Azure vulnerability scanning is the process of finding and evaluating security holes in the resources and assets of an organization that are housed on the Microsoft Azure cloud platform. Vulnerability scanning is an important part of cybersecurity because it helps organizations find and fix potential vulnerabilities in their Azure systems before attackers can use them.
Azure vulnerability scanning tools and services scan for vulnerabilities and improve the security of cloud operations.
What is Azure vulnerability scanning?
To improve cybersecurity, Azure vulnerability scanning is a proactive process that finds, evaluates, and fixes security flaws across its assets.
It entails employing Azure’s robust capabilities, including configuration management programs, patch management, and vulnerability scanners.
These technologies make it possible to locate assets, evaluate vulnerabilities, look for misconfigurations, and handle security patches. Azure’s risk-based prioritization effectively mitigates critical vulnerabilities.
Workflows for managing vulnerabilities are automated by integrating the currently installed security infrastructure. Collaborative features make real-time progress monitoring and remedy tracking simpler.
Organizations may improve their cybersecurity posture, safeguard essential assets, and proactively manage threats with the help of Azure vulnerability scanning tools.
Top 7 Azure vulnerability scanning tools
1. Astra Vulnerability Scanner
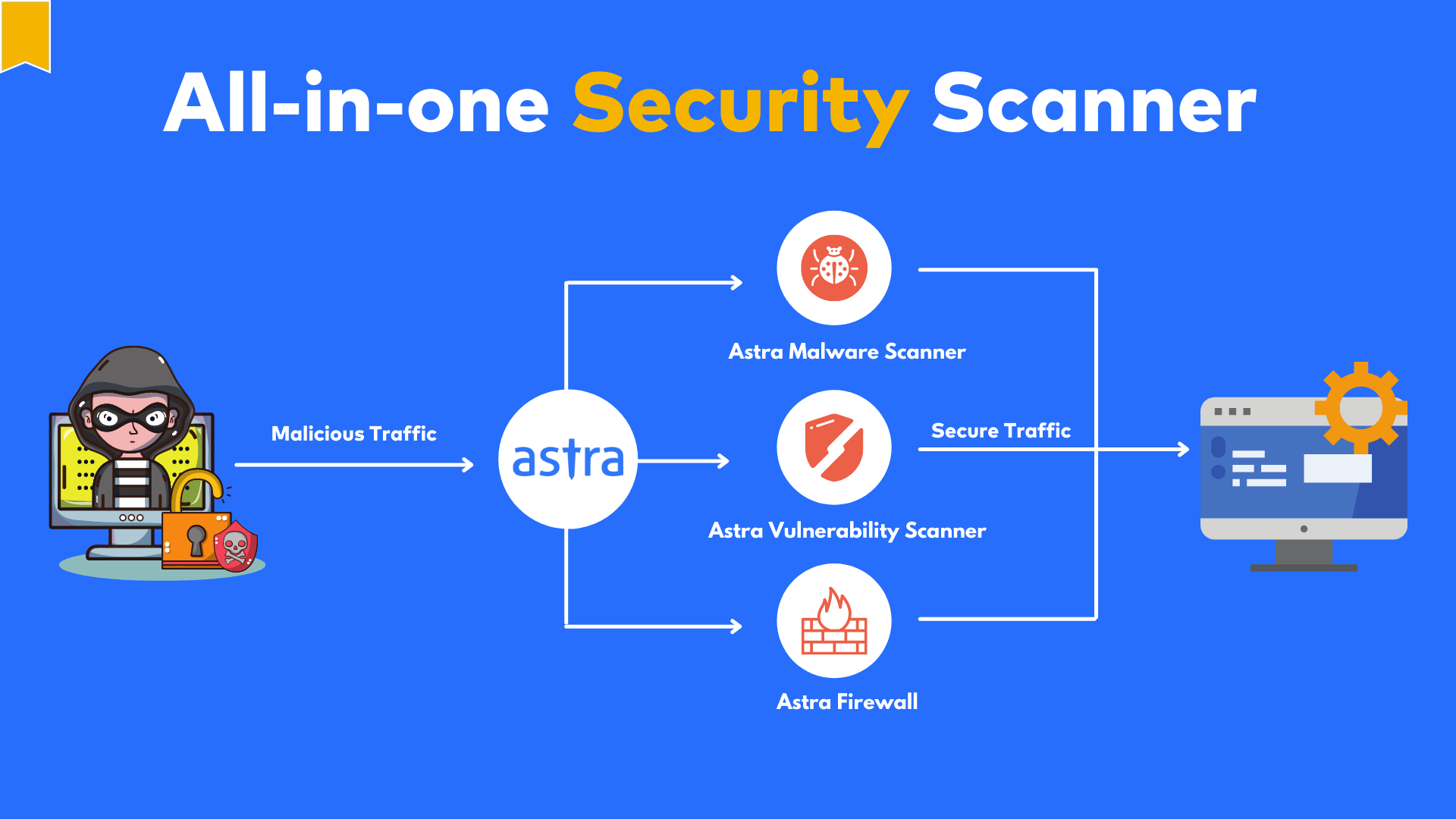
Astra Vulnerability Scanner is a leader in vulnerability scanning and assessment services with top-notch security methods to strengthen your company’s protection.
