Are your website’s search results showing Japanese text? If so, you may have been the target of the Japanese SEO Spam or Japanese Keyword Hack. Many website owners have contacted us worried about this type of attack. To find out what it is and how to fix it, read on!
What is a Japanese Keyword Hack or Japanese SEO Spam?
In a Japanese keyword hack, auto generated Japanese text starts to appear on your site. This particular black hat SEO technique hijacks Google search results by displaying Japanese words in the title and description of the infected pages. It happens when different web pages are shown to search engines and normal visitors. This attack is also known as the “Japanese Keyword Hack“, “Japanese SEO Spam“, “known spam detected: spam-seo?japanese.0” or the “Japanese Symbol Spam”.
When using a Content Management System (CMS) like OpenCart, Magento, Drupal or WordPress you’ll find auto-generated Japanese SEO Spam pages. These pages contain affiliate links to stores selling fake brand merchandise. These Japanese products are ‘spamvetised’ to increase revenue and benefit from the outbound links from your site.
Reasons for the Japanese Keyword Hack
There could be many reasons for the appearance of Japanese hack on your site. The most common of them are:
Outdated CMS version
If you look at these shocking stats, you will know that an outdated CMS is the number one reason why your website might have been hacked. Hackers often target vulnerabilities or loopholes present in software. Even though the CMS developers release security patches regularly, web owners often ignore them and hold off on updates. These unpatched security loopholes become a reason for the Japanese Keyword Hack later.
Do Google or Bing show weird search results for your website? Find out in 15 seconds.
Third-party Plugins
Not all plugins are secure, and surely not all are maintained & updated regularly. So, you may want to check the plugins before installing them. It is also a good idea to limit the usage of third-party plugins. If you are compelled to use one, make sure you check its latest update, reviews, and support. A plugin with bugs is another target for a Japanese Keyword Hack.
Enabled Directory browsing
Enabled Directory browsing allows a hacker to fetch the details of your directory by a simple online search. The results may be hazardous for your website. They can, then, use this data to execute the Japanese keyword hack. So, always make sure to disable your directory browsing.
Improper File Permissions
File permissions are very important, as they specify who can read, write, and execute it. Having improper file permissions is another security hole. Generally, setting permissions of 644 for files and 755 for directories is considered best – as recommended by the WordPress Codex. Also, the recommended permission for sensitive files like the config.php file and contents folder, is 400/440.
Japanese Keyword Hack – Finding SEO Spam Results
1. Japanese SEO Spam: Identify the infected pages using Google Search
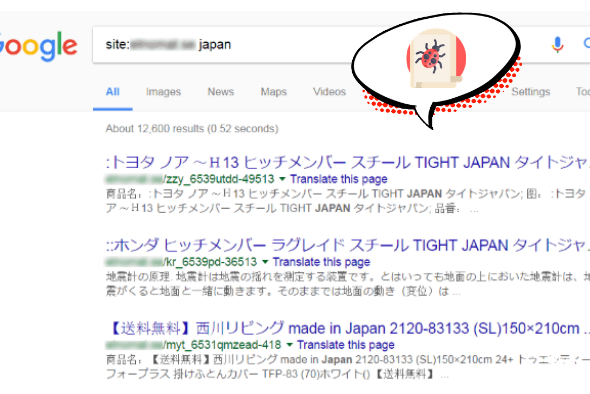
You can uncover such pages by searching for site:[your site root URL] japan in the Google search.
