WordPress sites have yet again become the victim of a widespread redirection malware. A lot of WordPress web owners contacted us worried about their websites redirecting or admin panel throwing an error.
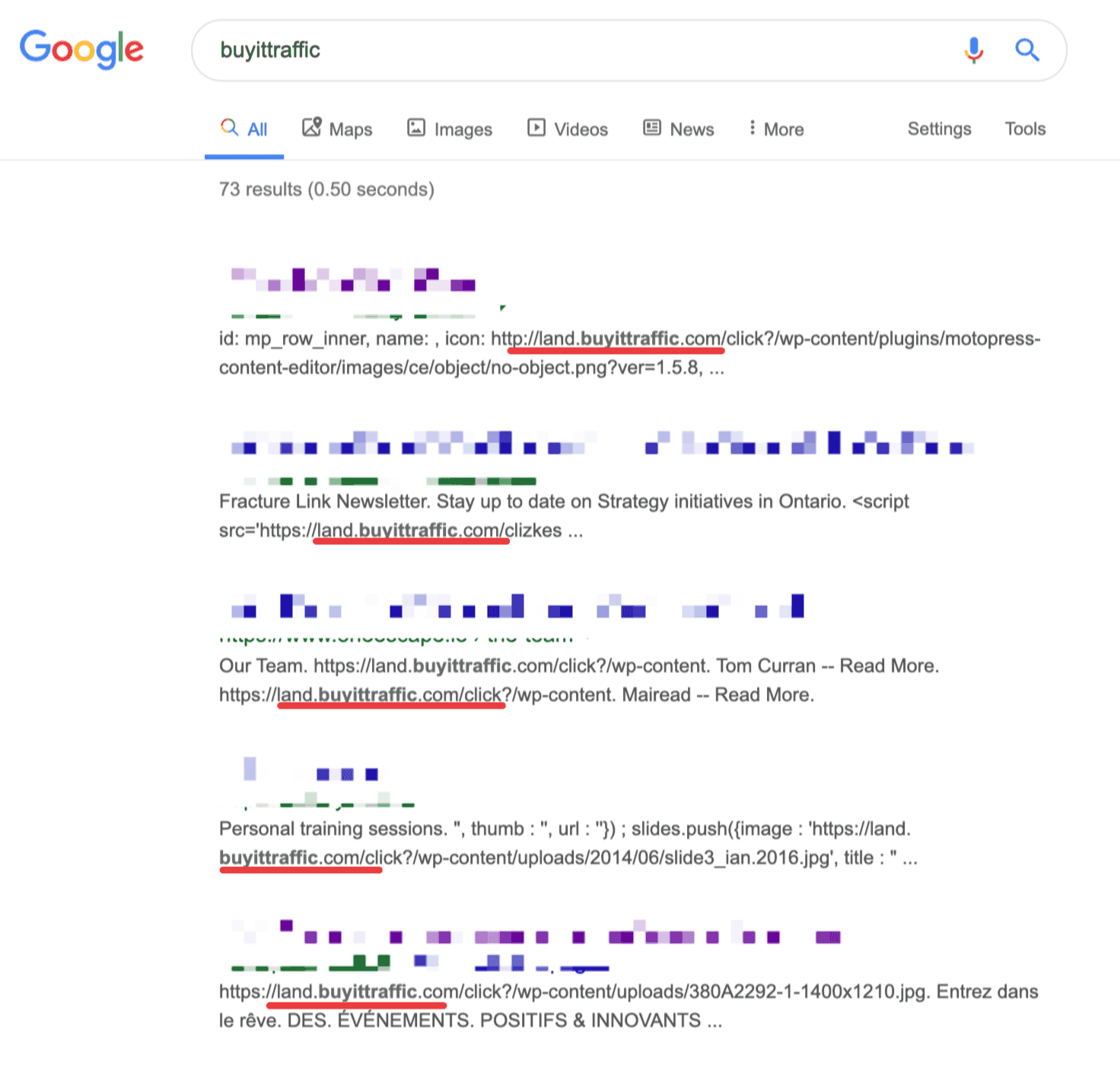
While doing the cleanups on these websites, we could draw similarities in their hacking fashion. All these websites happened to have been infected by the same redirection malware. This malware redirected them first to a malicious domain by the name buyittraffic[.com] and then finally to a domain named sinowncrers12 [.] live, cuttraffic[.com] or puttraffic[.com] or importtraffic[.com] or gianttraffic[.com], js. greenlabelfrancisco. [com]/touch.js, dl. gotosecond2.[com]/talk.js, statistic[.]admarketlocation[.]com, stat.trackstatisticsss.[com]slan.[js], silvergatest15 [.] live, www.wow-robotics.[xyz], planeobservetoo1[.]live, dock.lovegreenpencils[.]ga/m.js?n=nb5, cht.secondaryinformtrand[.]com/m.js?n=nb5, main.travelfornamewalking[.]ga/, irc.lovegreenpencils[.]ga/, etc.