Astra conducts extensive evaluations and finds over 3,000 security flaws using their industry-recognized NIST and OWASP techniques. It ensures GDPR, HIPAA, PCI-DSS, ISO 27001, and SOC2 compliance.
The frequent automated and manual pentests conducted by Astra serve as proof of its dedication to complete security. To evaluate the effectiveness of the remediation, they carry out the necessary rescans. The Astra pentesting specialists minimize false positives and guarantee precise evaluation results.
Astra provides a variety of services, including login scanning, 24/7 customer support, and seamless integration with CI/CD pipelines. Expect end-to-end scanning, useful insights, and publicly verifiable certificates for a thorough evaluation experience.
Features
Astra Scans: Astra thoroughly scans your systems, applications, and network architecture.
Regular Assessments: Astra regularly evaluates vulnerabilities by scanning to maintain continued security.
Actionable Reports: Comprehensive reports outlining the vulnerabilities found, their levels of severity, and suggestions for fixing them
Customization Options: You can adjust Astra’s scanning parameters to narrow in on certain problem areas.
Expert Support: Astra provides knowledgeable assistance from security specialists who can help you learn about the risks.
What is good?
- It does authorized scans behind logins.
- It keeps running automatic and manual pentests on your Azure infrastructure.
- you can see all of your results on the dashboard itself
What could be better?
- Increased Scan Frequency
2. Azure Defender
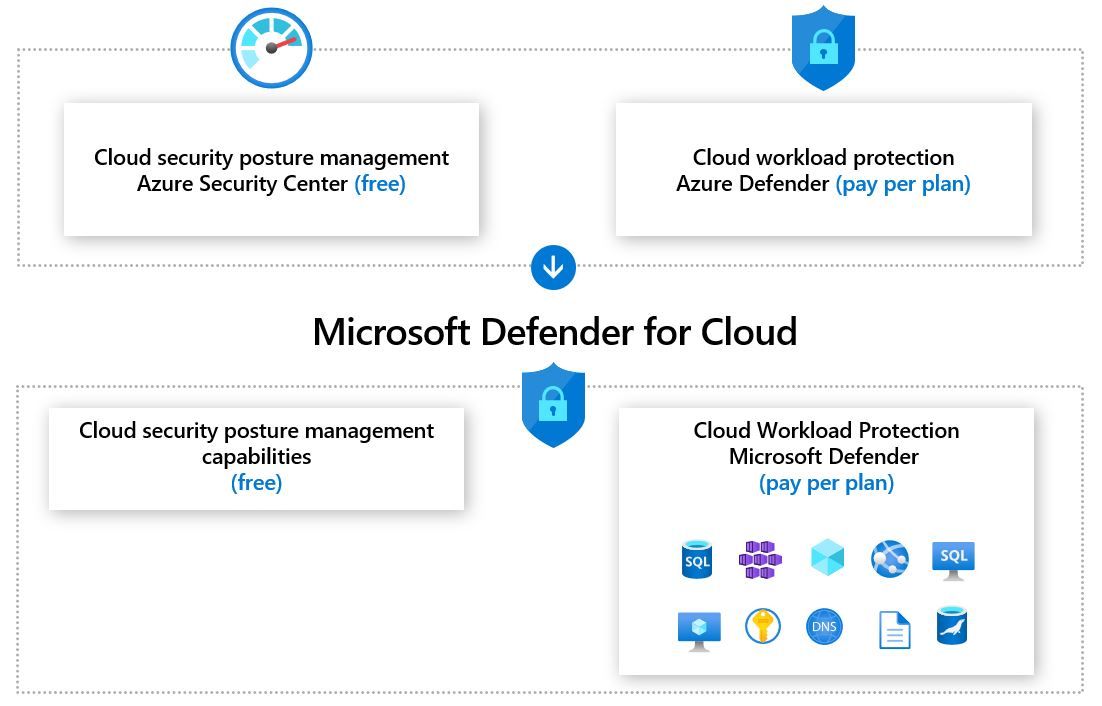
The complete cloud-native application protection platform (CNAPP), Azure Defender (formerly Microsoft Defender for Cloud), protects your cloud-based apps.
