Cloud security scanners are tools that help companies discover any flaws and loopholes within the cloud platform they make use of for data storage and transmission. However, it not only scans for these weak points but rather also points out remediation measures to strengthen the security system too.
An ideal cloud security scanner should have the following features:
- Continuous Automated Vulnerability Scanning
- Regular Penetration Testing
- Compliance-specific scans
Why Cloud Security Scanners Are Needed?
The above-mentioned features together ensure that your company’s services remain the best in terms of protection and compliance.
- Cloud security forms a vital part of cloud computing, as such, due importance is to be given to its security since it too is susceptible to malicious attacks and data breaches. Not doing so can lead to the tarnishing of your company’s reputation.
- Compliance with sector-specific security standards like HIPAA, ISO 27001, PCI-DSS, and more are crucial since it determines and showcases the quality of your company. Additionally, not meeting compliance requirements can lead up to hefty punishments and fines.
- Cloud security scanners can be integrated into the CI/CD pipeline. This means that any possible flaws can be diagnosed and remedied at the development stage of projects.
- Cloud security scanners can help customer organizations keep up with the shared responsibility model of security opted by cloud platforms like AWS. With this model, the maintenance of security is the shared responsibility of the customer and the cloud service provider.
How Do the Scanners Help With Cloud Security?
- Cloud security scanners provide cloud security assessment and protection at every stage of the cloud application development process. This allows the shift from DevOps to DevSecOps thus enabling the integration of vulnerability scanning into every step throughout. This allows the early detection of flaws which can then quickly be fixed to move further in development.
- Continuous automated vulnerability scanning helps ensure that there is a periodic check of the cloud platform for weaknesses in security. These automated scans check for known vulnerabilities and other CVEs based on intel or well-established frameworks like NIST, OWASP Top 10 Risks, and SANS 25.
- Regular Penetration Testing refers to hacker-style testing of the defenses put up by one’s cloud security. Vulnerable areas are penetrated to see the extent of possible damage and assess the amount of data that would be compromised from such an attack.
- Compliance-Specific Scan scans for certifications like PCI-DSS, HIPAA, ISO 27001, and SOC2 help maintain some internationally accepted standards that make your organization stand out among others in terms of service. It also plays a vital role in ensuring the smooth functioning of your company in terms of cloud security.
Also Read: 5 Best Cloud Security Companies: Features Offered And Factors To Consider
Top 3 Cloud Platforms That Utilize Cloud Security
This section will detail the top 3 cloud service providers which are Google Cloud Platform, Azure, and Amazon Web Services. These three major cloud providers provide a variety of data storage, transmission, and networking options.
Google Cloud Platform Security Scanner
This range of cloud computing services is provided by Google, and it includes data analytics, storage, transmissions, and management services. Google Cloud Platform Security Scanner provides a venue not only for Software-as-a-Service applications but also for Infrastructure-as-a-Service (IaaS) models too.
As a part of security for its customers it also has a security command center with the following features:
- Threat Detection
This refers to the detection of risks and associated threats through constant and continuous monitoring. There are two types of threat detection, container, and event-based detection.
Container threat detection refers to finding threats by monitoring large suspicious files, images, and attempts to gain access remotely. Secondly, event threat detection refers to the immediate detection of threats through monitoring the cloud using detection logic. Both types provide alerts for the detection of threats.
- Security Scanner
This application scans web applications and other services running on Google engines. It crawls through applications and carries out security tests for vulnerabilities like cross-site scripting and more. This scanner helps identify flaws in the data and services on the Google cloud before they can be exploited by hackers with malicious intent.
Microsoft Azure Cloud Security Scanner
Microsoft Azure was specifically made for designing, building, releasing, and managing a variety of applications. Its services include computation, networking, and data management that offers storage redundancy across multiple data centers thus ensuring the safety of information.
Azure is known for its extensive networking capacities. This is because it can support site-to-site virtual network connections from different regions. It also has a Security center that manages all Azure security concerns. Its features include:
- Vulnerability Management
Azure penetration testing services for virtual machines, database servers, networks, and web applications as well. If virtual machines do not have their own security management system Microsoft Azure deploys Qualys vulnerability scanner for security management.
