Internet Security for online businesses and applications is an ever pressing issue. While organizations are regularly updating their defense mechanisms against rising cyber-attacks, cyber criminals are constantly finding new hack techniques to break into firewalls and steal sensitive information. 2016 witnessed a steep rise in cyber-crime attacks, all the while with no exception of insider threats getting prominent each year. Enlisted below are some of the most commonly website security leaks encountered by businesses and websites worldwide.
1. Using a default Admin login URL
A major reason why web-users are advised to change their login page is security against brute force attacks. As a good security practice, it is recommended to use a unique, custom Admin URL instead of a default “admin”.
A standard login URL is a potential security risk for a brute force attack, which involves guessing of login credentials until the correct combination is discovered by the attacker. This leaves the attacker with the need to crack only 3 variables – username, password, and login URL.
If web users continue to use the default login URL, this leaves the attacker with only 2 variables to decipher – username and password. By moving your login page to custom Admin URL, it can reduce exposure to scripts which try to break into your site.
2. Weak password vulnerability
You’ve heard this often but weak passwords pose as a huge risk to the security of a website. What’s more perturbing is that sometimes web users, developers or server admins overlook its implications . Following are some of the astounding statistics which reveal the type of passwords that get leaked (source: acunetix blog):
- A detailed analysis of the 2009 Hotmail password leak revealed a staggering 42% of passwords containing only lowercase alpha characters (a-z) with majority of passwords being between 6-9 characters long.
- Another analysis of a 2010 Gawker media website user details leak where over a million user details were exposed revealed that the most popular password was “123456” with “password” being the second most popular. Many users chose their passwords as the media website’s name itself.
- A perusal of the 2013 data leak of millions of Adobe customers inspired a list of worst possible passwords, some of which were ones like “password1”, “letmein”, and “123456”.
The password you choose is the main impediment standing between your information remaining safe or getting exposed. A hacker can easily access your information by using a Brute Force attack – a specially written software which assays a site to login using your credentials. Moreover, if you are using the same password for multiple accounts and one gets compromised, the hacker gains access to all your other accounts instantly.
Weak passwords which are small and contain single form of characters are easily discover-able. Here is an estimate of the amount of time it would take to generate every possible combination of passwords by a hacker for a given number of characters
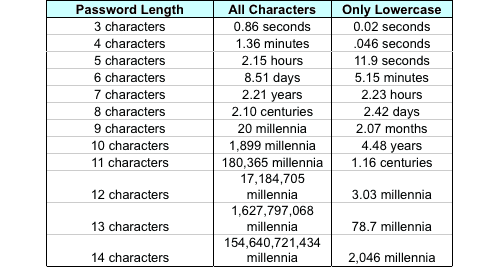
What can you do?
Following measures if pursued during the creation of a password can help reduce the risks and increase internet security of your site.
It is imperative to build a strong password meeting the following requirements:
- Be at least 10 characters long (can be even longer)
- Uses both uppercase and lowercase characters, alpha-numeric characters, including special characters (e.g. !?$)
- Should not be an easy guess like date of birth, parent name, birth city etc.
- Should not be a word from a common dictionary (e.g. apple, radio, laptop)
- Have no part of the username in it
Following additional practices would further ensure internet security:
- Remember to change the password every 2-3 months
- With-hold password information striclty to yourself
- Use salted passwords and cryptographic algorithms for password protected areas of the website (if you are a web developer)
- As a web developer, adding an extra layer of protection against brute force attacks by implementing an account lockout method to disable the account after a number of failed attempts.
Moreover, performing periodic security checks on your website using Astra’s Web Vulnerability Scanner can help you timely fix potential vulnerabilities.
3. Clickjacking
Clickjacking is a commonly used malicious tactic to trick the user into clicking on a button or link controlled by the attacker while ‘hijacking’ it from the original page, by hiding it under multiple complicated layers. This malpractice is widely used to exploit users, especially in e-commerce websites, and has become a dangerous threat.
Clickjacking had made its way to even widely used well known services including Adobe Flash Player and Twitter. An attacker can trick a user into modifying the security settings of Flash, thus allowing any Flash animation to use the computer’s camera or microphone. Whereas in case of Twitter, click-jacking got into a Twitter worm, forcing the users to re-tweet a location and spread it widely before Twitter stepped in to control the virus. In case of websites hosting a payment platform, a click-jacking attack can convince customers to enter their bank details into a third-party page that exactly mirrors the original one.
