Cloud penetration testing is a unique network penetration testing that focuses on cloud applications and infrastructure security. The goal of cloud penetration testing is to test for cloud application vulnerabilities that may impact the security of the organization’s internal network. Google Cloud Platform (GCP) is one of the widely used cloud platforms, and it’s equally important to understand how to keep it secure.

What is GCP?
GCP or Google Cloud Platform is one of the widely used cloud platforms that is used for creating websites, and for other organizational applications.
GCP’s applications for an organization can be for varied purposes like infrastructure management, back services, and even data processing.
What is Google Cloud Penetration Testing?
Google Cloud Penetration Testing is the process of pentesting done on google cloud applications.
GCP pentesting consists of testing various vulnerabilities (found through GCP vulnerability scanning) to check if the application can withstand an attack.
It is done to determine whether the GCP application in question needs a security upgrade or improvement.
Why is Google Cloud Penetration Testing important?
Google cloud penetration testing is a mandatory process for organizations that are seriously considering cloud deployment. Penetration testing is an integral part of any security program, but it’s even more critical in the cloud. That’s because cloud environments are shared resources that sit outside an organization’s firewall.
For penetration testing services to be effective, it needs to be comprehensive. That means testing not just the application but also the underlying cloud infrastructure. It also means testing the whole system, including the cloud, to ensure there are no weak spots.
The importance of google cloud penetration testing is not limited to this; here are few more points to understand the purpose of pentest:
- Identify security vulnerabilities
- Identify broken access controls
- What all things hackers can get from your google cloud?
- Real-life exploitation of security risks and vulnerabilities.
- Standard best practices to prevent security risks.
Does GCP allow penetration testing?
We all know that the Google Cloud Platform is becoming more and more popular in the industry. Google has become one of the big three cloud service providers. Although AWS and Azure pentest needs permission but Google never stops any google cloud user keeping in mind they follow the guidelines.
If you plan to evaluate the security of your Cloud Platform infrastructure with penetration testing, you are not required to contact us. You will have to abide by the Cloud Platform Acceptable Use Policy and Terms of Service and ensure that your tests only affect your projects (and not other customers’ applications).
– According to Google
What are 3 different types of Google Cloud Pentest?
Google Cloud Penetration is considered to be of 3 different types similar to traditional penetration testing. Let’s understand the types of google cloud pentest in detail:
1. Black Box Penetration Testing
Black box penetration testing is an attack simulation in which the cloud penetration testers have no prior knowledge of or access to your cloud systems. With black-box penetration testing, cloud penetration testers must work only with the information they can find online. This is the most realistic way to test your security because a stranger is genuinely attacking you with no knowledge of your cloud infrastructure.
2. White Box Penetration Testing
White box penetration testing is a type of google cloud penetration testing in which the white box penetration tester is granted admin-level access to google cloud systems. This is also known as visible penetration testing.
3. Gray Box Penetration Testing
A grey box penetration test is an assessment strategy that combines both white box and black box penetration testing. It is designed to simulate an attack by internal malicious cloud users having limited access to the google cloud or an external hacker. A gray box penetration test determines how well the organization can detect, respond to, and repair the attack.
Also Read: API Penetration Testing: What You Need To Know
List of GCP controls to be tested for security
Many organizations see cloud computing as a cost-effective way to get IT services. But the cloud is not a panacea for all of an organization’s security ills. Cloud security is a significant concern for many organizations.
According to a survey by helpnetsecurity, more than 35% of organizations suffered a serious data leak or a breach in the past 12 months, and eight out of ten are worried that they’re vulnerable to a major data breach related to cloud misconfiguration.
Let’s understand the top 4 controls that need to be tested while doing google cloud penetration testing:
1. Access Level Controls
Privilege escalation attacks are one of the most severe threats to any cloud infrastructure. It enables the attacker to compromise high-level accounts and other security mechanisms by targeting the access level controls (ACL). It can ultimately result in the attacker gaining complete control over the system. Hence, testing for access level against attacks such as privilege escalation is important.
2. Misconfigured In-bound ports
Inbound ports are also one of the major controls of GCP that needs to be tested while pentesting your GCP infra. Here the inbound ports can be secured by enforcing inbound VPC firewall rules to block unwanted traffic from the Internet to your internal cloud instances. Inbound firewall rules include ICMP, IPv4, and IPv6 traffic andare created to block certain types of traffic or specific ports.
3. Over Permissive Storage Buckets
Storage Bucket is a scalable storage service that offers developers and enterprises a variety of features to store and retrieve any amount of data, at any time, from anywhere on the web.
When applications no longer need access to your data, they should revoke their authentication credentials. You can do this for Google services and APIs by logging into your Google Account Permissions, clicking on the unneeded applications, and clicking Remove access.
4. Logging and monitoring
Many companies are not using any of the monitoring tools available to monitor application logs. In all cases, you need to enable logging and monitoring on servers that have been provisioned by google cloud.