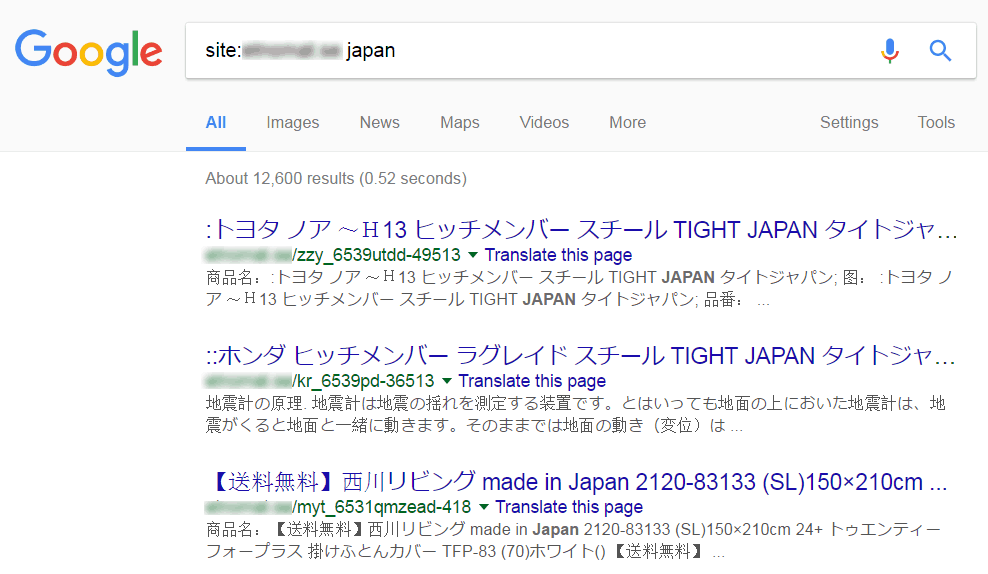
Next, look through some of the search results to see if you discover any suspicious-looking URLs. These are the pages indexed by Google containing the word ‘Japan’. If you notice pages with the Japanese characters in the title or description, it is likely your website is infected.
Recently, our engineers came across a website where the entire front page loaded with Japanese! This is a definite sign that you have been a target of this attack – it is a great idea to seek professional help if you face this issue:
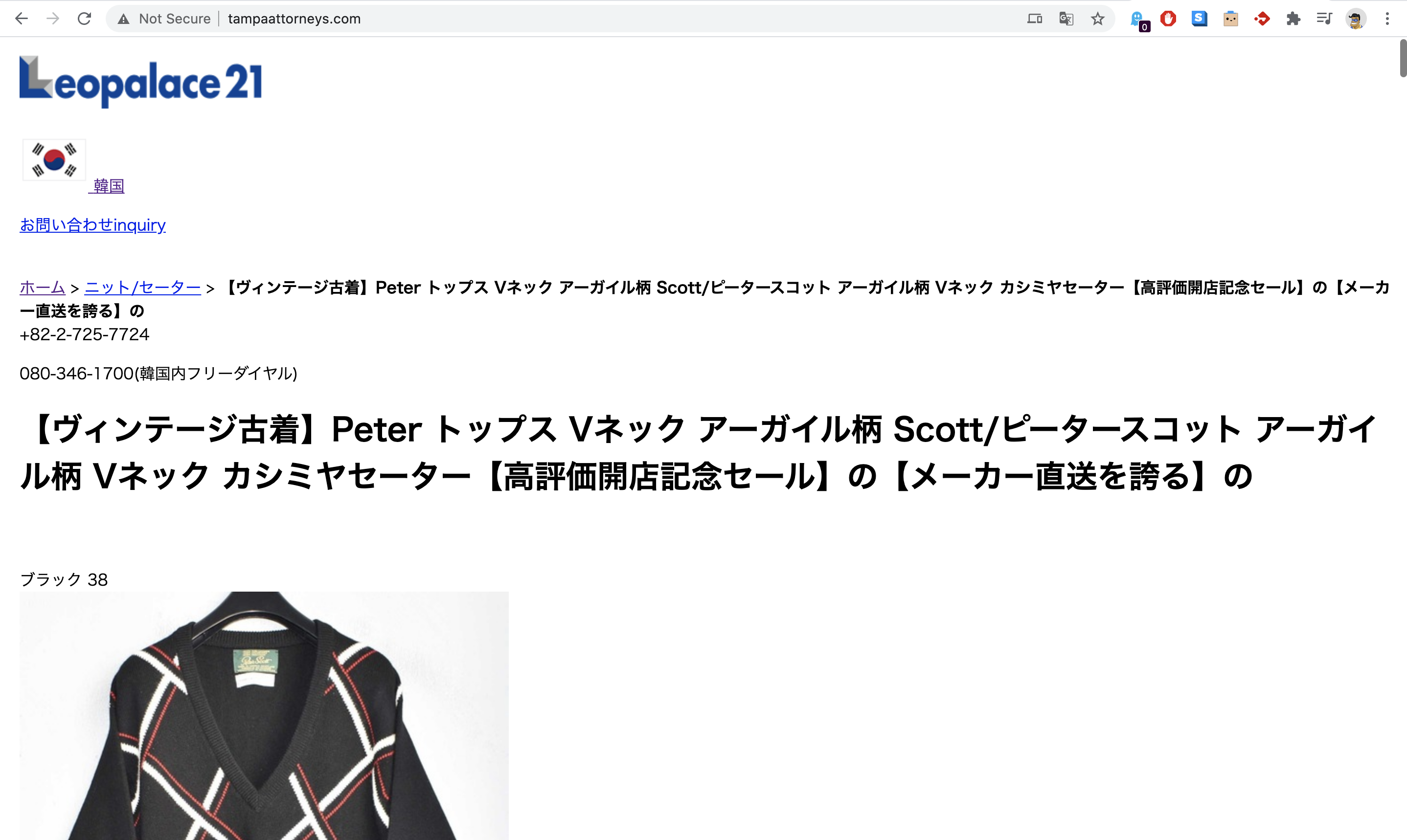
2. Verify-in Google Search Console
In your Google Search Console (earlier called Google Webmaster Tools), navigate to the Security Issues Tool in the left sidebar.
