Enterprise cloud adoption is accelerating, with more companies moving from exploring the use of public cloud infrastructure to providing production services to their clients over public clouds. 67% of enterprise infrastructure right now is cloud-based. For the protection of today’s cloud-based, distributed environments and workforce, traditional security frameworks are unsafe.
With Google Cloud security tools, you can put into practice a zero-trust strategy that safeguards your workforce and workloads by establishing trust in users and resources in a variety of ways and ensuring it remains consistent over time. This article will guide you through various Google security tools, features, and importance as well.
Top GCP Security Tools
The following Google cloud security solutions provide you with in-depth insights to find the critical vulnerabilities in GCP infrastructure and build a secure cloud environment for your business:
- Astra Security
- Chronicle Detect
- Datadog
- Site24x7
- VPC service controls
- Google Cloud Armour
- Google Cloud key management services
7 Best GCP Security Tools
1. Astra Security
Astra Security is an exceptional software that performs a deep scan to find critical security vulnerabilities and misconfigurations in your GCP infrastructure and create a safe cloud environment for your company. Astra’s qualified engineers run specific tests to detect and close gaps in your GCP infrastructure.
To help your CI/CD pipeline integrations, Astra’s testing services seamlessly shift your DevOps to DevSecOps without disrupting your production environment. Astra’s customized compliance scan makes your compliance easy with GDPR, HIPAA, SOC2, PCI-DSS, and ISO 27001.
Astra’s cloud security testing services integration will assist you in getting relevant audit reports without false positives and performing deep authentication scans behind the login to eliminate internal risks.
Publicly verifiable certificates from Astra are given after the application penetration testing service has been completed successfully by fixing flaws and verifying that the fixes have been made.
Through a robust security scanner, the Astra cloud security platform evaluates the security of web applications, mobile apps, and other software by adapting code reviews, performing an in-depth scan against the OWASP top 10 vulnerabilities in web applications, and using fuzzing techniques.
Features
- Astra’s security engine performs comprehensive pentests to detect, identify, and fix your cloud misconfigurations.
- Astra’s offensive guard lets you experience deep back-and-forth rescans for unbreakable security to find vulnerabilities proactively.
- An intelligent scanner integrated with Astra Pentest’s GCP security services performs a 360-degree security audit to uncover vulnerabilities
- Astra Security provides actionable VAPT reports with risk scores
What is good?
- Comprehensive defense against vulnerabilities
- Seamless GCP integration
- Easy-to-use interface for vulnerability management
- Support from experts for prompt assistance
What could be better?
- Complex integration
- New users take more time to learn Astra security
2. Chronicle Detect

GCP Chronicle Detect is one of GCP security products that help businesses find threats on a large scale.
The next-generation rules engine in Chronicle Detect works “at the speed of search” by using the YARA detection language, which was made to describe how threats act.
YARA, which makes it easy to build detections for the MITRE ATT&CK security framework’s methods and techniques.
The end result is an entire platform that will help GCP customers better find risk, put threats in order of importance faster, and fill in security gaps.
Features
- It offers real-time threat indicators
- This platform helps GCP users better spot risk, put threats in order of importance more quickly, and fill in security gaps in their cloud
- Chronicle Detect can find threat patterns by injecting logs from various GCP resources
What is good?
- It offers advanced threat detection and analysis
- Chronicle Detect can scale to meet the goals of the organization.
- Adaptation to more GCP services
What could be better?
- Concerns about data protection and compliance could be raised.
- Possibility of configuration errors causing access control problems
- The price could change based on how much data is processed.
3. DataDog
DataDog is one of the Google cloud platform security tools that provides cloud monitoring and analytics and other solutions to improve the safety of the Google Cloud Platform (GCP). For GCP resources and services, it offers continuous monitoring, alerting, and log management.
Datadog Security will significantly improve your security and compliance posture with over 900 predefined detection rules aligned with MITRE ATT&CK® and compliance frameworks.
Features
- Threats may be quickly analyzed, and security signals can be simply filtered based on essential features like severity level.
- It requires little setup and gives you insight into your network, identity providers, and SaaS apps.
- Integrations with ticketing platforms, chat systems, and remediation tools let you work with more than one team.
What is good?
- Focused threat detection with lower hardware maintenance
- Customize threat rules without knowing a proprietary query language.
- enriches logs and third-party security alerts
What could be better?
- Smaller enterprises may not like the cost structure.
- DataDog implementation and configuration can be difficult for different application stacks.
