Over the last few years, applications have become complex and evolved into many forms. We have microservices, APIs, Web Sockets, data streaming, web components, PWA, etc., that constantly push the boundaries of what we know. And, amid these innovations, we need to ensure that the user data is safe and secure. One of the best ways to secure organization before hackers knock on the door is by performing software security testing.
In this blog post, we will discuss how software security testing is performed, different types of software security testing and everything else you need to know.
Understanding Software Security Testing
Software Security Testing is a process of identifying and eliminating the weaknesses in the software that can lead to the attack on the infrastructure system of a company. Software security testing is a process that is done as part of software testing, and it has as its main objective to check the security of the product. This type of testing helps to identify the potential weaknesses in the software and allows to patch them before a malicious user can exploit them and compromise the entire IT system.
The main goal of software security testing is to make sure that the data and resources of the system are protected from possible intruders. The objective of security testing is to make sure that the system works properly and that it can defend itself against potential attacks. Thus, security testing is always combined with the testing of other parts of the system.
Software security testing is a special type of software testing in which an application is tested for security vulnerabilities. Software security testing is a critical component of software testing and should be an integral part of the SDLC and other testing processes.
Why is Software Security Testing important?
Software security testing – is a special type of software testing aimed at testing the security of software. Such testing is required for several reasons. First of all, it is necessary to ensure compliance with laws and requirements concerning the level of security of software and protect the interests of the customer of the software from the side of the supplier.
In addition, it is necessary to ensure that the security of the software is maintained throughout its entire lifecycle, from development to operation. In addition, the security of software is often taken into account as a criterion for assessing the quality of software, as it has a great influence on the security of the system as a whole.
Software Security Testing in SDLC
Security testing is a must in the software development life cycle (SDLC), and it is not a new concept. Testing has always been needed and is still required, and we will continue to need it for software development. But we must also understand that security testing is necessary to develop better and design software and protect the data processed and modified by the software.
Security testing is needed because as software becomes more complex and as software is developed as a service (SaaS), as we create more microservices, as we use more dynamic data rendering, we must create a secure foundation for making sure that the data and the software and the services and the functions and the microservices and everything we do will be secure to protect it.
Types of Software Security Testing
1. Penetration Testing
Penetration testing is one of the most important testing techniques to be performed by any company. It involves the execution of various attack vectors with the help of professional hackers. Penetration testing is also known as security testing. It is used to check the security of the system by simulating the real-time scenario.
2. Vulnerability Scanning
Vulnerability scanning involves testing for vulnerabilities or weaknesses that may exist in an information system. Vulnerability scanning is typically performed by an automated tool that analyzes the system against known vulnerability signatures. The results of the scan are usually reported in a file known as a vulnerability scanning report.
3. Risk Assessment
Security risk assessment is a process that helps in identifying and mitigating potential threats and vulnerabilities in the information system and data. It helps in assessing the status of information security in an organization and identifies areas of risk. It is a systematic and objective method of evaluating the safety of an information system and identifying the security risks that can be exploited to cause harm or damage to an organization.
4. Security Auditing
Security auditing is a part of the activity of security assessment. It involves the examination of computer-based systems, networks or software to validate the effectiveness of security measures. A third-party service provider usually performs it called a security audit service provider. The security audit report should helps assess organization’s security preparedness and discover areas that are vulnerable to any security threats.
5. Source Code Review
Source code review is reviewing the complete source code of the application for potential security risks. A third-party security vendor can review the source code of an application to identify security risks that the developer might have missed. The idea of source code review is to review applications with a fresh set of eyes to look for potential security issues.
3 Approaches of Software Security Testing
Software Security Testing is a software testing task in which software is analyzed for vulnerabilities and weaknesses. Software Security Testing is performed using three different approaches. Let’s understand all three of them in detail.
