Around 69% of all vulnerabilities are accounted for by CVEs with a network attack vector. With vulnerabilities seeing an ever-rising high, vulnerability scanners are becoming a priority for organizations.
However if you are undecided on the free online vulnerability scanners to choose from, here’s we list down some of the best features to look for in a good vulnerability scanner as well mention some commercial and free online vulnerability scanners for you to pick from!
Top 10 Free Online Vulnerability Scanners 2024
Why is Astra Vulnerability Scanner the Best Scanner?
- Runs 8000+ tests with weekly updated scanner rules
- Scans behind the login page
- Scan results are vetted by security experts to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities from one place.
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Integrates with Slack and Jira for better workflow management
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

Features To Look For In Reliable Free Online Vulnerability Scanners
Here are some of the features of free online vulnerability scanners:
1. Scan Capacity
Though limited when compared to commercial vulnerability scanners, free online vulnerability scanners can target networks, APIs, and websites to detect any potential vulnerabilities through port scanning, and web and API scanning.
2. Scan Frequency
Ensure that the scanner is capable of detecting vulnerabilities at a fast rate based on a known database. Make sure it provides continuous regular scans for your networks to detect any anomalies in the security.
3. Evolving Vulnerability Database
Ensure that the vulnerability database is constantly updated based on the latest CVEs, intel, bug bounty reports, and other sources of information regarding new vulnerabilities. This ensures that the vulnerability scanner you opt for will have a higher chance of discovering any and all the latest security threats.
4. Report Generation
The vulnerability scanner should provide detailed reports with all possible information about the vulnerabilities found. It should include the vulnerability’s CVSS scores, an explanation of what the vulnerability is and how it affects the asset’s security, along with remediation measures for each vulnerability.
5. Rescanning
This is an important aspect that should not be overlooked as rescanning allows you to verify the fixes made based on the initial vulnerability scan. It also helps find any vulnerabilities missed during the initial scan.
6. Support
Although traditional one-on-one customer support is hard to come by with free vulnerability scanners, open-source tools are maintained by large communities of security professionals who share their knowledge and help with issues encountered.
These are the features offered by tools that provide free vulnerability scanning. However, these scanners offer limited to no help in terms of remediation and customer support.
Hence it is prudent to consider the features of commercial scanners to make an informed choice that secures your assets.
Features Applicable To Paid Vulnerability Scanner That You Should Consider
Here are some of the features of commercial vulnerability scanners.
1. Compliance Scanning
The vulnerability scanner should also scan for areas of non-compliance to various regulatory standards. Employ a vulnerability scanner that can help assess your networks for discrepancies in compliance so that you can remedy them quickly. This should include PCI-DSS, HIPAA, SOC2, ISO 27001, and GDPR.
2. Customer Support
The scanner tool should provide an excellent customer experience in terms of clearing queries and helping customers understand the various remediation measures offered by their reports. Make sure that the customer service and remediation assistance are provided by experts who can help you resolve doubts efficiently and effectively.
3. False Positive Vetting
Make sure that the results of the scan can be vetted by a scanning team to avoid all false positives, and also conduct scans behind logins.
4. Remediation Measures
Remediation is another important aspect to consider when choosing a vulnerability scanner. This decides the level of support you will receive upon completion of a vulnerability scan in terms of report generation and the remediation steps mentioned for each discovered vulnerability.
14 Top Free Online Vulnerability Scanners
This list contains detailed information about tools that provide free vulnerability scanning through trial periods and as open-source tools.
1. Astra Pentest
A comprehensive penetration testing platform for web applications, mobile applications, APIs, and cloud infrastructures.
Features
- Scanner Capacity: Unlimited continuous scans
- Manual pentest: Available for web app, mobile app, APIs, and cloud infrastructures
- Accuracy: Zero false positives
- Vulnerability management: Comes with a dynamic vulnerability management dashboard
Astra Vulnerability Scanner provides a free web vulnerability scanner that scans for blacklisting, and SEO spam and also carries out general security checks for your website.
