Google vulnerability scanners are best known for finding vulnerabilities in your App Engine, Google Kubernetes Engine (GKE), and Compute Engine web apps.
Sophisticated threats aimed at your Google Cloud resources can be detected and patched in real-time with the help of GCP vulnerability scanning tools.
With its many distinct technologies and locations, the cloud environment mandates a different security method than a traditional on-premise data center.
To detect and mitigate threats targeting your Google Cloud resources, we walk you through this in-depth guide to provide deep insights about the features and best practices.
What Is GCP Vulnerability Scanning?
GCP vulnerability scanning is the continuous process of finding and identifying vulnerabilities for mitigation in your Google Cloud infrastructure to minimize the attack surface. Continuous scanning of your GCP helps in the quick remediation of vulnerabilities before they threaten your GCP security.
What is the GCP vulnerability scanning tool?
The tool that automatically scans and detects exploitable vulnerabilities in the GCP infrastructure and application resources on the Google Cloud Platform is called the GCP vulnerability scanning tool. GCP scans different GCP resources like Compute Engine instances, App Engine apps, Kubernetes clusters, databases, and websites.
GCP assigns severity scores and provides remediation guidance to help organizations fix issues and strengthen the security of their GCP environments.
7 Best GCP Vulnerability Scanning Tools of 2024
- Astra Pentest
- Google Cloud Security Scanner
- Nessus
- Qualys Cloud Platform
- OpenVAS
- Burp Suite
- Nexpose
Top 7 GCP vulnerability scanning tools & software
1. Astra security
Astra GCP Security Services is a cloud-based solution that provides comprehensive security for applications running on the Google Cloud Platform (GCP) and identifies security issues in GCP resources like VM instances, Kubernetes clusters, storage buckets, etc.
It enables individualized multiple compliance scans for GDPR, HIPAA, SOC2, PCI-DSS, and ISO 27001. Astra creates comprehensive vulnerability scanning reports with zero false positives. You can keep up with every process step using Astra Pentest, including the vulnerability status, developer actions, and any updates on the overall security situation.
Utilizing Astra’s advanced scanner and leveraging Astra Pentest’s GCP security services, you gain the ability to perform a comprehensive 360-degree security audit, proactively identifying vulnerabilities before malicious hackers can exploit them.
Why should you opt for Astra Pentest:
- Continuous Offensive Security
- Comprehensive Scanning
- 8000+ tests
- NIST and OWASP methodologies
- Intuitive Dashboard
- Actionable VAPT reports
- Publicly Verifiable Certificate
- Compliance Scans
- CI/CD Integrations
- Scan-Behind-Logins
Features
- CI/CD Integrations: Seamless Shift from DevOps to DevSecOps. With this seamless shift, developers can focus on delivering high-quality code while being confident that security measures are integral to the process.
- VAPT Certificate: A publicly verifiable certificate issued after penetration testing is completed.
- Collaboration within Context: Hassle-free, collaborative remediation process with POCs and one-on-one chats
- Security Standards: Coverage of essential security standards like OWASP, SANS, CSA, and CIS. Astra Security is also empanelled by CERT-In for providing information security auditing services.
What is good?
- Uses OWASP and NIST methodologies.
- Provides expert remediation assistance.
- Compliance-Specific Scans
- Automated and manual pentests
What could be Better?
- The dashboard could be more intuitive.
2. Google Cloud Security Scanner
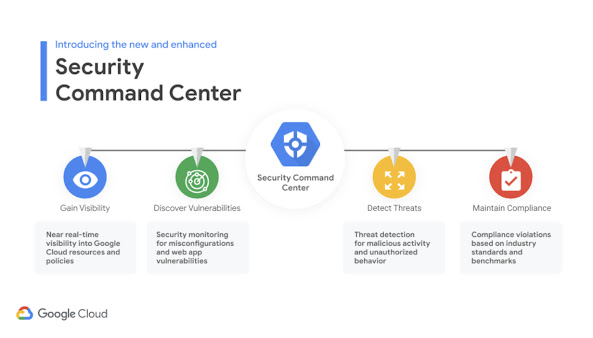
The Google Cloud Security Scanner identifies security vulnerabilities in Google App Engine web applications. It scans web applications deployed on GCP for vulnerabilities such as cross-site scripting (XSS), SQL injection, and other security issues.
The scanner attempts to test as many user inputs and event handlers as it can as it crawls the application, following all links within the range of the starting URLs.