3. Japanese SEO Spam: Fetch as Google to check for ‘Cloaking’
When you visit any of these hacked pages, you might see a ‘404 page not found’ suggesting that the web page doesn’t exist. Be careful, the hacker may be using a technique called cloaking. Check for cloaking by using the “Fetch as Google” tool in your Google Search Console.
How To Fix Japanese Keyword Hack
1. Backup your site before cleaning
Before starting with the WordPress malware cleanup process, it’s good practice to take a backup of your current site. In the event of anything going wrong, you can restore this version. Make sure to take the backup file in a compressed format like a .zip file.
2. Remove any newly created user accounts in the Search Console
Check “Users and Property Owners” tab – this is where you can find out if hackers have admin access to your site. If you don’t recognize any user or see suspicious activity, immediately revoke their access. Hackers add spammy Gmail accounts as admins so that they can change your site’s settings like sitemaps and geo-targeting.
3. Run a Malware Scan
Scan your web server for malware and malicious files. You can use the ‘Virus Scanner’ tool in the cPanel provided by your web host, or get expert malware cleanup with the Astra Pro Plan.
4. Check your .htaccess file
Hackers often use the .htaccess file to redirect users & search engines to malicious pages. Verify the contents of the .htaccess file from a last known clean version of your backups. If you find any suspicious code, comment it out by putting the ‘#’ character in front of the rule.
5. Copy your WordPress configuration database connection strings
Your wp-config file is your website’s configuration file and clearly most wanted by hackers. In case of a hack, the attacker can insert malicious content in this file too. Make sure to thoroughly scan this file and remove the unfamiliar contents to remove Japanese SEO spam from your website.
However, editing wp-config may create a mess if you unknowingly delete something vital. Thus, in spite of editing it, you can take a copy of your WordPress database connection strings and make a totally new file out of this. Then, delete the former infected wp-config file. A word of caution – wrongly editing the wp-config file can take your website down, so be very careful!
6. Check the recently modified files
You can find any recently modified files by following these steps:
– Log in to your web server via SSH.
– Execute the following command to find the most modified filesfind /path-of-www -type f -printf '%TY-%Tm-%Td %TT %p\n' | sort -r
If you are an Astra customer, you would have received an email telling you about any malicious file changes.
7. Replace the core files, plugin files & theme files
You can replace the infected core files with the original versions of the same from WordPress.org. After downloading the fresh and updated versions of these files & directories, you can delete the older ones.
8. Check your uploads directory
Check your wp-content/uploads directory for files with blacklisted extensions, like .php, .js and .ico. If you find such files, check the content for characters like base64_decode, rot13, eval, strrev, gzinflate, etc. Eliminate files all such files as they are can be malicious.
9. Check your sitemap
A hacker may have modified or added a new sitemap to index the Japanese SEO Spam pages quickly. If you notice any suspicious links in the sitemap, quickly update your CMS core files from a last known clean backup.
10. Prevent future attacks with a Website Firewall
Like the Japanese Keyword hack, another similar SEO spam attack in WordPress is the pharma attack, which shows spam pharmaceutical products like Viagra, Cialis, etc on your website’s SEO titles or URLs. A great option to prevent such infections is to use a Website Firewall. Our Security Suite helps to automatically secure your site and virtually patch software by preventing malicious requests from reaching your website.
