Security automation refers to the process of automatic detection, inspecting, and remediation of cyber threats. This can be done with or without the aid of humans by using specific applications built for the purpose. This minimally human-assisted process is used for integrating security flows, applications, and organizational infrastructure.
Organizations in the IT field are growing by leaps and bounds daily. This doesn’t just refer to the number, but also the size of the businesses. The scaling of numerous such companies has brought about the need for a faster pace in security.
This is where security automation comes into play. This article will go in-depth about security automation, its importance, types, and significant signs of needing automation.
Why Is IT Security Automation Important?
IT security automation is vital for companies in this era for multiple reasons:
Standardized Workflows
Automating security results in the simplification of actions that will be consistently applied without the need for human intervention thereby ensuring a continuous, repeatable process or an efficient workflow.
Certain actions that can be implemented through automation for standardized workflows are the deletion of infected files, searching for particular files, and quarantining devices from a network.
Seamless Integrations
Automation in cybersecurity paves the way for seamless integrations between other security measures such as endpoint security, firewalls, vulnerability management services, ticketing systems, and even security incident and event management services.
Helps Set Priorities
Security automation helps organizations and the teams within to get a birds-eye view of their cybersecurity posture. This allows them to prioritize the security concerns that need immediate attention over issues that are of lesser importance.
Having clear priorities also allows teams to find more opportunities to integrate automation into the workflow.
Aids in Documentation
Steps that you take while automating your cybersecurity can be documented thoroughly and used as a playbook for the establishment of other automated processes. A well-structured automated process can only be as effective as the information put into it. This means the transfer of organizational knowledge from you to automation has to be flawless.
Reduced Workload
Automating security has a direct effect on the workload and pressure that is put on security teams. Most IT infrastructures are complex and spread out making it difficult to keep track of everything by monitoring it.
Automating security means that the security team has more time to focus on effective security solutions rather than chasing possible false positives or low-risk issues.
Types of Security Automation
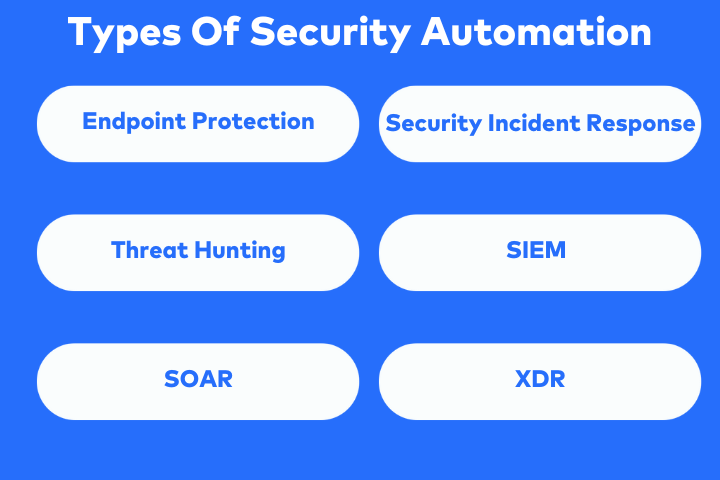
Security automation comes in a variety of applications that are designed to help organizations of various stature. Some of the major applications that aid in the automation of cybersecurity are:
End-Point Protection
Automated Endpoint Protection Platforms can be availed for the detection, investigation, and remediation of malicious activities on user-end devices. User-end devices constitute the most vulnerable and attack-prone components of an IT company’s infrastructure.
Security Incident Response
Timely detection and response to security breaches often cost millions of dollars and hundreds of days at a minimum. Automated security incident responses can help reduce the time taken for detection, thereby reducing the impact and the costs incurred due to the breach.
Automated security response can be applied throughout applications and forums seamlessly to reduce erroneous vulnerability detection and allow rapid mitigation responses.
Threat Hunting
Threat detection is usually a time-consuming, manual process that drains team energy, expense, and effort. However, by automating this process one’s security team can focus on more urgent security matters.
Automating threat detection makes it more speedy and cost-efficient by ensuring the detection and identification of vulnerabilities at a faster rate without human assistance.
