The AWS cloud environment is one of the most used cloud platforms in the world. It provides a heightened level of flexibility in terms of storage, security, and functionality. However, cloud platforms are not without their challenges in terms of security.
The shared responsibility model opted for by cloud platforms makes you an important entity in protecting your and your customers’ cloud assets. This is where AWS vulnerability scanning becomes an undeniably important practice to maintain.
This article details on what AWS vulnerability scanning is exactly, its importance, scope of scanning, best practices and more.
What Is AWS Vulnerability Scanning?
AWS vulnerability scanning is the process of detecting vulnerabilities in the AWS deployments – applications running on AWS, and the data management processes. You can use an automated vulnerability scanner to detect anomalies, deviations from security best practices, and security misconfigurations in the cloud.
Importance of Conducting AWS Vulnerability Scanning
Conducting AWS vulnerability scanning affords more protection to your AWS infrastructure. Let’s break this down to understand the importance of AWS vulnerability in clearer detail.
- Finding weaknesses: Identifying vulnerabilities within the AWS infrastructure can help in their timely mitigation and avoid any further complications arising from malicious attackers exploiting the vulnerability.
- Protection of sensitive data: Continuous vulnerability scanning reduces the number of vulnerabilities present at a given time and increases the protection of sensitive data of customers and their applications.
- Meeting Compliance: As a part of maintaining good security posture and global compliance standards, you must carry out continuous or regular vulnerability scans. They are usually recommended by GDPR, HIPAA, PCI-DSS, and SOC2 and in the shared responsibility mentioned by cloud providers.
Scope For AWS Vulnerability Scanning
As a customer, conducting AWS vulnerability scans is crucial to maintaining your AWS environment’s security and the assets within. Usually, the scope of AWS vulnerability scans is carried out from the user end includes:
- Scanning of web applications and their APIs to detect any vulnerabilities.
- Identification and inventory of AWS assets such as EC2 instances and S3 buckets.
- Assessment of the AWS configuration setting in place against best security practices.
- Review of IAM policies and permissions to ensure the least access privilege.
- AWS vulnerability scans also scan the network infrastructure such as VPC configurations to see if any settings are amiss.
How To Conduct Proper AWS Vulnerability Scanning?
There are three main steps to a successful vulnerability assessment of AWS security in the cloud. The first step is to choose a vulnerability scanner that suits your needs as well as AWS guidelines. The second step is the scan itself. Finally, you analyze the detected vulnerabilities and fix them according to a priority index. We will walk you through each of these steps.
Choose the right vulnerability scanner
The easiest procedure for AWS security scanning is installing an instance of a virtual vulnerability scanner directly into AWS. You need to choose a scanner that is designed to work within the AWS shared responsibility model. There are vulnerability scanners that run automated scans while maintaining adherence to the policies set by AWS so that you do not end up violating any of the guidelines.
Running the scan
Once the AWS vulnerability scanner is installed and set up, you can run or schedule a scan. It will probe the AWS deployments by referencing a vulnerability database to find vulnerabilities and loopholes in your systems. The scanner will detect
- Errors in code: Mistakes in software code can allow attackers to attach an endpoint to extract data, or erase data from your software.
- Security misconfiguration: A security misconfiguration is an erroneous security control that could lead to a breach.
- Unpatched software: Software patches are often released to tackle security vulnerabilities. Running outdated, unpatched software can lead to a breach.
Other than these a vulnerability scanner can detect malicious IPs and domains that might be trying to cause harm, issues related to access control, and S3 bucket misconfigurations.
There are certain tests that AWS does not allow you to run like
- DDoS attacks or simulations
- protocol flooding
- resource request flooding
Analyzing and Fixing the vulnerabilities
A good tool with AWS vulnerability management gives you a list of vulnerabilities indexed according to their risk scores. The risk score is a combination of the CVSS score of a vulnerability and the potential damage it can cause in that particular situation. The risk score should take a vulnerability’s general and situational aspects to make an accurate positioning.
You can base your remediation plan on the risk scores associated with vulnerabilities and allocate the resources in a way that does not engage the developers too much and yet manages to cope with the most critical vulnerabilities.
When it comes to fixing the vulnerabilities, you get some recommended steps from the vulnerability scan report itself. If you can also get some help from security experts in terms of reproducing and fixing the issues, the job becomes way easier for your developers.
AWS Vulnerability Scanning Best Practices
Here are some of the best practices to keep in mind for AWS vulnerability scanning:
- Vulnerability Scans: Regularly perform vulnerability scans on your AWS infrastructure. This can help you identify any security vulnerabilities that could be exploited by attackers.
- Automated Vulnerability Scans: Use automated tools to scan your AWS environment for vulnerabilities. AWS provides various tools such as AWS Inspector, which can scan your instances and provide you with a detailed report of any vulnerabilities that are found.
- Activity Monitoring: Monitor your AWS environment for any suspicious activity. You can use AWS CloudTrail to monitor and log API activity in your AWS account. This can help you identify potential security threats, as well as provide a record of all activity within your account for auditing purposes.