The scanner works in conjunction with the current secure design and development processes. A safe design and development process prioritizes security throughout the software development lifecycle, identifying and mitigating potential risks at every stage.
Features
- Easy-to-use: User-friendly and requires no setup or configuration.
- Integration: Integrates with other Google Cloud Platform services such as Compute Engine, App engine, etc.
- Scheduling: Automated scheduling of scans.
What is good?
- Provides remediation recommendations by analyzing the cause of found vulnerabilities
- The scanner gives notifications and data in real-time.
What could be Better?
- It may not support scanning web applications
- This scanner has Limited customization
3. Nessus

Nessus is a vulnerability scanner that can scan GCP infrastructure and applications for vulnerabilities; It can identify misconfigured settings, outdated software, and other security issues.
The Google Security Scanner by Nessus can scan GCP environments for compliance with industry standards such as PCI DSS, HIPAA, and CIS. Additionally, it also generates detailed reports that can be used to prioritize remediation efforts.
Nessus is a flexible and reliable tool for conducting proactive security assessments. It helps businesses reduce risks and keep their IT environment safe.
Features
- Integration: Nessus can integrate with other security tools, SIEM platforms, and reporting systems.
- Scans: PCI-DSS, malware scans, web application scans, etc.
- Compliance: Checks compliance for UNIX and Windows servers.
What is good?
- Highly customizable
- A comprehensive set of OWASP Top 10 vulnerability checks
- Accuracy in identifying real vulnerabilities
What could be better?
- Steep learning curve
- Expensive license
- Overwhelming documentation
4. Qualys Cloud Platform
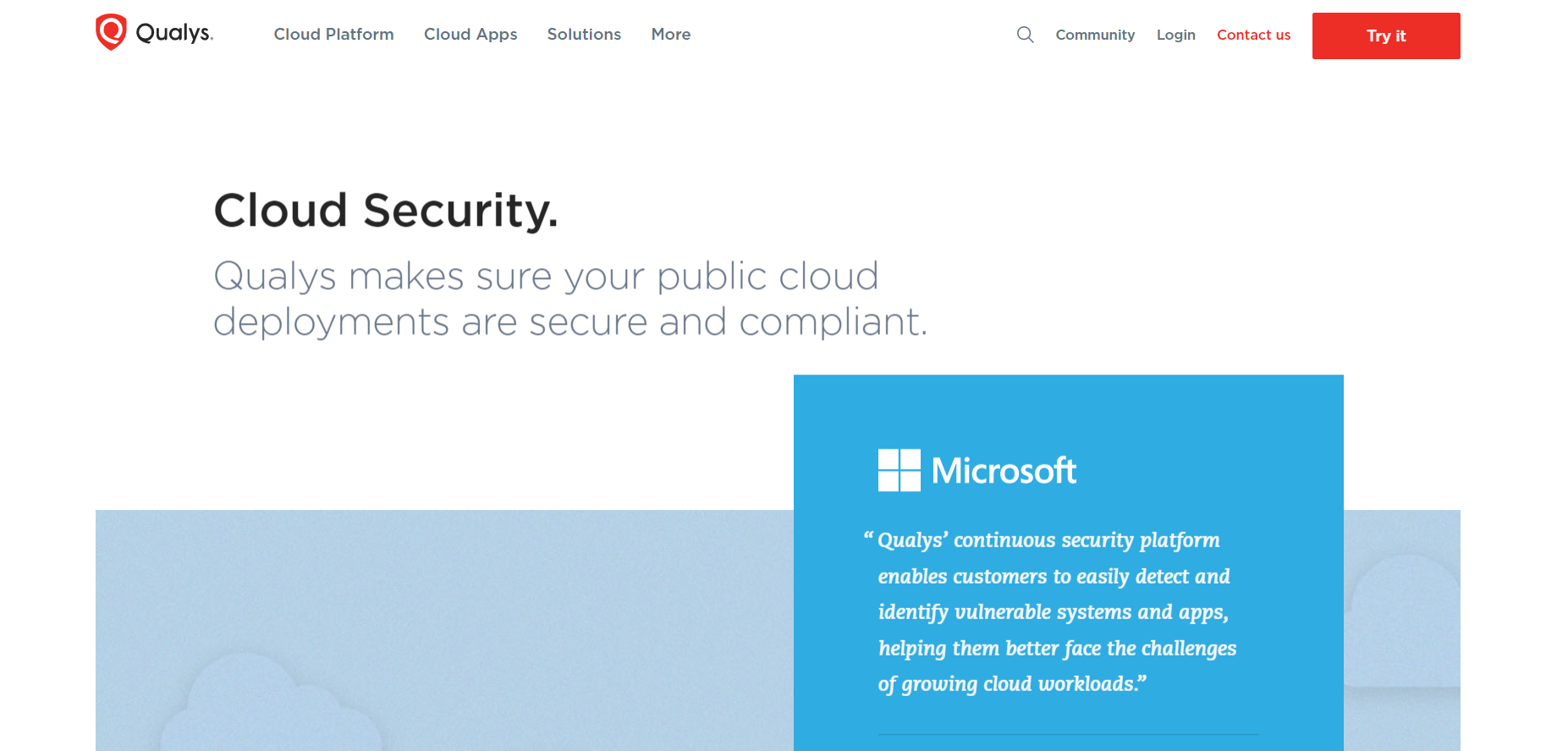
Qualys offers a cloud-based GCP vulnerability management platform with Google Cloud Security scanners that can monitor GCP virtual machines, storage buckets, Kubernetes clusters, etc., for vulnerabilities.