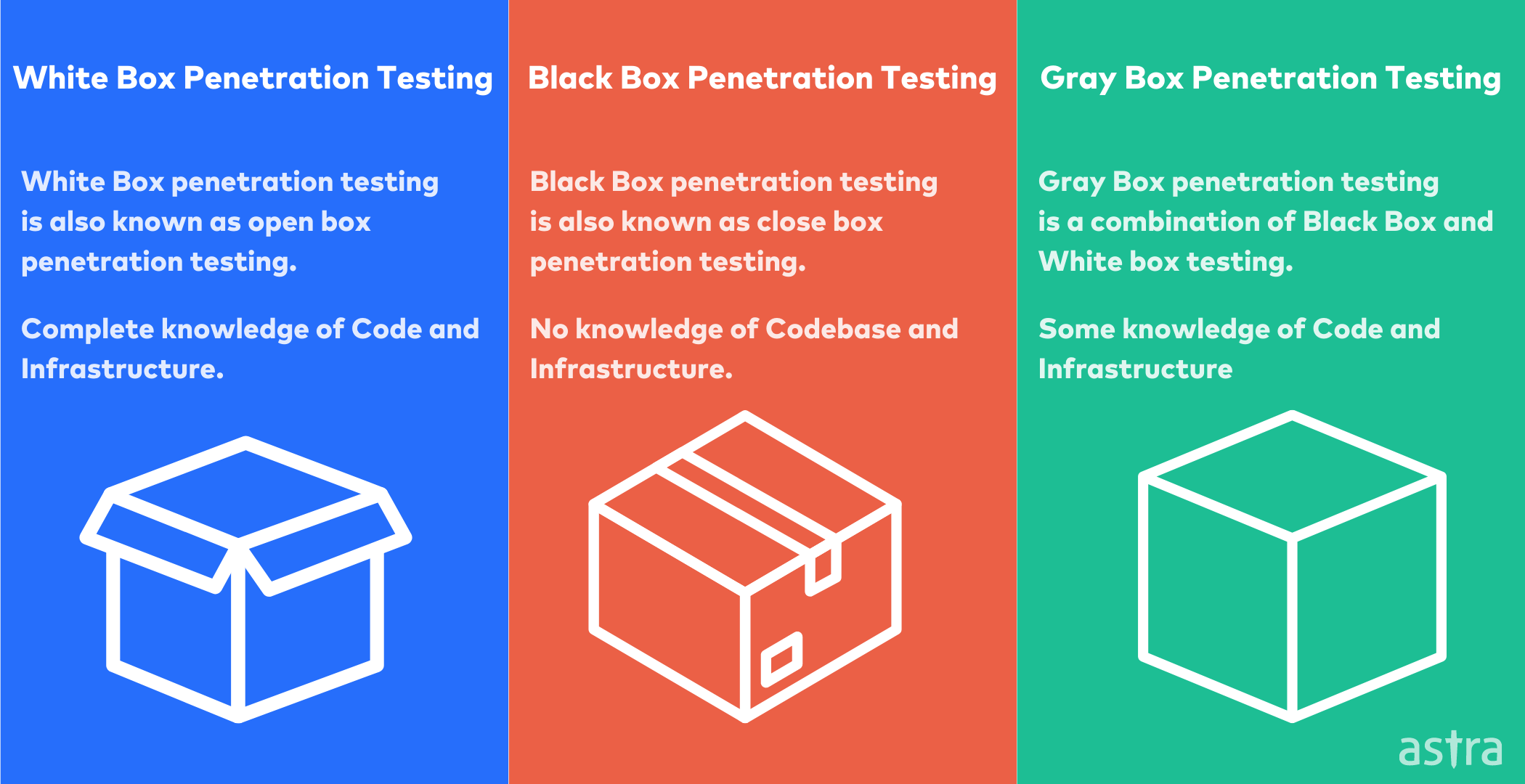
1. Black Box Testing
Black box security testing (also known as opaque testing) is a black box methodology for testing. In black-box security testing, the test engineer is unaware of the internal workings of the application or system under test.
The test engineer must rely on existing documentation, expertise, and input from the programmers and users to design tests. The test engineer has no knowledge of the internals of the system or application under test.
Black box testing is the most common approach to security testing. The tester does not know the system and designs the test as an uninformed attacker. The tester should determine the potential risk factors the client’s faces and design tests to attack these factors.
2. White Box Testing
White box testing is the opposite of black-box testing. A Black box test, or closed box test, is where you don’t know anything about the system you are testing.
White box testing or glass box testing is a software testing method in which the internal state of the system and the code structure are known to the tester. In white-box testing, an internal perspective is taken instead of black-box testing, where the software is treated as a “black box”. White box testing is also called glass box testing because the tester sees through the “walls” of the code.
3. Gray Box Testing
Gray box security testing is a form of security testing that requires a mix of knowledge and skills. This is a hybrid form of white box testing and black-box testing. In a white box test, an individual has access to the code, and a black box test is when an individual does not know the code or the source code. The gray box test is a mix of the two, with the tester having some knowledge but not all of the knowledge. The tester knows the code but not the source code.
Are you unable to access your website? Is your website experiencing hacking issues? Find out in 15 seconds.
Understanding SAST, DAST and IAST
What is Dynamic Application Security Testing (DAST)?
DAST is a method of finding security vulnerabilities while the application is in the production phase, which includes both manual and automation testing using various kinds of testing tools. This is considered to be a part of the Software Security Testing Method.