It combines CSPM, CWPP, and DevSecOps capabilities to improve your company’s security procedures.
Azure Defender safeguards different Azure Vulnerability Scanning assets like servers, containers, storage, and databases while providing helpful insights into your security posture and recommending securing resources.
Unified security management, which enables the management of threat detection, vulnerability assessments, and advanced controls across Azure, AWS, GCP, and on-premises systems, is one of Azure Defender’s primary benefits.
Azure Defender can benefit from improved dashboard integration, reduced solution complexity, increased monitoring capabilities for virtual machines running on different clouds, adaptable use cases, lower resource usage, integration of external threat intelligence, improved support, and feature bundles.
Features
- Alerts and real-time threat detection
- Constant vulnerability management and scanning
- Advanced defense against sophisticated assaults
- Practical trends and ideas for security monitoring
- Monitoring compliance and observance of industry norms
What is good?
- Integrated Security Insights
- Compliance Monitoring
- Integration with Azure Services
What could be better?
- Greater Customization
- Enhanced Automation
- Improved Response Orchestration
3. OpenVAS
A potent azure vulnerability scanning tool known for its extensive scanning capability is called OpenVAS Scanner.
It performs complete scans utilizing the for-profit Greenbone Enterprise Feed or the open-source Greenbone Community Feed, providing the most recent vulnerability data.
With new modules, an intuitive web interface, and the Greenbone Security Manager, OpenVAS has developed.
The Azure vulnerability scanning community has grown thanks to Greenbone’s dedication to openness.
A user-friendly installation process, a precise input method, thorough Azure web app vulnerability scanning, fewer false positives, increased compatibility, reliable PDF report generation, an updated user interface, and clear device-specific threat information on the dashboard are all areas where OpenVAS can be improved.
Features
- Comprehensive vulnerability scanning and evaluation
- Determines and reports security flaws in networks and systems.
- A broad range of target systems and technologies is supported.
- Delivers thorough reports with recommendations for corrective action and severity ratings.
- Flexible, actively maintained, open-source software that benefits from community assistance
What is good?
- Detailed Reports and Recommendations
- Platform Compatibility
- Open-Source and Actively Maintained
What could be better?
- False Positive Reduction
- Integration Capabilities
- Scanning Performance
4. Nessus

Tenable’s Nessus is a well-known Azure vulnerability scanning and cybersecurity solutions industry standard.
Focusing on external attack surface scanning and cloud infrastructure scanning, it provides comprehensive solutions for evaluating the modern threat surface.
Nessus offers user-friendly features, flexible reporting, real-time data, and a grouped view for effective remediation.
Nessus may increase its custom reporting capabilities, solve slowness with big datasets, optimize resource usage, boost scan status visibility, and streamline setups for a better user experience.
Features
- Robust vulnerability evaluation and scanning.
- Finds and discloses security flaws in applications, systems, and networks.
- Various platforms and technologies are supported.
- Provides thorough reports with recommendations for corrective action and severity ratings.
- Provides customization possibilities and a user-friendly interface for scanning setups.
What is good?
- Robust Vulnerability Scanning
- Diverse Platform Support
- Active Community and Support
What could be better?
- User Interface Enhancement
- Scan Performance Optimization
- Reporting Flexibility
5. Qualys Cloud Platform
Qualys Security Configuration Assessment (SCA) automates the configuration assessments of global IT assets.
Organizations can assess, report, monitor, and fix security-related configuration issues using Qualys SCA as an add-on for Qualys Vulnerability Management, Detection, and Response (VMDR).
Some areas covered include task scheduling, scan frequencies, user interface improvements, and excellent documentation. While performing scans, some users have noted confusion and outages, while larger organizations have voiced worries about cost.
Features
- comprehensive scanning and management of vulnerabilities
- Threat intelligence and ongoing monitoring for proactive security
- Asset tracking and inventory are essential for efficient asset management.
- Regulation adherence through the administration of compliance and policies
- Analytics and reporting for practical security knowledge
What is good?
- Comprehensive Vulnerability Management
- Asset Inventory and Tracking
- Strong Community and Support
What could be better?
- User Interface Enhancement
- Performance Optimization
- Integration with DevOps Processes
6. Rapid7 InsightVM
A complete Azure vulnerability scanning and risk management solution is InsightVM by Rapid7. It offers a glimpse of your ecosystem in real-time, thanks to ongoing endpoint monitoring with the Insight Agent.
