With an 8+ Trillion dollar plus economy, cybersecurity threats are on a rampage. But even the most vigilant companies, religiously following best practices, still face risk. So, how can you eliminate risk? Simply put, the risk can’t be eliminated, but it can be minimized.
That’s where security audits come in. Think of them as a controlled “hack” that exposes vulnerabilities before real attackers do. They’re not just about compliance – they empower you to patch the holes in your website’s defences before a breach occurs with systematic assessments and mitigation of the vulnerabilities in a web application.
What is a Website Security Audit?
A website security audit is a process that evaluates your websites and infrastructure for vulnerabilities and loopholes. A thorough audit typically involves static and dynamic code analysis, business logic error testing, and configuration tests uncovering potential entry points for attackers through software vulnerabilities and misconfigurations.
The most reliable security audits use both automated tools and human acumen. The ideal VAPT program is not just tailored to your tech stack but uses advanced security tools, expert vigilance, and professionally performed manual testing to conduct end-to-end website security auditing and vulnerability management.
How is a Security Audit Different From a Penetration Test?
| Security Audit | Penetration Test | |
|---|---|---|
| Focus | Aims to identify vulnerabilities, weaknesses, and entry points. | Aims to exploit the found vulnerabilities, weaknesses, and entry points |
| Methodology | Uses tools like vulnerability scanners, code analyzers, and configuration reviews. | Uses tools and techniques used by real-world attackers. |
| Approach | Follows defined guidelines to cover every aspect of the application. | Manual testing and thorough exploitation of weaknesses in the application involve creative thinking |
| Outcome | Provide an overview of the web application security. | Evaluate the effectiveness of security controls by trying to breach them. |
Real-World Examples of Most Common Web-based Vulnerabilities
Injection Attacks
Injection attacks like Cross-Site Scripting(XSS) and SQL Injection are the most common vulnerabilities in a web application.
Since November 2023, a threat actor group, “Resume Looters” has been actively targeting job listing sites with SQL Injection and Cross-Site Scripting attacks. The attackers have leveraged this vulnerability to steal the personal data of over 2 million job seekers.
Cloud Environment Loopholes
Ever since the rise in cloud-hosted applications, hackers have been targeting vulnerabilities that arise due to misconfiguration in cloud systems.
The Capital One data breach in 2019 is a great example of cloud-based vulnerability exploitation. Due to a misconfiguration in Capitol One’s AWS infrastructure, hackers could leverage a Server-Side Request Forgery (SSRF) vulnerability to steal confidential data of over 100 million customers.
Know Vulnerabilities (CVEs)
Hackers are well-known to use the CVE index to exploit vulnerabilities in various software and services.
In March 2024, Korean threat actors exploited a vulnerability in the ConnectWise ScreenConnect software using CVE-2024-1709, an authentication bypass vulnerability. Attackers exploited this flaw and gained unauthorized access allowing them to perform a Remote Code Execution attack to spread malware.
Why is a website security audit important?
According to recent research from Verizon, web application attacks are involved in 26% of all breaches, making it the second most common attack pattern. Performing regular security audits on your web applications helps to:
1. Mitigate Risks and Improve Your Security Posture
A website security audit helps identify vulnerabilities in your infrastructure, code, and configurations. A proactive approach towards these issues can significantly reduce the risk of cyberattacks such as data breaches, malware infections, and hacking attempts.
2. Protect User Trust by Showing Persistence
Ensuring that the personal and financial information of the users is a top priority when interacting with your website. A security breach can erode that trust, damaging reputation and customer loss. Conducting regular security audits demonstrates your commitment to safeguarding user data, fostering trust, and maintaining a positive brand image.
3. Implement and Maintain Regulatory Compliance
Many industries are subject to regulations and standards related to data protection and security, where failure in compliance can result in legal consequences and financial penalties. A web security audit helps ensure that your website aligns with industry standards, keeping you compliant with relevant regulations and enhancing your credibility in the eyes of both customers and regulatory bodies.
