Website Vulnerability Testing is a methodical way to find any weak spots or vulnerabilities in your organization’s website or application that can be used by malicious hackers and bots to gain unauthorized access or control of your data.
Also known as website security testing or web application security testing, the goal is to proactively find, assess, and rank potential security issues to empower your business to fix the same before malicious hackers can exploit them.
What is a vulnerability?
A vulnerability is a particular aspect or configuration within your organization’s system (including employees) that can be misused by hackers to gain illegal access. Once they gain access, they can steal sensitive company and customer data, or manipulate the system to work for their will.
Because of the importance of data and websites for any organization, most realize the importance of conducting cyber security checks. One way of going about this is the Vulnerability Assessment and Penetration Testing (VAPT) procedure, of which the vulnerability assessment is what we’re going to talk about now.
How will you identify vulnerabilities in a website?
There is a wide variety of tools available in the market that can help you identify various vulnerabilities. They can be grouped together into 3 major categories, namely:
- Web application scanners – For testing and simulating known attack patterns and analyzing the response of the website
- Network scanners – Understand the networks of the organization and look out for potential issues like unprotected IP addresses, suspicious generation of packets, or spoofed packets from one IP address.
- Protocol scanners – Look out for vulnerable ports, network services, or protocols
OWASP provides an open-source list of the different issues that need to be kept in mind for web application security. Check this out to get a better perspective on what applies to your situation and plan accordingly.
Why is Astra Vulnerability Scanner the Best Scanner?
- Runs 8000+ tests with weekly updated scanner rules
- Scans behind the login page
- Scan results are vetted by security experts to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities from one place.
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Integrates with Slack and Jira for better workflow management
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

Common vulnerabilities found in websites
VAPT procedures – and website vulnerability testing – are designed to find a range of issues within websites and systems that could compromise your security. Here are a few of the commonly found vulnerabilities:
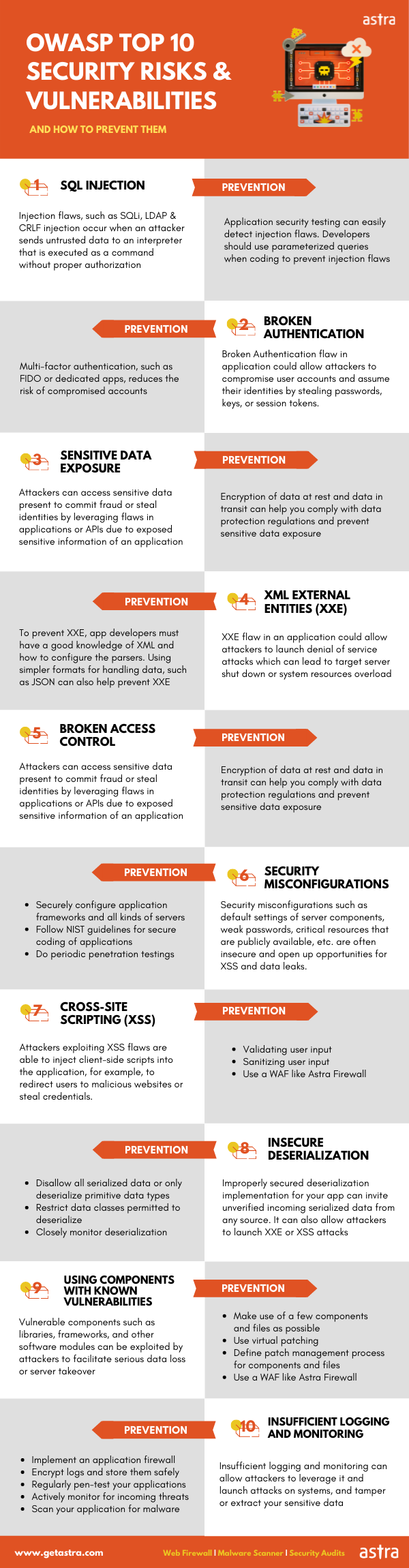
- SQL Injection: This involves inserting malicious SQL code into a web application’s database query, potentially giving unauthorized access to the database.
- Cross-Site Scripting (XSS): This occurs when an attacker injects malicious scripts into a website, which are then executed by a user’s browser, potentially stealing sensitive information or performing actions on behalf of the user.
