One of the worst feelings you can experience as a website owner is finding out that your WordPress website has been hacked. If proactive security measures are not taken, a hacker may be able to launch pharma attacks, phishing pages, Japanese SEO spam, redirection malware, etc. through the WordPress Admin panel hack.
A new type of wp-admin hack has surfaced which adds an unauthorized WordPress admin user and infects the site with a pharma hack. The typical consequences of such a hack include complete website takeover, data theft, database compromise, and SEO hijacking. The WordPress admin is the most crucial part of your website – getting locked out of the admin would mean losing access to your website!
What are the symptoms of the wp-admin hack?
Here are some signs you may see if your WordPress admin panel is hacked:
- You find that admin users you’re not aware of have been added to your WordPress site, or find that a lot of spam WordPress users have been created then definitely it is wp-admin hack situation.
- Google indexes your site with pharma spam pages.
- Your WordPress website becomes very slow.
- New web pages are added to your website with Japanese text (Japanese SEO spam pages).
- Any WordPress Security plugins that you’ve added to your site automatically get disabled.
- You find unknown files like admin.php, adminer.php in the /public_html folder or /public_html/wp-admin folder.
- Your wp-admin page loads a different UI, is blank, or a file Manager named ‘B Ge Team File Manager’ is uploaded and instead of the login page, you see a black/grey screen with a list of files on the server.
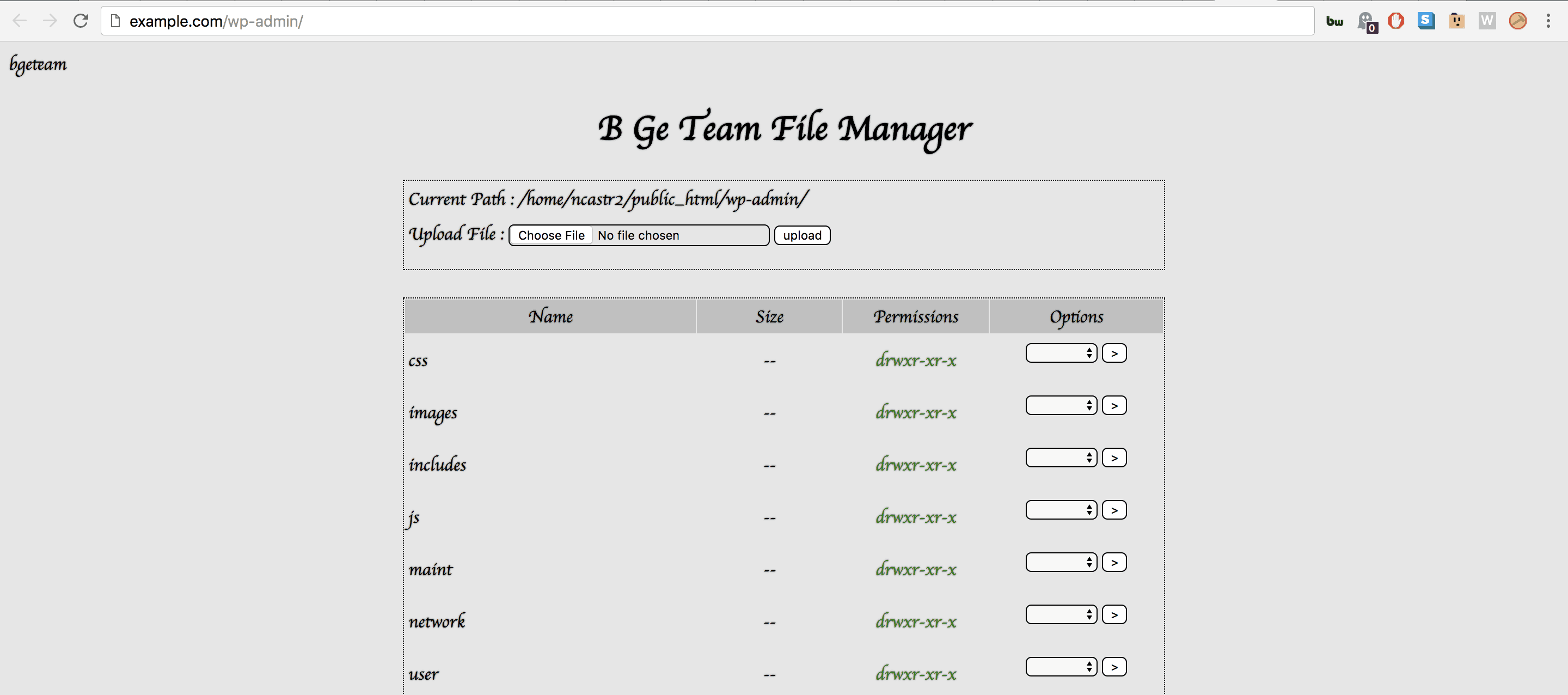
- You get a PHP 500 internal server error on visiting wp-admin or after logging in.