The free website scanner is available without a trial period. Other comprehensive paid vulnerability scanning packages (with vulnerability management) are also available with the following features:
Astra Vulnerability Scanner
Astra’s free scan or trial scan uses NIST and OWASP methodologies to give a brief scan of your system.
Astra Pentest provides continuous scanning facilities with its comprehensive scanner that is capable of conducting more the 8000 tests to find any and every hidden vulnerability.
It offers deep scans for web applications, APIs, networks, mobile applications, and cloud infrastructure at a cost.
Detailed Reports
Once the vulnerability scanning is completed a report is generated which includes the scope of testing, a list of vulnerabilities found, their details, and possible remediation measures.
It also mentions its CVSS score and Astra goes a step further by providing customers with an actionable vulnerability risk score based on which critical vulnerabilities can be prioritized.
Other features offered by Astra vulnerability scanner for its paid packages include:
Intuitive Dashboard (CXO friendly)
Astra’s vulnerability scanner boasts a CXO-friendly dashboard that is super easy to navigate. It displays the vulnerabilities as and when they are found.
Members of the development team can be added to the dashboard to collaborate with pentesters for quicker vulnerability resolution.
The dashboard also offers the option to comment under each vulnerability so that the development team can clear queries quickly.
CI/CD Integrations
Astra offers CI/CD integration services for organizations. This helps companies move from DevOps To DevSecOps, thus giving more priority to security within every phase of a project’s development. It offers integrations with Slack, GitHub, and GitLab to name a few.
Compliance-specific Scans
Astra offers the option to scan for specific compliances required by your organization. It provides a compliance-specific dashboard where you can opt for the specific compliance to scan for.
Once the scan is complete the results reveal the areas of non-compliance. Compliance-specific scans provided by Astra include PCI-DSS, HIPAA, SOC2, ISO 27001, and GDPR.
Remediation Support
Once vulnerability scanning with Astra is complete Astra also provides detailed steps for remediation based on risk prioritization. This is done with the aid of POC videos and collaboration within the vulnerability dashboard.
Pros
- Free website scanning for general security checks.
- Can detect business logic errors and conduct scans behind logins.
- Provides rescanning upon successful remediation of vulnerabilities.
- Provides compliance-specific scans and reports.
- Ensure zero false positives through vetted scans.
Cons
- Could have more integrations.
2. Intruder
Features:
- Scanner Capacity: Websites, servers, and cloud
- Manual pentest: No
- Accuracy: False Positive Present
- Vulnerability management: No
Intruder is a leading vulnerability scan and penetration testing service provider. It provides a free windows vulnerability scanner with a 14-day trial period for its Pro Plan scanning services which can be availed.
It has a comprehensive security scanner that is capable of detecting flaws manually and through automated means across a whole large infrastructure.
Lots of tests are available to check for even historic vulnerabilities and new ones.
Pros
- Its interface is easy-to-use with a powerful scanner.
- Cloud-based data security audit solution.
- Provides integration opportunities with Jira, Slack, and more.
- 14-day free trial period.
Cons
- Does not provide a zero false positive assurance.
- Reports are difficult to understand.
3. Qualys
Features:
- Scanner Capacity: Web applications, cloud
- Manual Pentests: No
- Accuracy: False positives possible
- Vulnerability Management: Yes
Qualys provides its cloud customers with continuous monitoring, vulnerability scanning and management, compliance solutions, and web application firewalls.
Qualys provides its scanning solution for a free trial period of 30 days and allows the trial of all their cloud based applications.
Besides its notable vulnerability management services, Qualys also offers network mapping and detection, vulnerability prioritization and remediation as well as cloud security.
Pros
- Timely alerts and responses.
- Well-designed and easy-to-navigate user interface.
- Constant updates ensure the current security measures for the cloud environment.
Cons
- Limited scheduling options.
- Scans are not applicable to all applications.
4. HostedScan Security
Features:
- Scanner Capacity: Web applications, cloud
- Manual Pentests: No
- Accuracy: False positives possible
- Vulnerability Management: No
This vulnerability scanning service provides scans for networks, servers, and websites for vulnerabilities and flaws.
