Data breaches are costly, both in terms of the monetary losses associated with the theft of customer or employee data and the damage to a company’s reputation. To prevent data breaches, security testing plays an essential role, but what does comprehensive security testing involve? Let’s understand.
Security testing is a complex process for finding out potential security vulnerabilities in a software system that malicious users or hackers might exploit. It’s essential that security testing is performed thoroughly with the help of application security testing tools to ensure that all the security loopholes are identified and fixed before they are exploited. Many organizations use interactive application security testing (IAST) tools to get rid of security vulnerabilities.
SAST, DAST, and IAST are the testing methods that organizations use to carry out effective security testing on their applications. There are tools available in the market for each type of testing process. This article will discuss the different types of security testing tools and why Interaction Application Security Testing (IAST) is an important method that helps organizations achieve satisfactory test results.
What are the types of Security Testing?
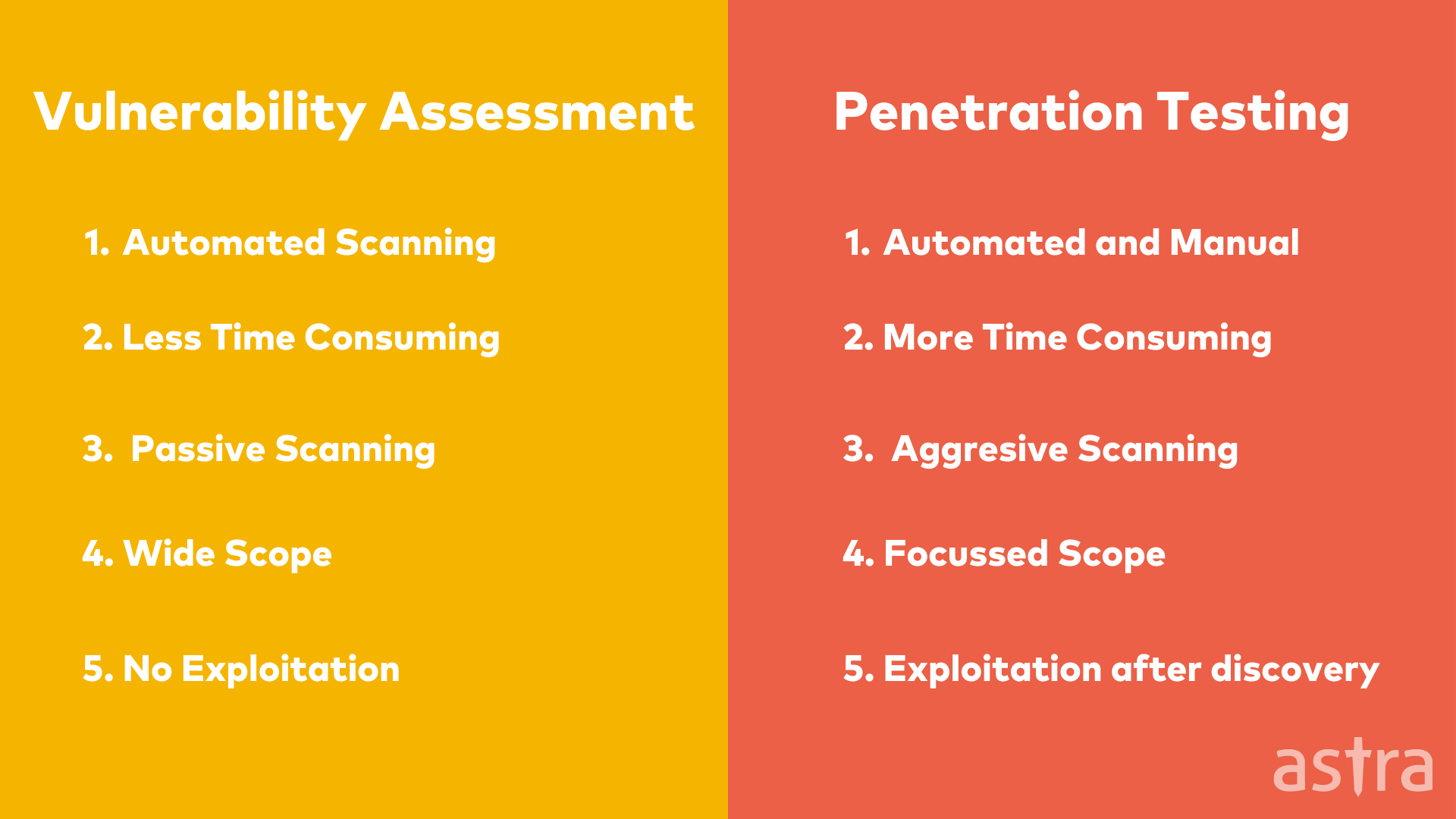
1. Vulnerability Scanning
Vulnerability scanning is the process of identifying vulnerabilities in IT systems. These systems can be web applications, local applications, operating systems, or computer networks.