In many cases, we are also seeing websites to redirect first to clicks.worldctraffic[.com], top.worldctraffic[.com], red.toupandgoforward[.com], bluelabelmoscow.[com] or ticker.trasnaltemyrecords[.com] before landing on one of the above sites.
It is a typical example of malware redirection ‘chains’. Where websites get redirected multiple times before landing on the desired domain.
On further investigation, a few hundred websites seem to be infected with this malware now:
Symptoms That Tell Your Website is Hacked
The homepage redirecting to other domains is, obviously, a tell-tale sign of the hack. However, there are other signs as well, attached to this malware. You can tell you are hacked, if:
- you are unable to access the website.
- you are unable to log into your wp-admin panel.
- your wp-admin throws a 404 error.
- you log in to the WordPress admin area, and it gives the following error:
“ERROR: There is no user registered with that email address”.
If your websites are also showing similar symptoms, contact us. We will clean your website of the hack in no more than a few hours. Rather our malware scanner does finds malware within minutes.
Technicalities Behind the Hack
I have already mentioned how this malware redirects your website multiple times. Let’s see how this happens:
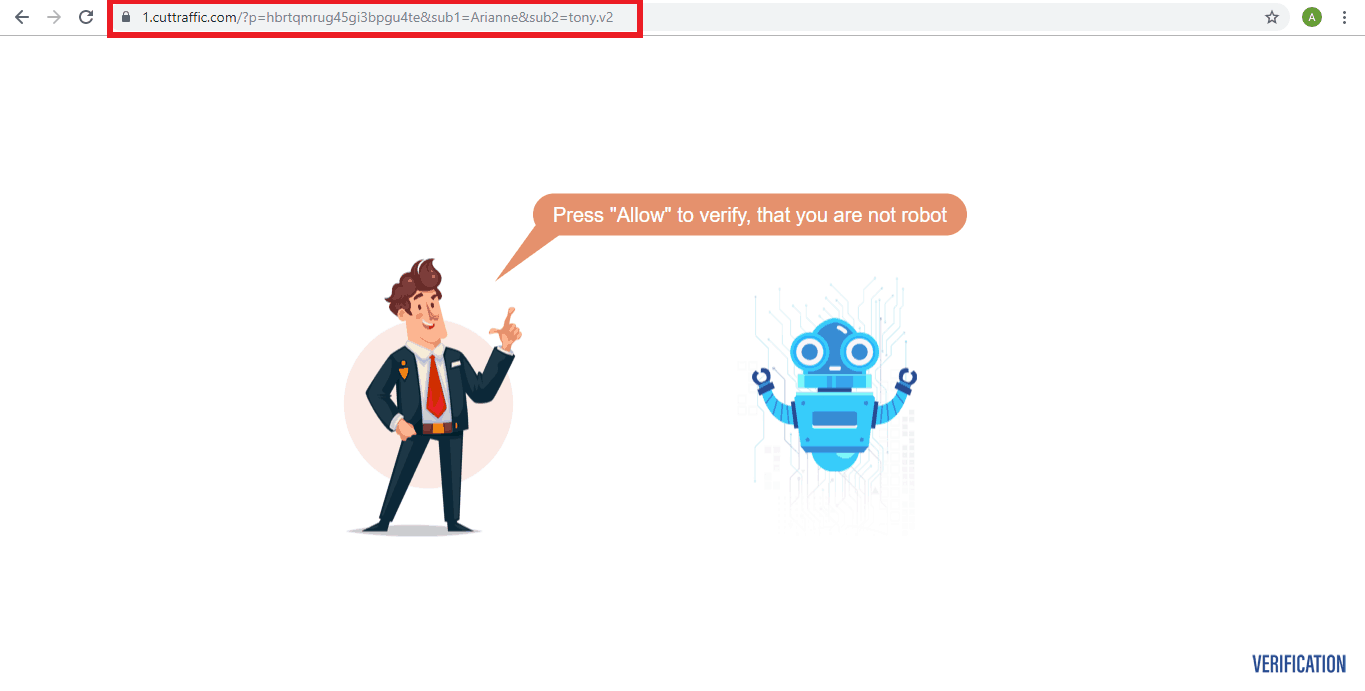
The following image is from one of the hacked sites that came to us. Notice the domain name.