HostedScan Security provides a free online vulnerability scanner for web applications, servers, and networks.
It has user-friendly dashboards so that anyone can manage their reports and risks without any hassle.
Pros
- Provides alerts upon discovery of the vulnerability.
- User-friendly dashboard.
- Supports all scans.
Cons
- The free scans plan is limited to ten scans per month.
5. Probely
Features:
- Scanner Capacity: Web applications, APIs
- Manual Pentests: No
- Accuracy: False positives possible
- Vulnerability Management: No
Probely is designed for web application scanning and API scanning. Probely comes with a free trial period of 14 days for all its packages and provides a Lite package at no cost.
It includes features such as web and API scanning, partial and incremental scans as well as fully featured API.
Probely automatically prioritizes vulnerabilities based on the risk of the vulnerabilities and provides proof of legitimacy for each issue.
Pros
- CI/CD integration
- Spider crawler that crawls JavaScript apps and single-page apps with ease
- Detailed management reports assisting compliance audits
- Interactive dashboard
- Scalable application scanning
Cons
- Not much feedback while the scan is running.
- Custom vulnerability scoring does not align with general scoring.
6. ZAP
Features:
- Scanner Capacity: Web application security testing, network ports, and API testing
- Manual pentest: Yes (Used by experts to carry it out)
- Accuracy: False positives possible
- Vulnerability management: No
ZAP is perhaps the best of free pen test tool available that is open-source and provided by OWASP. It can be used for Linux, Microsoft, and Mac systems to run penetration tests on web apps to detect a variety of flaws.
Pros
- Sends automated alerts after crawls and scans
- Perfect for beginners and experts alike.
- Open-source online penetration testing tool.
Cons
- Can be slow.
- Reports can be cluttered and long.
7. Wapiti
Features:
- Scanner Capacity: Web application security testing
- Manual pentest: No
- Accuracy: False positives possible
- Vulnerability management: No
Wapiti is an open-source web application security scanner that is used to scan a website and find vulnerabilities.
Wapiti offers several inbuilt features that help with performing a penetration test on a website. The tool is written in Java and hence is cross-platform.
It uses a vulnerability database that is updated daily to ensure that it provides accurate reports.
Pros
- Detects a wide range of vulnerabilities
- Black -box pentesting by scanning
- Scans web pages and injects data
Cons
- Not suitable for beginners
- Requires the knowledge of a lot of command lines.
8. WebScarab
Features:
- Scanner Capacity: Web applications
- Manual pentest: No
- Accuracy: False positives possible
- Vulnerability management: No
WebScarab is a free, open-source vulnerability scanner developed by OWASP. It is a Java-based security framework used for analyzing web applications that use HTTP and HTTPS protocols.
It has many features like Spider for finding new URLs for target websites, a Proxy to observe traffic, along with detection of common vulnerabilities like SQL injections, XSS, and more.
Pros
- Can easily extract scripts and the HTML of the page
- Can take control of requests and response
Cons
- Not ideal for beginners.
- Must have a good understanding of HTTP protocol
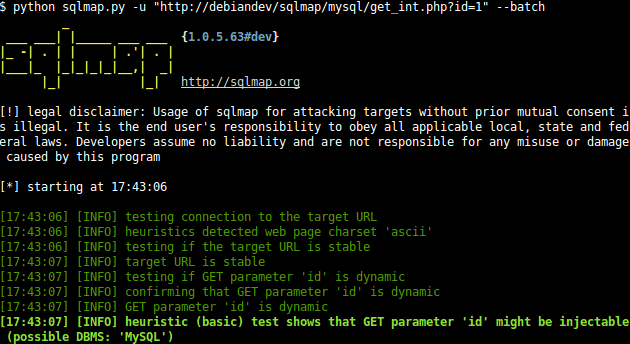
9. SQLmap
Features:
- Scanner Capacity: Web applications
- Manual pentest: No
- Accuracy: False positives possible
- Vulnerability management: No
Yet another important open-source tool for penetration testing online, SQLmap is the best tool for finding SQL injections vulnerabilities through thorough scans of web applications.
