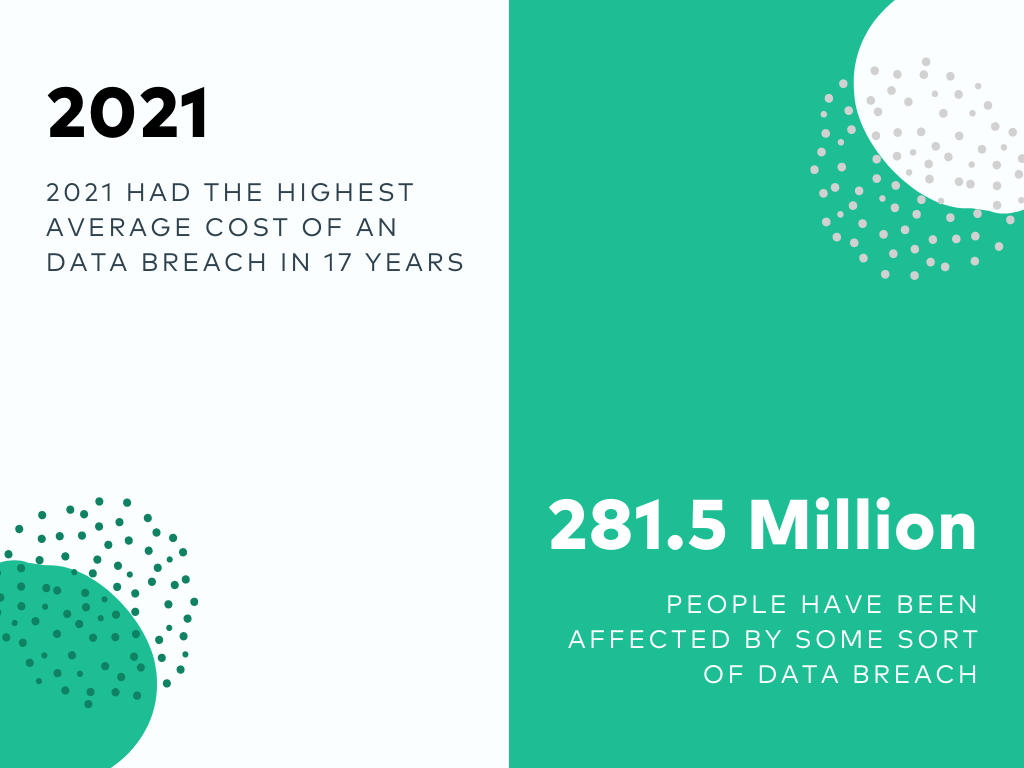
In today’s world, where a huge amount of information is generated from multiple platforms, all organizations need to ensure that their information is safe from all kinds of cyber threats. The biggest threat that attacks organizations is the vulnerability of cyber security. According to a report by ITRC, data breaches have exceeded the total number of data compromises in 2020 by 17 percent.
Cyber security is a major concern for a lot of organizations today. Organizations are losing millions of dollars every year due to data breaches. The situation is getting worse each day as businesses are not aware of the latest techniques used by hackers. This makes understanding a security audit report all the more important.
Hackers are using sophisticated techniques to bypass apps and networks to steal confidential data. Organizations must conduct regular security audits to make sure that confidential data is not leaked to hackers.
What is a Security Audit?
It’s no secret that most businesses use the Internet for communicating, storing data, and doing business. However, it’s also no secret that many cybercriminals out there are looking to access this data for their gain. Therefore, it pays to understand the best ways to protect your business from these cybercriminals.
The security audit is a comprehensive assessment of a business or organization’s security policies, procedures, and technologies. The security audit is a fact-finding mission to investigate a company’s network and information security practices.
The objective of a security audit is to identify vulnerabilities and make recommendations to the business. Performing security audits make businesses more secure from security breaches and data loss. A security audit involves a detailed examination of a business’s security policies, procedures, and technologies.
A security audit may be performed by a third party or by the business itself and it does not necessarily have to be a one-time activity. A business can opt for a security audit on a periodic basis.
5 Common IT Security Audit Standards
The auditing process is critical for maintaining compliance with IT security standards. Still, the sheer volume of standards out there is enough to make even the most seasoned audit professionals lose sleep at night.
But the good news is that most of the standards are in some way interconnected. That means that you can comply with multiple standards in many cases by following the same audit protocol.
For example, If you are following one of the ISO standards, you are at least in compliance with some key security standards, including many directly related to the ISO standards.
Let’s find out some common compliance standards:
1. ISO 27001
ISO 27001 is the International Standard for Information Technology – Security techniques – Information security management systems – Requirements. ISO 27001 is an information security management standard that enables an organization to improve its security posture.
There are many ways to improve your information security posture. Still, this standard provides a framework of best practices that can make it easier for your organization to identify, analyze, and manage the risks of your information assets.
2. PCI DSS Compliance
PCI DSS is a set of 12 requirements that specifically target how organizations store, process, and transmit cardholder data. The Payment Card Industry Security Standards Council (PCI SSC) developed the PCI DSS to protect against credit card fraud.