Collaboration with IT operations and developers is made simple through shared visibility and automation, guaranteeing compliance and secure setups.
Cloud services, virtual infrastructure, and container repositories are effortlessly integrated with InsightVM.
Pricing, customer service, scanning results accuracy, user interface, scan execution speed, noise tuning, filtering options, device removal, database stability, and scheduling functionality may be improved.
Features
- Practical risk assessment and vulnerability scanning
- Ongoing surveillance and immediate threat detection.
- Complete awareness of resources and their weaknesses
- Tracking and prioritizing remediation for efficient risk reduction.
- Integrated processes for security tools for improved security
What is good?
- Actionable Insights
- Integration with Security Tools
- Provides real-time threat detection
What could be better?
- Simplified Deployment
- Enhanced Automation
- Increasing automation capabilities
7. Tenable.io

A risk-based technology called Tenable Vulnerability Management offers complete network awareness, anticipates assaults, and enables timely solutions to significant vulnerabilities.
Real-time reporting, asset visibility, automatic prioritization, threat intelligence, and thorough Azure vulnerability screening are all included. Tenable.io uses Tenable Nessus’ technology for cloud-based administration.
Tenable.io Azure vulnerability scanning can be improved by reducing the complexity of the initial setup, boosting support capabilities, enabling greater dashboard customization, providing integration tools, changing pricing, enhancing executive-level reports, and streamlining the license renewal procedure.
To improve the user experience, changes can be made to asset turnover, unclear interfaces, scan speeds, and resource usage.
Features
- For proactive security, complete vulnerability scanning and management.
- Threat detection and response capabilities in real-time
- Actionable knowledge and suggestions for repairing vulnerabilities well
- Asset tracking and discovery for better asset management and visibility
- Integration with other security technologies and workflows makes collaboration and streamlining of security activities possible.
What is good?
- Efficient asset discovery and tracking features
- Integrates with other security tools
- Strong community and offers reliable support
What could be better?
- Adding more flexibility to scan
- Introducing advanced analytics features
- Further reducing false positives
How to choose the best Azure vulnerability scanning tool?
1. Comprehensive Scanning Capabilities:
Choose an Azure vulnerability scanning tool that has a variety of scanning options, like automated scanning, deep scanning, and prioritize vulnerabilities by scan. This will provide a holistic testing coverage of your Azure data security measures.
It should be able to check for various flaws, including network flaws, Azure web app flaw scanning, database flaws, and more.
2. Continuous Scanning and Monitoring:
Pick an Azure vulnerability scanning tool with the capability for continuous scanning and monitoring.
A scanner that can regularly scan your Azure vulnerability-checking assets and notify you of new vulnerabilities is essential because exposures can appear at any time.
This keeps you on guard and defends your systems from the most recent dangers.
3. Integration with Azure Services:
Choose an Azure vulnerability scanning tool that works with Azure services seamlessly.
This integration allows the scanner to access and examine your Azure infrastructure effectively.
Thanks to the integration, the scanner can now use Azure-specific capabilities and APIs for enhanced vulnerability identification.
4. Scalability and Performance:
Think about the an Azure vulnerability scanning tool’s performance and scalability. It should be capable of scaling up as your infrastructure expands and handling massive Azure deployments.
The vulnerability scanning for Azure should also have low false-positive and false-negative rates to provide reliable vulnerability identification and lower the possibility of overlooking critical issues.
5. Compliance and Regulatory:
Check if the Azure vulnerability scanning tool complies with the compliance and regulatory standards that apply to your firm.
This is especially crucial if you work in the heavily regulated healthcare, banking, or government fields.
To assist you in maintaining compliance with the relevant security standards, the scanner should support industry-specific standards like HIPAA, PCI DSS, ISO 27001, and others.
Why is Astra Vulnerability Scanner the Best Scanner?
- Runs 8000+ tests with weekly updated scanner rules
- Scans behind the login page
- Scan results are vetted by security experts to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities from one place.
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Integrates with Slack and Jira for better workflow management
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

What is the method for vulnerability scanning for Azure?
Follow these suggested procedures to scan Azure for vulnerabilities successfully:
- Start using the automatic vulnerability scanning software the Azure Security Center suggests. Conduct evaluations on SQL servers, container images, and virtual machines. Use third-party products for online applications and network devices. JIT provisioning should be used for the scan account.
- To automatically update your Linux and Windows OS, use automated operating system patch management utilizing Azure’s “Update Management” feature.
- Introduce an automatic patch management program for external software. Utilize Update Publisher and System Center Configuration Manager to patch machines with customized updates.