The found SQL injections are exploited automatically and are popular for various database servers like Microsoft, MySQL, IBM, Oracle, and more.
Pros
- Open source website penetration testing tool
- Supports servers like MySQL, and Microsoft Access.
- Automated methods of finding various types of SQLs.
Cons
- No graphical user interface.
10. Nmap
Features
- Scanner Capacity: Usually scans the 1000 most popular ports of each network protocol
- Manual pentest: NMap is actively used for network mapping and port scanning. These are parts of the manual pentest effort.
- Accuracy: Occasionally shows false positives and faulty insights
- Vulnerability management: No
Nmap is an open-source vulnerability scanner that helps with cloud network discovery, management, and monitoring. This free network vulnerability scanner is designed to scan large cloud networks, however, it also works fine against singlet networks.
Pros
- Shows open ports, running serves, and other critical facets of a network
- Freely available.
- Usable for large and small networks alike
Cons
- The user interface can be improved.
- Might show different results each time.
11. Arachni
Features:
- Scanner Capacity: Web applications
- Manual Pentests: No
- Accuracy: False positives possible
- Vulnerability Management: No
Arachni is an open-source high-performance Ruby framework that is primarily directed toward helping with pentesting activities. It also allows administrators to assess the security of modern web applications.
It is versatile enough to encompass many use cases ranging from the simple command line scanner utility to a global high-performance grid. It runs on the Ruby library which permits scripted audits.
Pros
- Can detect various web application security vulnerabilities.
- XSS, injections, local file inclusion, remote file inclusion, and more.
Cons
- No advanced support
- No official updates since 2017
12. OpenVAS
Features:
- Scanner Capacity: web applications, network protocols
- Manual Pentests: No
- Accuracy: False positives possible
- Vulnerability Management: No
OpenVAS is yet another open-source network vulnerability scanner that is provided by Greenbone Networks.
It’s constantly updated and therefore can carry out over 50,000 tests to detect vulnerabilities.
Pros
- Automated vulnerability scanning is quick and efficient
- Freely available network vulnerability scanning tool.
- Constantly updated
Cons
- Could be difficult for beginners to make use of.
- Automated causes false positives to appear.
13. Wireshark
Features
- Scanner Capacity: Captures live packet data from a network interface
- Manual pentest: Useful tool for pentesting
- Accuracy: Fairly accurate
- Vulnerability management: No
Yet another tool that’s famous among free vulnerability scanning tools is Wireshark which allows the inspection of protocols as well as the analysis of network traffic.
The contributions of numerous expert pentesters all over the world help boost the efficiency and credibility of this pentest tool.
Pros
- Easy to install
- Freely available
Cons
- Can be difficult for beginners to navigate.
- Could improve its user interface.
14. Vega
Features
- Scanner Capacity: Web applications
- Manual pentest: Yes
- Accuracy: False Positives Possible
- Vulnerability management: No
Vega Vulnerability Scanner is a free and open-source web security scanner and web security testing platform to test the security of web applications.
It is also available as a commercial product. Vega was developed by the team behind the popular open-source penetration testing framework, OpenVAS.
Pros
- Provides customizable configurations
- Well designed user interface
Cons
- Not suitable for beginners
- Shows false positives
Benefits Of Free Online Vulnerability Scanners
Free online vulnerability scanners have several benefits, including:
- Convenience: They are easily accessible from anywhere with an internet connection and do not require any installation or setup.
- Cost-effectiveness: They are free, providing a cost-effective way for organizations and individuals to test the security of their systems.
- Initial assessment: They can provide an initial assessment of a system’s security posture, identifying potential vulnerabilities that can then be addressed.
- Automation: They automate the process of identifying vulnerabilities, reducing the time and effort required to perform manual security assessments.
- Regular scanning: They can be used to regularly scan systems, allowing organizations to stay informed about their security status and make timely updates to address any newly discovered vulnerabilities.
However, it’s important to note that free online vulnerability scanners may have limitations, let us see what they are.