- Vulnerability Assessment
Microsoft Azure’s security center does not directly conduct vulnerability assessments but instead checks whether the machines and VMs have deployed vulnerability assessment tools.
- Defenders for Container Registries
This tool scans container images added to the Azure container registry that were either added recently or pulled in the previous month. The scans are automatic and they find known vulnerabilities and CVEs. The report provided gives extensive details on the vulnerabilities, their risk severity scores, and remediation measures.
Read also: Azure Penetration Testing Guide – Policies, Tools & Tips | 10 Best Cyber Security Audit Companies [Features and Services Explained]
AWS Cloud Security Scanner
AWS was by Amazon is considered one of the best pioneering cloud computing services that set the gold standard for all other cloud services. It offers a wide range of IaaS services that includes storage, networking, computing, and content delivery.
It also provides tools for service management and resource monitoring and smooth data collection among others. It is one of the largest providers of cloud services that significantly contributes to company enhancement and growth.
For security purposes, AWS provides customers with AWS Security Hub. This is a central console for managing all things security-related. It identifies security issues according to two main categories. Here are its features:
- The first category of security issues compiled are called Findings, this includes security issues from various regions like third-party services and certain customizations. These findings are then crossed checked against all AWS services to find their severity.
- The second is a collection of specific findings which are termed Insights. These are security issues found that have a high-risk probability and need to fix as soon as possible. The AWS security hub provides an in-built library of such findings and insights or they can also be customized.
You may like to Read: Complete Guide on AWS Security Audit | Astra Security
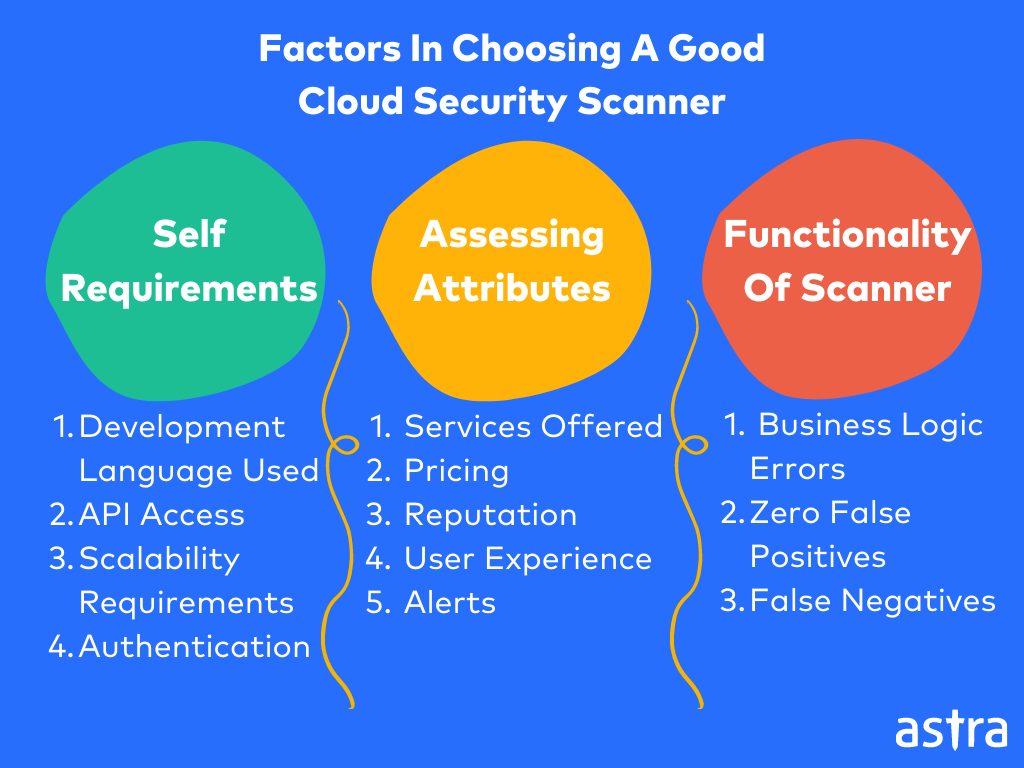
Factors In Choosing A Good Cloud Security Scanner
Here’s a list of factors that aid in picking a good vulnerability scanner from different cloud security companies.