- Regular Updates: Regularly update your AWS resources with the latest security patches and updates. This can help reduce the risk of exploitation of known vulnerabilities.
- AWS IAM: Use AWS IAM (Identity and Access Management) to control access to your AWS resources. This can help ensure that only authorized users have access to your resources.
5 things to keep in mind while choosing an AWS vulnerability scanning tool
We will not talk about the price or the reviews here, nor the usual bits about the number of tests and the timeline for the vulnerability scan. We will shed light on some scarcely mentioned issues that can have quite an impact on your experience with AWS vulnerability scanning tools.
- A tool with a CXO-friendly dashboard can save hours of your time. It lets you monitor vulnerabilities, assign remediations, and collaborate with security experts, all from a single place. It helps you move faster, taxes your brain less, and makes life easier for all stakeholders.
- Look for a scanner that evolves. The CVEs are evolving, and new vulnerabilities are emerging constantly. A tool that does not review and revamp the scanner rules regularly, falls behind.
- A tool that has a strong security team behind it comes in handy. Your developers will face some issues while trying to fix vulnerabilities. A little support at that point from security experts can make things smoother.
- Actionable reports and step-by-step guidelines for remediation can help you move ahead with vulnerability management faster.
- Compliance-specific scans add a lot of value to your AWS vulnerability scanning routine.
Isn’t cloud security handled by the cloud provider?
Yes and no. A cloud provider like AWS takes care of certain aspects of the security of your cloud platform and infrastructure. You as a cloud service customer are responsible for certain other aspects of security. This is called the shared responsibility model of cloud security. Your responsibilities are usually determined by the type of service program you are in and the service level agreement between the cloud provider and the cloud customer.
If you think about it, if AWS were to provide vulnerability management for its clients, it would soon turn into a data-privacy nightmare as the cloud provider would require root-level credentials to all its client servers. Hence, it is recommended that an enterprise extend its corporate vulnerability management policies to IP addresses hosted on AWS.
| Type of Cloud Service | Security Responsibilities of Cloud Providers | Security Responsibilities of Clients |
|---|---|---|
| Infrastructure as a Service (IaaS) | Virtualization. Network, Infrastructure, Physical | User Access, Data, Application, Operating System |
| Platform as as Service (PaaS) | Operating System, Virtualization, Network, Infrastructure, Physical | User Access, Data, Application |
| Software as a Service (SaaS) | Application, Operating System, Virtualization, Network, Infrastructure, Physical | User Access, Data |
Security in the cloud – the responsibilities of the AWS customer
The security and compliance responsibilities of the AWS customer are determined by the services that the customer has opted for.
For instance, if you opt for Amazon EC2 (Elastic Compute Cloud) which is categorized as infrastructure as a service (IaaS), you will be responsible for managing and configuring the guest operating systems – you will have to apply the patches where required, and ensure the security of all the applications running on each instance. You will also have to configure the firewall provided by AWS.
S3 buckets are simple and scalable storage units offered by AWS and it is a raging success among enterprise owners as well as developers for their ease of use. But it is also the most common cause of AWS security breaches.
In 2021, a COVID-19 test service center in Utah exposed the personal information of more than 50,000 patients due to an S3 bucket misconfiguration. Similar mishaps have taken place all around the world and affected millions of people. For instance, a company called SeniorAdvisor exposed the information of 3 million senior citizens due to an S3 misconfiguration.
In the cases of AWS S3 and DynamoDB, AWS takes care of the operating system, the infrastructure layers, and the platforms. The customer, who in this case, accesses the endpoints to store and manage data, is responsible for data security – encryption of the data, setting up permissions, classifying the assets, etc.
Each of these areas that are controlled by the customers can incur potential security threats unless they are carefully managed and regularly monitored. This is where AWS vulnerability scanning can help out.
Why choose Astra’s Vulnerability scanner for AWS vulnerability scanning?
The vulnerability scanner by Astra Security is a perfect solution for your AWS vulnerability scanning needs. It is optimized for cloud-based application security testing. It fits in your CI/CD pipeline. It makes it super simple to schedule scans or set up continuous scanning.
