Healthcare statistics by HIPAA revealed that healthcare cybersecurity incidents fell by 8% in February 2022 but still faced 46 incidents affecting 2.5 million people.
HIPAA compliance is vital for data safety and security within the healthcare industry. Continued compliance with HIPAA helps avoid drastic, damaging, and expensive scenarios that not only affect the organization but hundreds and thousands of individual patients too.
This is why HIPAA vulnerability scan comes as a vital requirement in today’s efforts to keep healthcare data like PHI, medical records, patient personal information, and more, confidential and protected at all times. Let’s take a deep dive to see why HIPAA vulnerability scan is and should be all the rage in the healthcare industry.
Why is Astra Vulnerability Scanner the Best Scanner?
- Runs 8000+ tests with weekly updated scanner rules
- Scans behind the login page
- Scan results are vetted by security experts to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities from one place.
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Integrates with Slack and Jira for better workflow management
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

HIPAA Vulnerability Scan: Is It Necessary?
One of the mandates set forth by HIPAA requires a regular risk analysis or assessment of the security features deployed for protecting confidential healthcare information. However, HIPAA does not specify what kind of risk assessment is to be performed and this decision is left to each individual organization.
Organizations like hospitals, healthcare centers, medical institutions, and others can choose as they see fit between two major types of risk assessment, i.e. HIPAA vulnerability scans or HIPAA penetration tests.
A HIPAA vulnerability scan can help organizations identify areas of weaknesses within their cyber security system before it is exploited by any malicious entity.
Before we explore the pros of HIPAA vulnerability scans over pentests, let us first read more about its compliance requirements, steps and other facets that make HIPAA compliance through vulnerability scans absolutely critical.
HIPAA Compliance Requirements
Here are some the compliance requirements that need to be met by any healthcare organization to stay compliant with HIPAA.
1. Risk Analysis
Risk analysis is the process of scanning and or analyzing an organization’s security system to identify vulnerabilities that could cause potential damage to the sensitive data stored by that organization. This can range from confidential patient health information to various results from tests.
HIPAA compliance requires risk analysis to be done continuously in order to ensure constant high-level protection from threats that look to access and exploit personal healthcare information.
However, it does not mention a specific type of risk analysis which leaves the decision of choosing between penetration tests and vulnerability assessments to the organization itself.
Regular HIPAA vulnerability scans are comprehensive and in-depth. This is because it scans for vulnerabilities to assess the enormity of a potential hack using that vulnerability.
2. Vulnerability Fixing
HIPAA compliance requires that once the risk assessment is successfully completed, proper steps to remediate the vulnerabilities and areas of non-compliance be done as soon as possible.
Not doing so can leave the security system exposed and vulnerable to a host of threats like a data breach, deletion, or theft. Once the penetration testing is done, a detailed report is generated that mentions the scope of testing, rules of engagement, and a list of vulnerabilities found with an executive summary.
The vulnerabilities listed will also have all their information including actionable risk scores for prioritization and remediation measures which can help in the immediate fixing of vulnerabilities.
3. Employee Training
All healthcare sector employees must be mandatorily made to attend HIPAA security compliance training as it will help them gain a better understanding of how to securely handle PHI.
It will also clarify the do’s and don’ts, compliant and non-compliant posture revolving around PHI. Such training should be offered periodically to ensure that all employees are updated on the relevant information.
Along with this, such training also gives employees a better understanding of the seriousness of mishandling PHI and violating HIPAA security compliance.
4. HIPAA Email Compliance
HIPAA-compliant emails ensure that the contents within the emails, like patient health information, are safely and securely delivered to the receiver. A HIPAA-compliant email must be encrypted to protect the data or information that is to be sent.
Risk analysis is another way to go to ensure that an email is HIPAA compliant. Using email disclaimers, confidentiality notices, strong passwords, and multifactor authentication are also ways to ensure that an email with sensitive data is being handled carefully.
5. Monitoring Compliance
In order to maintain compliance and or achieve HIPAA security compliance, continuous monitoring with HIPAA vulnerability scans is a must to identify any new vulnerabilities that pose a threat to an organization’s online security.
The tools opted for HIPAA risk assessments must be fully integrated with the security system in order to provide automated continuous monitoring. It should also ensure that there will not be any false positives which could lead to unnecessary expenditure of resources like manpower, time, and expense.