1. Understand Self Requirements
Before starting the hunt for a good cloud security scanner, it is vital to analyze the needs and requirements of your organization and its services. Since there is no one fixed solution to anything in the cyber world, it goes without saying that having a clear resolution to your requirements can greatly help you narrow down your choices.
Some of the things to keep in mind include:
- The web application development language in use.
- Whether access to APIs is required?
- Your company’s scalability requirements.
- Do you need an extensive scanning report?
- Does your application require authentication or use anti-forgery tokens?
These are just a few of the questions that need to be answered to better understand your own requirements when looking for a cloud security scanner.
2. Assess Attributes
When choosing a quality cloud security scanner it is important to compare tools and also to assess the features of each tool. This involves assessing aspects such as:
- Services offered: Do they just offer vulnerability scanning services or do they have more extensive options like penetration testing or security audits?
- Pricing: Are the tool and the package of services it includes affordable and fair?
- Support: How good is their customer support? Is it reliable and quick?
- Reputation and Experience: These two factors are extremely important as they tell you the social standing of the tools on your list. Longer experience generally leads to a better reputation but this need not always be the case.
- Scalability: Can the tool used be scaled up if you decide to add or scan more applications?
- Scanner: Is the scanner comprehensive and does it scan for all the components required by your company? Is it capable of identifying OWASP Top 10, SANS 25, and other known vulnerabilities?
- User Experience: Does it have a demo and is it easy to navigate by oneself?
- Alerts: Does it provide real-time alerts based on the threat discovered during the scans?
- Updates: Is the scanner currently up to date with all the latest vulnerabilities?
3. Functionality of Scanners
Lastly, before choosing a scanner it is important to assess its functionality. This refers to gaining a deep insight into how well the scanners work.
Is it capable of detecting:
- business logic errors
- ensure zero false positives
- false negatives
It is also crucial to check the comprehensiveness of the solutions suggested to fix the vulnerabilities found.
Also Read: 11 Top Penetration Testing Tools/Software of 2022 [Reviewed]
Astra Security- The Best Cloud Security Scanner
Astra Security provides cloud security scanning services that are comprehensive which in turn ensures safety. With the cloud platform undergoing constant changes and development it comes as no surprise that the security for these systems would also need to evolve and become more efficient.
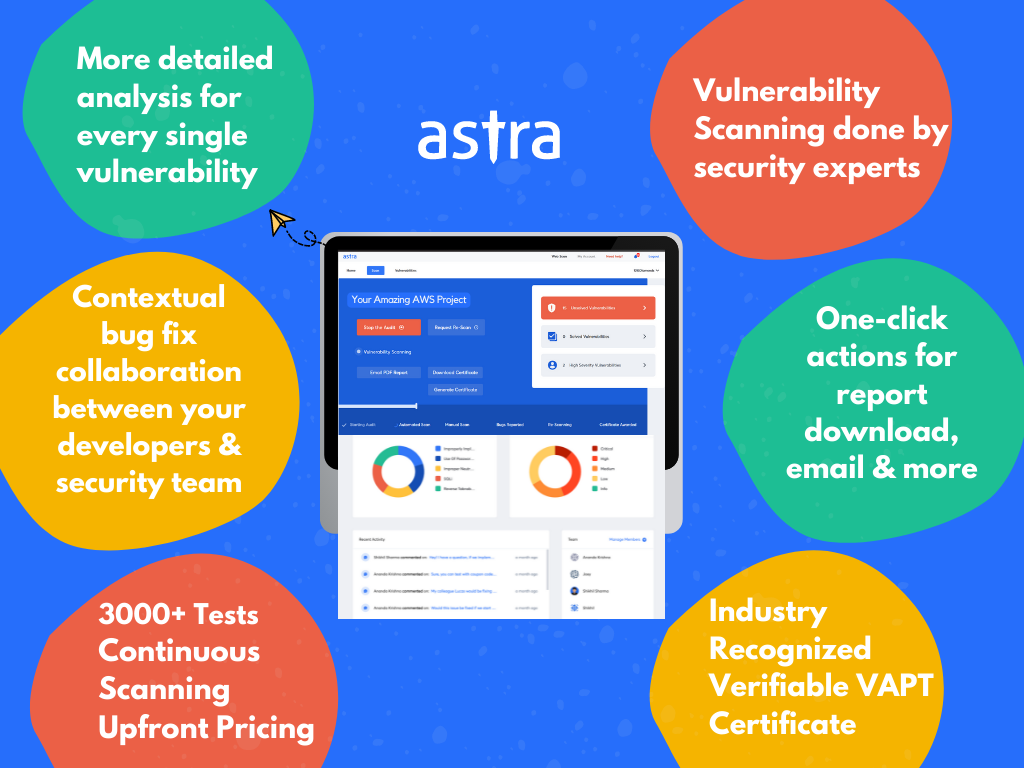
Here are some of the features that make Astra Security’s Cloud Security Scanner the prime option for your organization:
1. Continuous Vulnerability Scanning
Astra’s comprehensive scanner is just right for your needs as it scans for all known vulnerabilities ranging from the OWASP Top 10 to SANS 25. It also follows the NIST, OWASP, and CIS benchmarks for security standards.
