34% of all cloud-related data breaches can be attributed to the hijacking of privileged accounts. More than 90% of the users utilize only 5% of the access granted to them. Can you spot a pattern there?
There is simply too much access, and too little time to review all the security controls manually. A good cloud vulnerability scanner can make a significant difference there, and we will help you find just the right one for your business.
An automated cloud vulnerability scanner allows you to be vigilant without losing time. You can create a secure cloud environment without compromising on the speed of operations.
Best 5 Cloud Vulnerability Scanners
| Cloud Vulnerability Scanners | Key Features |
|---|---|
| Astra Pentest | 8000+ tests, CI/CD integration, scans behind logged-in pages, compliance-specific scans, risk scores, remediation support |
| Qualys | Visibility across all IT assets, real-time network analysis |
| Intruder | Attack surface monitoring |
| Aqua | Cloud agent, run time protection, compliance assistance |
| Orca Security | Compliance assistance |
How does a cloud vulnerability scanner work?
A cloud vulnerability scanner is a tool that automates the process of identifying vulnerabilities in cloud-hosted applications.
The scanner probes into the target system by sending certain requests and monitors the responses and compares those responses with details from a vulnerability database. If these responses signal an anomaly, the scanner flags the issue and reports it.
A cloud vulnerability scanner essentially performs the scans in the cloud, hence your servers remain stress-free and your business uninterrupted. It helps you address a number of tricky security-related issues such as security misconfiguration, unauthorized access, insecure interfaces, and account hijacking.
Also Read: Cloud Security Audit: Everything You Need to Know
Cloud vulnerability scanning in 4 steps
Planning and scoping the scan:
In this stage, you will need to determine the scope of the scan. This includes identifying which cloud-based assets need to be scanned and setting the frequency of scanning.
This step is crucial for cloud vulnerability scans as the policies set by cloud providers have to be taken into consideration before proceeding with the scan.
In this stage, the scanner will identify vulnerabilities in your cloud-hosted application.
Reporting:
In this stage, companies that provide cloud security scanners will generate a report that details the findings of the scan. The vulnerability assessment report usually includes a list of all the detected vulnerabilities categorized by severity.
Other than that, the test cases used in the scan are also mentioned in the report along with some guidance to fix the issues.
Remediation:
Your developers use the suggestions to fix the most critical vulnerabilities first and work their way down the list according to priority. With some cloud vulnerability assessment providers, you can get expert help from security professionals.
Read also: A Complete Guide to Cloud Security Testing | Top 6 Web Pentest Tools You Should Not Miss in 2022
7 features you should look for in a cloud vulnerability scanner
Cloud vulnerability scanning is a little different from website scanning as the scanner needs to support the cloud infrastructure, and some other factors like cloud security policies and guidelines come into play. You need to make sure that you get the right tool on the first go. Here are some features that will help your business in the long run.
Supports GCP, AWS, & Azure
Your scanner should support all the major cloud providers. This will allow you to scan for vulnerabilities across different cloud environments and get a comprehensive view of your application’s security posture.
Optimized for security policies set by the cloud provider
The cloud provider that you use will have a set of security policies in place. The scanner should be able to adhere to those policies so that you don’t have to worry about any compliance issues.
Scanning in the cloud so as not to stress the servers
As mentioned earlier, automated vulnerability scanners for the cloud perform the scans in the cloud. This means that your servers don’t have to bear the brunt of the scan and can continue working without any hiccups.
CI/CD integration and continuous scanning
The scanner should be able to integrate with your CI/CD pipeline so that you can automate the scans. This way, you can ensure that your application is scanned for vulnerabilities at regular intervals.
Compliance-specific scans
Depending on the industry that you’re in, you might have to comply with certain regulations. The cloud vulnerability scanning tool should be able to perform compliance-specific scans so that you can be sure that your application is up to the mark.
Detailed reporting with video PoCs
You should get a detailed report that includes all the information that you need about the vulnerabilities. In addition to that, the report should also have video PoCs so that you can see how the exploit works.
Remediation support
It’s not enough for the cloud security scanner to just identify the vulnerabilities. The scanner should also provide you with guidance on how to fix the issues so that you can remediate them as quickly as possible.