The Effects of Japanese Keyword Hack on Your Website’s SEO & Traffic?
Cyber attacks are horrible – but their after-effects are more so. We conducted a little study on one of our customers’ websites to see the effect the Japanese keyword hack had on his website.
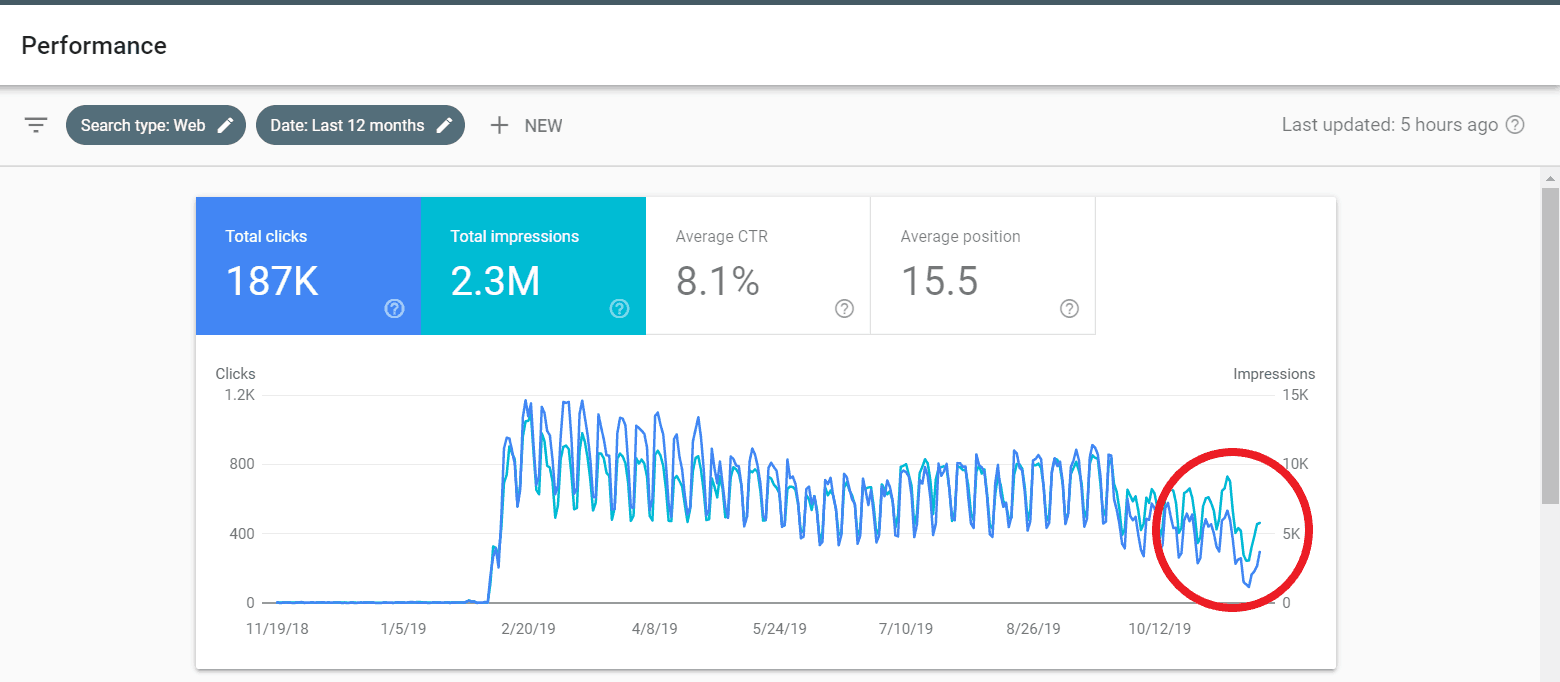
We monitored the website for days after the hack and this is what we saw:
The website traffic shows a steep drop towards the end when it was hacked last November. The data in the above picture spans a year and traffic never saw a dip as it did in November.