2. Penetration Testing
Penetration testing is a method used to check if a system is vulnerable to internal and external attacks. A penetration tester might attack a network to see if he can compromise it. A penetration tester will generally try to gain access to the system by exploiting the flaws or vulnerabilities in the system or by social engineering.
Are you unable to access your website? Is your website experiencing hacking issues? Find out in 15 seconds.
3. Risk Assessment
Risk assessment, also known as risk analysis, identifies, analyses and evaluates risks in information security. These risks can be either to assets or to individuals or groups of users in a particular environment. Risk assessment is a crucial part of information security management. It establishes a priority list of the risks in a system and is used to determine which risks can be eliminated or mitigated effectively.
4. Security Audit
Security Audit is the process of identifying, quantifying and qualifying security-related assets that are at risk of being affected by malicious activities, misconfigurations or other kinds of vulnerabilities. The audit results are used to assess the degree of risk posed to the business and identify areas where improvements are necessary to prevent, detect, counteract or recover from attacks.
Also Read: All You Need to Know About Security Audit Report | Security Testing Software – 5 Things to Understand Before You Choose One
Understanding different Application Security Testing Methods
Testing the application for security loopholes is a crucial step before pushing it live. It is a critical part of any Software Development Life Cycle (SDLC).
The main objective of the application security testing is to identify security weaknesses and vulnerabilities in source code and thus minimize the risk of security breaches.
Here are the three application security testing methods organizations use to perform security tests:
- Static Application Security Testing (SAST)
Static Application Security Testing (SAST) is a specialized application testing that analyzes an application’s source code without executing it. SAST is also known as code review, source code analysis, or white box testing.
The goal of this testing is to find defects that could lead to security risks. The testing is performed on the source code (hence the term “static”) to ensure that it doesn’t allow for any vulnerabilities.
SAST inspects static source code and reports on security weaknesses. The weaknesses can include missing security checks, unsafe usage of cryptographic functions, and poor input validation.
Also Read: A Complete Guide to Cloud Security Testing
- Dynamic Application Security Testing
Dynamic Application Security Testing (DAST) involves the inspection of the functionality of an application. The purpose of DAST is to evaluate the security of the application, particularly in response to malicious attacks. This is in contrast to black-box testing, in which the internal structure of the application or system under test is not examined.
DAST is used from a black-box perspective, meaning it tests from the outside in, not from the inside out. This allows for a more significant number of vulnerabilities to be detected and more applications to be tested.
- Interactive Application Security Testing
Interactive Application Security Testing (IAST) is a modern approach to application security testing. IAST is a best-in-class methodology for evaluating the security of web and mobile applications that are designed to identify and report vulnerabilities in the application under test.
Unlike traditional application security testing methods that focus on static analysis and scanning, IAST focuses on dynamic and interactive testing and probing the application under test using actual user inputs and actions in a controlled and supervised manner.
IAST is a holistic and integrated approach to application security testing that empowers the tester to find and report security vulnerabilities at the earliest possible stage in the development lifecycle.
What is Interactive Application Security Testing?
When it comes to web application security, several techniques can be used to check for vulnerabilities in a web application. These techniques are collectively known as “Interactive Application Security Testing” (IAST).
IAST is a way of testing applications for security vulnerabilities. It does this by analyzing code while it is running. IAST is a relatively new form of testing, and it is becoming increasingly popular due to the number of advantages it has over other types of application security testing.
IAST allows the security testers to test the application while it is running and interacting with it. This approach is different from traditional penetration testing, where tests are performed on the application only while it is idle and not running.
Also Read: SaaS Security Management- A Complete Guide To 6 Best Security Practices
Importance of IAST
The importance of interactive application security testing has become more relevant than ever before. Security experts can now pinpoint vulnerabilities quickly, but sometimes even the most advanced tools can’t find all the bugs.
The main reason for this is that static application security testing (SAST) only looks for security issues in the code, but it’s not enough. For example, it’s not enough to know that SQL injection is present in the code, but it is essential to understand what part of the code is vulnerable. This is where Interactive Application Security Testing (IAST) comes into play.
IAST is essentially a combination of SAST and DAST. The IAST method analyzes only the code executed in your tests, like DAST, but it also pinpoints the exact place in the code where the vulnerability was found, as with SAST.
IAST takes the best of both worlds (SAST & DAST) and merges them into a more interactive testing method. Applying this method, testing engineers can get a better understanding of the application and its security risks.