Qualys has multiple scanners, such as remote, local, and passive, to manage vulnerabilities.
This GCP vulnerability scanning platform offers a centralized dashboard to see all the assets, scans, and compliance status of GCP infrastructure in a single place.
Features
- Wide scan range: VMs, containers, storage buckets, web apps, Kubernetes clusters, etc.
- Compliance: PCI, HIPAA, GDPR, and more
What is good?
- There is nothing to install or handle, and all services can be accessed through a web interface in the cloud.
- Vulnerability data is saved and processed safely on a network of load-balanced servers.
Disadvantages
- Documentation can be improved.
- Complicated to use.
- Response time could be better.
5. OpenVAS
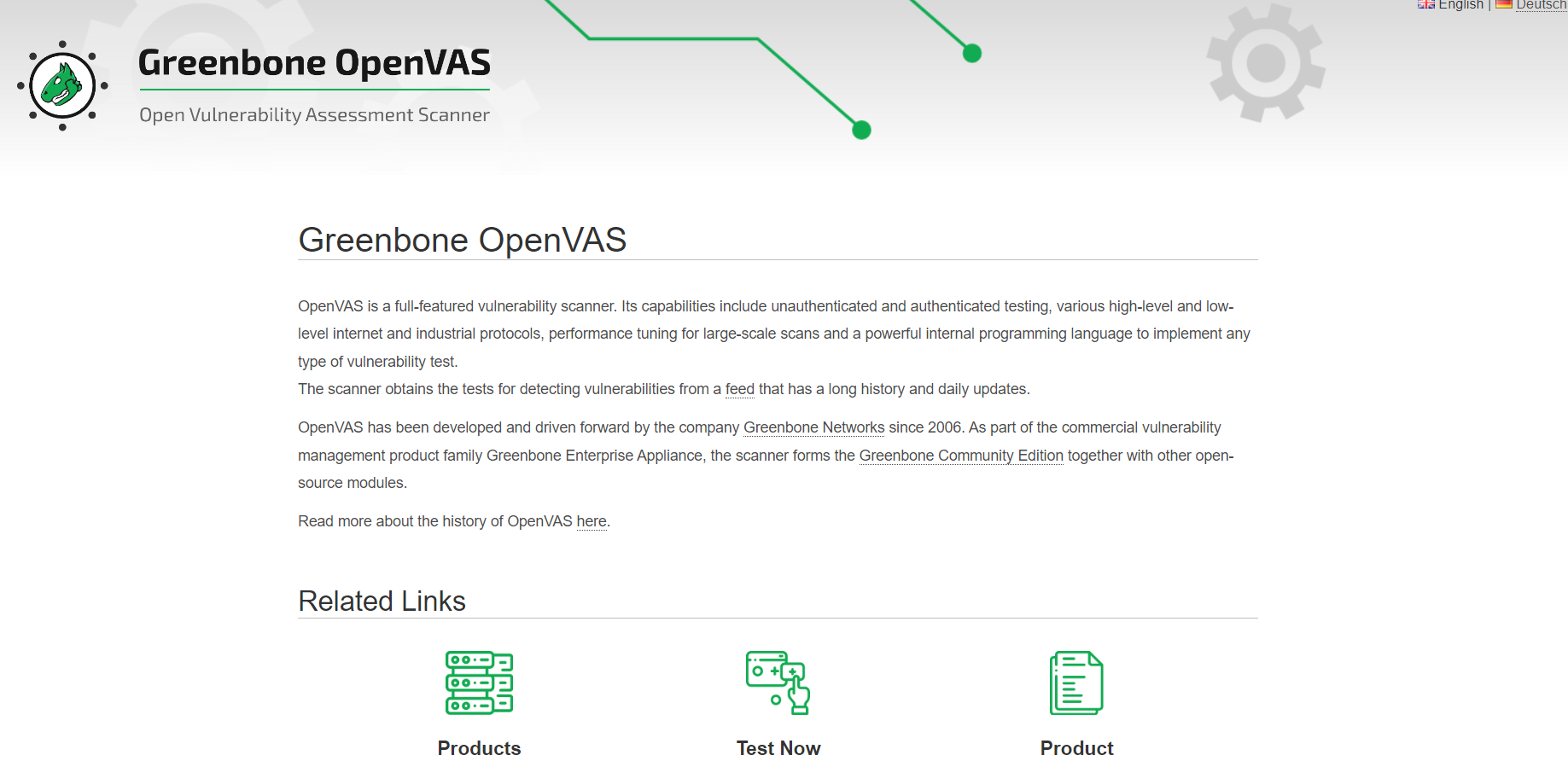
OpenVAS is an open-source Google Cloud security scanner that can scan GCP infrastructure and applications to find vulnerabilities and be customized to meet specific security requirements.
OpenVAS can find and categorize potential weak spots in your infrastructure, calculate their dangers, and suggest ways to fix the problem.
Potential vulnerabilities are then compared to a database of known security vulnerabilities to quickly find and fix the weaknesses.
Features
- Scanning: comprehensive scans of networks, systems, and applications
- Network vulnerability tests: The utility evaluates network security by checking open ports, services running, banner grabbing, etc.
- Automation: Automatic scans can be scheduled and conducted at user-defined intervals.