The PCI Security Standards Council (PCI SSC) maintains the PCI DSS, the de facto global standard for organizations that handle credit card information. The PCI DSS also applies to organizations that store, process, or transmit any cardholder data, which includes the following: Name, address, and Social Security number (SSN).
3. NIST Cyber-Security Framework
The NIST Cyber-Security Framework (NIST CSF) defines a set of best practices that enables IT organizations to more effectively manage cybersecurity risks. The NIST CSF promotes the use of risk management as a means to achieve organizational objectives for cybersecurity.
The NIST CSF is a voluntary, risk-based approach to cybersecurity and offers flexible and repeatable processes and controls tailored to an organization’s needs. The NIST CSF is a set of standards and guidelines that federal agencies can use to comply with the Federal Information Security Modernization Act (FISMA).
4. SOC2
SOC 2 is an auditing procedure that ensures your service providers securely manage your data to protect the interests of your organization and the privacy of its clients. This compliance is necessary to meet the standards of your organization’s clients and to stay compliant with the industry standards.
SOC 2 compliance ensures the security of your company’s information assets and protects the interests of your organization. It is a certification of trust, which says that your company protects the type of information that is considered personal and private. SOC 2 is one of the most widely used standards for third-party service providers, and is an absolute must for any organization that is looking to be compliant with the industry standards.
5. HIPAA
The Health Insurance Portability and Accountability Act (HIPAA) is a federal law that requires covered entities to protect the confidentiality, integrity, and availability of electronic health information that they create, receive, maintain, or transmit.
HIPAA protects the privacy and security of health information and sets national standards for how health care providers, health plans, and health care clearinghouses and their business associates must work together and with covered entities to ensure the safety and privacy of personal health information.
Why do you need a Security Audit Report?
A security audit report can be defined as a comprehensive document containing a security assessment of a business or an organization. It aims to identify the weaknesses and loopholes in the security of the organization, and therefore, it is an important document that can help an organization secure itself.
The security audit report is one of the most important documents used to assess the strengths and weaknesses of the security of an organization.
A security audit report typically lists all the audit team’s findings, which can be in the form of misconfiguration errors, vulnerabilities, or any other security defects in a system. The audit report also recommends remediation actions to the respective management to improve the security of their organization.
Some other use cases of security audit reports are:
- Compliance and Standards
- Global and local laws
- Customer Trust and Reputation
Key Components of Security Audit Report
One of the main goals of any audit is to provide actionable feedback so that the client can work towards improving their security. This feedback comes in the form of the report generated at the end of the test.
A security audit report may contain several different sections. There can be a section with information about the deliverables, audit scope, timelines, details about the testing process, findings, recommendations, etc.
Although there are many different types of penetration tests or hybrid application analysis, they all share key components of a security audit report mentioned below:
1. Title
Title of the security audit report.
2. Table of Contents
The table of contents is an essential part of the audit reports. They provide a quick and convenient way to view the most important information in the report.
The table of contents is especially useful in large and detailed audit reports. It helps to quickly locate any detailed information, such as the auditor’s name, the scope of the audit, the date of the audit, and the number of pages in the audit report.
3. Scope of Audit
Scope of audit refers to a broad description of what is included in a project or the scope of a contract. In the scope of work, the project manager and other stakeholders identify the work needed to accomplish the project purpose.
4. Description
The description section in the security audit report is the detailed technical description of the security risk. The description contains:
- All relevant details about the issue
- How to reproduce the issue
- How easily can a hacker exploit it
- The severity of the issue
- CVSS Score of the vulnerability
5. Recommendations
The recommendation section contains details about the fix or patch that needs to be done to mitigate the security risk. Here, the fix depends on the type of security vulnerability.
For Example, Developers can mitigate an XSS by escaping or encoding characters and using a WAF. But, the XSS can be prevented by not using the outdated version of jQuery.
6. References
References are important from a company’s point of view. References could be a blog, a news item, a whitepaper, or any informative material that might help the company to better understand the vulnerability and its fix.

Who prepares a Security Audit Report?
A security audit report is prepared by a team of security auditors (Internal or External) who performs an audit on businesses or their websites to ensure that the business is compliant with the industry standards and regulations.
In most cases, organizations hire external security auditors to perform an audit, and they prepare a security audit report.
External security auditors are a very important aspect of any organization opting for a security audit by a third-party vendor. The organization should consider a well-known or reputed vendor that has prior experience and trust factor in the industry.
The purpose of an audit could be to determine the organization’s risk, provide advice leading to improvements, test the controls in place, provide assurance that the organization is following an established set of procedures, etc.
Organizations may perform a security review for various reasons, including meeting compliance requirements, gaining a better understanding of an organization’s security posture, or improving the overall security.
How does Astra help you get a security audit report?
Cyber security has become a major concern for organizations. The growth of hackers and cybercriminals has increased to hacking a website, a database, or a server. They hack into the accounts of the companies and steal critical information. So, it is very important to keep track of everything that is going on in your company.
