WordPress is one of the most popular CMSs used to create websites and e-commerce stores. However, its popularity has made it a frequent target for hackers and SEO spammers. Hackers target WordPress based sites with different kinds of malware attacks and hacking attempts. One of most frequent hacking technique they use is they try to manipulate search indexes to include undeserving content on prominent search positions. This Black Hat SEO (hacking) technique is also dubbed as ‘WordPress Pharma hack or SEO Spam‘.
Why do hackers target WordPress sites with Pharma Hack?
The answer is simple. Online searches are a major source of valuable referrals, and SEO hacks are the easiest way to achieve this without putting in the necessary work. It secures hackers a legit place in the SERP by hacking into high-authority sites and infect them with spam redirection hacks. A recent such attack, “Pharma Hack” or “Pharma SEO Spam” is somewhat similar to Spam link Injection attacks that have come to light, and were found to be one of the most common Black Hat SEO techniques used by hackers.
What is a Pharma Hack?
Pharma hack is a type of malware infection that infects WordPress websites which leads a legitimate site to redirect to spammy pages that display advertisements selling duplicate versions of branded goods of illegal drugs such as Viagra and Cialis. Sometimes there can be an infection of other sorts of pharma products too. However, Viagra and Cialis are the most common.
In one of the recent WordPress Pharma hacks, we even see a sophisticated version of the hack. In this version, the hackers tailored the Google search results with a website’s name in the title. This makes people believe that a legit website is indeed about pharma products.
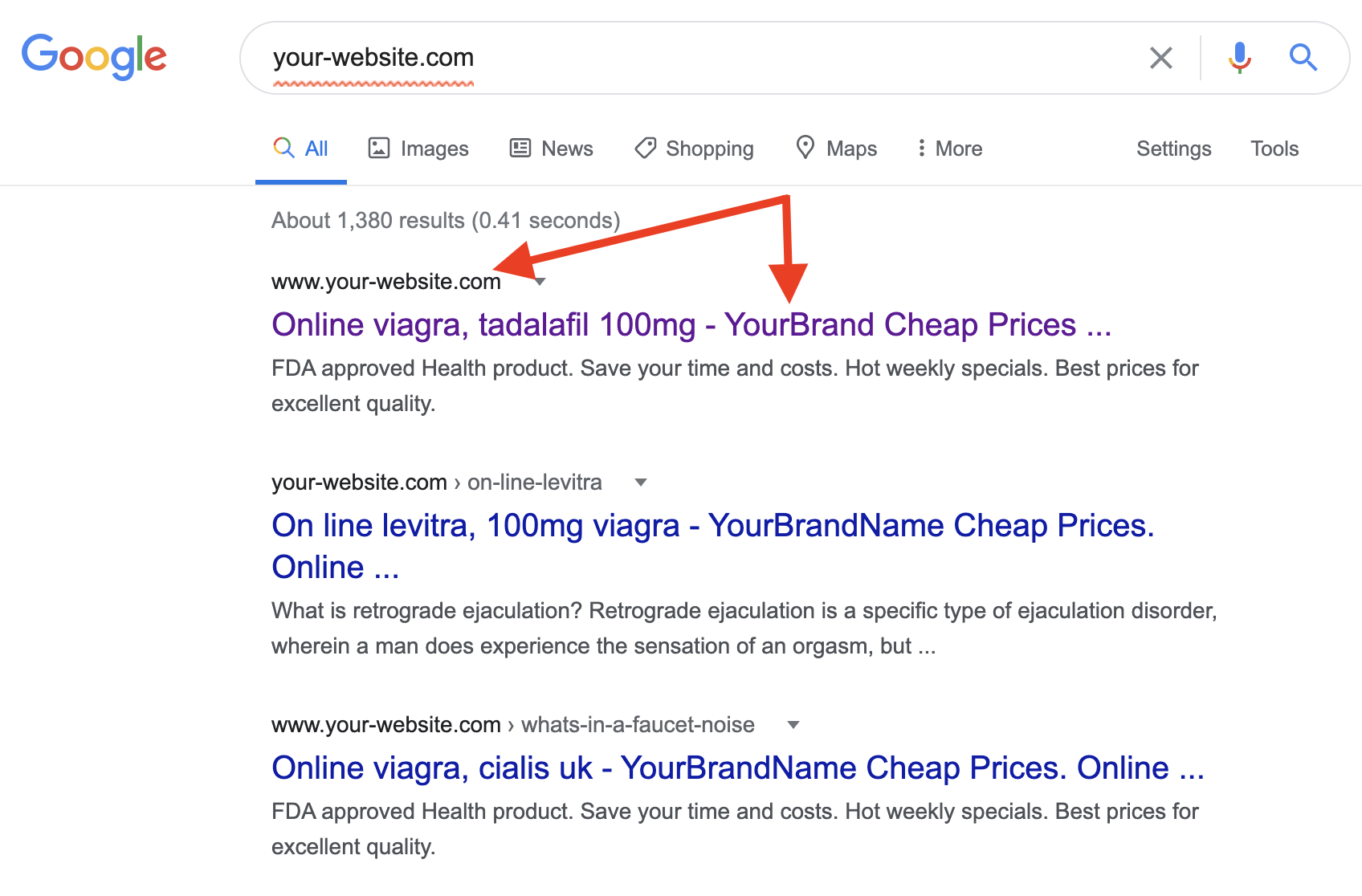
How to find if your WordPress site is infected with Pharma Hack
SEO spam is difficult to detect because it is not directly visible to webmasters. Spammers do everything to hide their work, following practices such as ‘cloaking.’ However, there are ways you can check whether your website is infected with a Pharma hack or not. Read on to find out how you can find the WordPress pharma hack:
Method 1: Check with Google Search
A list of affected websites can be displayed by a Google search with keywords like viagra wp-page. But, as a result of the webmaster policies of Google, the affected websites are not visible on the first page. So, you’ll have to scroll till page 3 or 4. If your website appears in the search, it means that you are a victim of the WordPress Pharma Hack or other Black Hat SEO Spam.