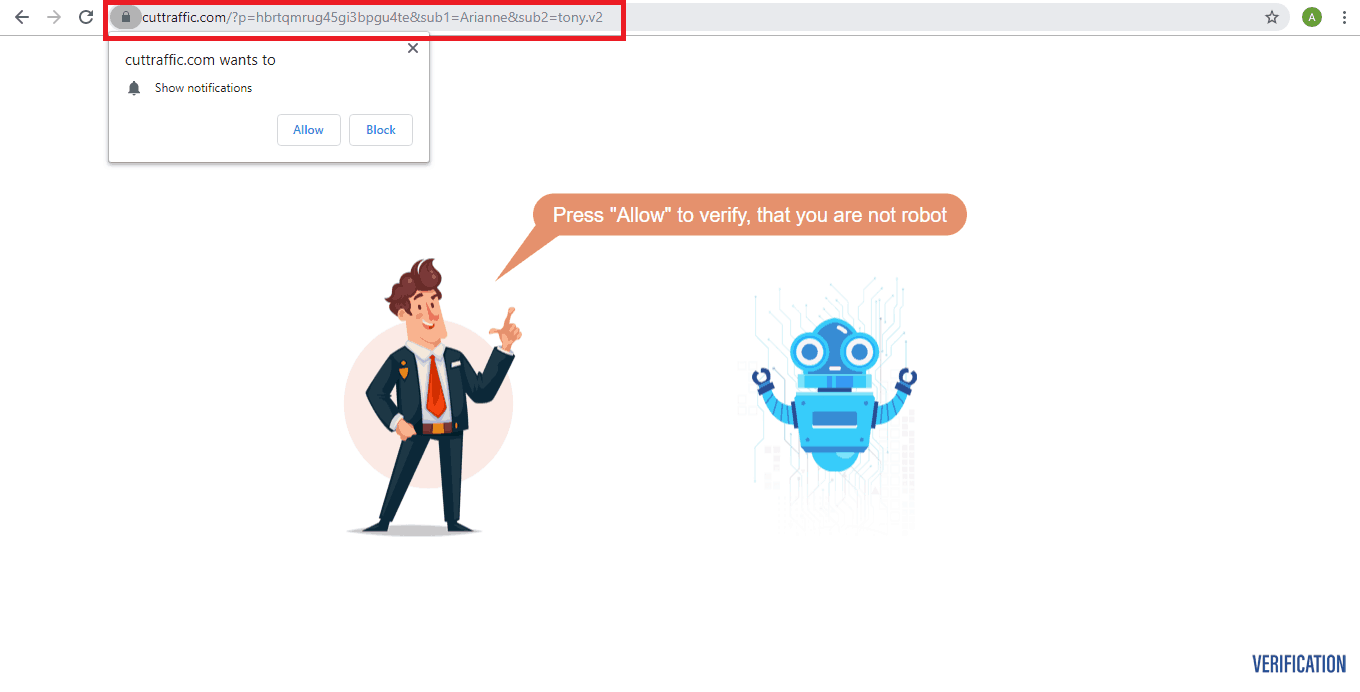
Now, when I try closing the notification bar on this domain, it redirects me to a slight variation of the same domain – 0.cuttraffic[.com].
If I cross the notification bar yet again, it redirects to 1.cuttraffic[.com] and so on.
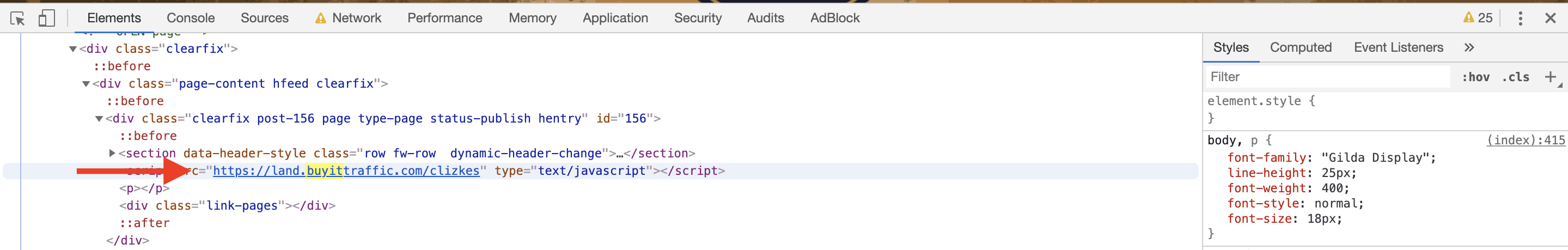
A quick inspection also confirms the injection of the link buyittraffic[.com] in the site.