4. Site24x7
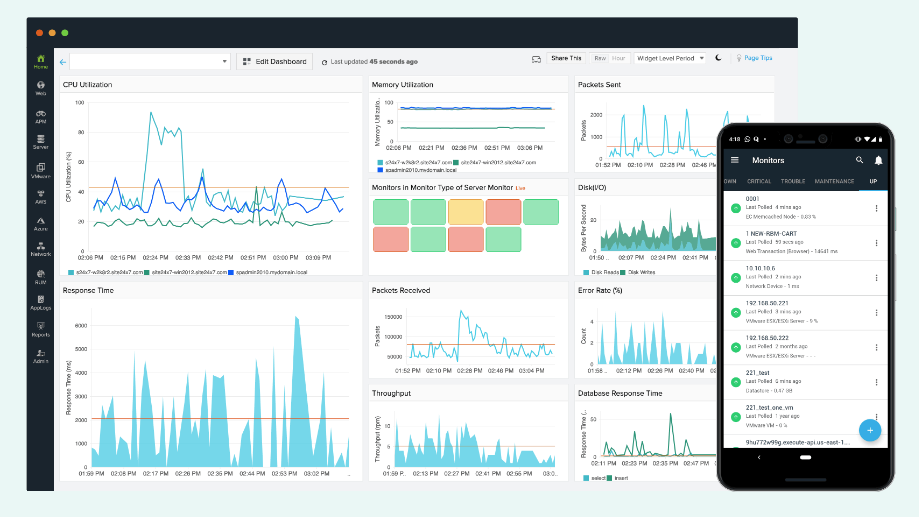
Site24x7 is one among the best GCP monitoring tools that monitors your applications and services running in the Google Cloud and can help you fix slowdowns and optimize performance by tracking your company’s day-to-day activities, utilization of resources, and cloud capacity planning
Since Site24x7 is compatible with several cloud providers, users can keep tabs on GCP and other clouds from a single interface.
Features
- The GCP Cloud Security Scanner automatically checks your web applications for common security flaws to help you spot vulnerabilities.
- Site24x7’s AI engine facilitates rapid bug detection and resolution.
- Start monitoring your cloud apps using Site24x7’s pre-built plugin interfaces for popular platforms, including MySQL, WebLogic, Redis, NGINX, and Hadoop.
What is good?
- With Site24x7, you can manage GCP and other cloud providers from a unified dashboard
- Notifications can be created based on achieving certain levels of performance.
- Custom dashboards and reports for decision-making and optimization
What could be better?
- Setting monitoring can take time.
- As the number of monitored resources and monitoring frequency increase, Site24x7’s pricing may concern some organizations.
5. VPC Service Controls

Access restrictions for the internet, service to service, and VPC to service are all fully covered by VPC Service restrictions.
Its robust security logging features enable monitoring access denials and continuously identifying potentially harmful behavior.
Through the secure configuration of hybrid environments with Private Google Access, private communication between VPC networks and cloud resources is made possible.
Companies and vendors have total control over secure communication with this Google Cloud security solution, and they can create context-aware access based on factors like IP address and user identification.
Features
- On Google Cloud Platform (GCP), VPC Service Controls extend security perimeters around your cloud resources to add an extra layer of security.
- It lets you set access boundaries to prevent communication between resources inside a Virtual Private Cloud (VPC) and other services outside the VPC.
- By limiting unauthorized access to critical information or resources, VPC Service Controls give you the ability to reduce the risks of data exfiltration.
What is good?
- Additional security measures to safeguard cloud resources
- Granular control over communication and access restrictions inside a VPC
- Risks of data exfiltration and unauthorized access reduction
What could be better?
- Difficulty in establishing and maintaining access limits
- Impact on latency and network speed that could occur
- Limited protection within the VPC limits
6. Google Cloud Armor
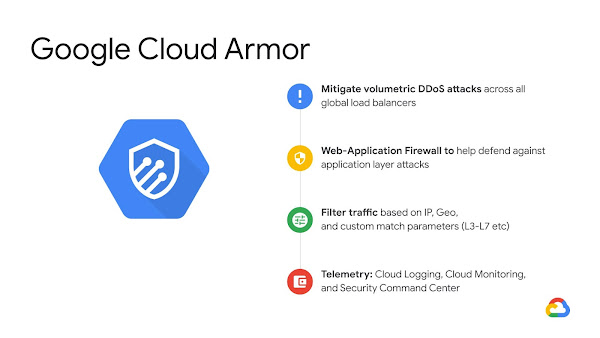
Google Cloud Armor is a powerful security tool that aids in defending your websites and applications from various dangers, including denial-of-service assaults and web-based attacks.
It offers enterprise-grade security for your deployments with features like DDoS defense, adaptive ML-based defense against Layer 7 attacks, and pre-configured WAF rules to prevent OWASP Top 10 risks.