Related Guide – WordPress Hack Removal
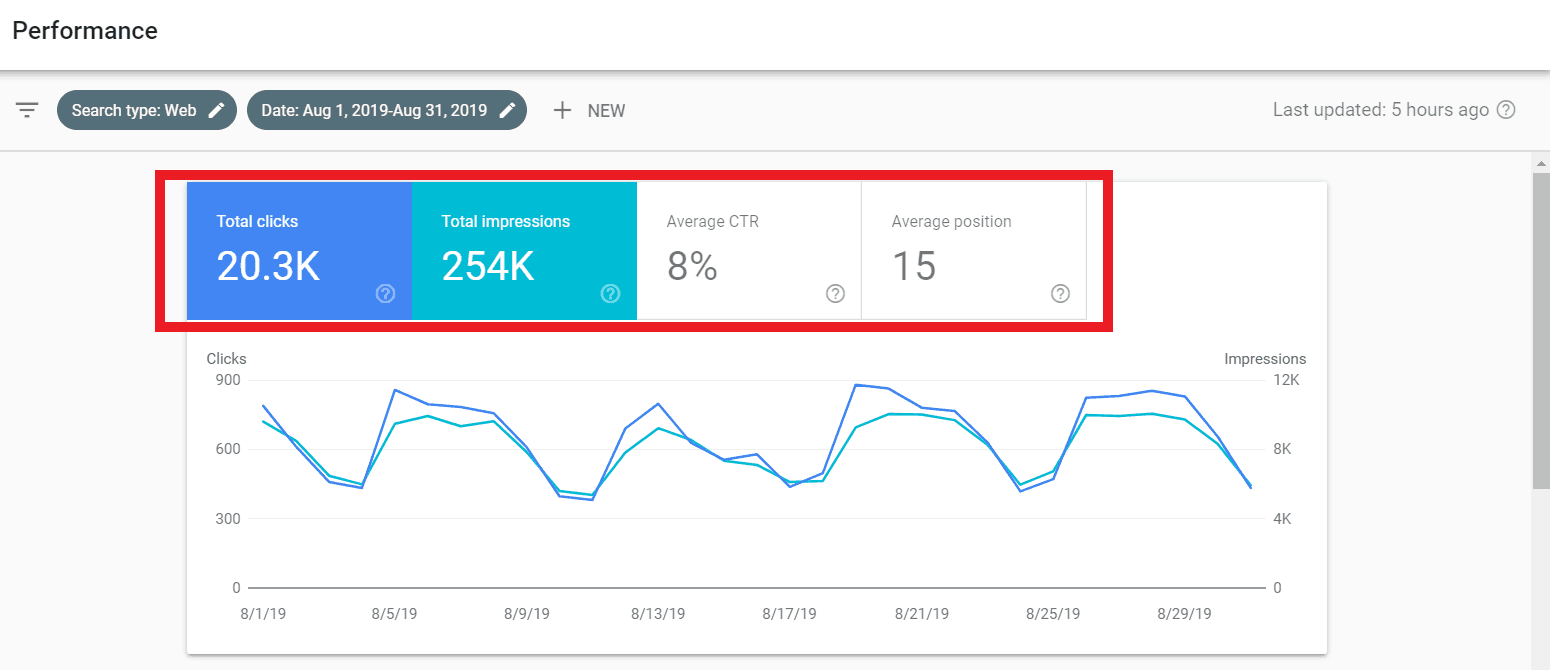
Then, we went on to narrow our search to the hacked month’s data which we compared to that of August – which we chose since no major Google update was pushed in that month.
