to change.
Timeline
A full-fledged security testing in India can take a couple of days to a few weeks to complete. Again, timelines vary according to scope, number of applications, depth of the audit, and several other things.
How can Astra Security help?
Astra Security has carved a niche for itself in providing advanced security testing in India with its VAPT (Vulnerability Assessment and Penetration Testing) program.
Our certified security professionals uncover loopholes in your application with the right mix of automated & manual security testing. Each audit is tailored to the technology stack of your application and follows the global security testing standards as dictated by OWASP, SANS, CERT, PCI, ISO27001, and others.
We have a clear and crisp security audit dashboard that lets you/your developer collaborate directly with the tester on the reported vulnerabilities. This dashboard lets you see the vulnerabilities being reported live.
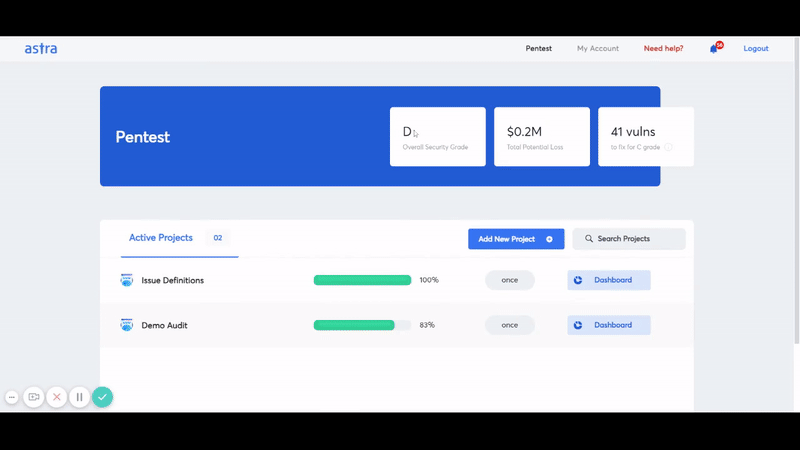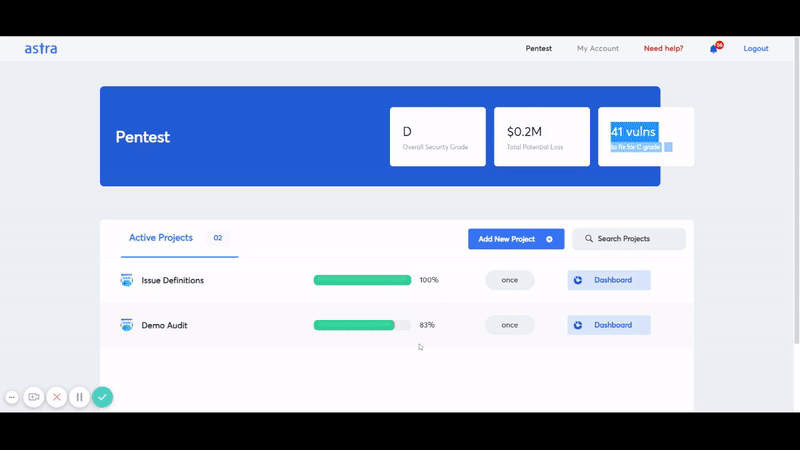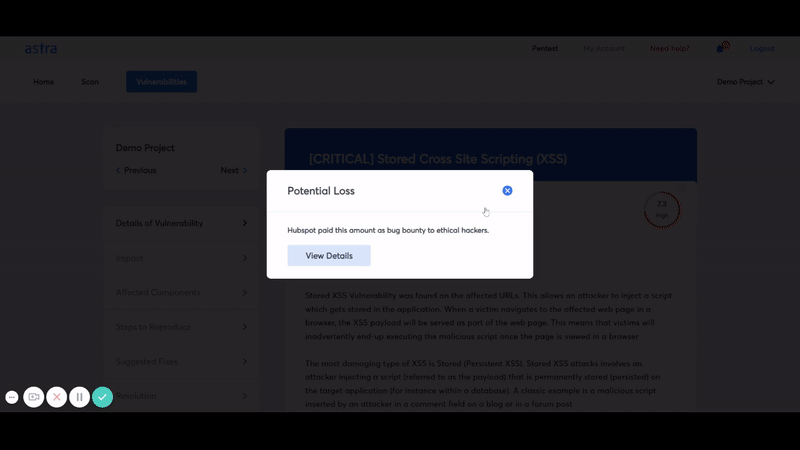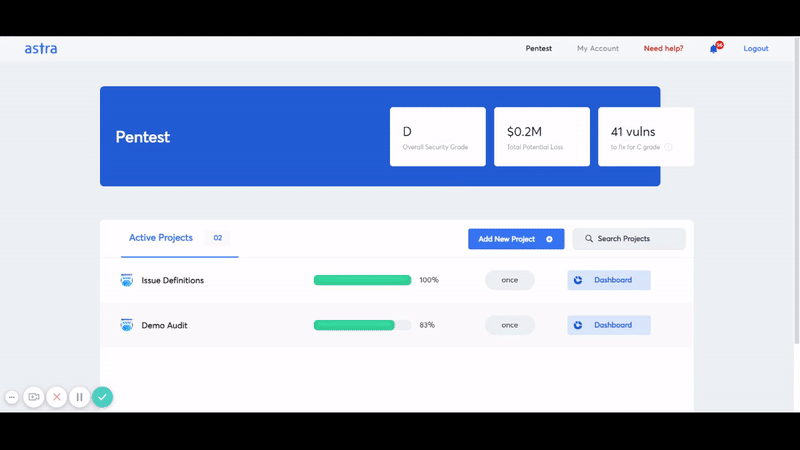
You also get video PoCs and selenium scripts in order to reproduce the vulnerabilities. In effect, this means you can go ahead with the remediation parallel to the VAPT and save precious time.
When your developers have patched the issue, they can raise a re-test request and our security team would be happy to comply.
We follow an upfront process and a documented methodology. The following picture will give you a basic idea of our VAPT process:
Our VAPT offering comes in three different plans: Basic, Expert & Elite. The cost of each plan varies with frequency.
To Conclude…
Online threats are getting more sophisticated and so should your defense. Get security testing done for your business and eliminate all traces of security risks from your application.
