Now that you know what to look for in a cloud vulnerability scanner, it’s time to take a look at some of the best tools on the market.
Read also: AWS Vulnerability Scanning – A Complete Guide | What is Network Vulnerability Scanning? The Ultimate Guide
5 best cloud vulnerability scanners [Reviewed]
You are already familiar with some of the top cloud vulnerability scanning tools, here’s a more detailed view.
Astra Pentest
Astra Pentest combines automated vulnerability scanning with manual pentesting to bring you the most comprehensive security testing for your cloud-hosted application. The pentest suite offered by Astra Security is designed to make cloud vulnerability assessment better and easier for users.
The security engineers at Astra are always on their toes to find new opportunities to improve the scanner.
The scanner rules are updated every week to stay ahead of the curve. By paying keen attention to every step of the user journey, we have built the perfect cloud vulnerability scanner for any situation.
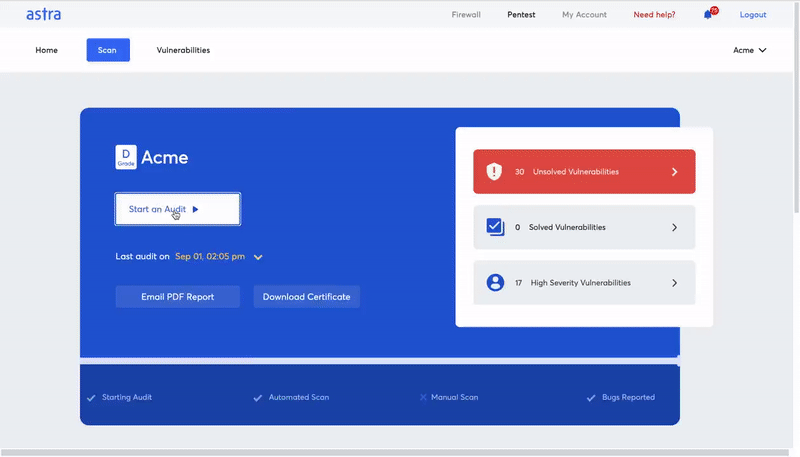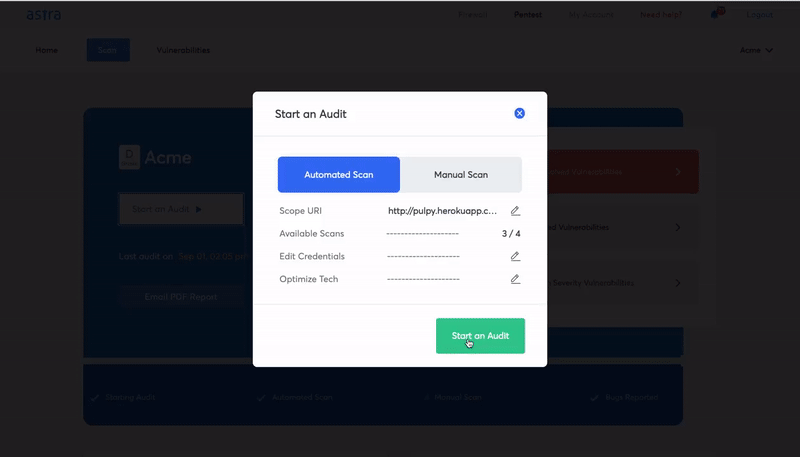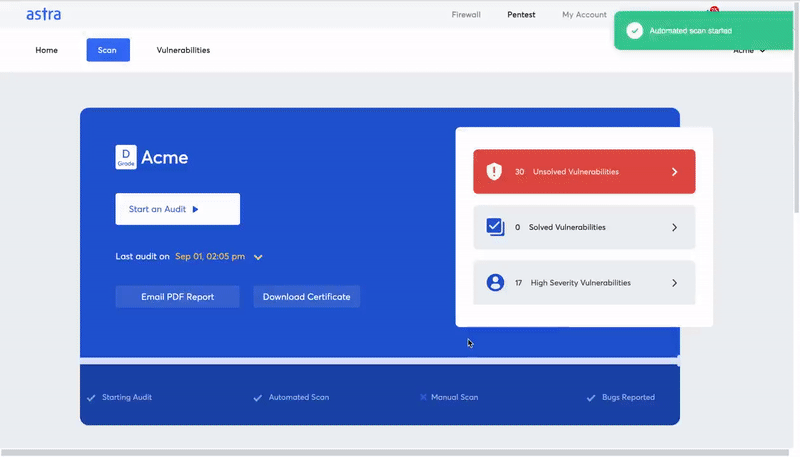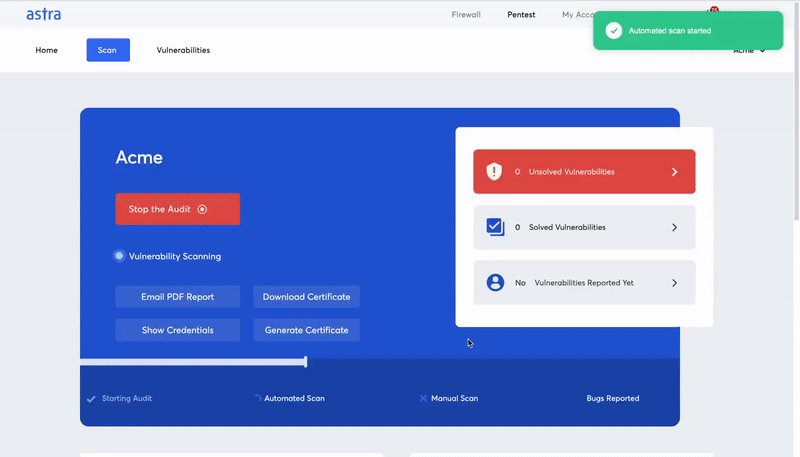
Key features
- The scans are performed in the cloud which means that your servers are not stressed
- The vulnerability management dashboard allows you to collaborate with security experts for remediation
- You can integrate the scanner with your CI/CD pipeline
- You can run compliance-specific scans to improve audit readiness
- 8000+ tests that cover all prominent CVEs
- Manual pentest to detect business logic errors and ensure zero false positives
Qualys
Qualys Cloud Platform is a cloud vulnerability scanner that provides you with comprehensive visibility into your cloud infrastructure. The platform offers a single pane of glass to view all your assets, vulnerabilities, and compliance status.
The platform is constantly updated with the latest CVEs so that you can be sure that no threats go undetected. In addition to that, Qualys offers a cloud agent that you can use to scan your cloud infrastructure for vulnerabilities.