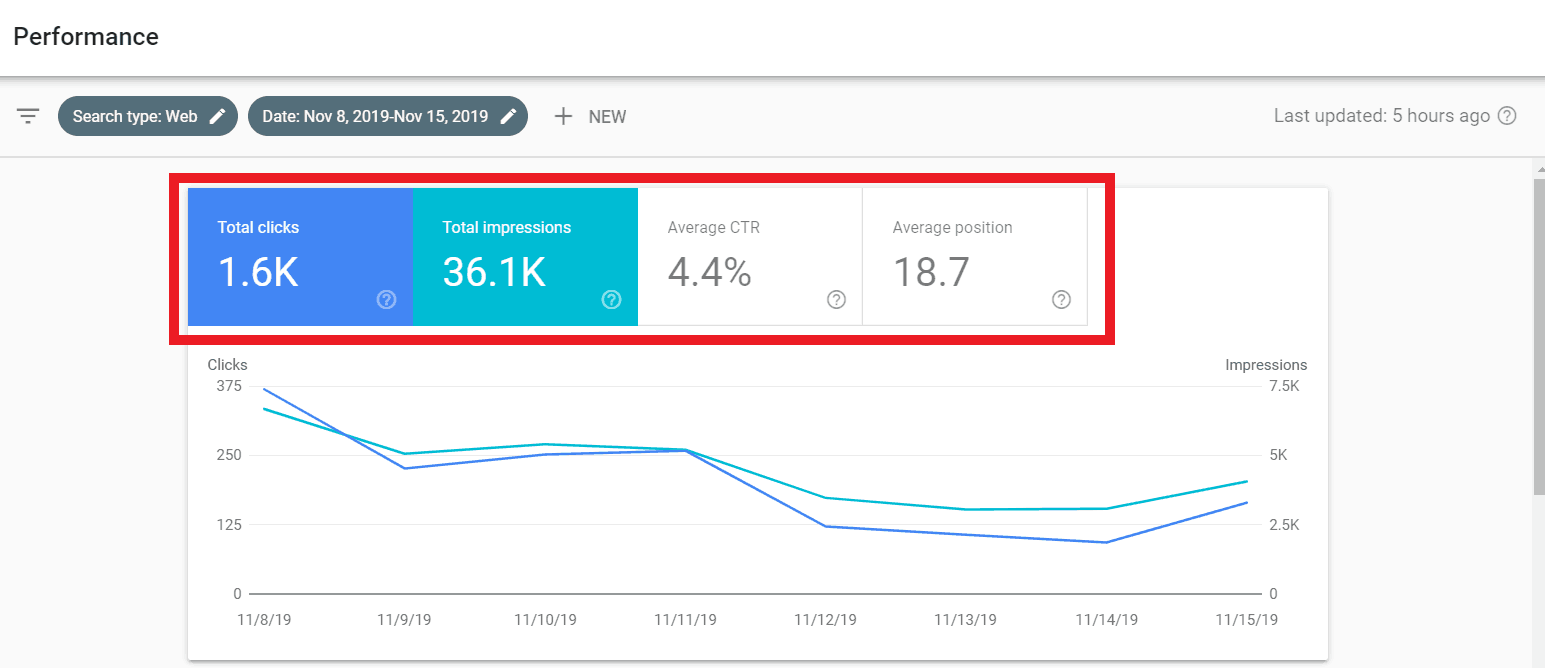
The following picture shows the website’s data from Aug 1, 2019, to Aug 31, 2019. As you can see, total clicks = 20.3k, impressions= 254k, average CTR= 8% and average position=15 in August. Also, notice the graph. The crests and troughs more or less show the same behavior throughout the month.
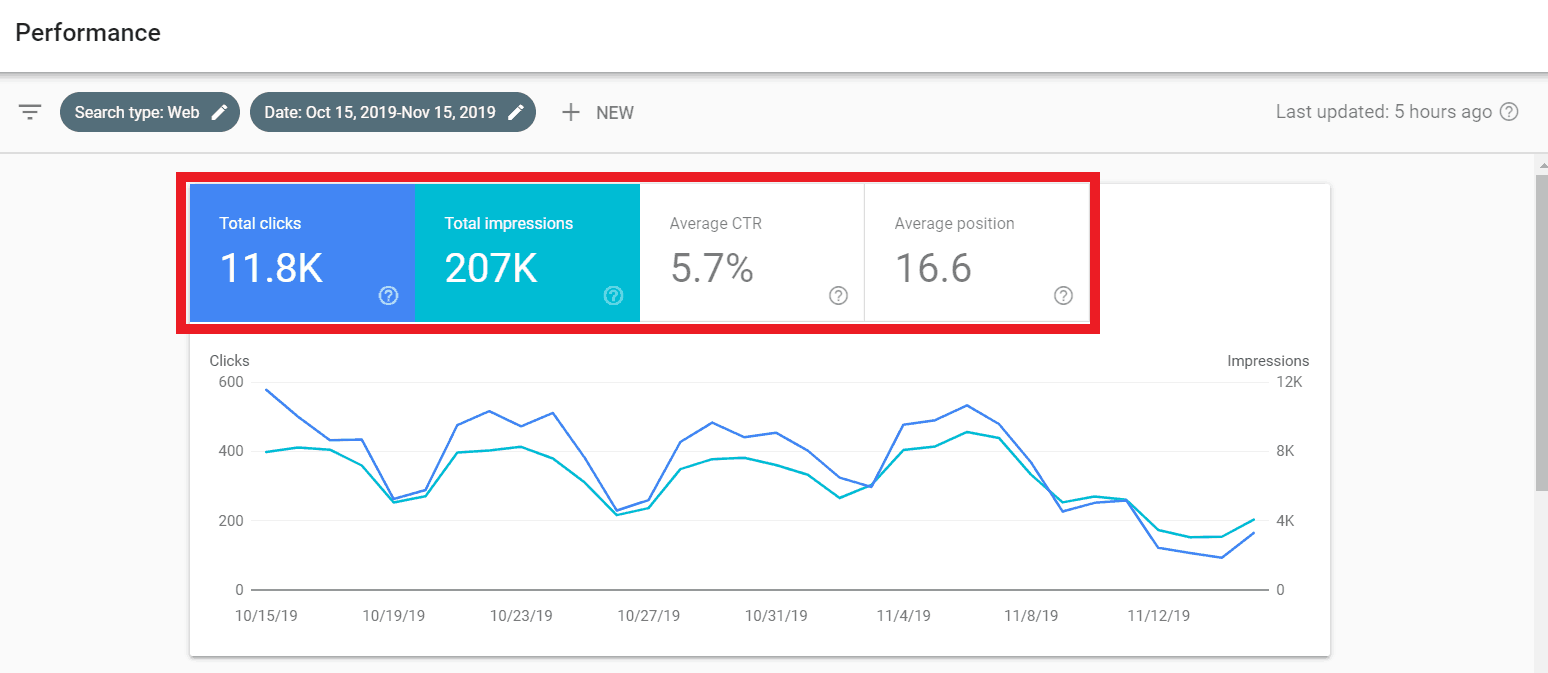
After the website was hacked in November, this is what the data transformed to:
Clearly, everything plummets. Total clicks to 11.8k, impressions to 207k, average CTR to 5.7%, average position to 16.6.
When we further narrowed our research to track only the days the site was hacked, this is what we got:
The CTR shows almost a 50% dip, whereas the average position has also dropped by 2 places.
The Japanese keyword hack has a lasting effect on websites. Even if you’re prompt in curing your website of the hack, its SEO takes a hit. As a website owner, I don’t need to tell you that the effort that goes into rebuilding a website’s SEO and reputation is huge.
If you do not wish to face such a fate, don’t depend on fate! Invest and indulge.
Invest in proactive website protection while everything seems hunky-dory. Indulge in a standard security routine for your website. Firewalls and security plugins are tested solutions that go a long way in keeping your websites protected.
As the Japanese SEO Spam (Japanese Keyword Hack) is so prevalent, we’ve made a short video on it that you might find helpful:
About Astra Security Suite
Astra is the essential web security suite that fights hackers, internet threats & bots for you. We provide proactive security for your websites running popular CMSs like WordPress, OpenCart, Magento etc.

















[…] commonly find vulnerabilities in custom code written on top of your OpenCart (vQmod/OCMOD), Magento (local extensions) or WordPress (Plugins & Child Themes) […]
[…] are some known malwares which create links of pharmacy products on your website, or the famous Japanese spam trying to capitalize on your SEO efforts. Entering the following code in google often helps […]
[…] measures are not taken – a hacker may be able to launch pharma attacks, phishing pages, Japanese SEO spam pages or even plan a wp-admin […]
thanks
You’re welcome, Mohamed Murshid 🙂
[…] content appears on Laravel or Codeigniter site due to Japanese Keyword Hack or Pharma Hack […]
Thanks for a great list!
Thanks for your kind words, Jessica
[…] viagra and cialis. This SEO spam is known as Black Hat SEO. Another famous example of SEO spam is Japanese SEO Spam. In this spam, the spammers hijacked google search results and displayed Japanese words in the […]
How much time Google will take to update the site’s search page and remove all those Japanese URL’s from Search Console?
How much time it will take to look as it was in Google Search?
