Networks are a crucial part of any organization ranging from SMEs to the large enterprises. Without an IT network, an online company would not be able to run. But to run smoothly and uninterrupted, the company’s network must be protected from cyberattacks and security loophole exploits.
In today’s world, no system is immune to cyberattacks. To safeguard these systems a comprehensive network security audit is necessary. And to be effective, a thorough and complex set of network security checks must be done to discover potential security weaknesses, vulnerabilities, and misconfiguration errors within a network.
What is a Security Audit?
Security audits are also known as internal audits or compliance audits. These audits are performed to assess the security of your company’s information system, but they are also performed to assess compliance with security legislation. The frequency of security audits can vary depending on the company, but most organizations do them on a yearly basis.
Security audits can be categorized into various types such as network security audits, web app security audits, blockchain security audits, and so on. In this article, we’ll be discussing how network security audits help you stay secure from today’s cyberattacks and how they are important to achieve regulatory compliance.
Related Read: Cloud Security Audit: Everything You Need to Know | Why Firewall Penetration Testing is Essential to Your Security Strategy
What is a Network Security Audit?
Network security audit is a crucial part of the IT Operations of any organization as they are the first step to identifying potential threats and vulnerabilities. In a typical network security audit, you will analyze all network devices and infrastructure and the management of the network.
A network security audit usually consists of a review of all network infrastructure and systems accessible from the internet. It also involves a review of the security mechanisms used to protect the network infrastructure, including the network devices. A network security audit can be a part of a system, or a network compliance auditor can be a stand-alone if security is a large concern.
The goal of a network security audit is to identify and correct any vulnerabilities in the network and ensure that your systems are secure and will not be compromised.
Why are Network Security Audits important?
Security audits are an essential element of network security. Network security audits regularly enable organizations to keep abreast of the latest security threats and vulnerabilities.
Network security audits can be conducted manually by security experts or automated using various network testing tools. Network security audits are conducted to ensure that the networks are secure and free from vulnerabilities, security loopholes, or software bugs that hackers can exploit.
The best way to conduct a network security audit is to have a professional penetration testing team so that the network can be scanned and tested thoroughly. A penetration testing team can perform advanced network security audits, vulnerability tests, and penetration tests on a network. Network penetration testing tools are also called network vulnerability scanners or network security scanners.
Also Read: Security Audit Services: Importance, Types, Top 3 Companies
4 things to check while performing Network Security Audit
Although a network security audit is not a small task, still here are a few pointers that one should check while performing a network security audit.
- Password Security
- Proper password policy
- Use of password manager
- Insecure storage of passwords
- Common passwords usage
- Internal Network Security
- Proper access permissions
- Disable guest accounts
- Logs for unauthorized login attempts
- Firewall Security
- NAT implementation
- Inbound network rules
- Firewall policies for security risks.
- Mobile Devices Security
- Connected devices should be encrypted
- List of applications installed for verification of insecure apps.
Also Read: 10 Best Cyber Security Audit Companies: Features and Services Explained
How is Network Security Audit performed?