- The ‘anyone can register’ option has been enabled from the Settings » General page section in the WordPress admin area.
- You are unable to add/delete plugins.
- Your Hosting Provider suspends your account.
- A web shell is uploaded to your site.
- You find suspicious-looking base64 encoded code in the theme/core files.
- Your site’s core WordPress files have been modified.
Related Blog – Comprehensive Guide to Fix Hacked WordPress Site
How to remove the wp-admin malware code from my website?
1. Check the index.php file: A good first step is to check your site’s index.php or wp-admin/index.php to see if they have been modified. Usually, if your site is affected by the wp-admin hack, the following line of code is added to the top of the index.php file:
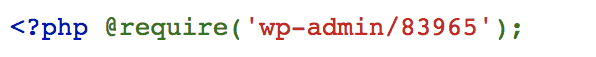
The file being ‘required’/’included’ here contains malicious code, which is executed each time WordPress is run. Such code can generate fake pharma pages, Japanese SEO spam pages, and other malware infections.
You can simply remove the @require code from the file after comparing it with the contents of the core WP files from their GitHub repository.
2. Look for files created by malware: You can also check if there are any new files in the root of the server or /wp-admin folder that was not created by you. Some example files that you may find are:
- Marvins.php
- db_.php
- 8c18ee
- 83965
- admin.php
- buddy.zip
- dm.php
If you find any of the above suspicious files, take a backup of your site and delete them. A standard WordPress installation generally has the following files in the root of the server – any files other than these that you haven’t created may be malware.
3. Look out for SEO Spam: You can perform a Google search to see the list of pages indexed for your domain, like so:
site: <enter your domain name>
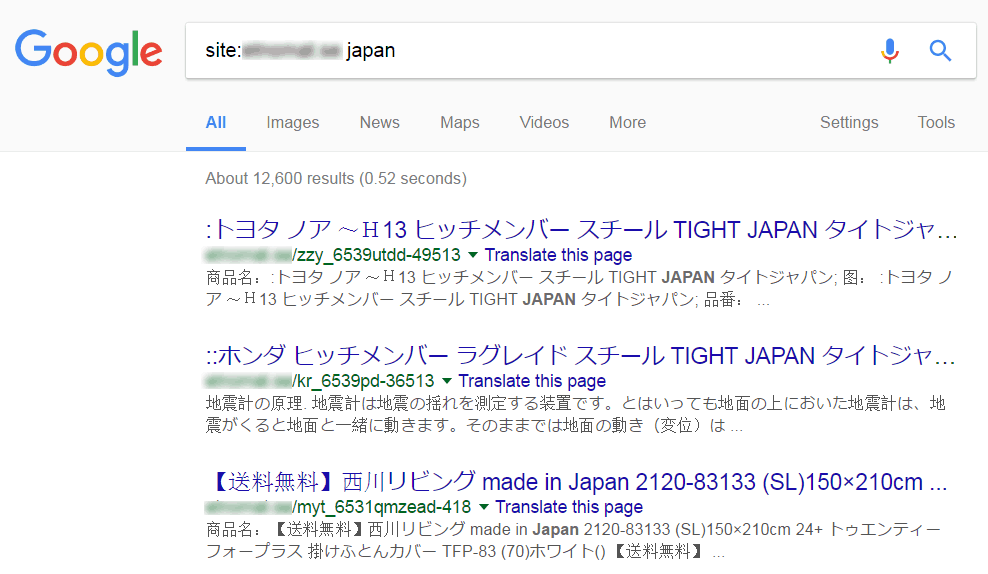
If the search results for your website are similar to the screenshot, refer to our Japanese SEO spam removal guide.