This list not only includes infected websites but also displays fake pages. Clicking on such pages might redirect you to other pages or load the content on the same page as a result of infection.
To check which pages of your website is infected with viagra SEO spam. Add the keyword ‘viagra‘ with your domain name in google search i.e. viagra mydomain.com. Sometimes only a few pages on your website are infected, and those are not visible to you. This search will bring out those infected pages. In case they redirect to websites selling Viagra and Cialis, you are infected with SEO spam. Sometimes rather than redirecting, the content is loaded on the same page as a result of infection.
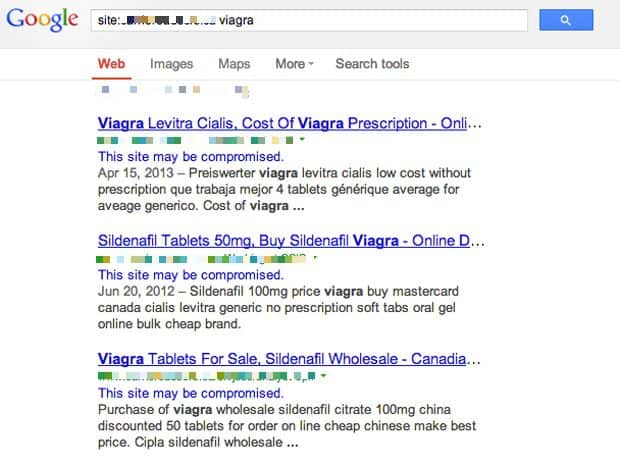
Method 2: Check results as Google Bot
As stated, these spam pages are not visible on the search engine but certain user agents, like Googlebot, can see them. In order to view what the Googlebot sees, you can use a browser User-Agent Switcher. You can install one for Chrome or Firefox.
- Install your favourite User-Agent Switcher add-on
- Navigate to the infected webpage
- Edit the User-Agent string to any of the ones given below:
a) Mozilla/5.0 (compatible; Googlebot/2.1; +http://www.google.com/bot.html)
b) Googlebot/2.1 (+http://www.google.com/bot.html) - Right-click on the page and view the page source. This will enable you to see the redirect.
Note: Keeping the User-Agent Switcher active for long could get you blocked or blacklisted from websites that maintain proper security because you will appear as Googlebot to them.
Similar to this, if you’re looking to remove pharma hack in Drupal CMS or PHP sites then read the Drupal pharma hack guide.
Anatomy of the WordPress Pharma Hack
Occurrence
To conduct a WordPress pharma hack, the attacker first exploits a known vulnerability or a zero-day exploit. Here is an exhaustive list of things that can go wrong in such a case. To simplify, a few of the most common ones are:
- SQL injections or XSS occur because of faulty coding standards. It’s a good idea to keep a tab on these two.
- Weak account or FTP passwords are the second major cause. Recently, the GitHub repository of Linux Gen, too, was hacked as a result of weak credentials.
- Most of the time, content listing and error display is enabled. As a result of this, crucial files are openly readable on the net.
- Using unpatched or outdated plugins is one of the major causes of WordPress hacks. Stay updated!
Persistence
WordPress pharma hacks work by altering the contents of the root directory. Most spam attacks happen through /misc folder and /includes folder. Spammers gain persistence (prolonged access) by known methods like:
- Modifying files like
index.php, wp-page.php, nav.phpetc. - Adding new pages like
leftpanelsin.php, cache.phpetc. - Editing
xmlrpc.phpto avoid detection by webmasters. - Using base64 encoding to obfuscate code.
