With the rapidly expanding omnipresence of cloud-based solutions in the modern business landscape, discussions on Azure security best practices have never been more pertinent.
80% of companies have experienced at least one cloud security incident in the last year — a number that dramatically underscores the importance of stringent network safety measures.
In this article, we serve as your guide to bolstering cloud security, diving into Azure NSG best practices, Azure network security group best practices, Azure networking best practices, and Azure policy best practices adding one more layer each time we telescope out for a wider view of a robust and unbreachable Azure defensive core.
Utilizing strategic defenses is essential in thwarting cybercrime, which can compromise your business’s finances and reputation.
Action Points
- Azure network security acts as a protective wall for Azure services, keeping out cyber threats.
- Best practices include encryption, access management, traffic monitoring, and Azure Security Center for comprehensive protection.
- Monitoring tools like Azure Monitor and Azure Security Center are vital for maintaining network security.
Let’s dig into how you can create a powerful Azure network fortification system.
What is Azure Network Security?
Azure Network Security, in simple terms, is the guardian of your Azure services. Imagine it as a robust castle wall, that keeps undesired visitors—cyber threats and vulnerabilities—from infiltrating your business dominion, that is, your private digital resources and applications.
It involves applying a set of well-thought-out Azure network security best practices that determine what traffic is allowed into the ‘castle’. These configurable Azure network security group best practices include restrictions on port and protocol usage to ensure only safe connections.
Also, azure networking best practices and Azure policy best practices become the guiding beacon in the fog of cyber threats, helping your business monitor, analyze, and react swiftly to prevent breaches.
For example, encrypting data is an integral Azure NSG best practice to provide a quick reaction force against external threats. Building on the castle analogy, proposed Azure networking best practices envision your(server) guard patrolling round the clock.
Why is Astra Vulnerability Scanner the Best Scanner?
- Runs 8000+ tests with weekly updated scanner rules
- Scans behind the login page
- Scan results are vetted by security experts to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities from one place.
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Integrates with Slack and Jira for better workflow management
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

What are Azure Security Best Practices?
1. Secure your data:
Store all sensitive information in the Azure key vault. This provides an extra layer of network security that cybercriminals would find challenging to bypass. This is an essential step in Azure data security.
2. Manage access:
Elaborate on ‘who’ has ‘what’ kind of access and when. Using Role-Based Access Control (RBAC), you can assign certain permissions to users or groups.
3. Traffic monitoring:
Use Azure’s Network Watcher to keep track of your network performance and security. It helps detect any unusual patterns suggesting a breach.
4. Network Security Group:
Make the most of Azure network security group best practices; for instance, choosing high-security configurations over defaults.
5. Set up a firewall:
Azure network security employs a highly effective Azure Firewall, designed to filter and analyze both inbound and outbound traffic, enforcing predefined network rules.
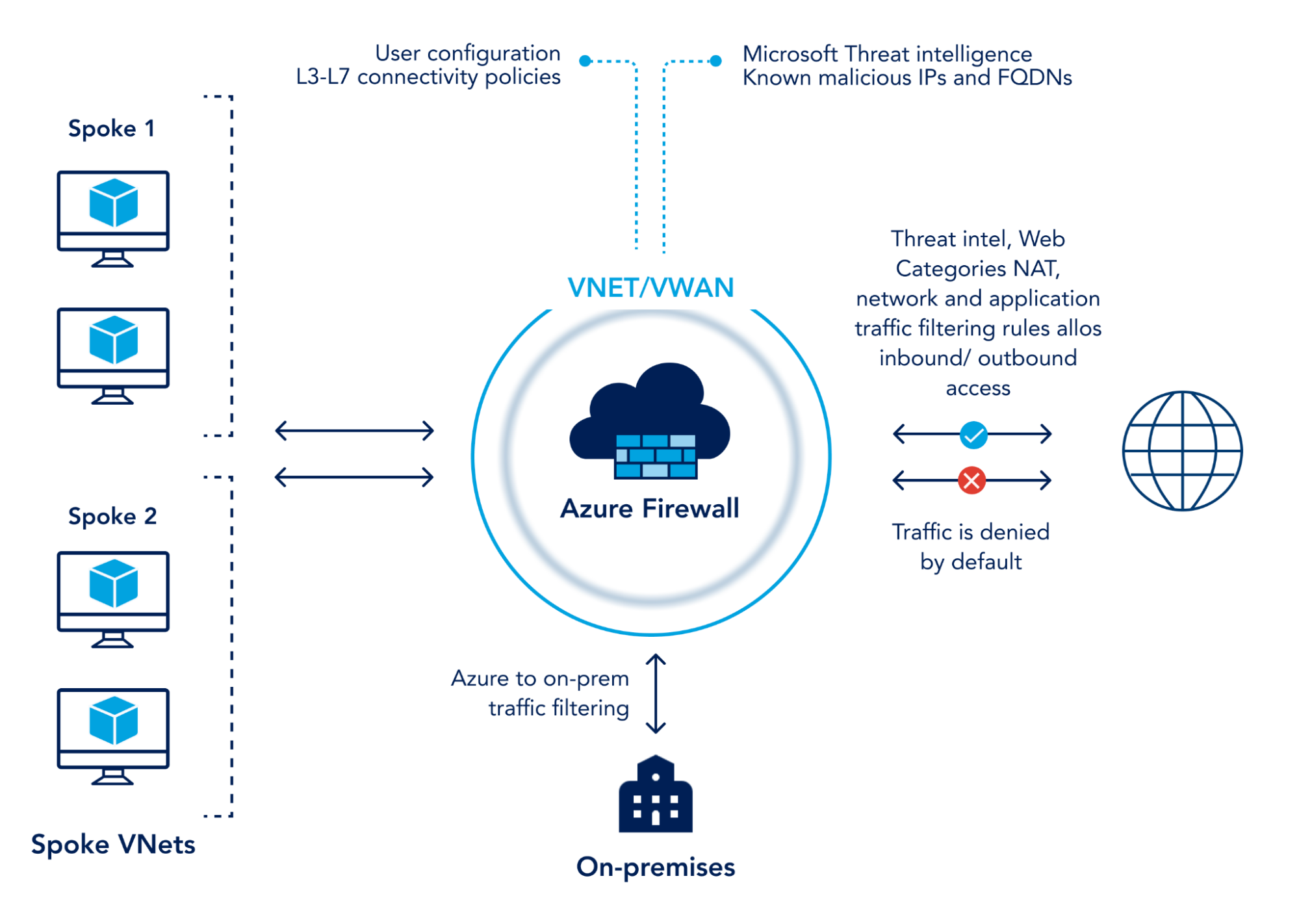
6. Encryption methods:
Use Azure’s data encryption capabilities at rest and in transit for a tightly-knit security net against breaches.
7. Consistent auditing:
Institutionalize Azure policy best practices by going for continuous auditing of your Azure resources and settings, aiding in anticipatory action.
8. Use of VPNs:
With Azure VPN Gateway, you can establish secure, cross-premises connections.
9. Incorporate Zero Trust model:
Implementing the Zero Trust model in your Azure strategy allows verification before granting any access.
10. Multi-factor Authentication:
Extra layers of security like multi-factor authentication can reduce the likelihood of intrusion. As the old adage goes, ‘Prevention is better than cure.’ With ever-growing advancements in destructive cybersecurity attacks, a single password-based gateway can make your entire data realm vulnerable.
11. Advanced Threat Protection:
Leverage Azure Security Center’s Advanced Threat Protection to identify, detect, and respond swiftly to any upcoming threats to your Azure infrastructure.
12. Regular Updates and Patches:
Making sure that all your Azure resources and services have the latest updates is an Azure NSG best practice, as they often come with improved security protections.
13. Logging and event data:
Logging and recording even mundane events can provide insightful data in the long run for tracing anomalies, hence it’s counted under both Azure networking best practices and Azure policy best practices.
14. Secure Coding Practices:
Adopt secure coding practices to eliminate software flaws that often bring about breaches. Train your developers in Secure Code principles.
15. User Awareness and Training:
Often, the weakest link in security is not technology but humans. Conduct regular awareness sessions and training to ensure your workers are educated about security threats and best practices.