Steps In A HIPAA Vulnerability Scan
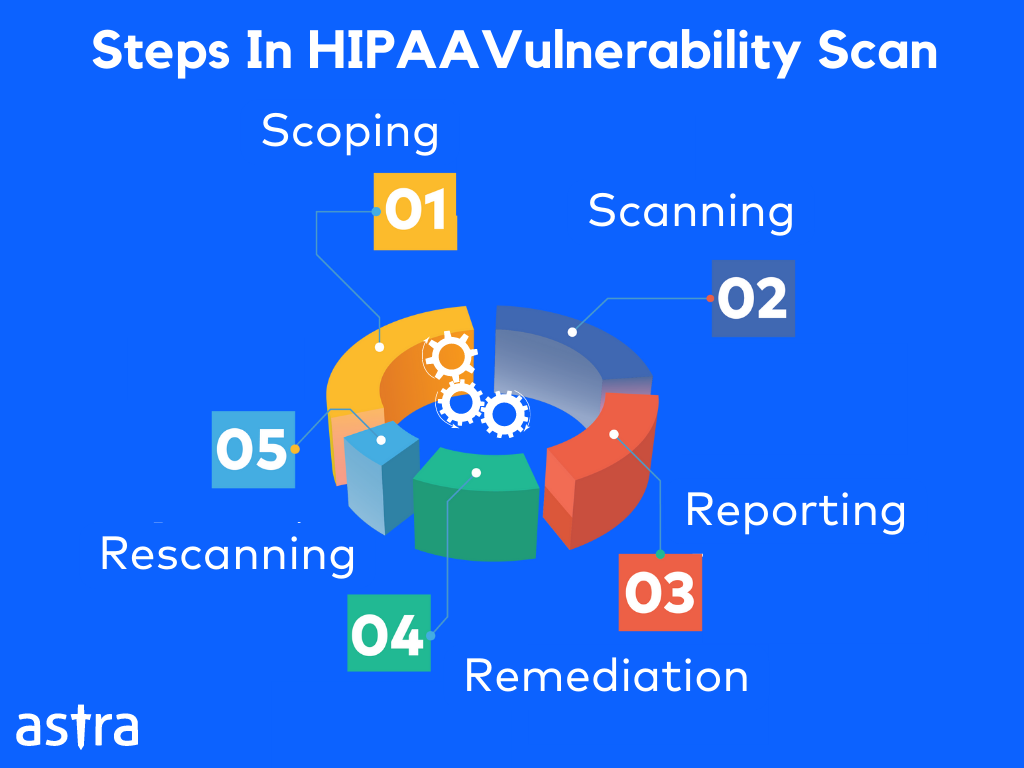
The steps in a HIPAA vulnerability scan are as follows:
1. Reconnaissance
Reconnaissance refers to the researching phase of the pentest where the pentesting teams aim to find all the information they can about the target that is publicly available. This is done after scoping where all the assets are to be tested, and the reasons and the limits are discussed so as to avoid any legal troubles and scope creeps.
There are two types of reconnaissance, active and passive reconnaissance:
Active reconnaissance refers to finding information about the target through thorough interaction with it. This type of surveillance requires prior permission from the target.
Passive reconnaissance refers to finding information without any interaction from the actual target but through online resources that are publicly available like websites for example.
2. Scanning
This is the phase where the information from the reconnaissance is scanned to find different vulnerabilities which are identified based on a vulnerability database of known CVEs, as well from OWASP Top 10 and SANs 25.
Vulnerabilities can also be found using an automated comprehensive vulnerability scanner the results of which can be vetted with a manual pentest to avoid any false positives.
3. Reporting
Once the vulnerability scanning is done, a detailed report is generated with an executive summary. It also includes information on the scope of the scan, rules of engagement, methods employed, and lastly, a list of the vulnerabilities found.
Each vulnerability is explained in detail with its CVSS scores, its impact on the security system, and actionable risk scores for prioritization and remediation measures. Some companies offer additional assistance through POC videos and customer assistance.
4. Resolution
Once the target organization obtains the detailed report upon the scan completion of its assets and its security, it is used to rectify and remedy the vulnerabilities found. This helps avoid any breaches and threats to security.
5. Rescanning
This is the last step in the vulnerability assessment procedure to safeguard the fixes made to the security of an organization’s assets. The security system is rescanned once the fixes are made to find any additional or new vulnerabilities that could have risen from the patching.
Once this step is complete and zero vulnerabilities have been detected, the organization’s online security can be said to be completely safe.
Pros Of HIPAA Vulnerability Scans Over HIPAA Pentests
Regular HIPAA vulnerability scans or HIPAA pentests form the backbone of maintaining HIPAA compliance and keeping confidential healthcare information, safe and secure.
However, when opting between the two, HIPAA vulnerability scans do have a few pros over HIPAA pentests as listed below.
- HIPAA vulnerability scans are a quick and easy solution to maintaining compliance continuously.
- It is also far more affordable when compared to the traditional methods of penetration testing which can weeks based on the size of scope and manpower.