- Hiding the spam files inside
/imagesfolder. Web crawlers don’t expect to see files here so it evades detection. - Appending dot before the file extension. Therefore, renaming the page as
.somefileto get invisible. - Cloaking: Differentiating between web crawlers based on user-agent. As a result, the content seen by Googlebot is different than content seen by Mozilla user.
- Using cron jobs to reinfect.
Results
- Your website loses hard-earned reputation as a result of displaying Viagra and Cialis Ads.
- You could get blacklisted by Google, which makes regaining reputation difficult.
- Your users don’t trust your website.
- Your search rankings take a hit and go down.
- Your website begins to generate clicks for other websites that you’ve worked hard to get.
Google showing Pharma spam results for your website? Drop us a message on the chat widget.
How to Fix the WordPress Pharma hack
The WordPress Pharma Hack is hidden. So, looking for infected files and removing them is going to be somewhat of a long, tedious task. Here’s what you should do to remove the hack:
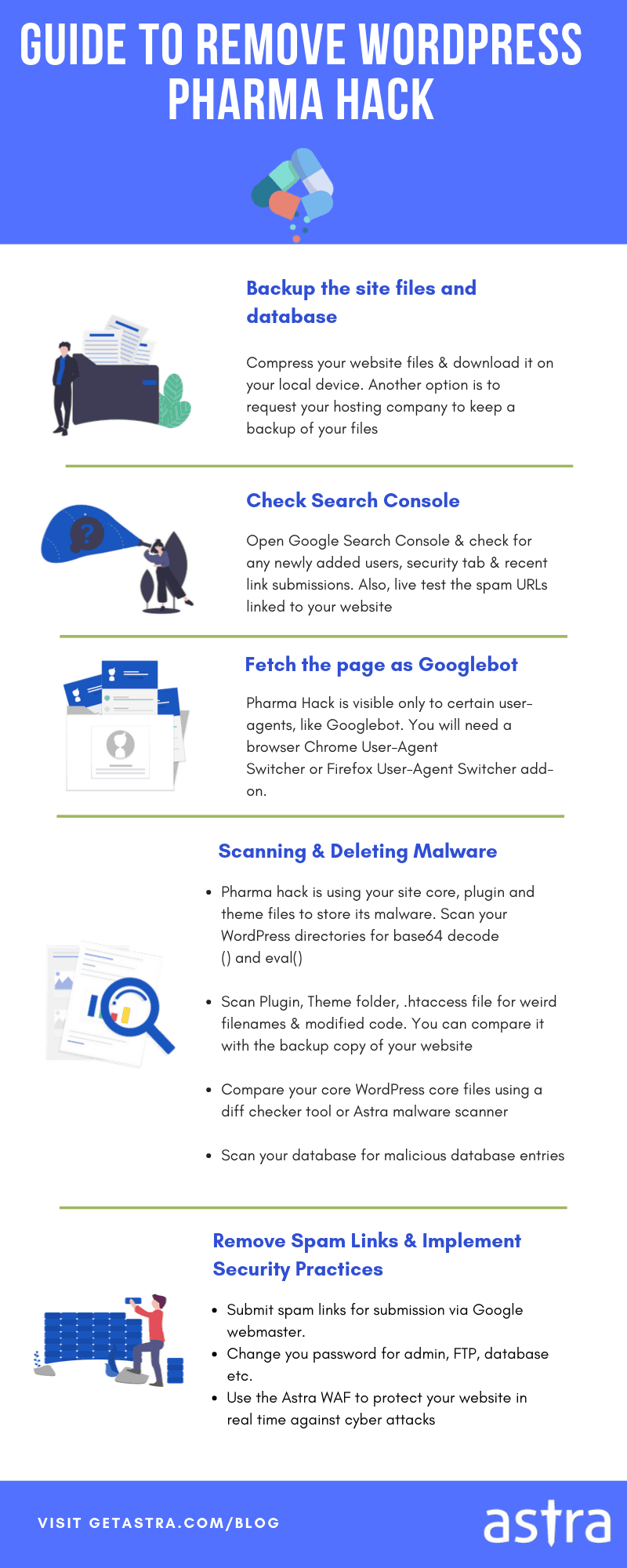
1. Take a backup
Creating a complete backup of your website is a recommended practice. It might come in handy if anything goes wrong with the cleanup process. So, always make sure to have a backup strategy ready. The backup should essentially include the core files, the database, and plugin and themes files.
2. Scan your website for malware
Use online malware scanning tools like VirusTotal to flag the infection. You can also try Astra’s Malware Scanner for a more accurate scanning. This would flag all the malicious files and code in your website in minutes, and help escalate the malware removal process for you.