Preventing Clickjacking
Following practices can prevent your business and employees from becoming a victim of a clickjacking fraud:
- Include X-Frame-Options HTTP header in all your web pages, ensuring protection of your site from being placed within a frame.
- Protect your browser by evaluating and installing browser plugins such as NoScript and NotScript, which in turn induce the users to allow javascript actions on sites they visit frequently and identify trusted domains.
- Another highly effective technique to escape a click-jacking attack is ‘Framebusting’ by checking the Javascript code to detect.
- Splurge on Web Application Firewalls as these will avert any attempts of attacks on your site from attackers trying to inject their code. In the case of businesses that have most of their data on the Internet, this is an important security action.
- Implement E-mail protection by putting up a strong e-mail spam filter. A click-jacking attack via e-mail usually begins through receipt of a harmless and authentic looking e-mail.
4. SQL Injection
SQL Injection has become a rather recurrent issue with database-driven web sites. A flaw in a database can be easily detected and exploited, exposing any site or web application with even a small amount of user base to potential attack. A SQL injection attack allows the attackers to inject a SQL query via the input data from the client to the application. The susceptibility to such an attack often increases when software developers build dynamic database queries that have user supplied input.
An SQL injection, if successful, can tamper with sensitive data from the database, modify the data, execute admin controlled operations on the database such as shutdown of the DBMS or even turn the attacker into the administrator of the database, steal contents of a particular file present on the DBMS file system and gain control of the operating system.
Example of an unsafe SQL code is
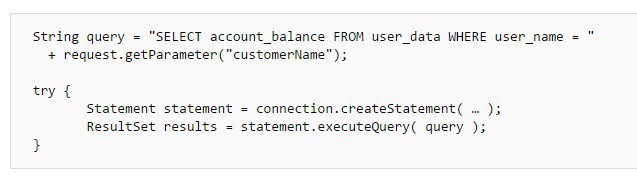
The above method for accessing databases is the most common of all. Here, the unvalidated “customerName” parameter that is simply affixed to the query allows an attacker to inject a SQL code of his/her choice. However, following some basic protection techniques can save you from the trouble of facing an SQL injection attack.
- Use of Prepared Statements (Parameterized Queries): A safer way to build SQL statements is to use parameterized queries rather than dynamic SQL statements. Parameterized stored procedures get compiled before user input is added, thus making it improbable for a hacker to alter a SQL statement.
- Provide Least Privilege: It is imperative to provide “Least privilege” to the account used to create the database connection. For example, if an application requires read-only access, then the account should be given read access only. Moreover, weak error handling is a great way for an attacker to profile SQL injection attacks. Therefore, avoid disclosing any error information.
- Escape all user supplied input: A frail methodology compared to other defenses, input validation can be used to escape user input before putting it in a query. Data validate all external inputs by ensuring that all SQL statements recognize user inputs as variables, and that statements are pre-compiled before the actual inputs are substituted for the variables in Java.
5. Cross-site scripting
Cross-site scripting (XSS) is a type of injection attack wherein malignant scripts are injected into websites to target users. This malicious script appears via a web application – normally in form of a browser side script – and is usually executed as there is no way to know that the script is injected by an attacker.
Doing so, the attacker may gain access to users cookies, session IDs, passwords, private messages etc. He can not only read and access the content displayed to the user, but also compromise the content shown to the user. One such attack occurred in 2014 when the Tweetdeck XSS worm caused a mass compromise of Twitter accounts by allowing the attacker to spread his malicious payload to all Tweetdeck users via Twitter.
Enlisted below are some XSS prevention rules one must follow while putting untrusted data into an HTML document:
- Validation: It is important that all data that is taken from the user on client side and also on server side is strongly typed, following the right syntax, within length boundary, and contains only permitted characters. GET, POST and REQUEST parameters all should be sanitized and validated before storing. This input validation sheet by OWASP is a great source to practically implement validations.
- Form Validation/Check for Business rules: Ensure that data is not only validated, but also conforms with all business rules. This is essential to ensure that any possible malicious input is not allowed. For example, a pin-code is either valid or not, or the state exists or not.
- HTML Escape data: Strip all HTML, XML and PHP tags from a string using strip_tags() function in PHP.

















[…] $3.34 billion! With the buying going online, there has been an increase in hacks also. Hackers target your website or app with the sole motive of compromising your customers for financial […]
[…] Encryption Standard (DES) keys or other encrypted information. This method is widely used to crack passwords to admin accounts, which in turn can be used to steal information and documents of paramount […]