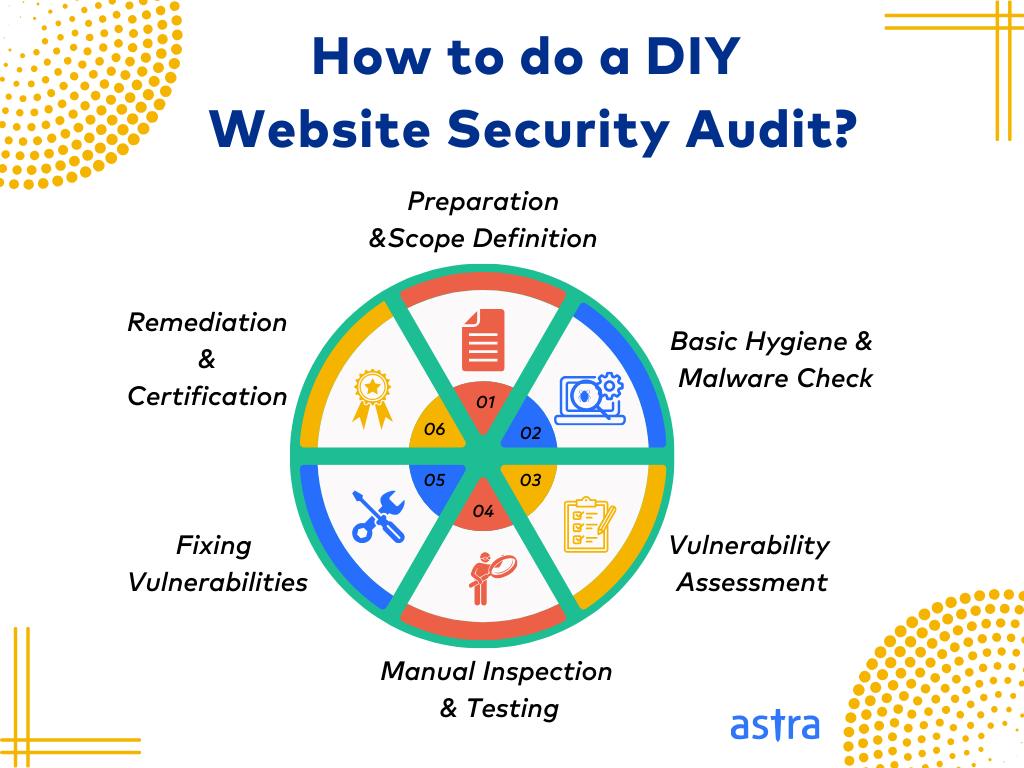
How to do a website security audit?
Step 1: Preparation and Scope Definition
Before diving into the audit, determine which aspects of your website you’ll assess, such as server infrastructure, application software, user authentication, data handling, and more. Identify the tools and resources needed for the audit, including scanners and relevant documentation access.
Pro Tip: Prepare a testing environment like a staging environment and testing credentials to conduct the audit without affecting the live website.
Step 2: Basic Hygiene & Malware Check
Perform a basic hygiene check on the web application to ensure all the best security practices are followed. These practices include enforcing proper encryption, implementing security headers, and checking SSL-related vulnerabilities. Tools like Astra’s security scanner or Mozilla’s Observatory can help you identify security gaps and Malware infections.
Step 3: Vulnerability Assessment
Conduct a thorough vulnerability assessment using appropriate security scanning tools. These tools will scan your website for known vulnerabilities, outdated software, misconfigurations, and potential weaknesses. Vulnerabilities like SQL injection & cross-site scripting (XSS) are the most common vulnerabilities.
Step 4: Manual Inspection and Testing
Review the scan results and ask cybersecurity experts to manually perform a penetration test on critical areas of your website. Remember to examine user authentication and authorization processes to ensure secure access controls.
Step 5: Fixing Vulnerabilities
Once vulnerabilities are found and the mitigations are suggested, work closely with the development team to implement these patches and secure the web application. Prioritize the more severe vulnerabilities to mitigate the risk of their exploitation.
Step 6: Remediation and Certification
Perform a final assessment of the web application to make sure all the patches are in place and implemented properly. Get the cybersecurity experts to issue a certificate and badge for the application and increase the trust of your users.
After completing one audit, create an incident response plan and perform regular security audits to keep the web application secure.
Since conducting a website security audit is quite cumbersome, most companies prefer to outsource it to experts, regardless of their size. This allows your firm to save time while taking advantage of an external team’s expert knowledge. Multiple website security audit tools are available in the market; let’s take a deeper look.