To make this decision easier for which IAST vendor to choose, We’ve made a list of the most important features to look for when you are evaluating IAST solutions.
Although there are many features, some are more important than others. A good IAST can offer you lower costs, easy integration with CI/CD, auto scaling and better customer support, and more.
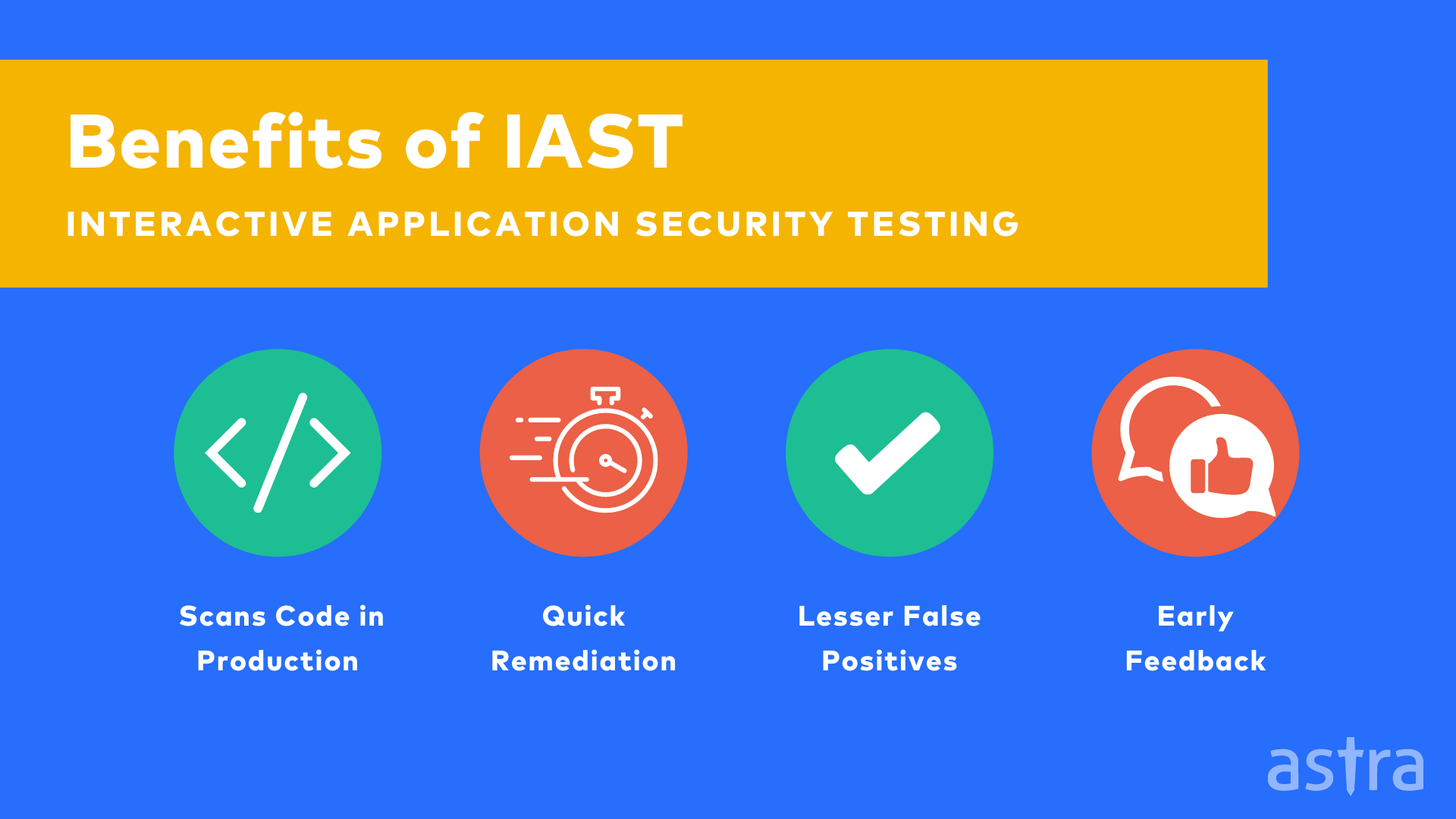
Some benefits of interactive application security testing are:
1. Scans code in production
2. Quick remediation
3. Lesser false positives
4. Allow you to get early feedback
Types of IAST methodologies (Active and Passive)
Active IAST
Active IAST is a web application security assessment methodology that combines a web application vulnerability scanner with an “agent” that works inside the application server hosting the application to provide additional analysis details, such as the location of the vulnerability in the application codebase.
Active IAST is effective because it combines a web application vulnerability scanner’s machine-learning and vulnerability detection capabilities with the manual and human-assisted analysis of an application security analyst.
