Securing digital assets is essential. You’ve probably heard that a lot. In truth, security is crucial, no matter your level of experience as a developer. This blog will discuss how you can protect your GCP account and the best practices to keep your GCP resources safe. GCP is an excellent service, but it isn’t a magic cure-all for security problems. It’s a platform that can make your life a lot easier, but it’s not a free pass to a secure environment.
What is GCP Security?
GCP security refers to measures taken by GCP customers to protect their assets and information stored in the cloud platform. It mainly includes access management, access control, and audits by cloud security service providers to ensure the confidentiality, integrity, and availability of data and resources hosted on the platform.
GCP security is crucial to the well-being of your business. GCP’s security is managed through the following services:
- Identity and Access Management (IAM) – Control user access to GCP resources, monitor usage, audit activity, and maintain compliance.
- Access Control Security Audit Logging – Control who uses GCP resources, monitor usage, audit activity, and maintain compliance.
- Cloud Audit Logging – Control who uses GCP resources, monitor usage, audit activity, and maintain compliance.
- Cloud Identity-Aware Proxy (Cloud IAP) – Control network traffic to GCP resources, monitor usage, audit activity, and maintain compliance.
Google Cloud Platform (GCP) security is a shared responsibility. Cloud providers like Google and customers like you share the responsibility to secure your data and applications in the cloud.
GCP security services offers a comprehensive set of security and compliance features and services to make it easier to protect your customers’ information.
What is GCP?
Google Cloud Platform, or GCP, is a public cloud vendor. With the GCP platform, customers can access computer resources housed in Google’s data centers worldwide for free or on a pay-per-use basis.
GCP is a Platform as a Service (PaaS) that includes three main categories:
- Compute
- Storage
- Networking
GCP platform offers services for App Engine, Compute Engine, Cloud Storage, BigQuery, Cloud SQL, Google Cloud DNS, Google Cloud Launcher, Google Cloud Endpoints, Google Container Engine, Kubernetes, AppScale, etc.
Why is Google Cloud Security important?
Cloud computing is a great way to save costs and increase the speed and efficiency of your business. If you use cloud computing options like Google Cloud Platform (GCP), you can develop and host your business applications on GCP.
The GCP penetration testing will identify the vulnerabilities and weaknesses in the GCP environment and help to fix those vulnerabilities helping you enhance GCP cloud security.