Security Information and Event Management (SIEM)
SIEM applications collect, compile, and analyze security data from an IT company’s infrastructure. SIEM provides contextual data security breaches by removing the need for manually collecting data from multiple resources.
Security Orchestration, Automation, And Response (SOAR)
SOAR applications automate security incident responses by adding on to SIEM solutions. It provides risk alerts and is also capable of dealing with potential threats thereby reducing the impact on the business and its revenue.
Extended Detection and Response (XDR)
Extended detection and response solutions combine both the technologies of SOAR and SIEM to bring forth a centrally managed security solution. XDR solutions can proactively prevent cyber-attacks based on its threat intelligence reports and raw data.
What Role Does Security Automation Play in SOC?
Modern security operations centers or SOCs largely rely on automation for basic tasks like security analyses, threat detection, and even vulnerability remediation.
Security automation systems essentially reduce the brunt of tasks on human analysts and cybersecurity professionals from having to through each alert. This gives them the opportunity to focus on the more pressing security matters at hand.
In SOCs of today security automation deals with:
- Detecting threats to IT infrastructure.
- Prioritizing alerts to speedy vulnerability detection and identification.
- Application of pre-set criteria to determine, identify and contain vulnerabilities or risks.
Security automation successfully solves the issue of alert fatigue, which is an issue that rises when human operatives have to deal with copious amounts of security alerts in a short span of time.
Capacities of Enterprise Security Automation
Security and automation go hand in hand in providing various solutions to handling IT infrastructure security in a more efficient manner. These capacities of security automation include:
Detection and Response To Threat
Automated security tools can aid in the continuous monitoring of organizational assets to ensure quick and timely detection of threats as well as in mounting an immediate response to vulnerabilities detected.
Timely detection of threats and immediate responses to mitigate them drastically reduce the impact and the cost of a security breach.
Continuous Monitoring For Compliance
The security of data in the IT field is governed by global compliance regulations like GDPR, HIPAA, ISO 27001, SOC2, and PCI-DSS. Automation here comes in the form of compliance scans to ensure that the security measures of an organization are continuously compliant with the required regulations.
Vulnerability Management
Automated vulnerability management tools can help right from the identification of vulnerabilities and threats to prioritizing them and providing recommendations and remediation measures for easy resolutions. This in turn helps reduce the chances of a successful exploitation of vulnerability in applications, networks, or systems.
Incident Response
Automation can help in producing a coordinated incident response with streamlined notifications and responses. Automation in incident responses can help reduce the impact of security breaches, reduce downtime, and make the restoration process quick.
Major Signs Of Needing Automation In Cyber Security?
Here are some of the major signs that indicate the immediate need for automation in your cybersecurity processes.
Security Breaches
One of the most evident signs of needing major automation and streamlining of cybersecurity is the failure of a security system to stop a security breach. The impact of cyber attacks varies greatly from costing nearly nothing to costing millions of dollars. Successful security breaches essentially indicate the failure of the currently present cybersecurity system.
Slow Incident Response Times
Without automation in security, the time taken to detect, identify, prioritize and finally respond to the threat at hand would be far too long by which point the damage to the organization would be tenfold. If the detection and remediation time taken by your security team is slow, it is clear cry for need for cybersecurity automation.
Numerous False Positives
If your company’s security team is handling an awful lot of false positives, it is wise to implement an automation vulnerability scanning or management system that is better equipped to weed out false positives to give your company the time it needs to focus on more important tasks.
Fatigued Security Team
Being bombarded with a myriad of security alerts can tire out any security team and drastically reduce their efficiency. Spending precious time chasing false positives will them and their resources thin leaving them weary for the actual security concerning issues.
Conclusion
Security and automation are terms that go together where one without the other in IT is redundant in the present age. As such, it is always prudent to establish automated processes where ever possible to ensure security teams on deck can deal with the more vital security concerns on priority.
This article has discussed in detail what security automation is, its different types, capacities, and major signs of needing it. With the continuously progressing towards newer technologies, security automation will quickly become the driving force that ensures the protection of all cyber assets.
FAQs
What are the different types of cyber security?
Different types of cyber security include web and mobile application security, network security, cloud security, API security, data security, and endpoint security.