Top 5 Website Security Audit Tools
1. Astra Pentest
Key Features:
- Platform: Online
- Pentest Capability: Continuous automated scans with manual tests
- Accuracy: Zero false positives
- Compliance: PCI-DSS, HIPAA, SOC2, and ISO27001
- Expert Remediation: Yes
- Integration: Slack, Jira, GitHub, GitLab, Jenkins, and more
- Price: Starting at $1999/yr
Astra’s VAPT Suite integrates the powerful, AI-driven Astra vulnerability scanner with expert manual penetration testing, ensuring compliance with industry benchmarks like OWASP TOP 10 and SANS 25.
With a portfolio of 9,300+ tests, vetted scans help guarantee zero false positives. In-depth pentests and custom AI test cases help identify unique attack vectors and business logic vulnerabilities like user privilege escalation.
What Makes Astra the Best VAPT Solution?
- We’re the only company that combines automated & manual pentest to create a one-of-a-kind pentest platform
- The Astra Vulnerability Scanner Runs 8000+ tests to uncover every single vulnerability
- Vetted scans to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities
- Astra pentest detects business logic errors and payment gateway hacks
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

2. Nikto
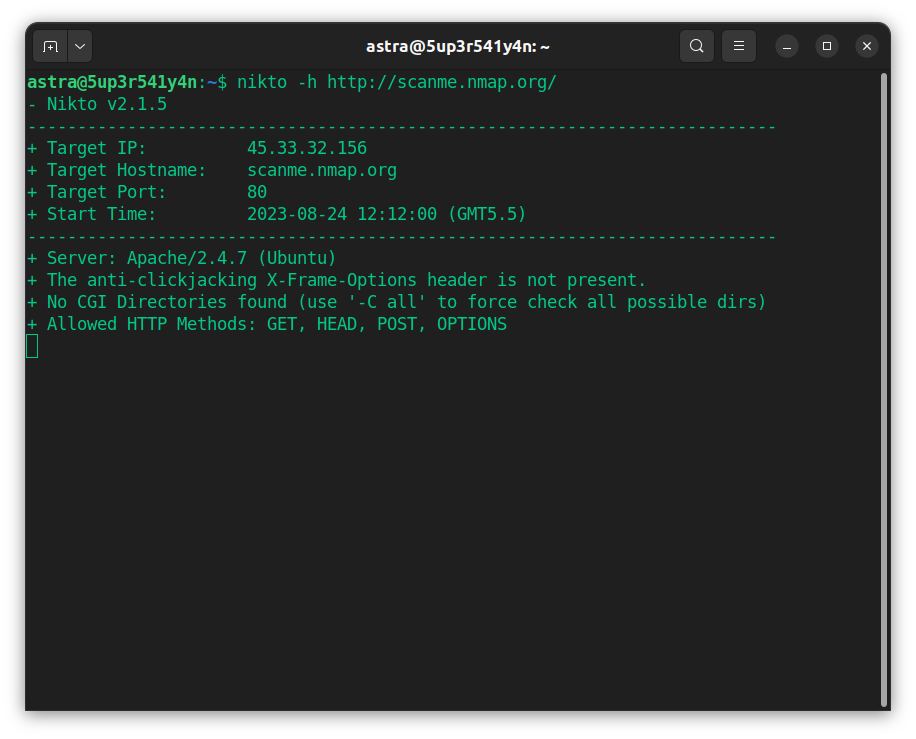
Key Features:
- Platform: Offline
- Pentest Capability: Automated Scans
- Accuracy: False positives possible
- Compliance: No
- Expert Remediation: No
- Integration: No
- Price: Open-Source(GPL)
Nikto is an open-source security solution designed to conduct thorough examinations on web servers, targeting a range of elements. It can detect over 7000 potentially harmful files and programs.
With complete HTTP support, it integrates a template engine that facilitates effortless report drafting and customization. It also comprehensively checks over 1250 servers for outdated versions.