Astra is a cybersecurity firm offering a range of high-end cyber security services and solutions for security audits, penetration testing, and vulnerability assessment, vulnerability scanning, malware removal, and website firewall.
Astra has a team of world-class security experts who work round the clock to keep clients secure from hackers. Astra’s team is one of the best in the industry and has successfully conducted many security audits for a wide range of clients.
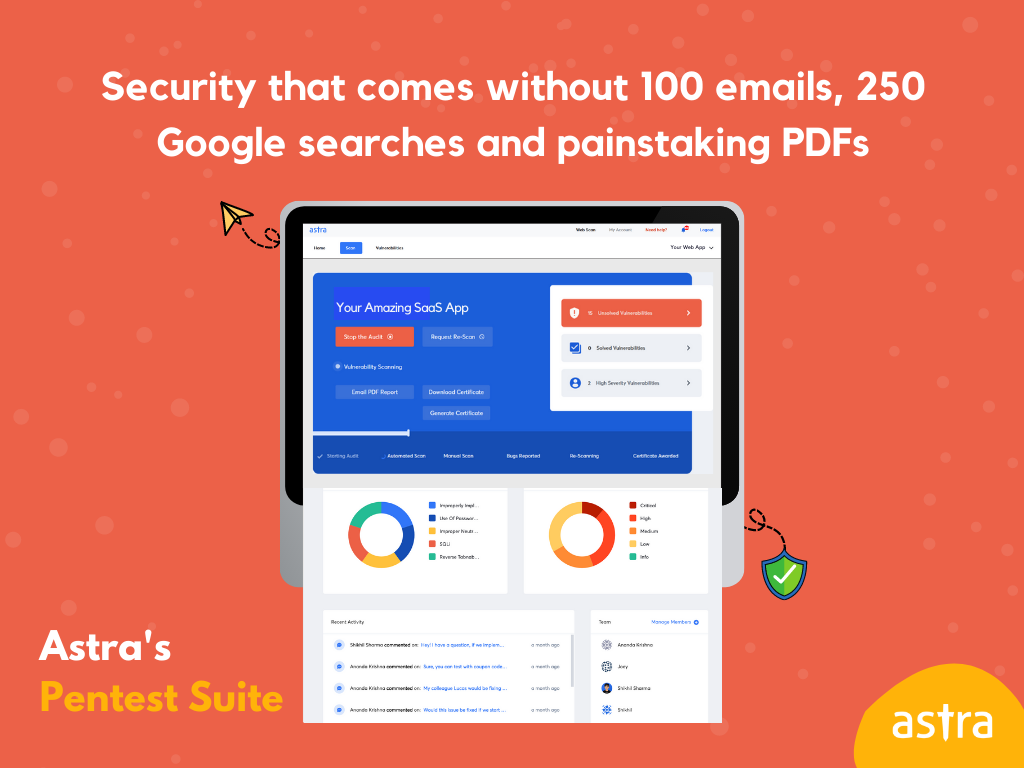
Key Highlights in Astra’s Security Audit Report
Astra’s Security Audit Report has the following key features:
1. Industry Standard Security Testing
Astra’s security specialists perform industry-standard security testing with over 2500+ tests that follow OWASP, SANS, ISO, and CREST guidelines and compliance requirements.
2. Detailed Vulnerability Analysis
Astra’s Security Scan dashboard and pen-test report show a detailed analysis of vulnerabilities, including the impact, severity, CVSS score, affected parameters, and steps to reproduce each vulnerability with video proofs-of-concept (PoCs).
3. Steps to Fix Vulnerabilities
Each vulnerability has a section within the report that describes it in detail and speaks of fixing such flaws and provides an overview of each mitigation with steps to fix (with external informative resource references).
4. Easy to access
The report can be downloaded easily from Astra’s main Pentest dashboard. You can either download the report in the format of PDF or Email.

Download Sample Security Audit Report by Astra Security
Conclusion
After a penetration test or a security audit, the first thing a client would ask for is the findings from the security audit report. This report must be a comprehensive security report that should include the entire audit process, vulnerability details, testing methodologies, any other findings, and finally recommendations on how to prevent the vulnerability as well as the steps to fix it. Security issues can be a real pain in the neck, but Astra can help you fix your problems.
FAQs
1. How Much Does an IT Security Audit Cost?
The cost of IT security audit varies according to the scope and depth of the audit.
2. Why do you need a Security Audit Report?
A security audit report lets lists down all the existing vulnerabilities and categorizes them according to severity. It also provides you with the necessary measures to fix those issues.
3. How Astra helps you get a security audit report?
Astra Security has an interactive and collaborative security audit reporting procedure. Not only do you get a detailed PDF report along with video POCs on how to reproduce vulnerabilities, but you also get expert assistance from security engineers at Astra while working on the issues.
4. Do I also get rescans after a vulnerability is fixed?
Yes, based on the plan you get 1-3 rescans. You can avail these scans within 30 days of the initial pentest completion.
