GCP penetration testing will help you identify and understand the security vulnerabilities of your GCP Cloud deployment which helps in GCP security. As a result of this test, you can get a comprehensive and thorough insight into the security of your Cloud deployment and take the necessary steps to fix the issues identified.
Challenges To GCP Security And Compliance
As the cloud revolution makes companies more agile, it is also upping the ante when it comes to security. The widespread availability of people, data, and infrastructure has created an interconnected world that is also incredibly vulnerable. The rise in cyber threats has forced companies to reevaluate their security measures and take action. While many still feel that the cloud is highly secure, the lack of security measures has recently come under scrutiny.
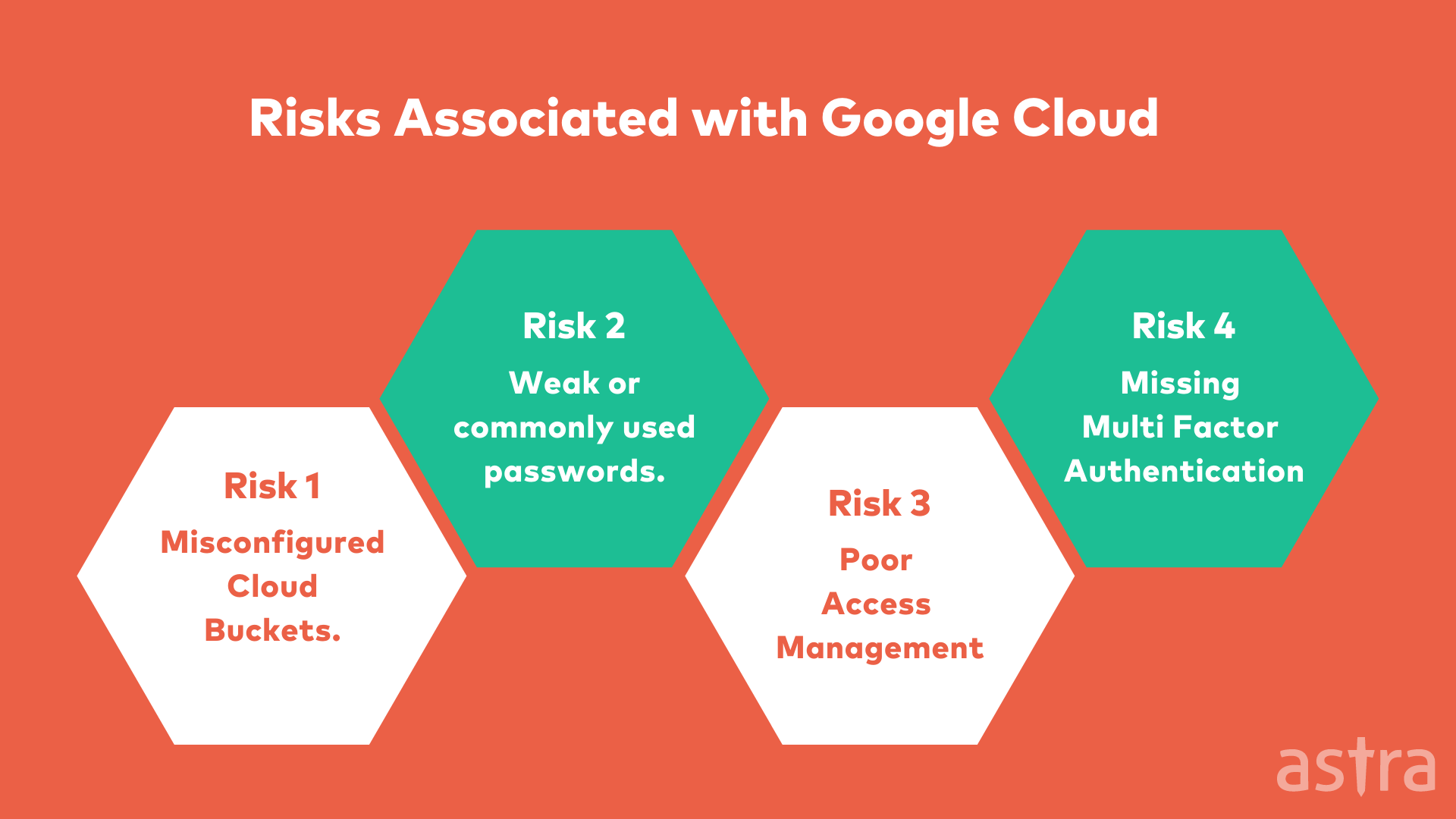
1. Misconfigured Cloud Buckets
Cloud computing offers a lot of benefits when it comes to scalability and cost-effectiveness. It is easier to manage and maintain with the proper security in place. However, when cloud security is misconfigured, it opens the door for hackers to breach your data, which can lead to a host of problems in terms of reputation and financial losses.
2. Poor Access Management
Poor access management is one of the most common security risks, which can be easily fixed. Cloud computing is transforming the way companies manage their IT. It is helping them to cut costs, improve agility and increase scalability. But with all the benefits, it also brings some risks that need to be addressed.
One of the most common cloud computing security risks is poor access management. Poor access management, or the lack of it, can be one of the most costly yet easily fixed security issues.
3. Missing Multi-Factor Authentication
Although many businesses implement multi-factor authentication (MFA) to protect their cloud infrastructure against cyber-attacks, not all are implementing it correctly.
The problem stems from the fact that multi-factor authentication is one of the most critical security components on the user’s side. It adds a layer to system access. Although it provides an extra layer of security, it’s not the only thing you should be doing.
How do hackers gain access to GCP Cloud Infrastructure?
Hackers use multiple tools and techniques to gain access to Google’s cloud infrastructure. Let’s discuss some of them in detail:
1. Weak Passwords
It’s no secret that many people use weak passwords like 123456 or password1. These are easy to remember but are also very easy to hack. Some people even have the same password for everything. If your password is the same for everything, it is effortless for hackers to get into your accounts because they can guess it on every site. Always use a different password for every site. If you use the same password for all of your sites, your accounts are vulnerable if one of the sites is hacked.