- Vulnerability scans can be automated which saves copious periods of time and energy.
- Automated HIPAA vulnerability scans can also be carried out continuously like weekly, monthly, or quarterly unlike pentests which are carried out far more sporadically.
- Vulnerability scan results can be vetted by pentesting professionals to weed out the false positives, thus saving your time considerably.
Here are some of the cons of vulnerability scanning over pentests:
- Might not be as comprehensive as a pentest.
- Doesn’t confirm the exploitability of a vulnerability.
- False positives are a possibility that needs to be vetted.
HIPAA Rules
HIPAA regulation is governed by two major elements that need to be abided by:
1. Security Rules

HIPAA’s security rule outlines various safeguards to adhere to for the optimal protection of PHI (Patient Health Information). They include administrative, physical, and technical strategies.
- Administrative
Administrative safeguards are essentially a guide for employees on how to handle PHI safely. These are implemented to train employees through thorough staff training on the safe handling of patient information and to place emergency protection plans for PHI by assigning a privacy official. Lastly to monitor and test the security that is placed to protect the PHI through risk assessments.
- Physical
This refers to protecting the physical access points to PHI. It also includes setting guidelines of best practices to be followed by employees to prevent the unwanted dissemination or leak of information from their workstations and other portable devices.
This includes installing alarm systems, ID badge access entry, surveillance cameras, and more.
- Technical
This refers to adding anti-virus, anti-malware, or data encryption for data stored in order to ensure that the information is not accessed without proper authorization, or that it isn’t altered, deleted, or stolen.
2. Privacy Rules
The privacy rule is instigated to protect the personal health information of people. Privacy rules put forth by HIPAA allows organizations and healthcare providers to follow best practices, rules, conditions, and limitations in accordance with patients’ authorization.
HIPAA’s privacy rule gives individuals rights over their protected health information such as the right to examine or obtain a copy of it, or the transfer of such records electronically as well as the ability to request corrections.
Records with HIPAA identifiers can only be used or can be released with due authorization and waivers from the patients.
The privacy rule permits the disclosure of patient PHI without authorization but with detailed conditions in the following cases:
- To business associates.
- Public health purposes as and when required by state and federal law.
- Public agencies oversee activities like audits, inspections, and legal proceedings.
- To law enforcement officials.
- For legal proceedings when demanded through a court order.
- For research purposes.
What Are HIPAA Identifiers?
HIPAA identifiers are elements of information within a patient’s private medical record that can be used to identify, contact, or location an individual. Documents with such identifiers can only be released or used with the patient’s written consent or waiver.
The following are the various elements that are categorized as identifiers by HIPAA:
- Names
- Addresses including street names and zip codes.
- All dates from birth dates to death of death, date of admission, and discharge.
- Telephone and fax numbers
- Email address
- Social security number
- Email addresses
- Medical record and health plan beneficiary numbers
- Account and license number
- Vehicle identifiers like license and serial numbers.
- Device identification numbers
- Web URLs and IP addresses
- Biometric identifiers like fingerprints.
- Full-face photographs.
- Any other characteristic that is unique to the individual.
Any document with such information needs to be tightly protected in healthcare organizations according to HIPAA’s security and privacy rules. Thus making HIPAA vulnerability scans the best way to protect such pivotal private information.
Are All Health Information Considered As PHI In HIPAA?
There is a rather common misconception that all health information is considered PHI according to HIPAA. However, this is not the case. According to HIPAA, health care information or patient data is only identifiable or acts as an identifier for health progress, and bill payments, among others.
PHI ceases to be PHI if all the identifiers in the data are removed. Such data is said to be de-identified.
According to HIPAA, health information is considered PHI if it involves information recorded by a healthcare entity regarding your mental and physical health as well as its prognosis.
Conclusion
HIPAA compliance is a critical norm to adhere to in the healthcare industry. One of the best ways to achieve this is by carrying out automated HIPAA vulnerability scans regularly as a method of risk analysis mandated by HIPAA.
Ensure the health of your organization today by teaming up with Astra for achieving and maintaining your HIPAA compliance!
FAQs
What are three security safeguards placed by HIPAA?
HIPAA has three major safeguards:
1. Administrative which includes risk assessments and staff training.
2. Technical which includes implementing MFA and data encryption.
3. Physical security which includes placing surveillance cameras and more.
What is the purpose of HIPAA?
The Health Insurance Portability and Accountability Act is designed to protect people covered by health insurance and also to secure their protected health information from any breaches and or theft.
What is protected by HIPAA’s Privacy rule?
HIPAA’s privacy rule protects all protected health information stored or transmitted through electronic, media, or paper.
