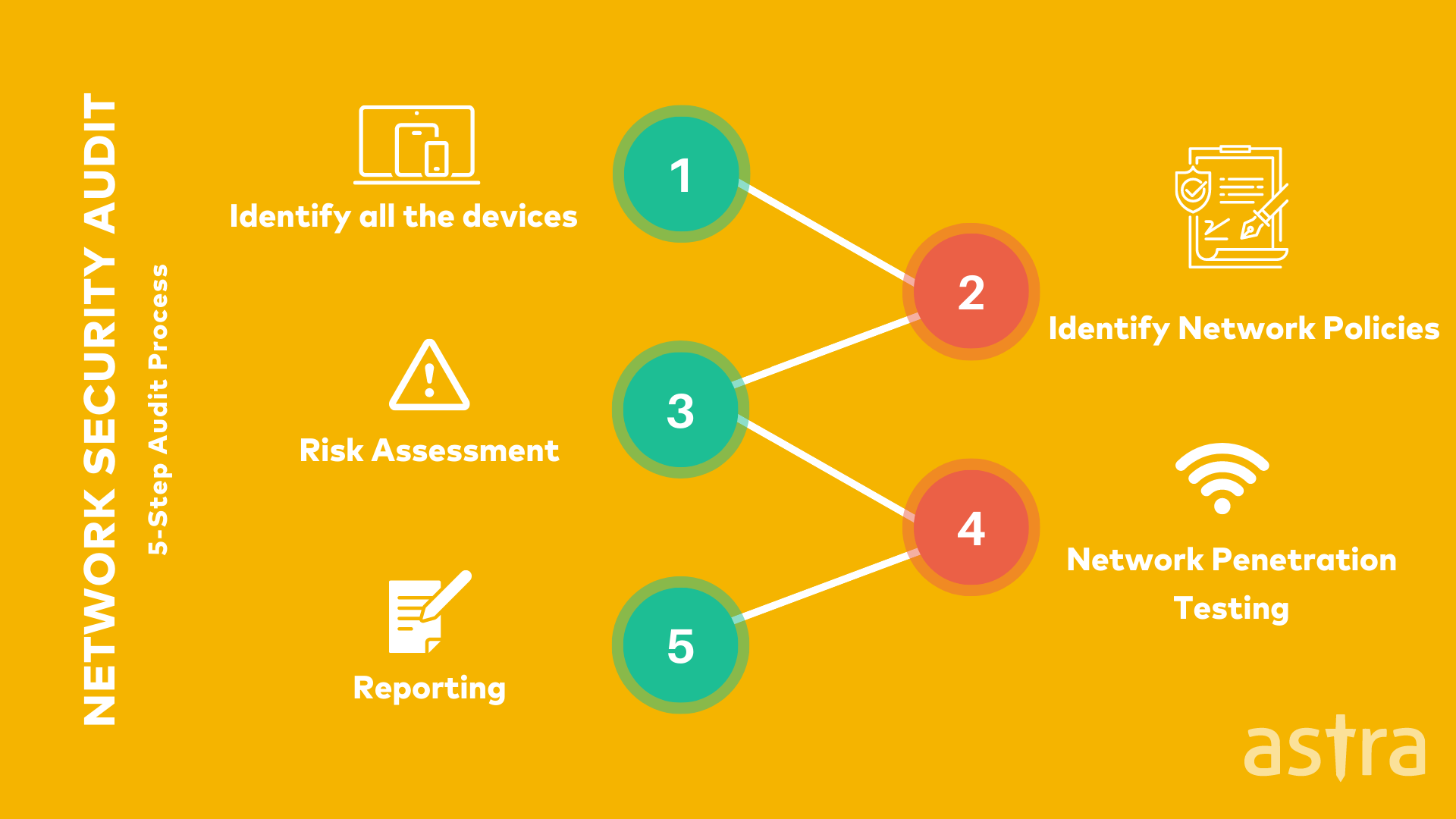
Network security audits are done in 5 simple steps. Let’s understand all of them in detail:
Step 1: Identify all the devices
Endpoint security is a major concern for most organizations as it is difficult to identify and track all the devices on the network. With an effective network security audit, you can identify the endpoint devices and their vulnerabilities.
The audit should provide a network diagram that identifies the devices and operating systems. This information can help an auditor locate endpoints and their vulnerabilities.
Step 2: Identify Network Policies
When a network audit is being planned, a company needs to make sure that they clearly understand all the security policies and procedures in place. Security policies and procedures are a significant part of a network audit.
These policies and procedures are what an auditor will use to determine if a company complies with the guidelines set forth by the organization that is being audited. In addition, security policies and procedures can also be used to identify if any areas need to be updated.
Step 3: Risk Assessment
A risk assessment is a process that identifies the risks that an entity faces in its operations and the potential effects of the risks on the entity, its management, and its stakeholders.
Risk assessments can be conducted on an ongoing basis to identify new risks, monitor changes in risks, and help to determine the appropriate control environment. Risk assessment is one of the core elements of an integrated control program.