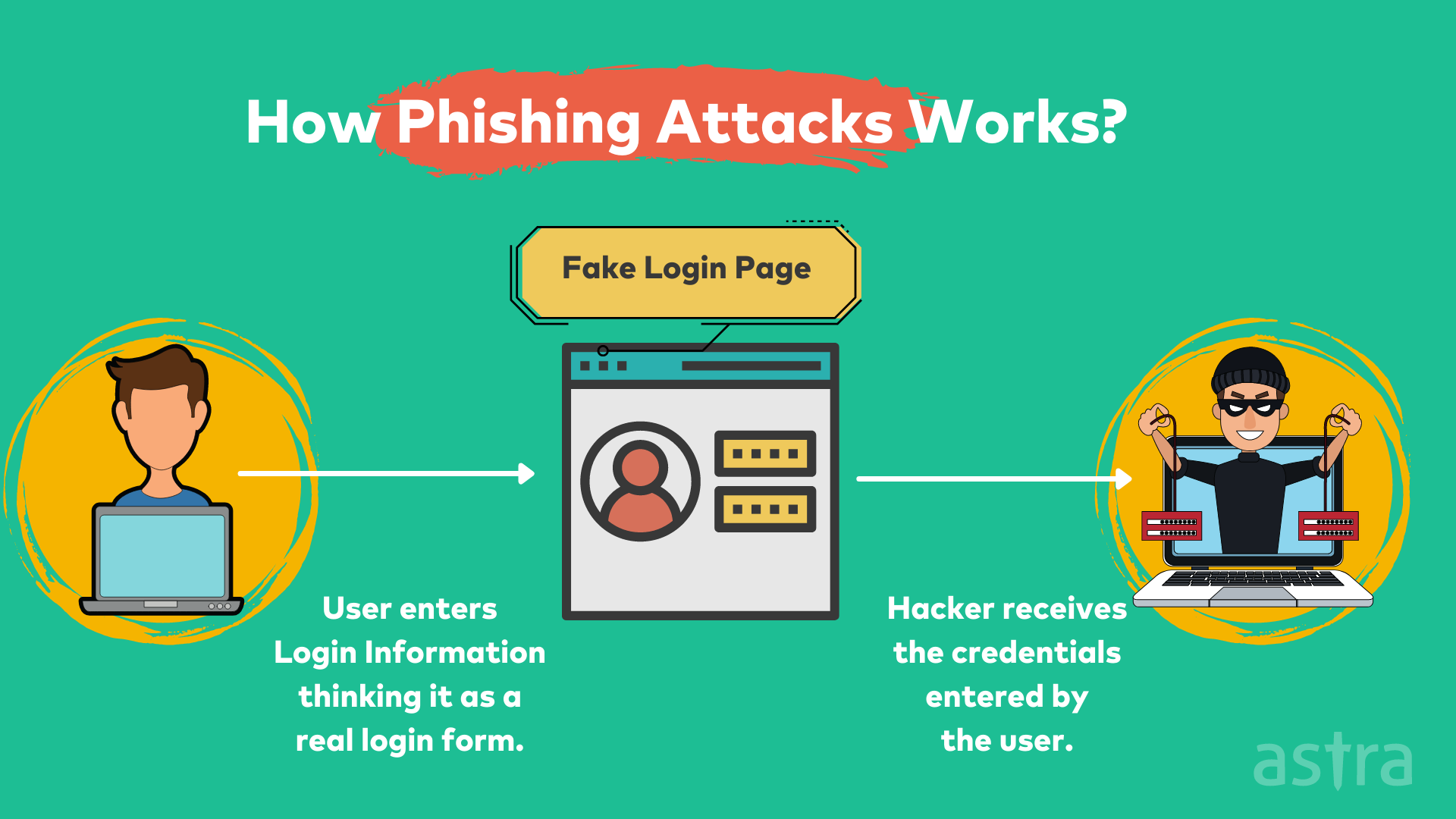
2. Phishing
Phishing is one of the most commonly-used methods by cybercriminals to gain access to login credentials. Phishing is the fraudulent attempt to acquire sensitive information such as usernames and passwords for malicious reasons by disguising it as a trustworthy entity in an electronic communication.
Phishing attacks are typically carried out with the help of social engineering techniques, such as spoofing email addresses or websites to trick users into disclosing confidential information.
Attackers use cloning tricks to clone the GCP login page and trick company employees to get access to email addresses and passwords, leading to compromised GCP infrastructure.