- Cross-Site Request Forgery (CSRF): In a CSRF attack, an attacker tricks a user into performing unwanted actions on a website, potentially leading to unauthorized actions being taken.
- Security Misconfigurations: These occur when security settings, server configurations, or application settings are improperly configured, leaving the website vulnerable to attacks.
- Sensitive Data Exposure: If sensitive data (such as passwords, credit card numbers, or personal information) is not properly protected, attackers may gain access to this information.
- Broken Authentication and Session Management: Flaws in the authentication and session management mechanisms can lead to unauthorized access to user accounts.
What are the benefits of vulnerability testing?
Vulnerability testing provides a range of significant benefits to your business. It plays a pivotal role in risk management by proactively identifying vulnerabilities in your systems. Moreover, by addressing vulnerabilities before exploitation, you can curtail potential financial losses and operational disruptions.
This approach not only safeguards sensitive information but also contributes to regulatory compliance efforts and improves the overall security barriers of the company as explained under.
Website Vulnerability Testing for Compliance
Let’s talk about the compliance requirements that organizations within certain industries have to fulfill. Following certain standards and regulations help you ensure that you’re compliant while giving you a competitive advantage over those who don’t. Standards can be both geography-specific and industry-specific, here are some of the common ones:
- HIPAA – Health Insurance Portability and Accountability Act
- GDPR – General Data Protection Regulation
- ISO 27001 – from the International Organization for Standardization for maintaining security standards
- PCI-DSS – Payment Card Industry Data Security Standard
Vulnerability Testing for Strengthening Security Barriers
Beyond the general advantages of improved security and risk mitigation, website vulnerability testing is a highly useful standard to assure system hardening measures. It helps you strengthen the security barriers and then minimize possible attack vectors.
Vulnerability Testing for website security provides a picture of unnecessarily open ports, ensuring updates of any outdated software/services, etc. Sometimes, major services may require separate servers, which will also be visible through this procedure.
How to conduct a successful website vulnerability testing?
Once you’ve armed yourself with the right information and tools, the only step left is to follow through with the required steps.
Step 1: Define your assets
This step basically covers defining the aspects of your network that need to be scanned. It isn’t a random decision and requires one to be aware of the system infrastructure, its possible flaws, or strengthening needs.
For example, if you deal with IoT elements as part of your organization’s functioning, it’s probably majorly connected to mobile networks. Devices used to connect to the system (mobiles, laptops, etc.) often connect and disconnect frequently from different locations. There’s also the question of the right balance between ease of accessibility and adequate safety when it comes to cloud-based services.
The good thing is that this step of the vulnerability assessment process is better done with automated tools. Vulnerability assessment tools have the ability to scan large public-facing systems while connecting with cloud service providers. This will help them to look into cloud-based infrastructure as well.
Step 2: Define your goals
As extensive as your system is, it may be difficult to run an extensive vulnerability assessment into all components. Beyond the scope of conducting such a test, often vendors charge per asset scanned, so it becomes important to prioritize.
Do you wish to look into databases with sensitive data first? Or, is it your preference to check internet-facing servers and customer-facing applications? Often, the target of mass, generalized attacks (like brute force or DDoS) is employees’ systems and internet-facing components.
Step 3: Pick the right kind of vulnerability scan
There are network vulnerability, host-based vulnerability, and wireless-based vulnerability scans.
The first kind investigates the networks, all communication channels, and supporting equipment used in the environment. This will also include the software and hardware devices, like routers, hubs, firewalls, switches, clusters, etc.
The second type goes a bit further and analyzes potential weaknesses with hosts based on these networks. You’ll need this kind of scanning to check into user directories, file systems, or memory settings. It majorly focuses on the endpoints and the level of functionality of the internal systems.
Finally, the third kind looks into the type and number of wireless devices on your network, plus their attributes for proper configuration. There could be possible rogue access points that can be exploited which need to be removed immediately as they can listen in on your wireless traffic. You will also need to test the LAN infrastructure and the wireless access points for extra security.