What is good?
- Security configuration auditing
- Controlling access and managing users.
- Customizable to meet specific security requirements.
What could be better?
- Problem with agent syncing.
- Potential false positives
- Lack of proper documentation.
6. Burp Suite
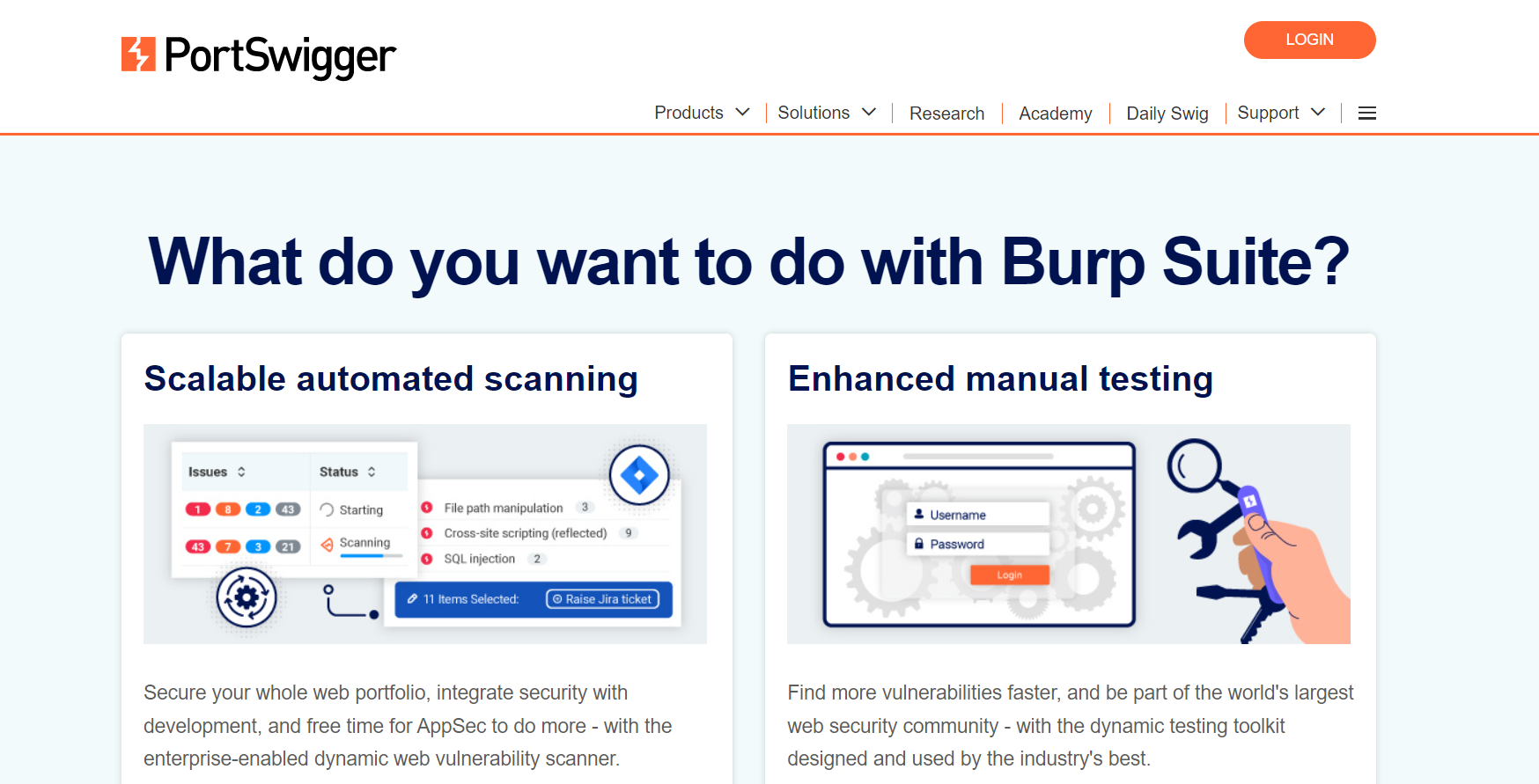
Burp Suite is a security testing tool that scans web applications deployed on GCP for vulnerabilities. It can be integrated with most CI/CD platforms using its generic, platform-agnostic driver.
This Google Cloud Scanner intercepts and modifies web traffic between a user’s browser and the tested web application to perform automated vulnerability scans of web applications deployed on GCP.
Features
- CI/CD integration: Jenkins, TeamCity, and other CI/CD platforms
- Customization: Create custom scripts, plugins, and other features.
- Scanning: Burp Scanner automates looking for threats in web apps.
What is good?
- Burp Scanner performs vulnerability checks, including common issues like XSS, SQL injection, and CSRF.
- Burp Suite makes thorough reports with information about vulnerabilities, proof of concept, and suggestions for fixing them.
What could be better?
- It is complex to set up and configure the scanner for users unfamiliar with the tool.
- Burp Scanner may produce false positive results.
7. Nexpose
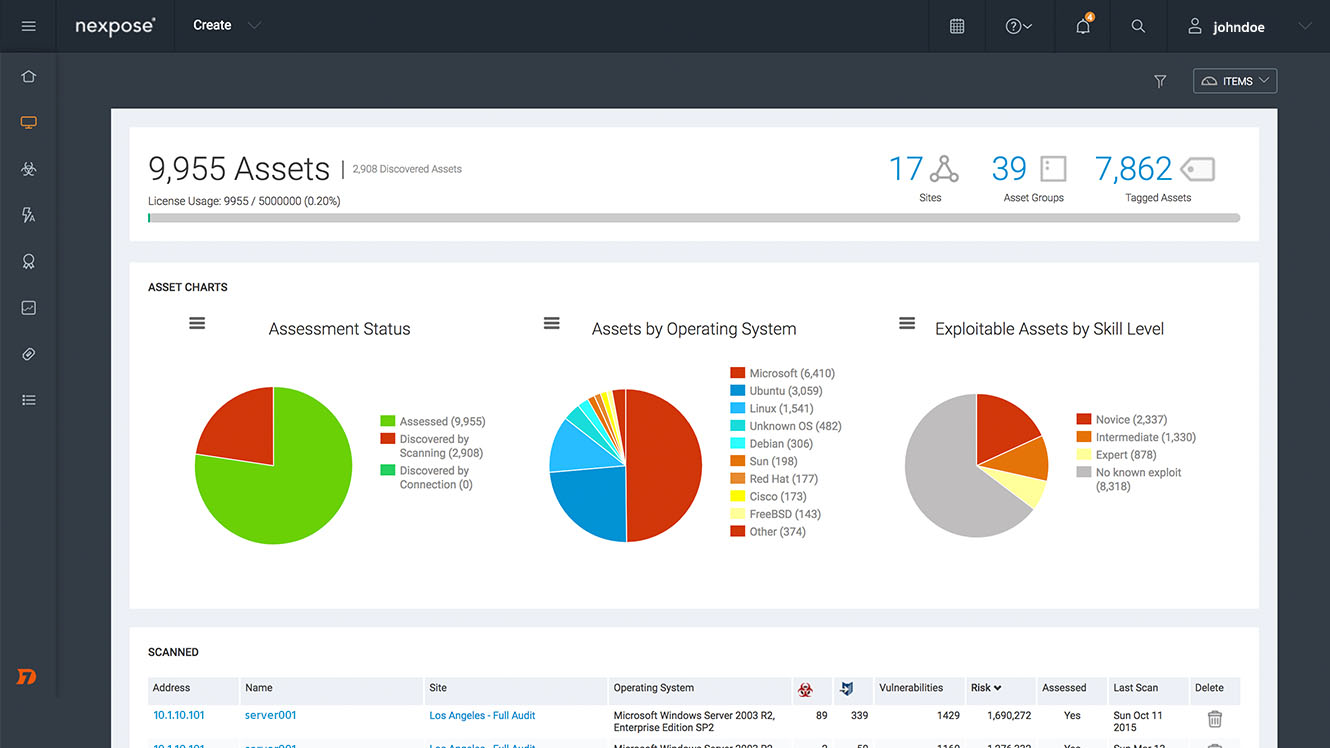
Nexpose, the GCP vulnerability management platform, offers a comprehensive set of vulnerability checks and can be customized to meet specific security requirements.