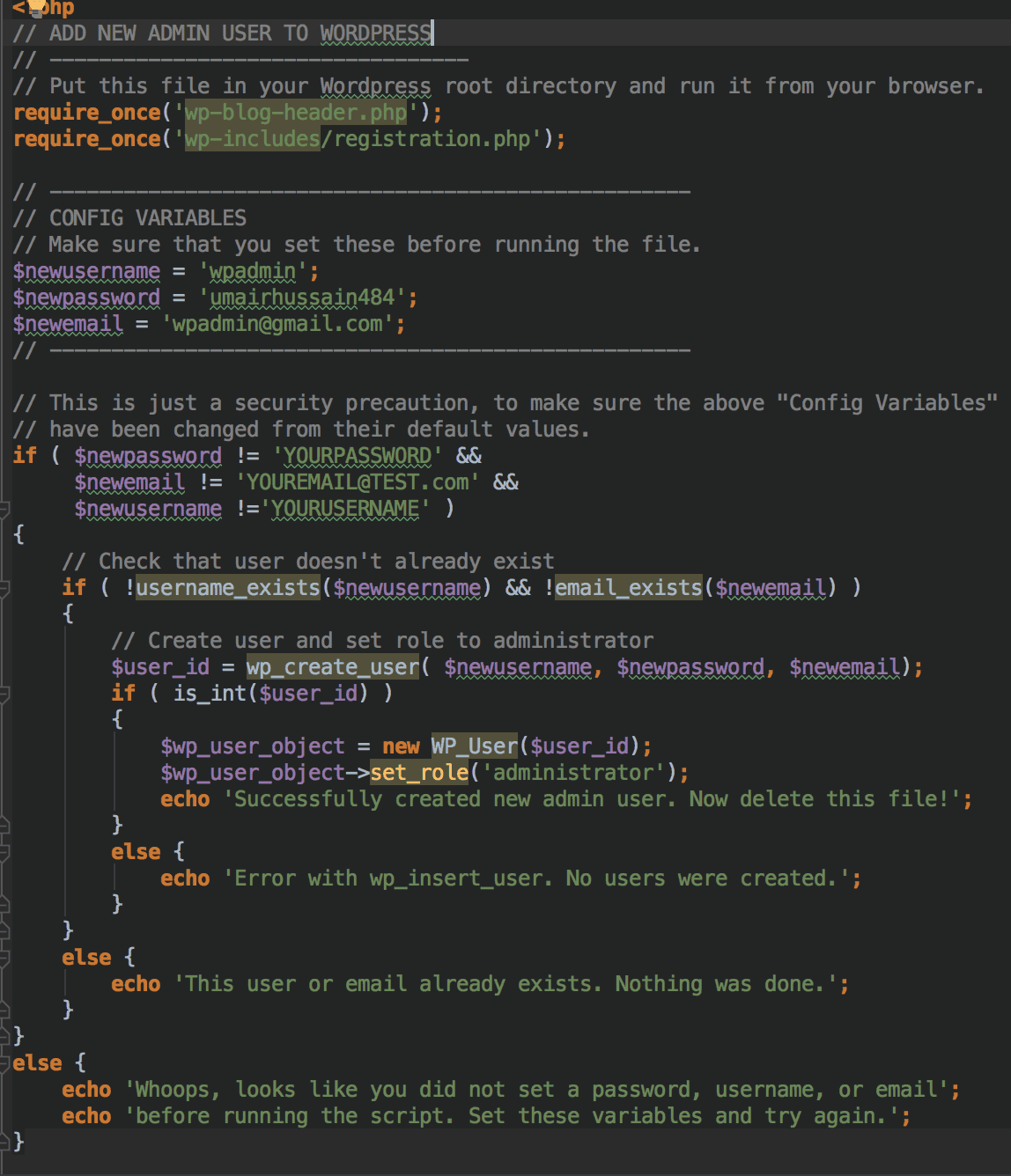
4. Track unknown WordPress admins: If you find multiple admins, delete the unknown WordPress accounts from the Users page, and track down the backdoor script which adds admin users to your WordPress website.