An application security analyst leverages the application scanners to identify vulnerabilities and then uses the application server agent to do a deep-dive analysis to determine their severity and the impact they may have on the application. Active IAST is also practical because it can be used as part of a broader penetration test or a stand-alone assessment.
Passive IAST
The Passive IAST technology only needs a detection component that seamlessly becomes part of the application server as a runtime agent. The IAST technology is built upon passive detection techniques.
The Passive IAST technology can detect and prevent an attack without the need for an active signature or hash definition. It can also detect and prevent an attack without the need for an active signature or hash definition.
4 Open Source IAST Tools
Interactive Application Security Testing (IAST) applies penetration testing techniques from within an application. Penetration testing is typically performed by externalizing the application. Meaning, the tester uses the application to simulate user actions and detect vulnerabilities.
IAST tools analyze an application’s code from within the application while an external test or human tester interacts with specific functionality. The penetration testing tool is placed within the application, and it interacts with the user to compromise application security.
The most common tools used for Interactive Application Security Testing are:
1. OWASP ZAP: OWASP ZAP is an application vulnerability assessment and management tool for web applications.ZAP is often used by developers who are building applications, as well as by security teams who are doing internal security assessments.
2. Vega: Vega is a tool for testing the security of web applications. Vega can also be used to scan and test internal networks and intranets. It can scan web servers and web applications running on the same server. Vega has a simple and easy-to-use interface which makes it easier for users to scan and test the security of their applications.
3. W3AF: W3AF is a Web Application Attack and Audit Framework. The framework is extensible with modules that are designed to be easy to configure and extend. The framework can either be used in a manual or in an automated way by using the API in the Python language.
4. SonarQube: SonarQube is a platform that provides a centralized location to assess the quality of your application or project’s code. SonarQube consolidates all of your project’s quality issues and metrics into a single platform, where you can view them from a central location. It also allows you to track changes over time. The most interesting part is that SonarQube can be integrated with a lot of different continuous integration servers.
Also Read: Top 5 Software Security Testing Tools You Should Know About
Why do you need Astra’s Pentest Solution?
Astra’s Pentest solution offers a comprehensive set of security tests for any type of application. The solution offers manual, automated and a mix of both security test cases and achieves SAST, DAST and IAST methods of security testing.
Astra’s interactive application security testing (IAST) offering enables you to identify and fix security vulnerabilities in your web applications very efficiently. It is a proactive approach to discovering and resolving security vulnerabilities in your software before hackers do. The need for IAST is enormous in today’s age of data theft and cybercrime.
Read Also: Software Penetration Testing: A Complete Guide
Further, Astra’s Interactive Application Security Testing will help you evaluate the security of your web applications and determine the vulnerabilities that your applications have. Astra’s expert security engineers will find bugs that can be exploited by potential hackers and help you to plug the security holes.
With Astra’s Interactive Application Security Testing, you can avoid any data breach that would cause your company’s reputation to suffer. Astra team will help you to eliminate security issues before they can do any harm.

Conclusion
When it comes to application security, organizations look for a silver bullet to take down application vulnerabilities. In reality, there is no such thing as a silver bullet, but there are multiple ways to reduce application vulnerabilities. One of them is through interactive application security testing (IAST). That’s where Astra Security comes in. We provide complete penetration testing that closely resembles the approach of an attacker. We seek out vulnerabilities in your application that hackers can exploit. These vulnerabilities are like the holes in your home’s security system. Astra is like the locksmith who comes in and helps you secure your home.
FAQ’s
1: What is Interactive Application Security Testing?
Interactive Application Security Testing (IAST) is a best-in-class methodology for evaluating the security of web and mobile applications that are designed to identify and report vulnerabilities in the application under test. Also known as vulnerability-driven testing, IAST is a methodology your team can apply to find and fix vulnerabilities quickly and effectively.
2. How is IAST different from DAST?
With DAST, you are testing the application at the time it is running, while with IAST, you are testing the application at the time it is not running. They are both effective, but they are used to test vulnerabilities in different parts of the application. IAST is used to find vulnerabilities that are not accessible with DAST.
3. Why security testing is important?
Security testing is the best way to ensure the security of your data and your business. It is also one of the most important steps in your DevOps lifecycle. You can have the most secure code in the world, but if it isn’t tested, your data is never going to be safe. This is why it’s crucial to have a security testing team that is experienced, knows what they’re doing, and knows how to test your code efficiently.
4. Why should you choose Astra?
Astra Security is leading provider of information security services and solutions to customers across the globe. We offer a wide range of pre-engagement services, including consultation and expert research and analysis, and we can conduct a full range of security tests: web application security testing, cloud pentest and network security testing, API testing, etc.
