3. Leaked Access and Secret Keys
GitHub is a web-based hosting service for version control using Git. It’s currently the most prominent code host on earth, with 16 million code repositories. Sharing and collaboration that Github offers can be a great thing, but it does create some security issues that developers need to be aware of.
The problem is that many developers don’t realize that they’re leaving sensitive information (like their GCP access keys, OAuth Client ID) on GitHub. They do this by accident and don’t even realize it. The problem is that it’s tough to search for random strings like this.
3 Different approaches to test GCP Cloud Infrastructure
GCP Testing is not just about testing web applications but also validating that you have implemented suitable security measures on your cloud applications. Let’s understand three different ways to test Google Cloud Platform security.
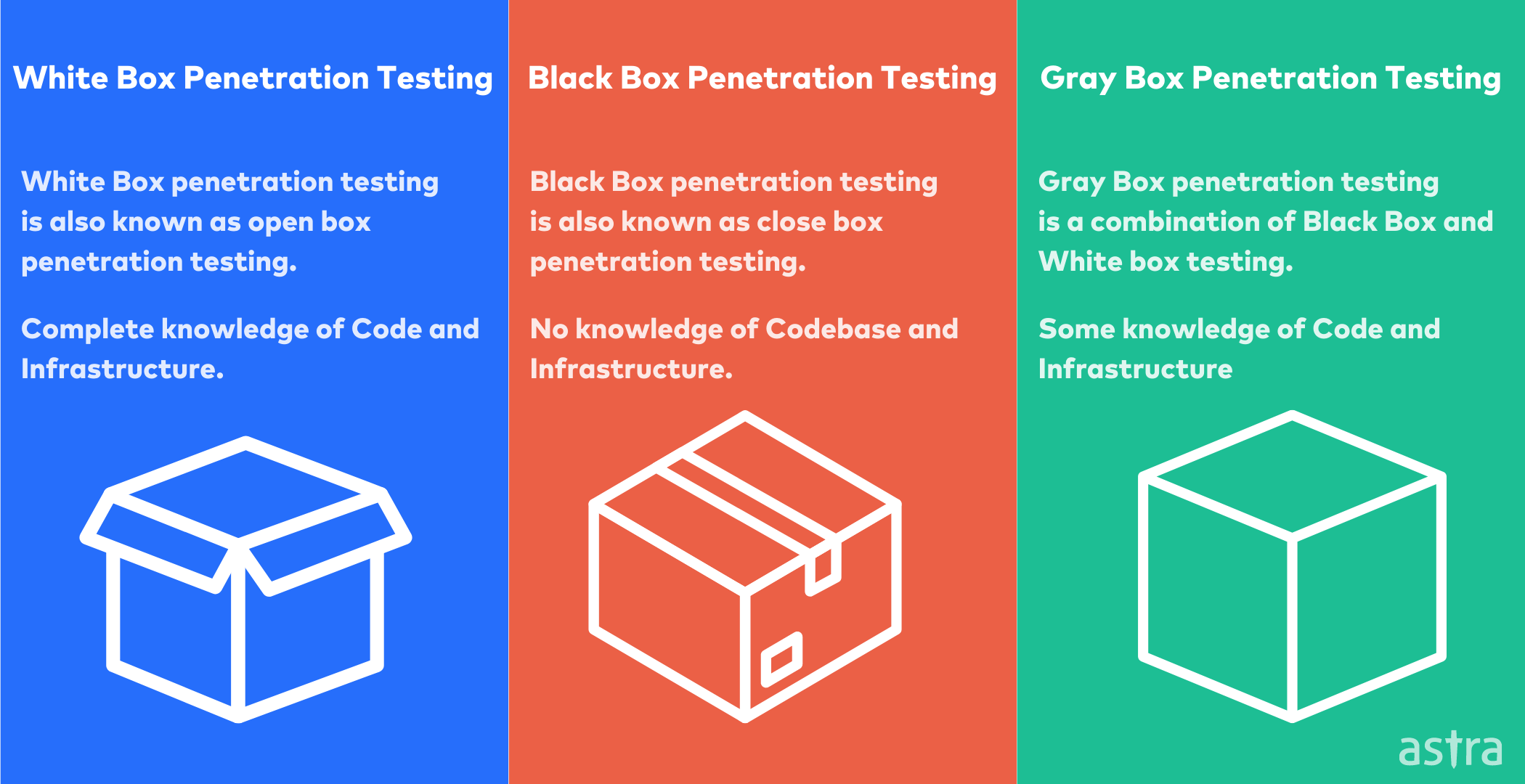
1. Black Box Testing
A black box pentest is a security assessment in which the tester has no prior knowledge of your systems. The black box testing follows the same principles of a black box flight test, where the tester has no previous knowledge of the aircraft being tested.