Key features
- Vulnerability management, detection, and response
- 2-second visibility across all IT assets
- Provides comprehensive visibility into assets, vulnerabilities, and compliance status
- Cloud agents for devices, mobiles, and all endpoints
- Real-time network analysis
Intruder
Intruder can be used to perform a wide range of tests including penetration testing, DDoS testing, and web application security testing. In addition to that, Intruder offers a cloud agent that you can use to scan your cloud infrastructure for vulnerabilities.
Key features
- Continuous monitoring of attack surfaces
- Comprehensive security checks
- Quick response to new threats
Aqua
Aqua Security provides a cloud-native security platform that you can use to secure your cloud-hosted application. The platform offers a wide range of features including cloud vulnerability scanning, runtime protection, and compliance management.
In addition to that, Aqua Security also offers a cloud agent that you can use to scan your cloud infrastructure for vulnerabilities.
Key features
- Offers a cloud agent for scanning cloud infrastructure
- Provides runtime protection and compliance management
- Allows you to generate reports and share them with stakeholders
- Helps you to track vulnerabilities over time
Orca security
Orca security promotes a new approach to cloud vulnerability scanning called Sidescanning. It replaces the cloud agent and collects data directly from your cloud configuration.
Orca helps you cover vulnerabilities that might have escaped the agent-based vulnerability scanning solutions.
Key features
- Combines all your cloud assets in a single graph
- It supports more than 40 CIS benchmarks and all major security regulations
- Makes actionable data easily available to the right teams
What makes Astra’s Pentest the top choice?
Astra’s Pentest suite conducts 8000+ automated tests to ensure all common vulnerabilities are detected and on top of that, you can opt for manual pentest to dig deeper and exploit more difficult security issues.