Astra’s vulnerability scanner can also scan and find business logic errors. It also guarantees zero false positives and this is made sure through thorough vetting by the in-house pentesters. They also provide gap analysis, meaning your current cloud system is scanned for gaps in security or performance.
2. Regular Penetration Tests
Astra Pentest is a holistic pentesting service that conducts hacker-style examinations of your security systems. After scanning for vulnerabilities, the found vulnerabilities are then exploited through suitable methods.
Once the exploitative penetration testing is over the damage to the system is assessed as well as the severity of the found vulnerabilities. A report is then generated to be given to the organization which will detail vulnerabilities, their CVSS scores, and the measures to remediate them will be mentioned.
3. 24*7 Customer Support
Astra’s provides an expert customer care experience that is available for you 24*7. Doubts can be clarified via mail or through calls if deemed necessary. One can also contact the support team directly through the “Help” option on the dashboard.
4. Maintain Compliance
Astra Security can help you maintain compliance with regulatory standards like HIPAA, PCI-DSS, SOC2, ISO 27001, and GDPR. Based on the sector your company belongs to, maintaining compliance with these is important, or else it could lead to non-compliance. Non-compliance can result in your organization receiving hefty penalties or even criminal charges.
5. Collaborative Dashboard
Astra boasts a highly intuitive CXO-friendly dashboard that is extremely user-friendly with ease of navigation and understanding. The dashboard also shows the current status of the scans, the vulnerabilities found, their CVSS score, and other details. These features allow streamlining the pentest and prioritization of vulnerability fixes based on ROI.
6. Publicly Verifiable Certificate
Once scanning and remediation of the found vulnerabilities are done, another re-scan is carried out to ensure that the patched fixes are good and that there are no further vulnerabilities.
Once this is confirmed, the organization is then eligible for a publicly verifiably certificate from Astra stating that security is top-notch. This can boost the company’s sales and reliability.
7. Experienced Team
Astra Security has a team of highly experienced pentesters with years of knowledge, education, and experience with pentesting. They also vet out the results of the scan to ensure that there are zero false positives in the report generated.
Also Read: Top 5 Software Security Testing Tools in 2022 [Reviewed]
Conclusion
This article has mentioned everything one needs to know about cloud security scanners. The need for it has and will continue to increase with time. Therefore it makes sense to invest in a good cloud security scanner to keep your applications, data, and ultimately your organization safe.
1. What are the best cloud security scanners?
The best cloud security scanners include Astra Pentest, Qualys Guard, Intruder, Aqua, and Orca Security.
2. What are the four pillars of comprehensive cloud security?
The four pillars for comprehensive cloud security are maintenance of compliance, proper implementation of access controls, continuous vulnerability scans, and immediate remediation of vulnerabilities.
3. How to secure data stored in the cloud?
The safety of data stored and transmitted within the cloud can be ensured by enabling data encryption and multi-factor authentication, installing good security software, carrying out regular vulnerability scans, and using strong passwords.
