The term “dynamic” is used because it is a process of testing that occurs at runtime rather than at compile time. DAST is a security testing technique that is used to detect security vulnerabilities during the development process. It allows a developer or a penetration tester to scan the software application for possible vulnerabilities before deploying it in the production environment.
What is Static Application Security Testing (SAST)?
Static application security testing (SAST), or static analysis, is a testing methodology that analyzes source code to find security vulnerabilities that make your organization’s applications susceptible to attack. It is used in software development to identify potential security problems in software in the early stages of development.
Static application security testing (SAST) is the practice of finding vulnerabilities in software without executing the program. It’s all about finding bugs before the software is built. The term static refers to the fact that the code is not executing when it is examined. Static analysis isn’t the same as dynamic analysis. Dynamic analysis is when the software is run. Static analysis is the analysis of software without execution.
What is Integration Application Security Testing (IAST)?
IAST is a testing technique used to check for security vulnerabilities in an application under development. With IAST, an automated system exposes an application’s functionality and observes the user’s actions and responses. Any deviation from expected behavior is flagged as a potential risk and can be investigated further.
3 Common Vulnerabilities found in Software
Vulnerabilities have been a problem for a long time. It’s been a problem for as long as there have been software products. Let us understand some common vulnerabilities found in applications.
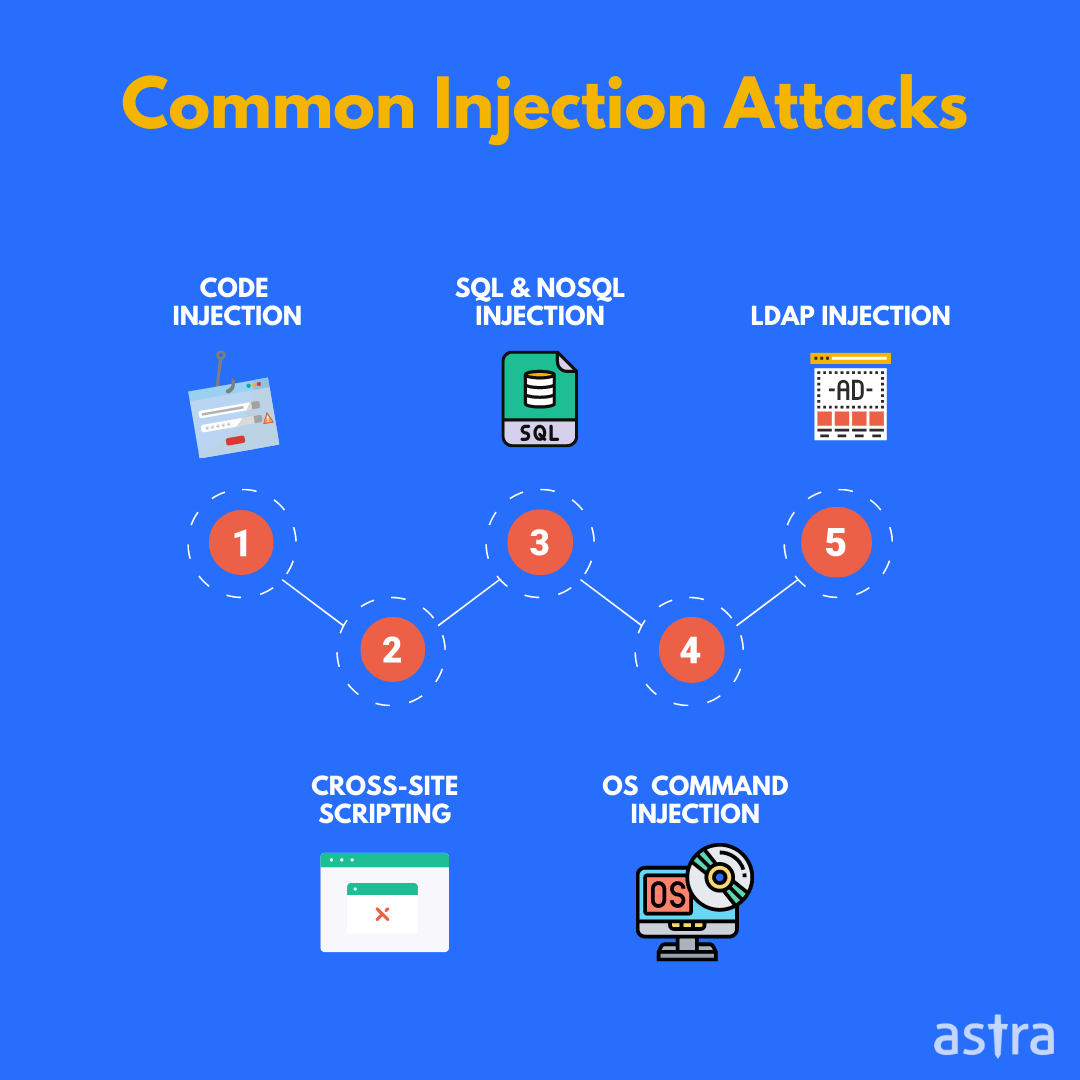
Injection Attacks
Injection attacks are one of the most dangerous threats for websites and the most common attack in the cybercriminal world. This attack is considered one of the most hazardous because it can be used to exploit almost every vulnerability in the system. The most popular injection attacks are SQL injection, LDAP injection, XPath injection, Code injection, OS command injection and XML injection.