Step 4: Network Penetration Testing
Network penetration testing is the practice of testing a network to find vulnerabilities that an outside intruder might exploit.
When you conduct a network penetration test, you typically have more time and resources at your disposal to test all aspects and facets of the network. Network penetration testing is a common method for ensuring that a network is secure. All companies and government agencies require network penetration testing before they will approve a system’s security.
Also Read: Network Security Testing and 5 Best Network Security Tools in 2022
Step 5: Reporting
Reporting is the final phase in the network security audit. It helps management to evaluate the risks of the internal and external security threats to their businesses. Generally, the auditing team prepares a report of their findings. The report includes a detailed summary of the findings and a full list of the risks of the internal and external security threats.
Who performs a Network Security Audit?
Network security audits can be performed by internal or external auditors, depending on the company’s size and whether a company has IT Staff or not.
Most small to medium-sized businesses will not have an internal IT Staff. Therefore they will need to hire an external network security auditor to conduct the audit. However, large corporations can have an internal IT staff and hire an external network security auditor or perform the audit internally.
Read Also: Choosing The Right Security Audit Company Made Easy
How much does a Network Security Audit Cost?
Like many other business owners, you may be wondering: “How much does a network security audit cost?” After all, it’s not cheap. But what you get in return is worth it. Network security audits are essential for any company that has a network with access to the internet.
It’s the only way to identify vulnerabilities in your system and fix them before hackers exploit them. But how much do they cost? Unfortunately, there is no one price. The costs vary depending on the size of your business, the number of cyber threats you are facing, and even the type of audit.
Generally, the cost of a network security audit usually ranges from $700 to $25000. This might seem like a lot – but when you look at the bigger picture, these audits can save your organization from cyber attacks – dealing with which can prove to be far more expensive.
Learn more about IT Security Audit Cost
Tools used to perform Network Security Audit
Some of the most popular tools used to perform network security audit are:
These are some of the most used tools that are used to perform network security audits.
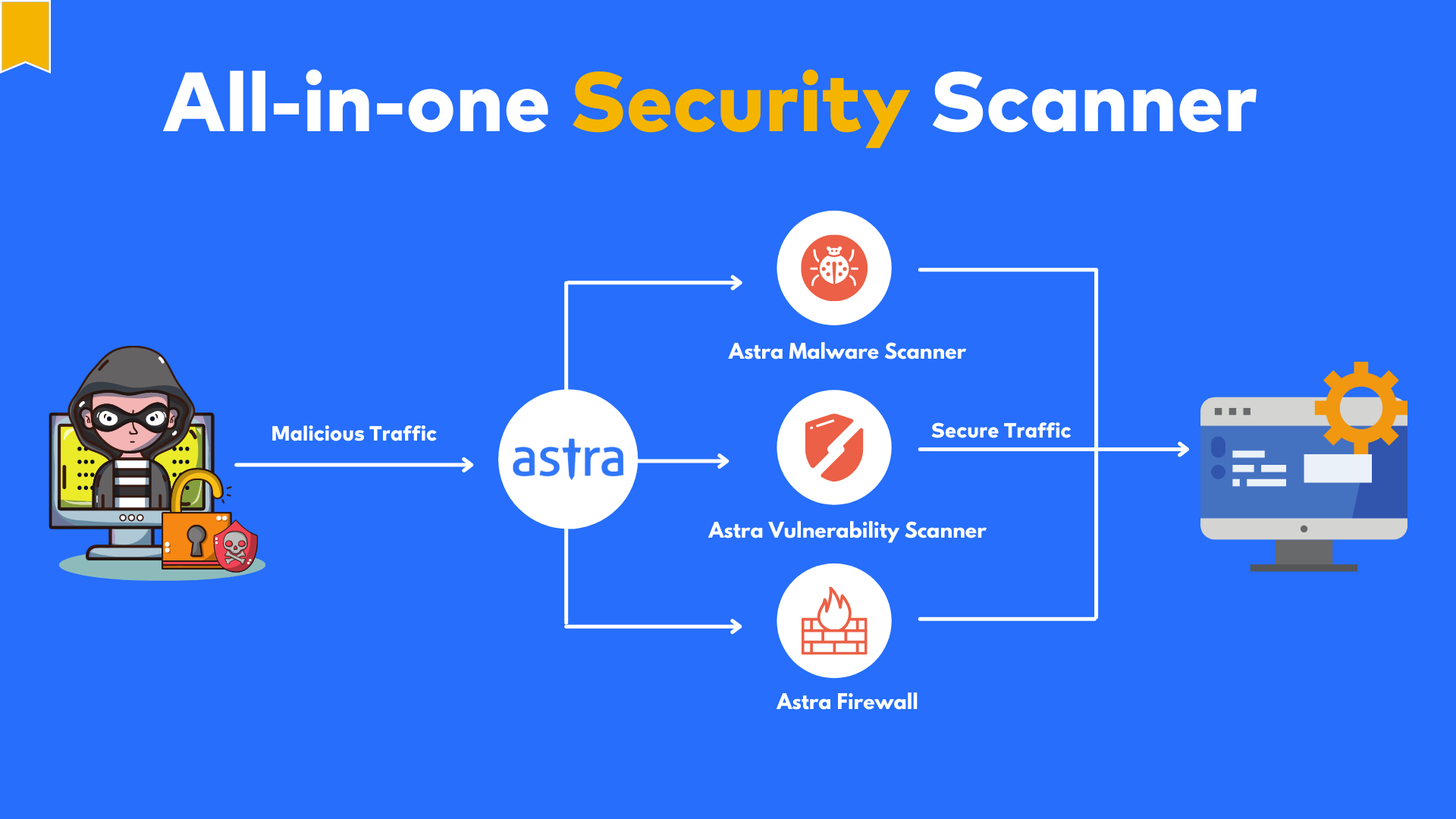
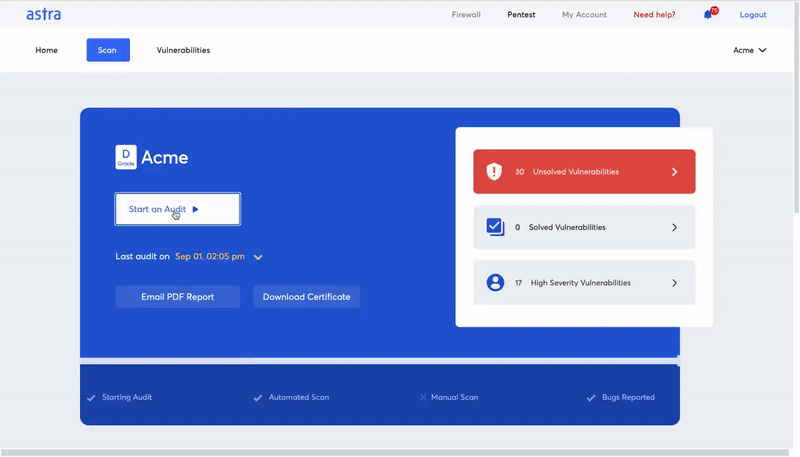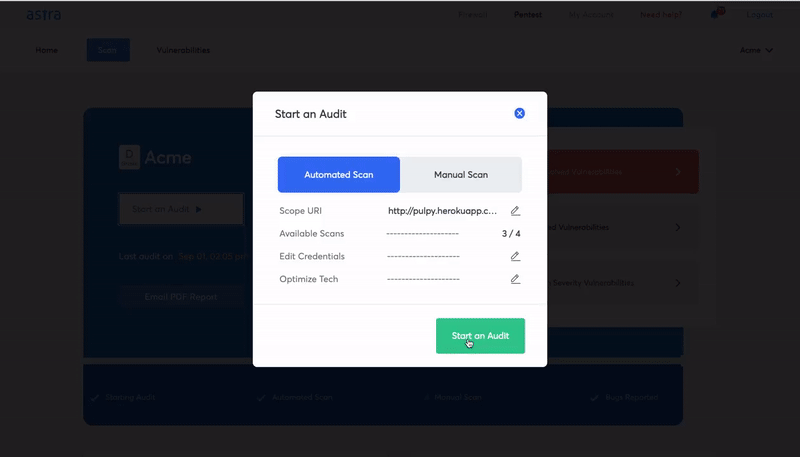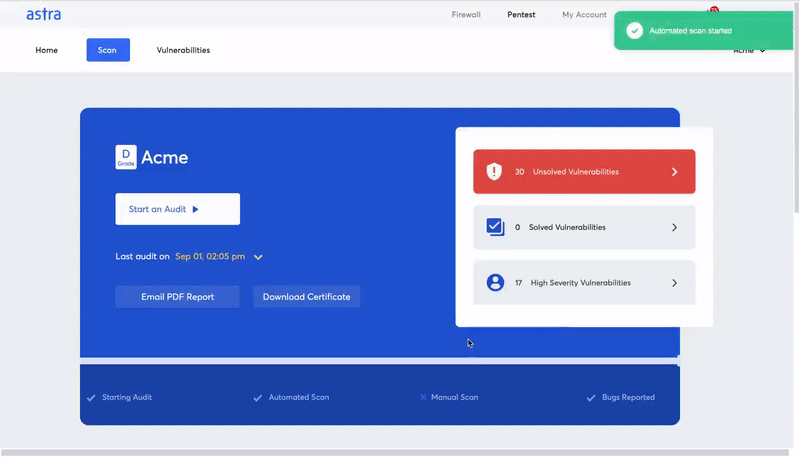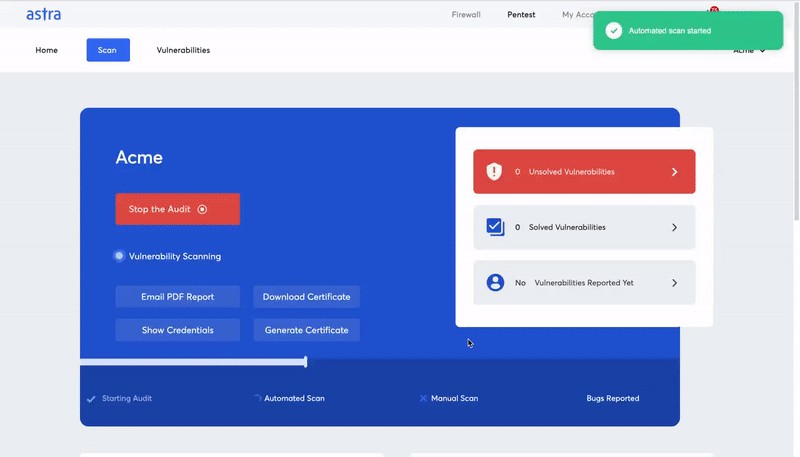
What is Astra’s Pentest solution?
Penetration testing is the most well-known service that Astra provides. It’s the most common way to dig into the areas of your business that might be vulnerable to outside attack.
The result of a penetration test is a report that provides you with detailed information about improving your security. The type of vulnerability typically breaks down the report, so you can easily see where the biggest holes are.
Think Astra as an army of “hackers” to your site trying to get in through any possible entry point. The goal of this attack is to show you the weaknesses in your site so you can stop hackers from getting in.
Checkout Astra’s Network Security Audit and Penetration Testing Checklist
Key Features of Astra’s Pentest Solution:
- Hacker style penetration testing methodology
- User-Friendly Dashboard
- Pentest Certificate to showcase security status
- More than 3000 tests to keep your assets secure
- Monetary loss value associated with a vulnerability
- Detailed steps-to-fix and fixing advice from security engineers
- Consultation call post penetration test
Get in touch with an Astra-naut and keep your data and assets secure from hackers.
Conclusion
Network security audits are a must to protect your company from potential data breaches and cyber-attacks. A network security audit or network security assessment is a formal security control analysis or a system used to protect your and your customers’ data and sensitive information.
