3. Remove any infected files
Connect to your hosting server through FTP. You can also use a file manager. Then, navigate to the /wp-contents/ folder and look for any hacked files in plugins.
The hacked files will have words like .class, .cache, .old in them to camouflage as plugin files. A dot (.) in front of the file name will make them hidden unless the “show hidden files” option is selected. Remove any such files.
4. Clear the temp directory
The /wp-contents/temp/ directory can appear as a result of the infection. Go to /wp-contents/temp/ and clear its contents. Hackers utilize the temp folder and TMP files to avoid any kind of corruption during the installation of malware.
5. Check the .htaccess file
The .htaccess file is a server configuration file. It defines the way server requests are processed. Hackers also utilize the power of the file to create backdoors into your website. Look out for code like this:
RewriteEngine On
RewriteCond %{ENV:REDIRECT_STATUS} 200
RewriteRule ^ - [L]
RewriteCond %{HTTP_USER_AGENT} (google|yahoo|msn|aol|bing) [OR] #checks for Google, Yahoo, msn, aol and bing crawler
RewriteCond %{HTTP_REFERER} (google|yahoo|msn|aol|bing)
RewriteRule ^(.*)$ somehackfile.php?$1 [L] #redirects to a hack file
You can also regenerate the .htaccess file.
- Go to your WordPress dashboard.
- Click Settings, then select Permalink.
- Click Save!
6. Remove malicious code from the database
It is highly recommended that you create a backup before making any changes to the database. If you haven’t done it before, you should really do it now, as this step could be sensitive.
For this step, you could buy professional malware removal services or try to clean your database on your own.
- Go to phpMyAdmin
- Select the database
- Click on wp_options table
- Search for the malicious entries using the Search tab
Some malicious entries you should search for are:
- wp_check_hash
- class_generic_support
- widget_generic_support
- ftp_credentials
- fwp
Note: Be very careful not to delete important information from the wp_options table, as it could cause your website to malfunction and crash.
Note: If you are not so well-versed with tech, it is better to seek external help.
7. Look for and remove suspicious code
Suspicious-looking code often is one of the major causes for WordPress websites getting hacked. The sample code would probably look something like this:
<ul id="menu">
<li><a href="attackerdomain.com">Something1</a></li>
This kind of code redirects your website to an attacker-controlled domain. So it’s a good idea to check for any domains that are not familiar. This is one of the major causes of WordPress pharma hacks.
Often the attackers hide their code in base64 to avoid detection. For example, attackerdomain.com would look something like “YXR0YWNrZXJkb21haW4uY29t”, making it hard to detect. In order to search for base 64 encodings in files, the grep command is helpful:
find . -name "*.php" -exec grep "base64"'{}'\; -print &> b64-detections.txt
This piece of code basically searches into the .php files of your choice for base64 encodings. Thereafter the result is stored in the file named b64-detections.txt. Finally, you can use an online resource to decode these and see what was going on behind the scenes.
8. Clear the temp directory
Go to /wp-contents/temp/ and clear its contents. Hackers utilize the temp folder and TMP files to avoid any kind of corruption during the installation of malware.
9. Scan for content differences
You can use online plugins to scan for file changes. An example of such a scanner is the Exploit Scanner. It scans all core files and 3rd party files present in WordPress’ official repository for suspicious and unusual file names or entries.
After figuring out which files are hacked, you could either delete infected code or restore the plugin files. It is important to thoroughly clean the code – any malicious code left behind could reinfect your website.
How to Prevent the WordPress Pharma Hack
- Use strong user credentials and passwords for your website and database login. Hackers can easily brute-force weak user credentials and then hack into your website.
- Implement a website firewall for your WordPress site. It will help you secure your site against Pharma hack infection and protect from a wide range of cyber threats.
- Limit folder permissions to avoid unwanted access.
- Disable or uninstall any suspicious or unused plugins and themes in your WordPress. Most plugins and themes can become easy entry points for the hackers due to vulnerability present in them.
- If your CMS core, plugin, or theme version is outdated then should update them as soon a possible to prevent vulnerability exploitation which may make you a victim of Pharma hack.
- It is always a good practice to know all the security loopholes and vulnerabilities present in your WordPress site. To uncover such potential security loopholes and fix them before hacker take advantage of them – you should do regular security audits for your website(s) and protect against hacks such as Pharma hack.

















[…] site also loses its valuable customers. A similar case was seen when Drupal was infected with the Pharma hack recently, where SEO spammers used its vulnerabilities to redirect users to pages selling viagra and […]
That’s really nice post. I appreciate your skills. Thanks for sharing.