Vulnerability scanning is a way of identifying the gaps in the security of your website, application, or network. The process is meant to find common, publicly recognized vulnerabilities in your system before the hackers do the same and exploit those vulnerabilities. We shall talk about five different vulnerability scanning types, and try to understand how each one can help us with security evaluation.
Five Types of Vulnerability Scanning
- Host-based vulnerability scanning Scanning of network hosts to find vulnerabilities.
- Network vulnerability scanning Vital scanning of an organization’s network infrastructure to find vulnerabilities if any.
- Database vulnerability scanning Scanning of databases where all confidential and application-related data is stored to detect any security risks.
- Cloud vulnerability scanning Refers to the scanning of cloud deployments to find flaws.
- Application vulnerability scanning Involves scanning web and mobile applications to identify security vulnerabilities.
What Are the Different Vulnerability Scanning Types?
We will talk about five different types of vulnerability scans and how they are used to assess different aspects of an organization’s cyber security. The types of vulnerability assessments that we will look at are host-based scans, network scanning, database scanning, cloud vulnerability scanning, and application vulnerability scans. Let’s dive right into the vulnerability assessment types.
1. Host-based vulnerability scanning
As you may be aware, a host is a device on a TCP/IP network that connects with other devices and sends and receives data. It can provide access to a network through a user interface, and specialized software, among other means.
In the open systems interconnection model, the host communicates with other hosts with transport layer protocols. For companies with a website, the host is a web server that stores and transmits data. If the company uses cloud hosting, then multiple servers located at different locations are responsible for the functionality of their website. Similarly, there are other virtual hosts and remote hosts. Our real concern here is host-based vulnerability scanning, so let us not delve any further into the particulars of hosts.
What is host-based security?
Host-based security refers to the creation of a perimeter around each user workstation, server, or other network hosts, that interact with the IT network. It means installing firewalls and intrusion prevention systems and patching up software on a regular basis to avoid vulnerabilities. host-based security not only prevents a host from being infected but also ensures that if a host is infected, it doesn’t spread the infection across the neighboring hosts.
What is host-based vulnerability scanning?
Host-based vulnerability scanning is the process of scanning a network host for security loopholes. A scan of this kind can reveal
- The history of security patches in said host
- Vulnerabilities incurred through outdated patches
- The damage that can be caused by the detected vulnerabilities
- The level of access a hacker can gain by infecting the said host
- Possible ways of mitigating the situation.
2. Network Scanning
This is one of the most vital among all the vulnerability scanning types. Network vulnerability scanning is the process of identifying the security vulnerabilities in an organization’s network infrastructure.
What does network vulnerability scanning entail?
- It Identifies all systems and devices operating in your network infrastructure
- Then it determines how the different devices and systems are connected
- After preparing an inventory of all the devices and systems under consideration, the scanner analyzes the said assets to detect common vulnerabilities.
- Then it scans for exploitable ports and services
- It identifies weak passwords and authentication errors
You get a detailed report of the vulnerabilities found during the assessment and suggestions for fixing the issues.
3. Database vulnerability scanning
The ultimate goal of most malicious actors is to get access to the database where you store all sensitive information. Hence, the importance of securing databases is immense. Database security involves multiple measures taken to ensure the confidentiality, integrity, and availability of databases along with the database management systems.
A hacked database can be devastating for a business as it impacts business continuity, brand value, finances, and intellectual property, and may incur fines and penalties.
What is a database vulnerability scanner?
A database vulnerability scanner is a tool specially designed for scanning your database for vulnerabilities like faulty security configuration, and lack of encryption.
Database vulnerability scanning helps you evaluate the overall data security health of your organization, detect vulnerabilities, and mitigate them before they are exploited by hackers.
4. Cloud vulnerability scanning
The process of scanning a cloud deployment for common vulnerabilities is called cloud vulnerability scanning. Cloud vulnerability scanning is a part of the holistic cloud security strategy that can be implemented to monitor, manage, and improve the overall security of cloud infrastructure.
What are some cloud-related vulnerabilities?