Steps to take before performing Google Cloud Penetration Testing
Google penetration testing is a tedious task and should be done correctly to avoid data leak, spamming or reputational loss. Here are some things that one need to keep in mind before starting penetration testing:
1. Develop a penetration testing plan
First things first, you need to have a proper plan on how things will work during the pentest, what all resources are to be tested. Should the pen-testers exploit the vulnerability, or should they notify you first? These all things need to be written down in a proper document and then shared with the penetration testing team before conducting a google cloud pentest.
Checkout: The finest Google cloud services security
2. Create Staging Projects/Instances
No one wants the production environment tested because the whole organization’s ecosystem will be down if something happens. It might take hours to fix that up, depending upon the attack vector. Most companies create staging or test projects in the google cloud platform for cloud pentest. Still, the most important thing to remember is that the staging environment must be a production replica.
3. Setup IAM for Pentest Team
Depending upon the type of pentest that you are conducting on your cloud infrastructure. You need to give proper access controls to the pentest team to access the appropriate resources such as GCP App Engine, Compute Engine, etc., for the penetration testing.
4. Authorize IP Addresses
Google cloud pentest will include both types of testing, i.e. manual and automation testing. As the cloud infrastructure does have restrictions on the inbound traffic, you need to whitelist the list of IP addresses provided by the pentest team so the cloud penetration testing tools can scan your cloud infrastructure.
5. Notify your Customers
Last but not least, notify your customers that you are undergoing google cloud penetration testing, which might lead to an outage of the database or any other resource. Although there’s always a different environment for penetration testing, there can always be a chance that both environments share a shared resource such as Storage Bucket, etc.
3 Step methodology to perform penetration testing on GCP
Cloud penetration testing is an integral part of any complete security strategy for cloud computing. It is all about making sure that your cloud is safe. The following are the primary stages of cloud penetration testing:
Step 1: Discovery and Evaluation
The primary aim of the evaluation stage is to examine the security of an organization’s IT infrastructure in the cloud. The penetration testers look at the existing cloud infrastructure during this stage to determine whether it can be compromised easily.
Furthermore, The penetration testers test the cloud infrastructure using various manual and automatic security testing techniques like using a google cloud security scanner to find the loopholes within the system.
Step 2: Exploitation
The exploitation phase is where actual attacks are stimulated from the authorized IP addresses to organizations google cloud infrastructure. The main motive of the exploitation phase is to test how the cloud infrastructure will perform when an actual attack happens, how much information an attacker can fetch if the infrastructure is compromised and so on.
Step 3: Reporting
The final step of google cloud penetration testing is the same as that of every pentest. The pentester team generates a detailed list of IP addresses scanned during google cloud pentest and the list of vulnerabilities found on the target IP addresses. The report also contains steps to reproduce and fix the issues, which are shared with the development or DevOps team.
Tools used in GCP Pentesting
Following are some of the most-used open-source tools for google cloud penetration testing:
- GCP Firewall Enum: This tool analyzes the output of several google cloud commands to determine which compute instances have network ports exposed to the public Internet.
- GCPBucketBrute: This is a python script used to enumerate Google Storage buckets, determine what access you have to them, and determine if they can be privilege escalated.
- GCP IAM Collector: This tool is a python script used for collecting and visualizing Google Cloud Platform IAM permissions by iterating over GCP projects using Google Cloud Resource Manager API.
GCP Penetration Testing Provider – Astra Security
The process of finding security vulnerabilities in Google cloud infrastructure is a complex task. It requires a tremendous amount of experience and expertise.
Astra is not just an ordinary security provider. It’s more than that. Astra is a team of highly professional and fun individuals that work hard to keep your cloud infrastructure safe and secure from hackers and cybercriminals.
Conclusion
As cloud computing becomes more popular, most businesses’ most common security concern is how secure their data is in the cloud. However, this popularity comes with a price: the more popular a platform is, the more likely hackers will target it. Google Cloud penetration testing is a vital part of your security strategy. Astra’s Google Cloud penetration testing will help you identify security vulnerabilities and weaknesses in your infrastructure and allow you to fix them before malicious attackers do.