All asset scan data is stored in the embedded PostgreSQL database in Nexpose, which is also used to produce vulnerability reports.
This GCP vulnerability scanning tool can automatically discover and catalog all assets in an organization’s GCP environments, including virtual machines, containers, and other infrastructure components, to perform a deep scan to find critical vulnerabilities and recommend the appropriate fix.
Features
- Components: PostgreSQL database, Security console, and scan engine
- Dashboard: A centralized dashboard for tracking and assigning tasks
- Customization: Scans, policies, reports, and rules can be customized with the integrated user-friendly dashboard
What is good?
- Real-time Dashboard notifications of Risks
- Risk and remediation prioritization
- Highly detailed reporting about vulnerabilities.
What could be better?
- Potential for false positives
- High pricing
How To Choose The Best GCP Vulnerability Scanning Tools?
1. Coverage
GCP vulnerability scanning tools should scan for vulnerabilities across all primary GCP services like Compute Engine, Kubernetes Engine, App Engine, Cloud Storage, SQL, and openness at the OS, network, and app levels, such as SQL injection, cross-site scripting (XSS), and remote code execution (RCE).
2. Continuous Scanning
Vulnerabilities can emerge anytime, so continuous scanning is essential for resources and workloads. It detects new vulnerabilities as they arise and provides real-time alerts. GCP vulnerability scanning tools comprehensively scan all assets in a user’s cloud infrastructure, including virtual machines, containers, and applications.
3. Integration with GCP
Google Security Scanner should integrate well with various GCP services like SIEMs, ticketing systems, and other DevOps tools. It allows for easy monitoring, alerting, and workflow automation and enables the device to provide better visibility into your security posture.
4. Vendor Reputation and Support
Having multiple support options like phone, email, documentation, and onboarding support helps the onboarding process and addresses issues during usage. The vendor providing the tool must have a proven track record of delivering reliable and effective vulnerability scanning tools.
5. Compliance checks
All Google cloud scanners should detect violations and scan for compliance with standards like PCI DSS, HIPAA, GDPR, etc.
6. Remediation recommendations
In addition to identifying flaws, it should make recommendations for addressing them. The recommendations should be prioritized based on the severity of the vulnerability and the potential impact on your GCP environment.
Importance of GCP vulnerability scanning software
- Identify Weaknesses: GCP vulnerability scanning tools help identify vulnerabilities, misconfigurations, and potential security weaknesses in cloud environments.
- Risk Mitigation: Risk mitigation involves applying security patches, updating software, changing configuration settings, or implementing additional security controls.