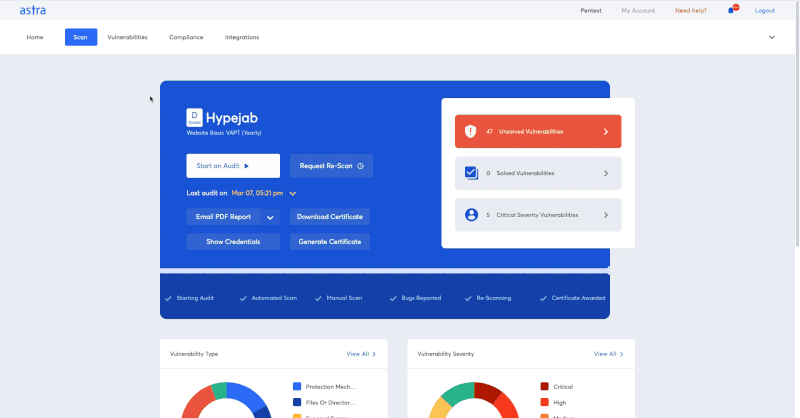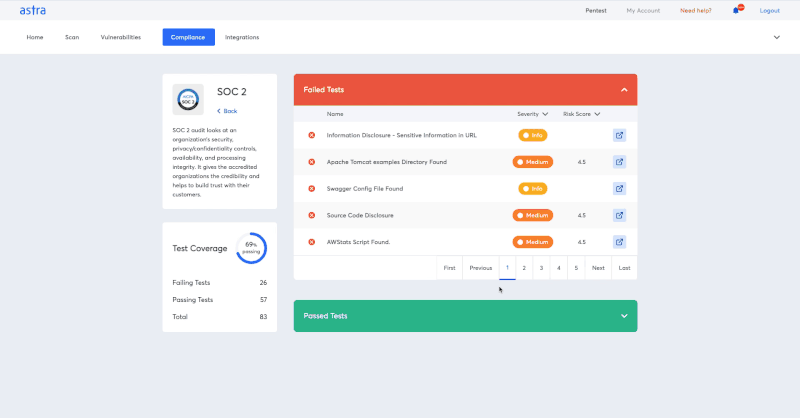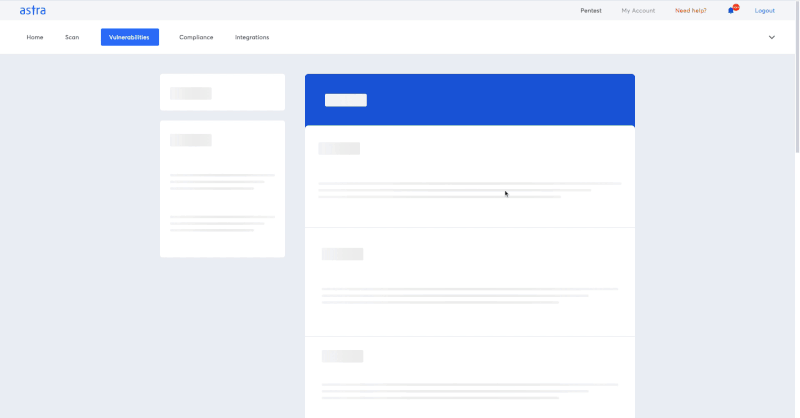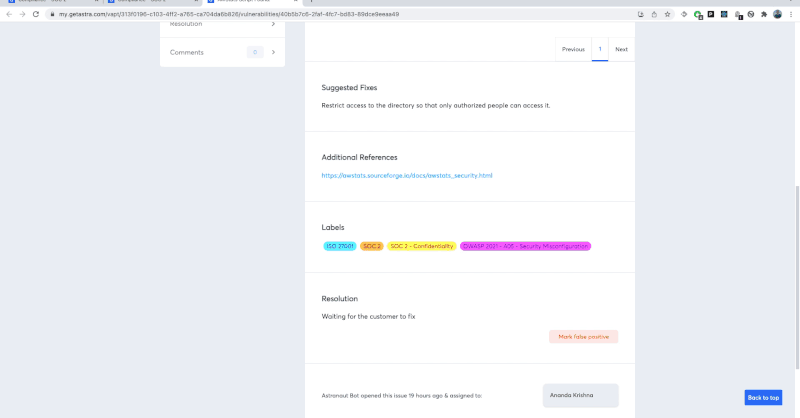
Here’s what you can do with Astra’s vulnerability scanner
- Manage, monitor, and assign vulnerabilities in one place
- Get step-by-step guidelines to reproduce vulnerabilities
- Collaborate with security experts
- Get accurate figures to understand the potential damage caused by a vulnerability
- Run compliance-specific scans to accelerate compliance readiness.
With more than 3000 tests, assured zero false positives, CI/CD integration, and the best-in-class human support, Astra’s vulnerability scanner is quite unbeatable. The outstanding reviews and widespread clientele attest to the same.
Conclusion
Security scans in the cloud environment are difficult given the nature of the policies and the sensitiveness of the assets involved. However, it is a necessary practice and you need to do it regularly. AWS vulnerability scanning comes across as a tricky but necessary task that all businesses using the AWS EC2 or S3 services need to conduct. Having a strong grasp of the particulars of the process helps you a lot. A vulnerability scanning solution that is optimized for the task and can be deployed and scaled easily is what you need to make things easier.
FAQs
1. What is the timeline for AWS security testing?
It takes 4-7 days to complete an AWS security testing, then half as much time to rescan the systems post-remediation.
2. What is the cost for AWS vulnerability scanning?
The cost for vulnerability scanning for AWS can be anywhere between $100 and $500.
