This Google Cloud Platform security application combines rate-limiting capabilities to guard against request floods with bot management and reCAPTCHA Enterprise to prevent fraud.
Features
- A web application firewall (WAF) solution called Google Cloud Armor in Google Cloud Platform (GCP) guards your apps against frequent web-based threats.
- It offers customizable security rules and policies to filter and stop unwanted traffic and protect against risks like SQL injection, cross-site scripting, etc.
- To defend against distributed denial-of-service (DDoS) assaults, Cloud Armor uses Google’s extensive worldwide infrastructure and DDoS defense capabilities.
What is good?
- Security from web-based threats
- Adaptation to Google’s worldwide infrastructure
- Real-time logging and monitoring tools
What could be better?
- False positives or false negatives could occur.
- It has to be correctly set up and tuned for maximum efficacy.
- Added expense because it is a distinct service
7. Google Cloud Key Management Service (KMS)

Key Management Service (KMS) from Google Cloud gives users command over their data’s encryption. While it is in transit, data kept in the Google Cloud is, by default, encrypted.
Key management methods provided by Cloud KMS include employing customer-managed encryption keys (CMEK), importing custom keys, and using hardware and software backends.
Customer control, access monitoring, regionalization, durability, and security are the main pillars of this Google Cloud Security Tool’s architecture.
Features
- A safe and scalable method for managing cryptographic keys and data encryption in Google Cloud Platform (GCP) is the Google Cloud Key Management Service (KMS).
- You can use it to create, store, and manage access to the encryption keys to safeguard sensitive data across all GCP services and apps.
- You may specify who can use, manage, and administer the keys with the help of Cloud KMS, which offers a central key management system with fine-grained access control.
What is good?
- A scalable and secure method of handling cryptographic keys
- Fine-grained access control with centralized key management
- Support for compliance via audit logs and key versioning
What could be better?
- The learning curve for people who are not accustomed to managing cryptographic keys
- The added expense is that KMS is an independent service.
- Requires adequate setup and execution to guarantee efficient protection.
How To Choose The Best GCP Security Tools
1. Security Requirements:
Understand your organization’s specific security needs. Look for GCP tools that address your unique threats and vulnerabilities, ensuring comprehensive protection.
2. Integration with GCP:
Seek google security tools that seamlessly integrate with GCP. This integration leverages GCP’s native security features, providing better visibility and control over your cloud infrastructure.
3. Industry Reputation and Reviews:
Research GCP security tools with a strong industry reputation and positive reviews. Check customer testimonials, case studies, and industry reviews to gain insights into their performance and customer satisfaction levels.
4. Compliance and Auditing:
You may have specific regulatory obligations to fulfill, depending on your industry. Ensure google security tools you choose has robust auditing capabilities and support relevant compliance standards such as GDPR, HIPAA, PCI DSS, or ISO 27001.
5. Scalability and Performance:
Assess the scalability and performance of the security tools. Confirm that they can handle the size and complexity of your GCP environment. Scalable google security tools ensure consistent protection as your infrastructure grows.

Conclusion
To protect your cloud infrastructure, GCP security tools provide a unique fusion of innovation and expertise.
You can create a robust security architecture by utilizing GCP tools like Astra Security, Cloud IAM, Cloud Data Loss Prevention, Cloud Security Scanner, VPC Service Controls, Google Cloud Armor, and Google Cloud KMS.
These GCP tools safeguard business data, streamline compliance administration, improve visibility, and provide secure communication within your cloud environment.
Utilize these google security tools’ interactive features, intuitive user interfaces, and cutting-edge capabilities to improve your cybersecurity posture in the elegant world of cloud computing.
Frequently Asked Questions
What are the security measures in GCP security tools?
Secure infrastructure, data protection, identity and access management (IAM), threat detection and prevention, compliance, and governance are just a few of the security features offered by GCP security solutions. Secure data centers, network security, encryption, IAM with granular access controls, threat monitoring, anomaly detection, compliance certifications, and organizational policies are a few of these measures.
What is the IAM security tool in GCP security tools?
Identity and Access Management, or IAM, is a term used in GCP security. Users may manage access to services like Cloud Storage, Compute engines, and more with complete control over their Google Cloud resources.
IAM enables policies to limit access and uses roles and procedures to establish permissions.
What is the Cloud Security Command Center (Cloud SCC)?
The Cloud Security Command Center (Cloud SCC) gives a thorough inventory of your cloud assets, identifies threats and vulnerabilities, and provides repair advice that can be implemented. It streamlines security administration when integrated with outside solutions.