The complete removal of Japanese URLs from Google search takes a few weeks. Actually, Google shows around 300-500 indexed spam URLs at a time, so you need to submit all those spam URLs from removal via search console. Also, you need to ensure that website is malware so that no new spam URLs get linked
A few weeks, thats insane! kinda weird it already showsup after 2-3 weeks when hijacked.
How Japanese Keyword Hack affects our SEO and Google ranking?
Japanese SEO Spam affects your website SEO & ranking adversely as Google thinks that your site is in Japanese not in the targeted language. Also, most of the indexed URLs give 404 putting a question on the site trust & authority.
You can check the mentioned case study in our blog of a site who is infected with Japanese Keyword Hack.
How much time it will take to remove all the Japanese keyword hack? Is there any fastest way for the same?
To fix Japanese Keyword hack you need to remove all the malware first that is responsible for linking of spam domains. Then next step will be to submit spam link for removal via Google search console. There are few extension like SEO quake that will help you to generate the list of indexed URLs.
For the faster removal, ensure all malware is removed & you submit spam links periodically to Google for removal, as Google show around 500 URLs at a time.
How to identify the Japanese keywords hack? I haven’t received any warning in the Google search console.
Most of the time you will not see any warning in the security tab in Search Console. To identify the Japanese Keyword Hack, check for newly submitted sitemaps & search in Google ‘site:yourwebsiteURL’
If you see any newly submitted sitemap (without your consent) & spam results in Google, it means your site is infected.
Also, a good technique is to check your site how Google or Search Engine bot sees it. You can also check the Japanese keyword hack using our scanner – https://www.getastra.com/japanese-keyword-hack-scanner
Can Anyone Tell me how to remove the Japanese word while searching the website name in google search?Its Little bit urgent, Please explain step by step.
Hi Jai,
I saw that your site is not only infected with Japanese SEO Spam but also redirecting to spam Japanese site. You can follow our Japanese keyword hack removal guide & WordPress redirection hack removal guide to fix the issue – https://www.getastra.com/blog/911/wordpress-redirect-hack/
In case you need our engineers help in fixing the issue we can surely help you to fix the site & ensure complete security for a year.
can anyone help me to sole,How to remove the japanese words, while searching the website in the Google search engine.
Hello, so how much time does it take normally for Google to get rid of spam URLs once submitted?
Hi Danny! It takes around 24-48 hrs for Google to get rid of spam URLs once we submit them. Also, it is recommended to submit the sitemap of your website too.
Hi, what’s the most common file to check when a Japanese spam hack hits a wordpress website?
Hey Grady! You can check the
index.phpin the root of your site, and also the functions.php of your theme. In some cases we’ve also see that.icofiles are created on your server which contain malicious PHP code for the Japanese Keyword hack.Hi Grady! The WordPress Spam malware creates junk pages on your website that get redirected to other malicious web-pages. Often this goes unnoticed by the naked eye. You can find the files that get affected the most in this article: https://www.getastra.com/blog/911/remove-wordpress-spam-search-results/
I have a WordPress site being redirected to strange websites. I am not techy but is there any way I can get rid of this on my own?
Hi Taylah! Sorry to hear that your WordPress site is getting redirected. WordPress malware redirect hack is a common form of attack where the visitors to the infected website are automatically redirected to phishing sites or malicious websites. You can follow this guide: https://www.getastra.com/blog/911/wordpress-redirect-hack/. If professional help is required, we can solve this for you in 4 hrs 🙂 You can get started here: https://www.getastra.com/pricing
what is wp vcd malware? How to protect against it? we own a site that is based on WordPress and I don’t want it to get hacked.
Hi there! The WP VCD malware can get a foothold in your site by leveraging loopholes in outdated plugins and themes. In most WP-VCD cases, the web owners infect themselves by installing a free/nulled plugin & themes from unauthorized sources, while in others it occurs as a result of contamination by infected sites. For more info read this article: https://www.getastra.com/blog/911/wp-vcd-malware-removal/
Thanks a lot Ananda Krishna for this elaboration! It helped us a lot actually! Recently our website got compromised, and didn’t know what was happened, after going through this guide, came to know that our site was compromised with Japanese SEO malware technique! This step by step guide helped us to recover, now it’s working good! Thanks again!