Visit the Users page (wp-admin/users.php?role=administrator) in your WordPress website to see if any new administrator users have been added, and delete the accounts you do not recognize.
You can now look for the WordPress backdoor script, which, when executed, allows the hacker to insert a new WordPress user with the Administrator role. Further, this backdoor can be used to regain access to the WordPress installation at any time the hacker wants – so it’s a good idea to remove this code to prevent further harm to your website.
5. Check uploads directory: You should delete any PHP files that are found in the ‘uploads‘ directory.
Due to security vulnerabilities in WordPress plugins or in the core itself, a hacker may be able to upload malicious PHP files to the web server. If you find any executable files with the .php, .php3, .php4, .php5, .py, .asp, .aspx file extension anywhere in the /uploads directory of your website, delete them.
You can also prevent PHP from running in this directory by placing an .htaccess at the root of /uploads using the following code:
# Kill PHP Execution
<Files ~ "\.ph(?:p[345]?|t|tml)$">
deny from all
</Files>
6. Malware scan is a must: You should consider running a malware scan on all files on your server.
In your web-hosting dashboard or cPanel, you should have an option called ‘Virus Scanner’. You can run it to identify any malicious files which may be residing on the server, and verify and delete any files that it flags. You can also go for a complete malware scan of your website, such as the one offered by Astra Security.
Steps to prevent a re-infection & identify the cause of the WP-admin hack
1. Consider installing a web application firewall which would detect security threats and block them.
While WordPress is built with security in mind, its plugins are often subjected to all kinds of security threats – so it’s important to proactively secure your WordPress website from the hundreds of new threats lurking out there. Security suites such as Astra ensure that you’re safe from such attacks.
2. Regularly update the WordPress core, plugins and themes.
Hackers and cyber-criminals often build tools to exploit known vulnerabilities in plugins and themes. So, the WordPress core, plugins, and themes receive updates to prevent exploitation. The easiest way to prevent getting hacked is to keep your software up-to-date.
3. Monitor the administrator accounts being created in your WordPress site.
In a typical store compromise, hackers create admin users for themselves to be able to access the WordPress admin area or back-end at a later stage. Be proactive with this step and follow the Principle of Least Privilege.
4. Take regular backups of your WordPress files & Database.
Configure automatic backups which archive all the files on the server and also the database. A good idea is to store your backups on an external server – so that, in the event of a hack, the backups can still be retrieved.