A black box test can be conducted with a third party, an internal stakeholder, or a combination of both. Black box testing is used to test security controls and evaluate the cloud environment’s overall security posture.
2. Gray Box Testing
The gray box pentesting is a method of testing that consists of black-box testing and white box testing. In this testing, some information is provided to the testers who are performing this. The testers will explore the application from the perspective of an external attacker.
Gray box testing aims to gain a greater understanding of the application and the context of the testing. A combination of black box and white box testing can give the application a better experience and provide a greater perspective of the application.
3. White Box Testing
White box pentesting is a method of assessing an application’s security by validating the application’s design against the threat model and by examining the source code for flaws. White box testing typically requires that the tester have extensive knowledge of the application’s design, programming language, and source code.
Best Practices For Google Cloud Security
1. Implement Multi-Factor Authentication
Everyone knows that logging into a web application is the easiest way to get into a corporate environment, which is why multi-factor authentication is such a great way to prevent attacks.
While the username and password remain the easiest way for attackers to get in, multi-factor authentication adds an extra layer of security. It helps reduce the chance of successful attacks.
2. Configure Inbound Traffic properly
Inbound ports are also one of the significant controls of GCP that needs to be tested while testing your GCP infrastructure. Here the inbound ports can be secured by enforcing inbound VPC firewall rules to block unwanted traffic from the Internet to your internal cloud instances.
3. Manage Logging and Monitoring
Logging and monitoring is a vital tool to keep our systems secure and working correctly. Logs give us a history of any changes we make to our systems and allow us to troubleshoot problems and improve the performance and security of our infrastructure.
Logs give us a history of any changes we make to our systems and allow us to troubleshoot problems and improve the performance and security of our infrastructure.
4. Use Key Rotation Techniques
Key rotation is the process of exchanging existing system keys for new system keys. Keys are used to encrypt sensitive data. Keys are encrypted using encryption algorithms and then stored on the system. The rotation of keys is done to prevent an adversary from obtaining the current key, then decrypting data encrypted with that key.
Key rotation is performed by updating the encryption software with the newly generated key of the same encryption algorithm. The new key is then used to encrypt the existing data.
GCP Security Tools
Check out the below-mentioned list of amazing open-source tools to enhance GCP security:
- GCP Firewall Enum: This tool analyzes the output of several google cloud commands to determine which compute instances have network ports exposed to the public Internet.
- GCP Bucket Brute: This is a python script used to enumerate Google Storage buckets, determine what access you have to them, and determine if they can be privileged escalated.
- GCP IAM Collector: This tool is a python script used for collecting and visualizing Google Cloud Platform IAM permissions by iterating over GCP projects using Google Cloud Resource Manager API.
How Astra’s Pentest suite can enhance your GCP Security?
Astra has been providing Google Cloud Security testing services for a long time. Astra is one of the first security companies to offer penetration testing services for GCP.
With Google’s focus on the cloud, it is becoming increasingly important to have a solution partner that can offer you an independent external perspective on your security posture. Through our Google Cloud Penetration Testing, Astra helps you identify security gaps in your Google Cloud environment and provide remediation recommendations.