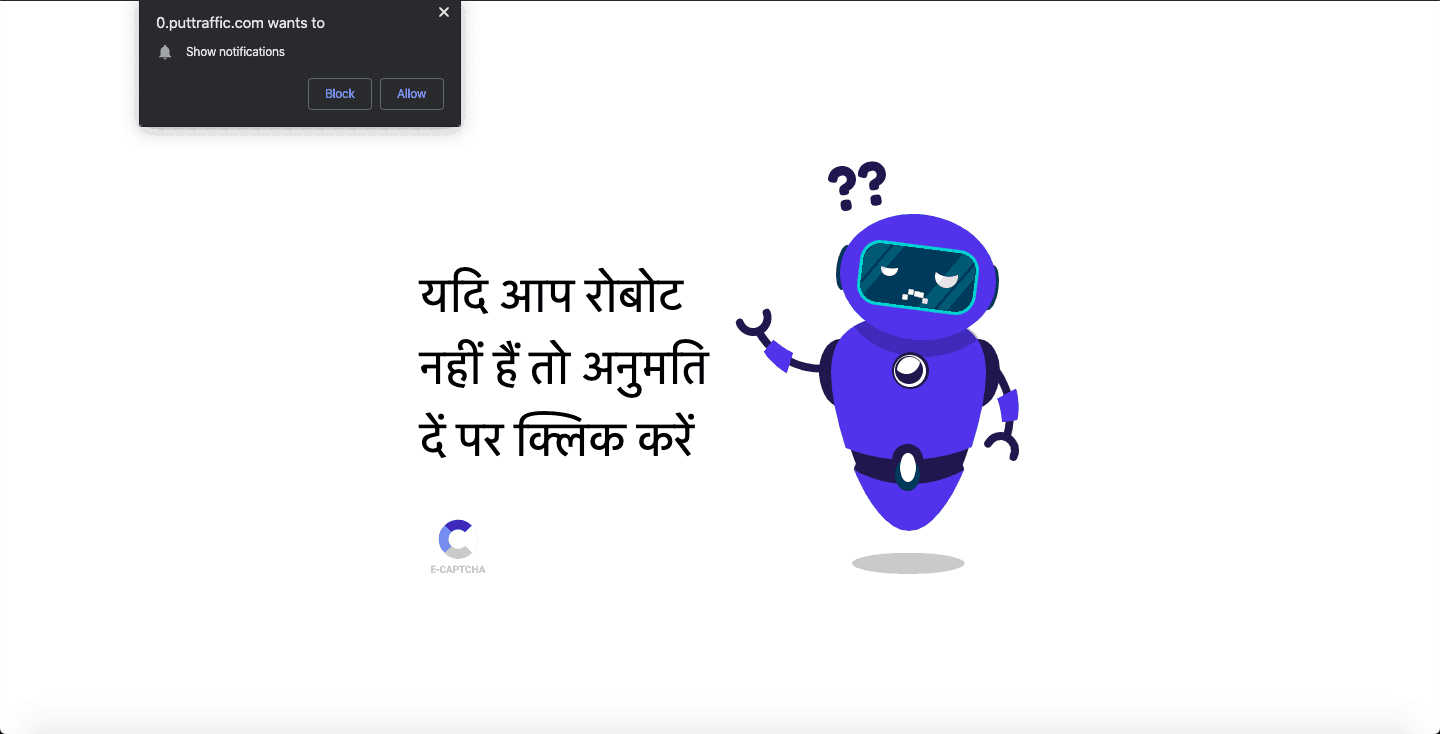
Moving on. We are also seeing the redirection page customize itself according to the regional languages of websites. See picture below:
How hackers infected your site?
Coming to the question of how hackers were able to infect so many websites.
The reason is not that apparent but we suspect that a vulnerable version of adminer could be the reason.
While doing the cleanups, we were able to find adminer.php file in the root folder of all the affected websites. It is, therefore, safe to assume that the hackers use adminer script to access and infect the database.
Combining the above information with the fact that adminer versions prior to 4.6.3 has a serious vulnerability. This vulnerability allows attackers to read local files on the server, such as wp-config.php on WordPress, local.xml on Magento, etc. These files contain the database credentials that could be used to access the database.
Thus, we recommend that you check for adminer.php file on your server and remove it.
To get more insight on WordPress redirection hacks, check out this blog.
What You Can Do About the Hack?
You realize your website is infected, now what?
Two things: You can either get professionals to clean your website. Or you can attempt to clean the website manually on your own.