- Server misconfigurations such as misconfigured S3 buckets are one of the most common cloud vulnerabilities.
- Using weak passwords can expose your cloud accounts to brute-force attacks.
- SQLi, XSS, and CSRF bugs are quite common in cloud-based applications, and they can be exploited easily by hackers.
- Running outdated, unpatched software on your cloud platform can compromise the cloud services.
Performing regular cloud vulnerability assessments ensures you stay on top of these issues.
5. Application Vulnerability Assessment
Application vulnerability scanning is one of the most widely used vulnerability scanning types. It involves scanning your web apps and mobile apps for security vulnerabilities.
Both web applications and mobile applications are updated with new features on a regular basis. New vulnerabilities may creep in with each new code update. That aside, an application needs various external components like themes and plugins to function properly. These external components may also incur exploitable vulnerabilities.
It is essential to incorporate a security regime in your application development lifecycle and an application vulnerability scanner plays a vital role in it.
Application vulnerability assessment helps you assess –
- The current state of security of your application
- The existing vulnerabilities and the risk posed by them
- The amount of potential damage caused by the vulnerabilities.
It also helps you find efficient ways of removing vulnerabilities.
Now that you have learned about five different vulnerability scanning types, it is time to understand some more categories of vulnerability assessment.
What is authenticated and unauthenticated vulnerability scanning?
In the case of an authenticated scan, the scanner is configured with credentials to conduct the scan on the privilege level granted to authenticated users. In simpler terms, the authenticated vulnerability scanner can scan behind the logged-in pages. We can also call it an internal vulnerability scan.