- Proactive Security Posture: GCP vulnerability scanning tools help maintain an aggressive security posture by identifying vulnerabilities before attackers can exploit them.
- Patch Management: Google cloud scanners can help manage security patches and updates across the cloud environment. The scanners identify which patches must be applied, schedule patching activities, and monitor patch compliance.
- Integration with DevOps: GCP vulnerability scanning tools can be integrated with DevOps processes to ensure security is built into the cloud infrastructure. Vulnerability scanning is part of the continuous integration and deployment (CI/CD) pipeline. Google Cloud security scanners can be integrated with SIEM systems, incident response tools, and other security services.
- Dynamic environments: GCP environments can change frequently with updates, new resources, etc. GCP vulnerability scanning tools are designed to work in dynamic cloud environments where resources are constantly being created, moved, and deleted.
What are the features of GCP vulnerability scanning tools?
1. Asset Discovery
The GCP scanning tools include asset discovery capabilities, which help users identify all the assets in their cloud infrastructure, including those that may have been forgotten or overlooked.
Asset discovery helps ensure that all potential security risks are identified and addressed. GCP tools use cloud metadata to discover assets and can be configured to find help in specific regions or projects.
2. Severity Assessment
Once vulnerabilities are identified, the scanning tools assess each exposure’s severity. GCP vulnerability scanning tools assess the severity of vulnerabilities based on industry-standard scoring systems such as the Common Vulnerability Scoring System (CVSS).
Severity assessment enables users to prioritize which vulnerabilities to address first based on their potential impact on the security of their cloud infrastructure.
3. Reporting and dashboards
The reports and dashboards include information on the number and severity of vulnerabilities discovered, the status of remediation efforts, and compliance status.
The new reporting and dashboard feature helps users stay informed about the security of their cloud infrastructure and make data-driven decisions about how to prioritize remediation efforts.
The Best practices for Google security scanners
Google Cloud security scanners are built on one of the most secure data infrastructures in the world. But it’s your responsibility to ensure your Google Apps security settings are set up correctly by following some of the best practices.
- Use Google’s Site Isolation feature to isolate each site in a separate sandbox or process. This contains vulnerabilities and prevents them from spreading.
- Integrate Cloud Malware Threat Protection to avoid data loss and severe threats to your organization’s customers, employees, trade secrets, and more.
- Require two-factor authentication for all Google accounts to add an extra layer of security beyond passwords.
- Enable automatic updates for all Google apps and plugins. Updates contain the latest security fixes for known vulnerabilities.
- Run regular security scans with Google’s Chrome Security Scanner and Android Device Manager to detect threats, malware, and vulnerabilities. Scan at least monthly.
- Limit employee access on a need-to-know basis. Only grant the minimum required access and promptly revoke access when no longer needed.
- Enable login notifications and activity auditing to monitor for suspicious activity. Investigate any abnormal login attempts or behavior.
- Provide ongoing security awareness training for employees on secure password practices, identifying phishing attempts, and other best security behaviors.
- Monitor the system and audit the Google Cloud security settings of the Google Cloud security scanner.
Conclusion
GCP vulnerability scanning identifies security weaknesses within Google Cloud Platform environments and infrastructures. GCP scans detect configuration issues, missing patches, and vulnerable software. Many vulnerability scanning tools exist for GCP.
Best practices include implementing multi-factor authentication, reviewing and prioritizing vulnerabilities, and rapidly remediating high-severity issues. When choosing a tool, consider the cost, compliance checks, compatibility with GCP, integration with DevOps tools, number of vulnerabilities detected, and false favorable rates to find a suitable option. Regular scanning with the right tool can significantly improve the security and resilience of your GCP infrastructure.
Frequently Asked Questions
What is a comprehensive scan on GCP Security Scanner?
A comprehensive scan is a full audit of all resources within a GCP project. Complete scans check Compute Engine instances, App Engine apps, Storage buckets, Kubernetes clusters, and other resources for vulnerabilities and misconfigurations.
How does GCP Vulnerability Scanning work?
These tools discover GCP resources, evaluate them against a vulnerability database, and produce a report of any issues found.
They authenticate to GCP using service accounts and access resources programmatically through the APIs.
Can I customize the scanning rules in GCP Vulnerability Scanning?
Yes, most tools allow you to customize controls and rules to exclude less critical vulnerabilities, focus on compliance needs, adjust severity levels, and create custom rules.