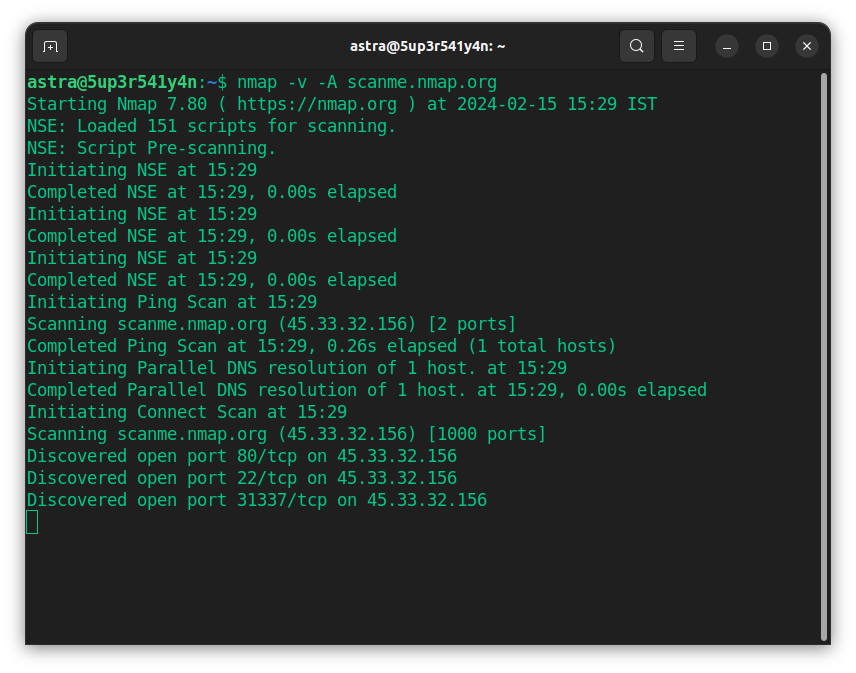
3. Nmap
Key Features:
- Platform: Across all OS
- Scanner Capacity: Network infrastructure, IoT devices, limited cloud instances
- Manual Pentest: No
- Accuracy: False positives are possible
- Vulnerability Management: No
- Compliance: No
- Price: Open-source tool
- Best Suited For: Network VAPT
Nmap, or Network Mapper, is a free, open-source tool for vulnerability assessment and network exploration. Network administrators frequently use this tool to determine the devices operating within their systems. It also helps pinpoint accessible ports and detect potential security loopholes.
4. Burp Suite:
Key Features:
- Platform: Windows, macOS
- Scanner Capacity: Web applications
- Manual pentest: Yes
- Accuracy: False positives possible
- Vulnerability management: No
- Compliance: PCI-DSS, OWASP Top 10, HIPAA, GDPR
- Price: $449/per user/per year
Burp Suite is a versatile cyber security tool for conducting web application assessments. It allows cyber security experts to perform in-depth testing and evaluate the web application’s security posture. Its scripted audits enhance the capabilities for conducting vulnerability assessments, and the large arsenal of tools allows advanced manual penetration testing.
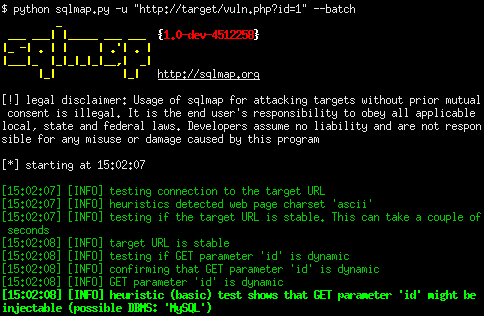
5. SQL Map:
Key Features:
- Platform: Across all OS
- Scanner Capacity: Web applications
- Manual pentest: No
- Accuracy: False positives possible
- Vulnerability management: No
- Compliance: No
- Price: Open-source tool
SQLMap is a free security tool that helps identify potential vulnerabilities to SQL injection. It boasts a resilient testing mechanism that accommodates various attacks and is compatible with several database servers, such as MySQL, Microsoft Access, IBM DB2, and SQLite.
What is a website security audit checklist?
A website security audit checklist is a structured list of tasks and best practices designed to assess and enhance the security posture of a website. Here are some basics to get you started in the right direction:
Vulnerability Assessment
- Regular scans/audits: Conduct regular security scans to identify vulnerabilities in your website, such as outdated software, plugins, and libraries.
- Severe Threats: Address critical vulnerabilities promptly to prevent potential exploitation.
Secure Authentication and Authorization
- Password Strengthening: Enforce strong password policies and encourage users to use unique, complex passwords.
- Multi-Step Authentication: Implement multi-factor authentication (MFA) with existing authentication to add an extra layer of security.
- Role-based Access Control: Review and restrict user access privileges to only necessary areas of the website.
Data Protection
- Encryption Standards: Use (SSL/TLS) to encrypt the data transmission between the user’s browser and your server.