An unauthenticated scanner scans for perimeter threats from the point of view of an outsider as it does not have privileged access. This is also called an external vulnerability scan.
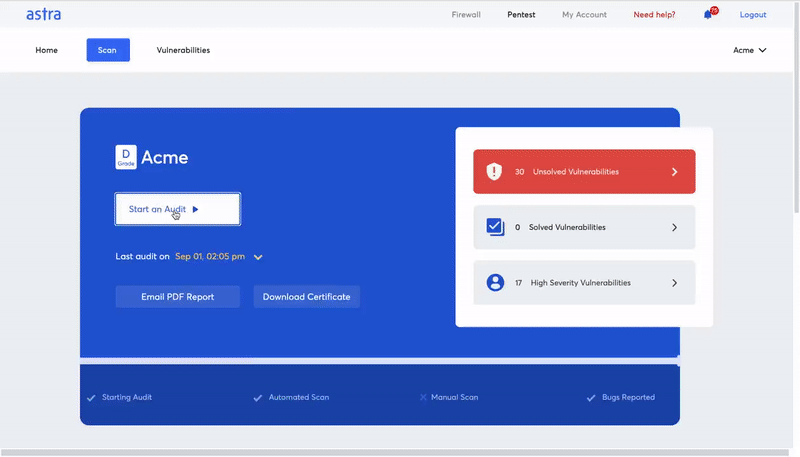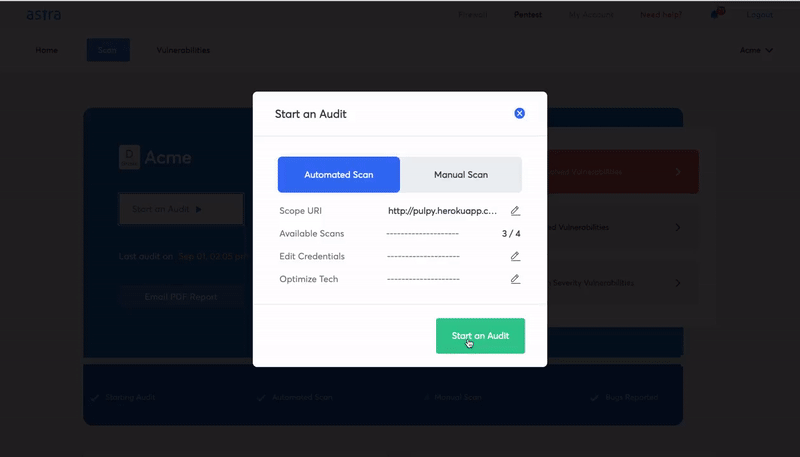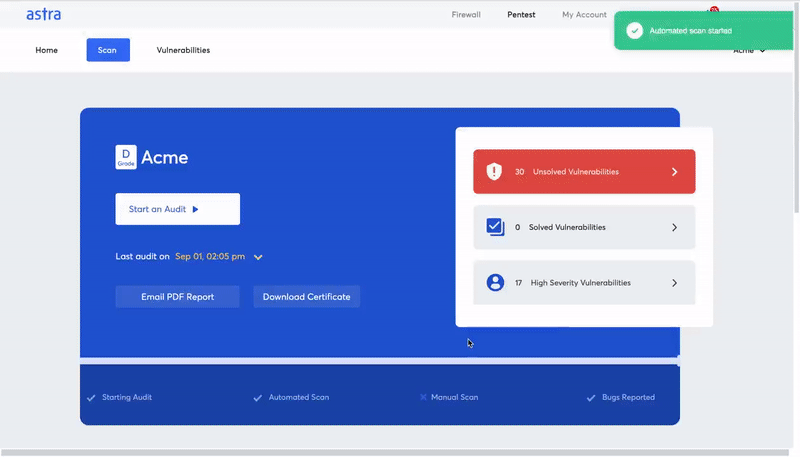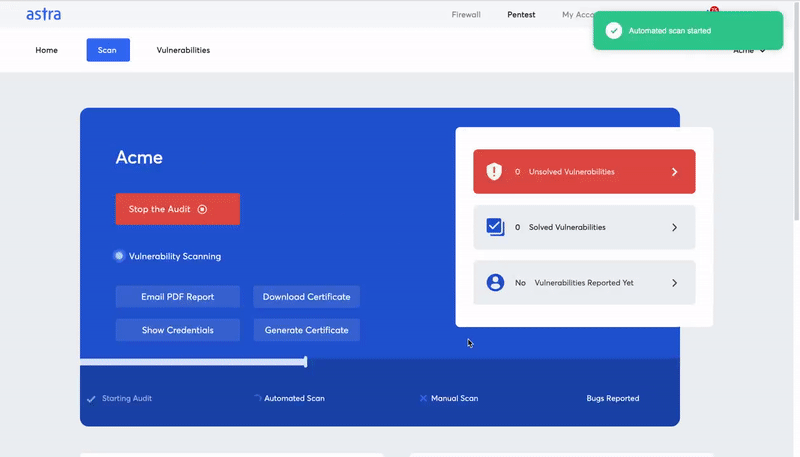
How to Select Vulnerability Scanners?
There are a variety of parameters that can help you judge a vulnerability assessment provider or even vulnerability scanners. Here are some crucial features you should look for in a vulnerability scanning provider and their vulnerability scanners.
- Coverage of all CVEs: Go for a vulnerability assessment that covers all CVEs mentioned on the OWASP top 10, SANS 25, and has all the tests required for major compliances.
- Continuous scanning: You need a scanner that can perform automated vulnerability scanning periodically and every time there is a code update.
- Scan behind the login screen: We have already discussed the importance of authenticated scanning, you need a scanner that scans behind the login screen without requiring you to authenticate it every time the session runs out.
- Vulnerability monitoring: You should be able to monitor the vulnerabilities along with their risk scores as they are found.
- Detailed suggestions for fixing the issues: A vulnerability scanning report with suggested fixes can ease up the task of mitigating the vulnerabilities manifold.
Apart from these features, you should also look at the presence of a particular vulnerability scanning company in the industry, their clientele, and online reviews, and also judge the price with respect to the quality of service you are promised.
The Advantages of Using Astra’s Pentest for Vulnerability Scanning
Astra’s Pentest is a complete vulnerability assessment and penetration testing solution with top-notch automated and manual pentesting capabilities. Even if you use it in the capacity of only an automated vulnerability scanner it could be a win for you.