16. Leverage Azure Security Center:
The Azure Security Center provides a consolidated view of the security status of all your resources providing faster detection and responses to possible threats.
17. Deny by Default Strategy:
A ‘deny all, allow some’ approach restricts all traffic, except those absolutely necessary. Every permitted connection must be purposeful and justified.
18. Intrusion Detection and Prevention Systems (IDPS):
Azure offers Security Center’s Fusion technology, cinching a comprehensive view over your applications, network, and infrastructure.
19. Regular Bouquets and Bricks Testing:
Bouquets testing (‘pat-on-the-back’ checks) ensures services work as they should, while Bricks testing (‘faux brick thrown at glasses’ checks) finds servers open to the web which must be closed. Scheduled tests like these shore up your Azure defense.
20. Azure Policy Monitoring:
Employing Azure Policy service for policy definition and enforcement alongside monitoring allows tracking of compliance and identification of non-compliant resources, enabling swift remediation actions.
21. Continuous network performance diagnostics:
Constant monitoring of the Azure network through Azure network performance diagnostic tests, can identify bottlenecks and optimize performance.
22. Leveraging Machine Learning:
Azure Machine Learning services enable the parsing and understanding of threat patterns, reputation analysis, and predictive analysis into your Azure security measurements. By examining millions of data points, these services alert you to potential security threats before they manifest.
While this is by no means an exhaustive list — there are always new techniques and technologies emerging in the realm of cybersecurity — these best practices act as a touchstone for securing your cloud services.
Maintaining Security with Monitoring Tools
In this section, we will delve into how monitoring tools aid in maintaining Azure’s network security:
1. Use Azure Monitor
Offering insights and detecting performance issues quickly is key. Azure Monitor collects and analyzes data, allowing you to spot trouble early on.
2. DevOps practice teams
They are better suited to fix potential issues when they practice DevOps methodologies. Utilizing Azure DevOps sole unit providing end-to-end development for optimal performance.
3. Leverage Azure Service Health
This essential gives real-time alerts about Azure Service incidents affecting your resources and maximizing uptimes.
4. Diverse Classification Suite
SharePoint Online’s eDiscovery tool can locate, preserve, and export data again of higher importance to business practices.
5. Azure Policy Remediations
Make use of a service that not only detects breaches but remediates too.
6. Implement RBAC Monitoring
Role-Based Access Control (RBAC) ensures that only authorized parties get access to specific Azure resources. It limits unnecessary access, curbing potential breaches.
7. Network Watcher integration
Extensive network traffic analytics using Azure’s Network Watcher, which integrates smoothly to aid IT teams in identifying suspicious activities quickly.
8. Azure Security Center for continuous assessment
Monitoring highlights vulnerability patterns over time continuously for easy assessment, isolation, and resolution.
9. Activity Logs
Keeping detailed logs aids in retrospectively diagnosing issues and mirrors the strength of security adherence.
Empower Your Network Security with Astra Security
Don’t compromise your network’s safety when Astra Security is at your disposal!
Be prepared for challenges and turn the cybersecurity tide to your advantage.
Discover a reliable ally in safeguarding your data with Astra’s comprehensive cybersecurity services.
Our team specializes in Azure security and focuses on bolstering your resources with meticulously outlined strategies.
With us, it’s not just about timely threat interception but also ensuring holistic preventive steps- education, robust coding, intrusion detection, and regular diagnostics, amongst other robust security measures. Stay a step ahead of potential threats with Astra Security, turning vulnerability into indomitable resilience.
Learn more: www.getastra.com
Conclusion
To sum up, Azure security best practices are the fortress against cyber threats, with the above outline of essential security best practices such as covering data encryption, access management, continuous monitoring, and threat detection. Furthermore, use monitoring tools like Azure Monitor, DevOps practices, Azure Service Health, and others to help maintain the security posture of your Azure environment. Get started today!
FAQs
What are the three types of Azure?
Azure encompasses three key service models: Infrastructure as a Service (IaaS), which offers virtualized computing resources; Platform as a Service (PaaS), providing a developer-friendly platform for app deployment; and Software as a Service (SaaS), delivering software applications accessible through web browsers, streamlining accessibility and management.