You can integrate the scanner with your CI/CD platforms and never worry about sending vulnerable code to the production stage. The scanner also integrates easily with platforms like Slack and Jira, making it even easier to maintain the DevOps workflow.
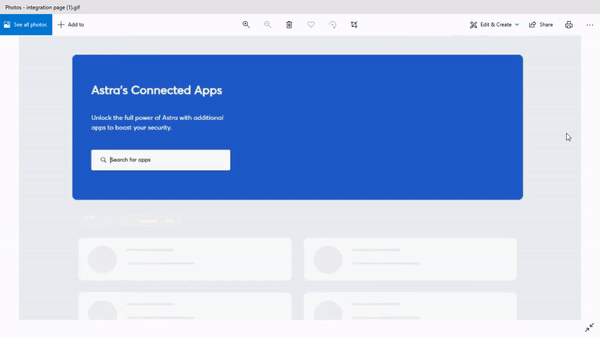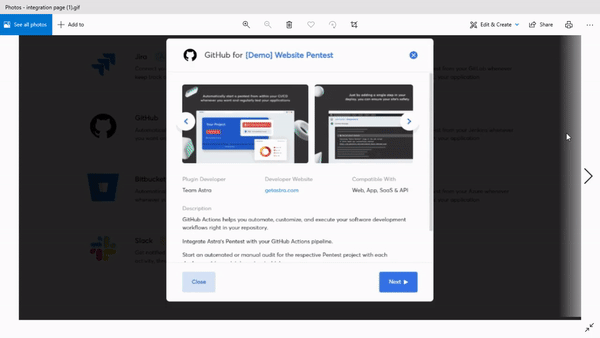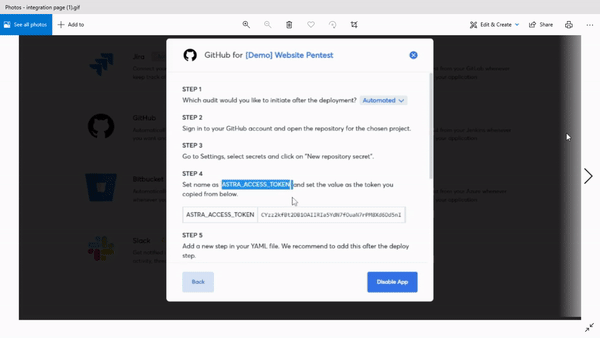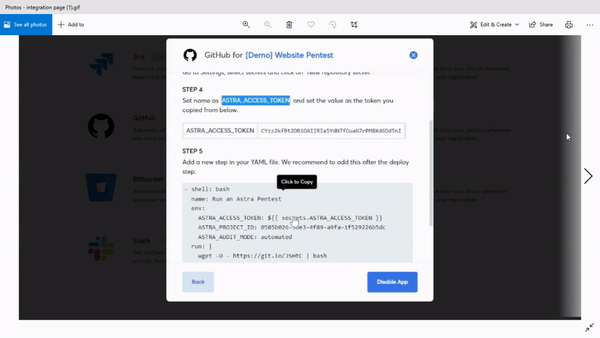
Astra’s Pentest is the perfect tool for you to achieve DevSecOps and more importantly, peace of mind.
Final thoughts
A cloud vulnerability scanner makes your life easier as a business owner or an information officer if you choose the right one and use the insights produced by it to make positive changes.
It is easy to get hacked given the amount of exposition our apps face despite the security offered by cloud providers. Nevertheless, it is also not too hard to take the right precautions, and follow the right practices to protect your cloud-hosted businesses.
Turn cloud vulnerability scanning into a part of the regular business workflow, treat it as a mission-critical practice, and choose the right tools, and you should be good.
FAQs
1. What are some cloud vulnerabilities?
Some common security vulnerabilities in the cloud are 1. Open S3 buckets 2. Misconfigured APIs 3. Lack of multifactor authentication for users 4. Incomplete data deletion. etc.
2. How long does a cloud security scan take?
Scanning a cloud infrastructure with an automated scanner can take up to 24 hours. Detecting and reporting all vulnerabilities by engaging manual pentest can take up to 7 days.
