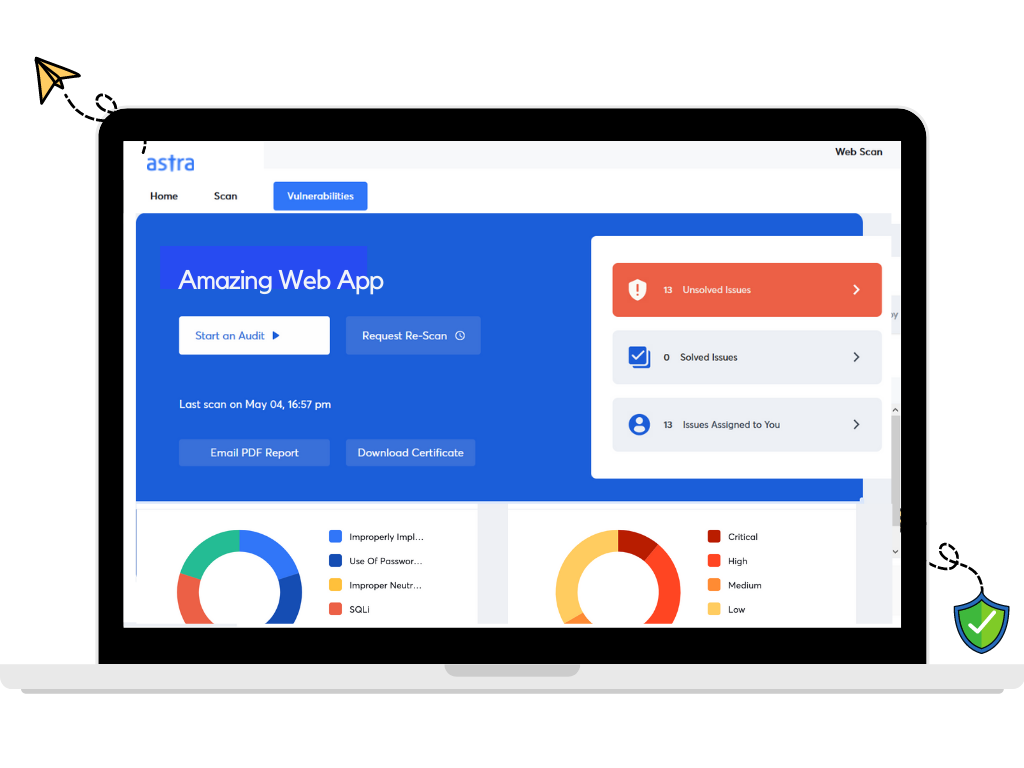
Astra Pentest conducts 8000+ automated tests that cover every CVE mentioned in OWASP top 10, SANS 25, and a host of other CVEs.
Not only does it conduct all the tests required for compliance with ISO 27001, HIPAA, SOC2, and GDPR, but the pentest suite also has a compliance reporting feature that shows you where you are falling short in terms of meeting the compliance requirements base on the results of the vulnerability scans.
The interactive pentest dashboard allows you to monitor the vulnerabilities, assign them to team members, update their status, practically anything you might like to do.
The CI/CD integration feature lets you automate the vulnerability scans before the new code is shipped.
The login recorder extension allows the vulnerability scanner to scan behind the logged-in pages.
Overall it is just a package you cannot pass over without reaping the benefits.
Conclusion
By now, you have learned about 5 vulnerability scanning types. We’re hoping this has enriched your understanding of a certain aspect of vulnerability management and cybersecurity as a whole. It should also have helped you understand the urgency under which the entire cybersecurity industry functions. If you have a vulnerability you are always a few minutes away from getting hacked. Be proactive about security, and thrive.
FAQs
1. What is the cost of web app vulnerability scanning?
The cost of web app vulnerability scanning is between $99 and $399.
2. Can the Astra Pentest scan behind login pages?
Yes, thanks to the login recorder extension, the Astra Pentest scanner can scan behind the logged-in pages.
3. How often should I conduct vulnerability scans?
It is necessary to conduct quarterly vulnerability scans. But you should also run a vulnerability scan before every code update in your application.
