Improper Access Control
An improper access control vulnerability is a specific form of confidentiality weakness. When access to an information system or application is not properly restricted, an intruder can access unauthorized data. Improper access control is often related to inadequate authentication schemes, inadequate auditing procedures, or inadequate segregation of duties by authorized personnel.
Server-Side Request Forgery
A server-side request forgery (SSRF) vulnerability is a flaw in a server-side program that allows an attacker to send a forged HTTP/HTTPS request from a vulnerable server to a third-party device or system. In the case of an HTTP server, the server sends a response to an IP address that is not the originating IP address. The implication is that the attacker can force a specific server to send a forged HTTP request, which may cause a denial of service or a resource to be used in a way that the server’s owner did not intend.
How does Secure Coding help in Software Security Testing?
For software to be secure, it must be tested for security vulnerabilities. Testing for security vulnerabilities is not an easy task. Due to a lack of software security testing, software systems are vulnerable to security breaches, privacy violations and software failures. This is where secure coding comes into the picture.
Secure coding includes the best practices for programmers to follow to make the software more secure. To make the software more secure, programmers need to follow secure coding best practices. These best practices help programmers make the software more secure by ensuring no vulnerabilities or cyber-attacks.
The application layer is where most cyberattacks happen, which is why secure Coding is essential to protecting the data of your customers. The application layer is also where the most secure Coding developers can apply best practices.

Open Source Software Security Testing Tools
Here’s a list of some of the best-known software security testing tools that are freely available.
1. OWASP ZAP
OWASP ZAP is a black box, free and open-source web application security scanner. ZAP gives an in-depth view of the tested application’s attack surface. ZAP can be used during all phases of an application security testing cycle, from the initial mapping of the application’s attack surface to penetration testing and vulnerability verification.
ZAP is designed to be used by people with a wide range of security experiences. As such, it is ideal for developers and functional testers who are new to penetration testing. ZAP is a tool for testing web applications. It is not a tool for testing the security of a particular implementation of a specific protocol. ZAP will only find the issues that arise from using a protocol, not the protocol itself.
2. Vega
Vega Vulnerability Scanner is a free and open-source web security scanner and web security testing platform to test the security of web applications. It is also available as a commercial product. Vega was developed by the team behind the popular open-source penetration testing framework, OpenVAS.
3. Wapiti
Wapiti is a web application security scanner that is used to scan a website and find vulnerabilities. It is one of the easiest tools to operate on for newcomers. Wapiti offers several inbuilt features that help with performing a penetration test on a website. The tool is written in Java and hence is cross-platform. It uses a vulnerability database that is updated daily to ensure that it provides accurate reports.
How can Astra help in Software Security Testing?
Astra Security is one of the leading software security testing provider companies. We offer various cyber-security services including software security testing, API testing, web security testing, network security testing, etc.
At Astra, we strive to deliver the highest level of security to our clients and their customers. Our suite of security testing services helps clients to ensure the safety of their systems and applications. We have a team of highly skilled and experienced security experts that you can trust to deliver the results you need.

Conclusion
Many things go into making sure that you can get the most out of your software. From making sure that you can develop properly to ensure that you can get the most out of it once you have it up and running. One of the most important parts of this process is software security testing. There are many different types of software security testing, but the more you learn about software security testing, the more you will get out of your software. We would be more than happy to answer any questions that you may have or get you started with software security testing. Please shoot us an email now, and let us take care of your application’s security.
FAQs
1. What is Software Security testing?
Software security testing refers to the type of testing that looks for design inconsistencies and misconfigurations that might make it vulnerable to cyberattacks.
2. How are software security tests performed?
Software security testing is performed through various methodologies like penetration testing, vulnerability scanning, risk analysis, code review, etc.
