Step 4: Scan for vulnerabilities
These scanners work to find out the weaknesses in your system with possible remediation measures. Since they find out known security risks, there will be information regarding where to find these loopholes and fix them. First, the scanner sends probes to note down the software versions used, the configuration settings currently present, and any open ports or running services. This information is used to find out if any vulnerable devices or software are hidden within the network.
There are also probes to identify individual vulnerabilities through an ethical exploit which shows the location and intensity of risk. Issues identified usually include command injections (SQL) or cross-site scripting (XSS) attacks. How complicated the system is, the number of components, etc. determine the time of a typical vulnerability assessment.
Step 5: Results & Resolution
After the detailed vulnerability assessment, the next important step is the final report prepared. The report includes all of the system details that need to be used for designing the right website penetration testing procedure. There are a couple of general features that you must be aware of when reading a vulnerability assessment report;
Exposure to vulnerabilities – While the probability is higher, vulnerabilities are not always on public-facing systems. You can find equally concerning vulnerabilities on internet-facing systems that can be exploited by hackers. The next priority is employee systems with potentially vulnerable software installed. All systems that host sensitive data of any kind or can negatively impact your business if compromised should be checked.
Identify the criticality – You should always be able to identify vulnerabilities based on the risk they possess, ideally on a quantifiable scale. This is so that remediation can focus on the most severe issues before moving on to the rest. Smaller vulnerabilities shouldn’t be ignored for too long, since hackers sometimes club multiple small ones to create one large security risk.
Different types of website vulnerability testing?
There are various kinds of vulnerability assessments depending on the scanning requirements, industry type, and other unique needs of your organization. Some of these are:
- Network and Wireless Assessment – This assessment specifically deals with the policies and general practices implemented within the company to ensure the safety of data. It will assess the steps taken to prevent illegal and forced access into the company servers, private or public networks, and connected resources.
- Scanning applications – Looking into web applications is crucial to identify the associated security vulnerabilities and any faults in the source coding. This can be done either through automated scans (done from the front end) or static or dynamic analysis of the source code.
- Host assessment – Some servers need to be assessed based on their criticality, vulnerability to attacks, and whether they’re tested periodically and within requirements.
- Assessing the database – The database of a website often contains sensitive data related to the owner, company, and customers accessing it. Therefore, big data systems need to be assessed regularly and in a detailed manner for any misconfigurations, vulnerabilities, etc.
Sometimes, rogue databases pop up or issues arise due to insecure developing/testing environments, which need to be dealt with. Also, make sure to classify the data used according to its importance, sensitivity, and frequency of use throughout the organization’s infrastructure.
Website vulnerability testing for small website owners?
Whether you are a start-up or an MNC, cyber threats like malicious code and ransomware pose serious risks to your business. While larger companies often have separate teams for infrastructure and security, due to budget constraints small businesses often need to outsource security procedures to trusted professionals.
When selecting a security provider, prioritization and steady progress are key. Understanding risk levels, fixing timelines, and aligning goals with your business’s unique needs are some basic requirements you should be on the lookout for. Assess the service quality and ask questions to check their understanding of your business model and their ability to provide security roadmaps.
In today’s digital era, protecting your website from cyber threats is essential. Vulnerability testing detects and addresses security weaknesses and vulnerabilities like SQL attacks, enabling preemptive action. It can be segmented into 3 major categories and offers multiple benefits including holistic security and compliance. Even small businesses benefit from outsourcing to VAPT experts like Astra Security.
FAQs
1. What is a website vulnerability?
A website vulnerability is a bug, misconfiguration, or outdated patch in the design, coding, configuration, or overall security of a website that could potentially be exploited by malicious actors to gain unauthorized access to sensitive data and compromise the integrity of the website.
2. What is the best web vulnerability scanner?
Astra’s Pentest with 8000+ tests, zero false positives, continuous scanning, and compliance reporting features is one of the best vulnerability testing tools for websites available in the market. Moreover, with budget-friendly plans, it is suitable for businesses of all sizes and purposes.
3. Is vulnerability scanning the same as penetration testing?
No, vulnerability scanning and penetration testing are different procedures with a similar goal. Vulnerability scanning automates the search for known security weaknesses, while penetration testing involves skilled professionals actively exploiting vulnerabilities to assess real-world risks.
