FAQs
1. What is the timeline for GCP pentesting?
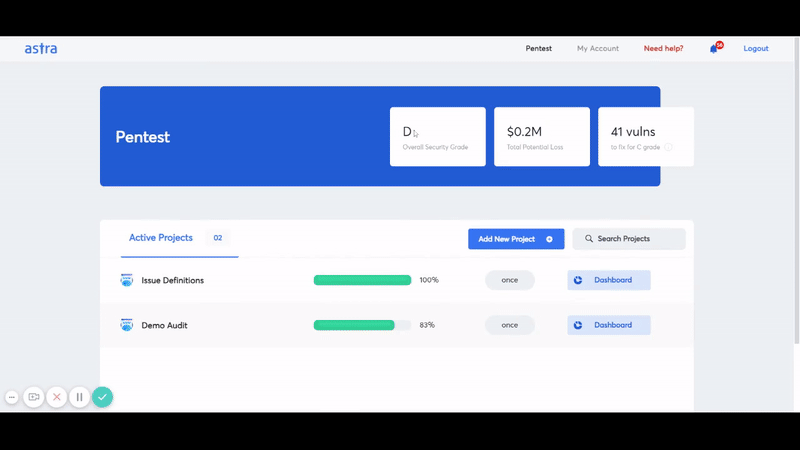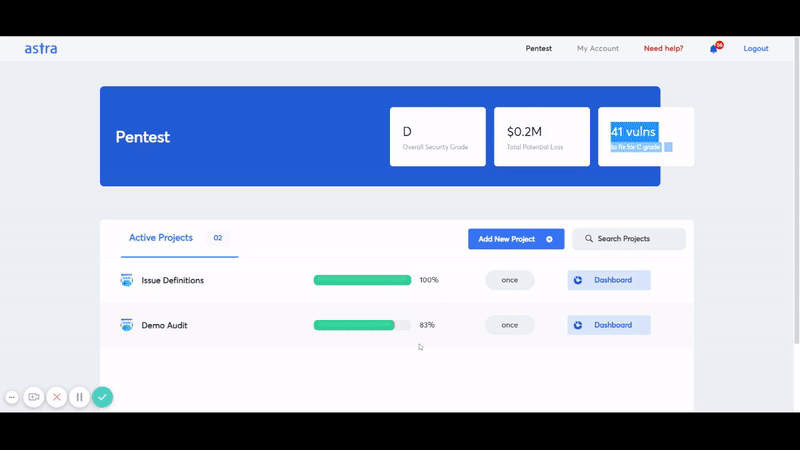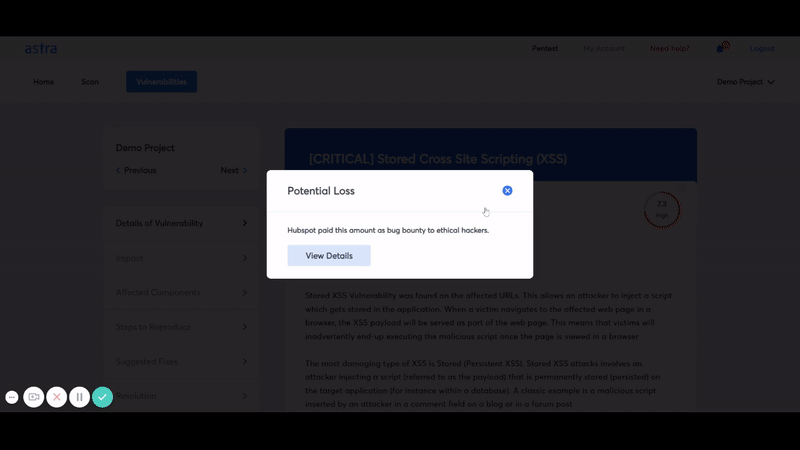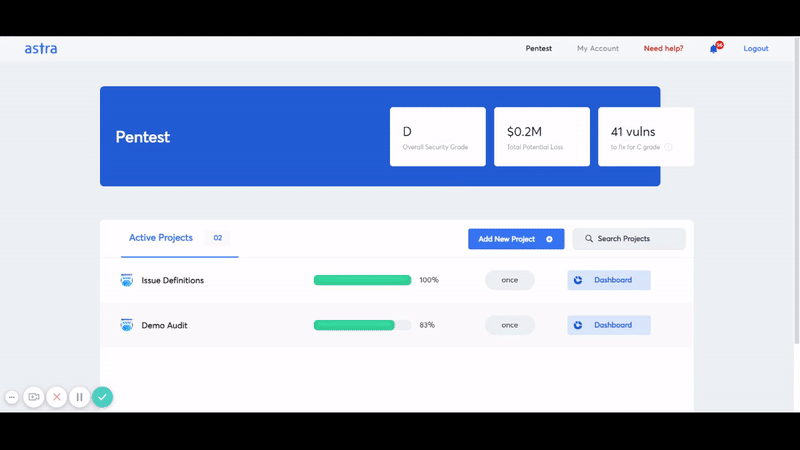
It should take no more than 4 to 5 days to perform Google cloud penetration testing. The vulnerabilities start showing up in Astra’s intuitive dashboard from the 2nd day.
2. How much does penetration testing cost?
Penetration testing in Google cloud costs between $490 and $999 per scan depending on the plan you are on.
3. Why choose Astra Pentest for Google cloud?
1250+ tests, adherence to global security standards, intuitive dashboard with dynamic visualization of vulnerabilities and their severity, security audit with simultaneous remediation assistance, multiple rescans, these are the features that give Astra an edge over all competitors.
4. Do I also get rescans after a vulnerability is fixed?
Yes, you get 1-2 rescans depending on the plan you are on. You can use the rescans within a period of 30 days from initial scan completion even after a vulnerability is fixed.
