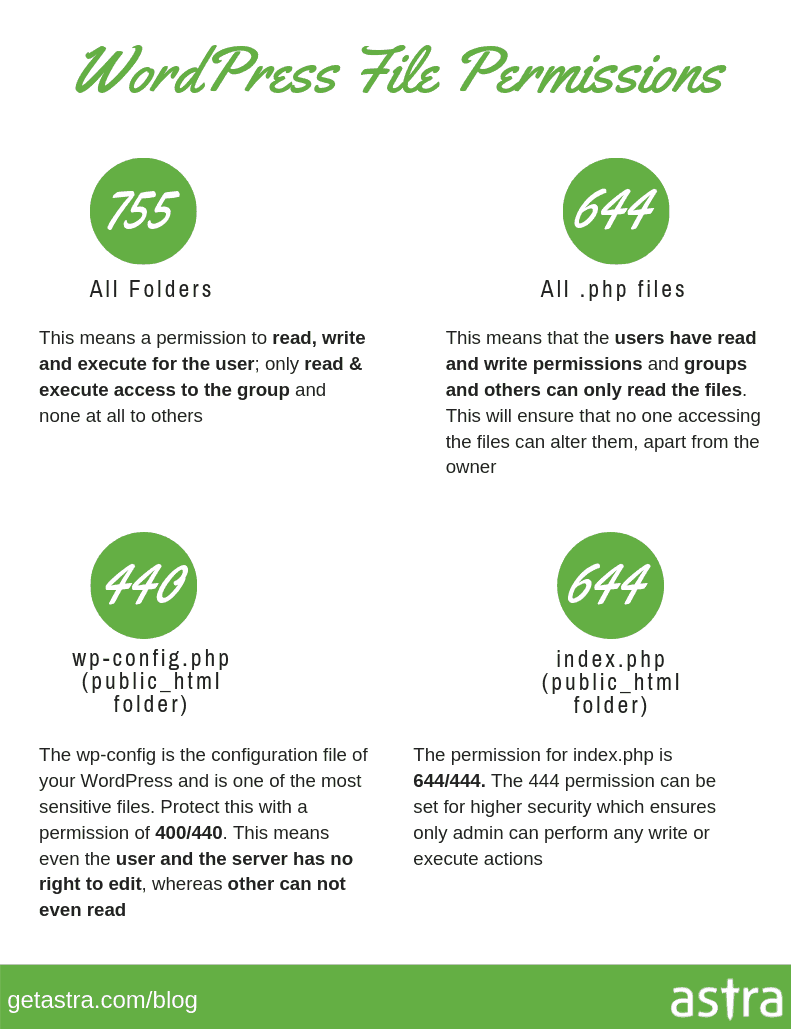
5. Update file & folder permissions on the server.
File permissions are very important, as they specify who can read, write, and execute it. Here are the file permissions as per the general guidelines recommended by the WordPress Codex:
- Folders – 755
- Files – 644
However, if you wish, you can change the file permissions recursively via command line:
For Directories:
find /path/to/your/wordpress/install/ -type d -exec chmod 755 {} \;For Files:
find /path/to/your/wordpress/install/ -type f -exec chmod 644 {} \;6. Disable file editing on your website.
It’s a good idea to disable file editing within the WordPress dashboard. Append the following two lines to the end of your wp-config.php file to disable file editing via the WordPress dashboard:
## Disable Editing in Dashboard
define('DISALLOW_FILE_EDIT', true);Get the ultimate WordPress security checklist with 300+ test parameters
Since this hack is so prevalent, we’ve made a detailed step-by-step video on how to secure your WordPress site that you might find helpful. You can also download this article as an infographic here.
About Astra Security Suite
Astra is the essential web security suite that fights hackers, internet threats & bots for you. We provide proactive security for your websites running popular CMSs like WordPress, OpenCart, Magento, etc.

















Great article!
Thanks, Jose
I’m impressed, I have to say. Really not often do I encounter a blog that’s both educative and entertaining, and let me let you know, you’ve gotten hit the nail on the head. Your concept is outstanding; the problem is something that not sufficient persons are speaking intelligently about.
Than you so much Dobkin for your kind words. I will pass it to the team
Thankyou for your great article. My site got hacked like what you described in this article. In my case, I found them in wp-config.php file.
You’re welcome, Franklin
You can check our comprehensive WordPress Hack & Malware Removal Guide here – https://www.getastra.com/blog/911/wordpress-site-hacked-malware-backdoor/
you’re in reality a excellent webmaster. The site loading speed is amazing.
It sort of feels that you are doing any unique trick.
In addition, The contents are masterwork. you have done a wonderful task on the topic
Thanks 🙂
That’s really great blog post on WordPress Admin hack. My Admin panel is defaced & a shell is uploaded.
Can you please suggest your WordPress Hack removal guide that I can follow? I have cPanel access to my site.
Thanks in advance.
Thanks, Mike. You can check our comprehensive WordPress Hack & Malware Removal Guide here – https://www.getastra.com/blog/911/wordpress-site-hacked-malware-backdoor/
Also, once your site is clean you can follow our WordPress Security Guide to Harden your site’s security – https://www.getastra.com/blog/cms/wordpress-security/wordpress-security-guide/