Limitations Of Free Online Vulnerability Scanners
Free online vulnerability scanners have several limitations, including:
- Accuracy: The results of these scanners may not always be accurate, as they may not detect all vulnerabilities or may produce false positives.
- Limited coverage: They may not cover all potential vulnerabilities or may only provide a limited assessment of a system’s security posture.
- Depth of analysis: They may not provide a comprehensive security assessment, as the depth of analysis is often limited in free tools.
- No remediation: They do not provide remediation or mitigation suggestions, meaning that organizations and individuals must manually address any vulnerabilities that are identified.
- Slow scan speed: The speed of the scan may be slow, and the process may take a long time to complete, particularly for larger systems.
- Dependency on updated threat databases: The accuracy of these scanners is dependent on the quality and currency of the threat databases they use.
While free online vulnerability scanners can be a useful tool for identifying potential vulnerabilities, they should not be relied on as the sole means of testing the security of a system. It’s recommended to use multiple tools and techniques, and to validate the results with manual security testing using tools like Astra Security.
Different Types of Vulnerability Scans
1. Website
Website vulnerability scan is a process of scanning one’s system to find vulnerabilities that could be hacked by a hacker to gain access to your website. It reveals your web application’s vulnerabilities and prevents data breaches, identity theft, financial loss, and other negative consequences.
The scan searches for different vulnerabilities such as SQL injection, cross-site scripting, and cross-site request forgery.
2. API
An API vulnerability scanning is a process of identifying vulnerabilities in an application programming interface (API). API vulnerability scanning scans the attack surface of an application by simulating the actions of a malicious user to identify any potential vulnerabilities that could be exploited by hackers.
3. Network
Network vulnerability scan check the security of a network to reveal any vulnerabilities that may leave the networks exposed and vulnerable to attacks.
This type of scanning aims to find exploitable vulnerabilities in the system that outside parties could exploit. Network vulnerability scans are performed on the network infrastructure, also known as the backbone of the network.
4. Mobile
Mobile Application vulnerability scanning is the process of scanning a mobile application for security vulnerabilities. The goal of vulnerability scanning mobile applications is to find weaknesses in mobile security and report them to the developers.
5. Cloud
Cloud vulnerability scanning analyzes a cloud computing environment for vulnerabilities that hackers could exploit. Cloud vulnerability scanning is a crucial component of a cloud security strategy because it can reveal potential weaknesses in cloud security controls.
Top Vulnerabilities Found During Scans
Here are some of the top vulnerabilities that are found in networks, web applications and other assets during vulnerability scans.
1. Injections
Injections are small codes like SQL queries that are injected to manipulate networks and gain access through web applications. Once loopholes are identified, they send malware through vulnerable areas to obtain sensitive information.
2. Misconfigurations
Misconfigurations refer to any glitches or gaps in the security measures adopted that can lead to leaving valuable information virtually unprotected. These are some of the major vulnerabilities that lead to big data breaches in cloud platforms, web applications, and more.
3. Weak Passwords
Weak passwords can be easily cracked by attackers using various methods such as brute-force attacks, dictionary attacks, and password-cracking software. Once exploited, they can potentially steal sensitive information, compromise the system’s security, spread malware, or carry out other malicious activities.
4. Vulnerable APIs
Insecure APIs pose a threat by opening channels of communication that can lead to them getting exploited. Insufficient authentication and authorization measures to restrict access to APIs are seen to be one of the most common causes that make APIs an extremely vulnerable region prone to getting attacked.
5. Broken Authentication and Authorization
Not having strong enough authentication and authorization measures, reusing old passwords, and writing them down, can leave the networks vulnerable to exposure. Not having multi-factor authentication measures deployed is a major cause of concern regarding vulnerabilities.
Conclusion
This article not only mentions some of the best free online vulnerability scanners but also some commercial ones like Astra Pentest to give you an alternative to overcome the limitations of free online vulnerability scanners.
The features to look for in a good vulnerability scanner, as well as the common vulnerabilities detected by it, have been explained in great detail within the article.
