For the latter option, you can start by checking your server for malicious files. Know that hackers usually exploit multiple vulnerabilities and create malicious files on the server. You will have to hunt for the infected files. Then remove precisely the bits that are triggering the redirection. Few key places to look for malware causing this infection:
- Look for adminer script: Log into your cPanel/FTP of the website and look for a file named ‘adminer.php’. Usually, this file is deployed by hackers to leave a backdoor access to the server. If you find this file, delete it immediately.
- Locate this backdoor: In cases like these we’ve often located a suspicious file at wp-content/force-download.php. Be sure to check if you find force-download.php file under wp-content folder of your WordPress. If you do, delete it.
- Check source: This is one of the most basic checks you should do, check your index page’s code and search for these malicious links. If you find them, please remove them.
- Check for Fake users: Go to the wp_users table of the database and verify no unknown and unauthorized users are there. With an intention to retain access to the attacked sites, hackers create fake admin accounts in them. This we also saw in this attack. Most infected sites that came to us have had malicious users/admin created in them.
Several known fake user IDs used in these attacks are testing@gmail[.com], [email protected][.]com (username: wordpresdadmin)
You can refer to this WordPress malware removal guide for the step-wise manual cleanup process.
Someone Who Clicked on These Malicious Links?
If you are someone who was visiting your favorite website clicked on ‘allow’ on one of these malicious pop-ups, here are a couple of things you can do:
- Review your push notifications on chrome. If you find any website you do not recognize just disable that
- Run an anti-virus on your PC
- Possibly, clear browser cache & history for today
How to Protect Your Site?
Get the ultimate WordPress security checklist with 300+ test parameters
To make sure you do not have to face these scary and costly outcomes, invest in a trusted security solution. Astra security suite offers a web application firewall, malware scanner, immediate malware cleanup, VAPT(Vulnerability Assessment and Penetration Testing), and more. With Astra’s WordPress security solution, you will not have to worry about these stuff again.
Further, the WP Hardening plugin is another multitude solution by Astra. It offers website audit and one-click security fixes for your site. You can now fix more than 12 crucial security areas with this tool.
The Bottom Line
Redirection hacks on WordPress are not new. However, the buyittraffic[.com] redirection malware does surprise us by affecting websites in more than one way. Clearly, there’s a lot going on with this infection.
These hacks are a direct result of vulnerabilities in your site. Poor site maintenance can be one of the causes for these vulnerabilities. Not opting for security audits and vulnerability testing could be another. If you manage to take care of these causes, you can be sure you will not have to browse for another malware removal method.
![WordPress Websites Redirecting to buyittraffic[.com], cuttraffic[.com] & puttraffic[.com]- Resolve Now](https://cdn-blog.getastra.com/2019/11/Redirect-malware.png)
















thank you – had been driving me batty all day
Glad you liked it Bob 🙂
On my sites this guy put their redirect link into siteurl in wp-options table. And put scripts codes in wp-post tables.
For clean this i use sql query:
UPDATE wp_posts SET post_content = replace(post_content, ‘\’, ”)
and change in admin panel site url
Yes, you are correct & it is helpful. But please make sure that you take a proper backup of the database because you are running commands directly on the database. Please make sure to double-check the SQL statement so that an unintended action does not get executed and break the website.
Find and remove adminer.php
It has a serious vulnerability.
Hi Mike,
Hackers are interested in Adminer versions below 4.6.3, which contain a security hole that allows them to read files on servers using the LOAD DATA LOCAL INFILE statement. To exploit this vulnerability, hackers need to find Adminer files—usually left in the site root directory with obvious names such as adminer.php, adminer-4.2.5.php, adminer-4.3.0-mysql-en.php, etc.—and use it to connect to a database on their own remote server, instead of the site’s local database.
Hello , i am facing the same issue for last 4 days but still not found any solution for this .
checked for adminer file , there is no such file. how can i restore my website please help me
Hi Gaurav,
There is no fixed pattern in which hackers are infecting a website. You can follow the blog steps & scan the database for malware infection. Let me know if you have any specific questions.
A similar attack is going around now with following Domains, i hope search engines pick them up here so people can find this. Main Redirecting Entrypoint (Also replaces “site_url” in databases): “js.greenlabelfrancisco.com/touch.js” other connected domains are: “dl.gotosecond2.com/talk.js” I can confirm that i had adminer.php with version 4.2.3 on an infected site. Altough i cannot remember installing it. From the access logs it looks like several exploits and direct script access were tried. They managed to upload and unzip their own plugin called “supersociall.zip” in extracted form “wp-simple-plugin.php” to the uploads folder. Added “Service” account with username “artalfred” to wp_users in… Read more »
Thanks for sharing your insights. The domains that you shared are indeed malicious & the yes adminer.php was common in most infected websites.