- To confirm remediation, compare back-to-back vulnerability scans. At regular intervals, export and compare the findings of the scan. For historical scan data, use the site for the Azure Security Center.
- Prioritize remediation using a process of risk rating. Use a well-known risk scoring program, such as CVSS, or rely on ratings provided by third-party scanning tools.
Although you can search for vulnerabilities and take steps to mitigate them, it’s best to abide by the rules established to enhance the organization’s overall security architecture.
Importance of Azure Vulnerability Scanning Tools
1. Identify Vulnerabilities:
Regular vulnerability management tool scanning identifies potential security holes that attackers could exploit. It helps you swiftly resolve these issues, protecting private client information and upholding confidence.
2. Protect Customer Data:
A data breach has serious repercussions, including harm to reputations and financial losses. Customer data is kept secure thanks to effective vulnerability management procedures that help stop unauthorized access and guard against potential exploits.
3. Stay Ahead of Emerging Threats:
Cyber threats are ever-changing. You may lower your risk of new attack vectors and developing cybersecurity risks by actively monitoring and patching vulnerabilities.
4. Proactive Risk Management:
The chance and effect of security events are considerably reduced when vulnerabilities are fixed before they are exploited. Being proactive reduces operational disruptions and safeguards the reputation of your company.
5. Enhance Security Posture:
Azure vulnerabilities are scanned regularly, and corrective actions narrow the attack surface while strengthening your overall security policies. You build a strong defense against potential breaches by consistently enhancing your security posture.
Features of Azure Vulnerability Scanning Tools
1. Asset Discovery:
As your watchful monitor, the vulnerability scanning for the Azure tool continuously monitors and detects dangers throughout your organization.
Your software programs, digital certificates, hardware, firmware, and browser extensions are all visible in real-time.
This increased visibility allows you to monitor and evaluate your essential assets quickly.
2. Vulnerability Assessment:
In Azure vulnerability scanning tools, built-in and agentless scanners provide advanced vulnerability and configuration assessments.
Utilize the capability to design flexible security baseline profiles to assess risk compliance against well-known standards.
Learn how to run authenticated Windows device scans, obtain visibility into the setup of your network shares, and find software vulnerabilities.
3. Misconfiguration Detection:
When finding misconfigurations that expose your company to dangerous cyber risks, Azure’s tools have your back.
They carefully examine any security holes that might be present in software, browser extensions, digital certificates, hardware, and firmware.
Avoid compromise by quickly identifying potential weaknesses and immediately addressing them.
4. Security Patch Management:
Maintain a competitive edge. You can count on Azure web app vulnerability scanning and vulnerability detection tools to keep track of essential software changes.
They ensure your systems are updated and protected against known vulnerabilities by handling everything from installations to uninstalls and fixes.
No more restless nights worrying about how strong your fortifications are.
5. API Integration:
Utilize your automation potential by smoothly integrating Azure’s solutions with your security architecture using their rich APIs.
Efficiently orchestrate vulnerability evaluations and mitigation processes by leveraging automation. Accept a future in which your security operations are modern, effective, and efficient.
Conclusion
In conclusion, vulnerability scanning for Azure is critical to locating and resolving security flaws in networks and computer systems.
Organizations may proactively identify vulnerabilities, assess risks, and swiftly implement corrective actions using Azure’s extensive tools and solutions.
Azure equips businesses to improve their cybersecurity and safeguard important assets with tools including asset discovery, vulnerability assessment, misconfiguration detection, and security patch management.
Azure vulnerability scanning allows effective and efficient management by integrating with current security infrastructure and applying risk-based prioritization.
Frequently Asked Questions
How do I scan for vulnerabilities in Azure?
Using Astra Security Center, you can do a vulnerability scan in Azure. It offers features for ongoing monitoring, threat detection, and vulnerability evaluation. To help you improve the overall security of your Azure environment, it analyzes your resources, evaluates their security posture, and offers recommendations to remedy vulnerabilities.
What are the types of vulnerability scanning assets
Azure vulnerability scanning tools can scan various assets, including VMs, containers, App Services, AKS, databases, NSGs, storage accounts, and more, depending on which scanning tool you use or integrate.
What is Web Application Security in Azure?
Security features such as Web Application Firewall (WAF) for defending against common attacks, DDoS Protection for guarding against denial-of-service attacks, Security Center for centralized monitoring and threat detection, Azure Active Directory (Azure AD) for identity and access management, Key Vault for secure key storage, network security groups for detailed network control, and routine patching updates for core components are all included in Azure web app vulnerability scanning tools.