- Input Sanitization: Implement proper data validation and sanitation to prevent SQL injection and other injection attacks.
- Continuous Assessment: Regularly review and audit sensitive data handling and storage practices to minimize the risk of data breaches.
Regular Updates and Patch Management
- Regular Updates: Regularly update the content management system (CMS), plugins, themes, and underlying server software.
- Regular Patching: Apply security patches as soon as they are released to address known vulnerabilities.
Security Monitoring and Incident Response
- Continuous Monitoring: Set up security monitoring tools to detect abnormal activities and potential breaches.
- Incident Response: Develop an incident response plan to take the necessary steps if a security incident occurs.
- Regular Log Review: Review logs regularly and monitor for signs of unauthorized access or suspicious behaviour. Understand the weaknesses and update your application’s security.
Final Thoughts
In our digital age, websites drive business interactions but are also vulnerable to cyber threats. To protect your business and customers from attackers, you need to find and patch your vulnerabilities at the earliest.
Website security audits can help you identify vulnerabilities and fortify your online presence. By taking the right steps, you can protect your reputation, user trust, and compliance status. If you want to hack your digital assets before hackers do, get it done by Astra.
Liked this article? Leave a comment below.

















Hi, I would like to know more about PCI Data security as I am going to start a online buisness soon.
Thanks for responding to the article. PCI DSS (as a shortcut of Payment Card Industry Data Security Standard) is a set of security policies and standards aimed at two main purposes. To know what they are, you can refer to this article: https://www.getastra.com/blog/knowledge-base/pci-data-security-standard/
Great article! Can you suggest me few tips on online buisness security that I should follow?
Thanks for responding to the article. Online business security is gaining its importance over time. With the growing digitization of the business, it is imperative to note that a compromise of the consumer’s data can lead to a $13 million loss to the firms annually. It is, thus, very important to ensure the online business security, if you are looking forward to sustaining. You can go through this article for more information: https://www.getastra.com/blog/knowledge-base/online-business-security-trends-2020/
hello, I am running a website (on wordpress) for a very long time and I have a concern about e-commerce fraud. How can I prevent that?
Thanks for responding to the article. WordPress is by far the world’s most popular CMS, and through plugins such as WooCommerce it can also serve as an excellent e-commerce system, but the easy setup isn’t a good indication of how easy it is to protect against fraud. The open nature of the system combined with the popularity actually makes it more vulnerable than comparable options. For more information check this link: https://www.getastra.com/blog/cms/wordpress-security/fight-fraudulent-transactions-on-wordpress/
Hi, are there any good password managers? I would like to protect my passwords from hackers.
Thanks for responding to the article. Security online is extremely important in times when hackers have become so powerful. Consequently, many business owners are looking for new ways to protect their personal data and particularly their passwords. Go through this link to see the best password managers suggested by us: https://www.getastra.com/blog/knowledge-base/best-password-managers/
Hello, Is there any use in investing a good VPN for my website? How important is it?
Thanks for responding to our article. Virtual Private Networks or VPNs have become a common tool for every privacy-conscious user. You can use them for many different purposes, and they genuinely provide you with unrestricted and completely anonymous browsing, something that is getting increasingly difficult to find today. For more information visit here: https://www.getastra.com/blog/knowledge-base/why-you-should-invest-in-vpn/
Hi, my blog is redirecting to strange websites and if its because of malware how can i fix this? I am using wordpress stack.
Thanks for responding to the article. WordPress redirect hacks have been a menace for such a long time now. It metamorphs itself into new redirect hacks every few weeks. We have been covering all those types of WordPress redirects as and when they come. Adding to the list is this blog post which uncovers yet another WordPress redirect hack type. This hack redirects blog page visitors to malicious domains. Click here for more information: https://www.getastra.com/blog/911/adaranth-wp-blog-redirection-hack/
Hello, strangely my website got blacklisted by Norton a couple of days ago. I am using magento CMS How can I get rid off this?
Thanks for responding to our article. A Magento blacklist by search engine means when a user searches for your website or any related keyword, your website will either not show up or show up with a warning page. Search engines continuously look for any malicious or harmful content on websites. Once they detect anything unusual or potentially harmful, the website will be added to a blacklist. For more information visit this link: https://www.getastra.com/blog/911/magento-blacklist-removal/
Glad that I came across such an important and productive content, I really appreciate your effort and I will definitely share it with my friends