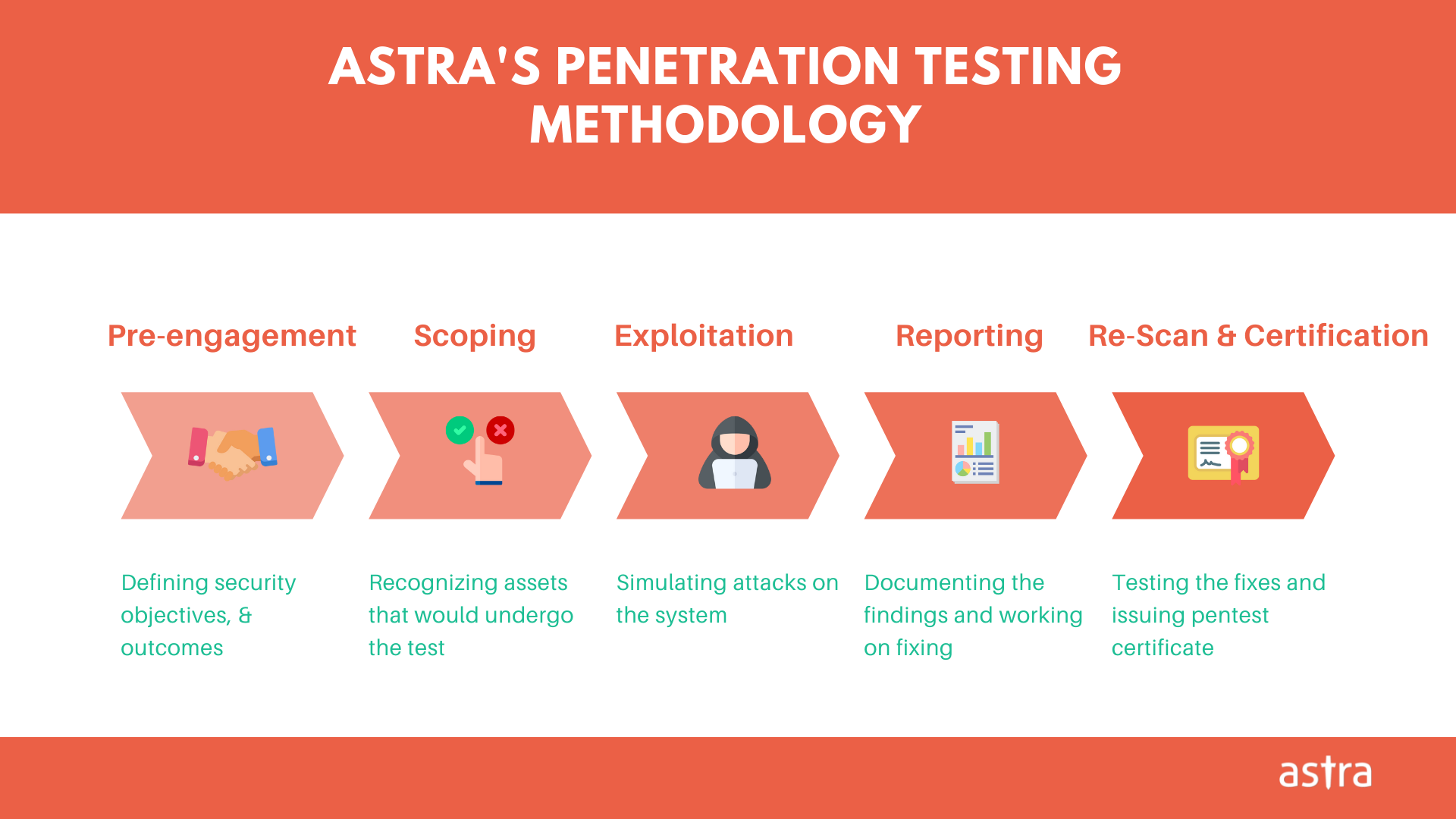
The GCP pentest is conducted using our proprietary methodology.
Have a glimpse at Astra’s Penetration Testing Methodology.
Conclusion
With over 49% running workloads, Google is a significant player in the cloud infrastructure market. They are the second-largest player in the cloud infrastructure market. While Google’s security is top-notch, it is always a good idea to have a checkup now and then. Astra’s Google Cloud Penetration Testing can help you maintain a secure GCP infrastructure.
FAQs
Why is GCP Security important?
GCP penetration testing services will help you identify and understand the security vulnerabilities of your GCP Cloud deployment which helps in GCP security. As a result of this test, you can get a comprehensive and thorough insight into the security of your Cloud deployment and take the necessary steps to fix the issues identified.
How do hackers gain access to GCP Cloud Infrastructure?
Hackers use multiple tools and techniques to gain access to Google’s cloud infrastructure. Let’s discuss some of them: Weak Passwords, Phishing, Leaked Access, and Secret Keys
















