In today’s rapidly evolving digital landscape, businesses are increasingly turning to cloud solutions to power their operations, streamline processes, and drive innovation. Among the leading players in this domain, Microsoft Azure stands out as a versatile and robust cloud platform that offers a wide array of services to meet diverse business needs. However, with great power comes great responsibility, and ensuring your Azure cloud’s security is paramount.
This article explores the top 7 best Azure security tools and provides you with the resources required to ensure maximum security of your Azure infrastructure.
Top 7 best Azure security tools
- Astra Security
- Azure Active Directory
- Azure Sentinel
- Azure Information Protection
- Azure Firewall
- Azure Key Vault
- Azure Advanced Threat Protection (ATP)
Astra Security

Astra’s Azure security solutions use automated controls, ongoing monitoring, and advanced threat intelligence to protect cloud infrastructure and data from online threats.
Astra’s security engine covers all the fundamental tests necessary to achieve ISO 27001, HIPAA, SOC2, or GDPR compliance.
Through Expert manual and automated Azure penetration testing services, Astra Security continuously tests your organization’s security for vulnerabilities.
Astra Security’s services can help identify vulnerabilities that may impact compliance standards, enabling you to take appropriate measures to address them.
Additionally, it offers secure configuration management, ensuring that Azure resources are correctly set up and compliant with security best practices.
Features
- Secure Cloud Infrastructure: Built-in hardware and firmware security controls with DDoS protection
- Comprehensive Cloud Pentest: With Astra, automation and manual pentests will become regular parts of maintaining the security of your Azure infrastructure.
- Threat Response: Identify and respond to new threats with global intelligence.
- Threat Detection: Insights from data analysis enable faster threat detection.
What is Good?
- Multi-layered Security
- Quick protection with built-in controls across Azure
- Advanced-Data Analysis
- Real-World Testing
- Actionable VAPT reports
- Conduct more than 3000 tests
- Continuous Offensive Security
Disadvantages
- No free trial
Azure Active Directory (AAD)
A component of Microsoft Entra, Azure Active Directory is an enterprise identity service that offers single sign-on, multi-factor authentication, and conditional access to protect against 99.9% of cyberattacks.
Governance involves granting timely and appropriate resource access to authorized individuals as needed.
Balancing user experience and security, robust authentication, and adaptive access policies safeguard resources and data.
Enhance visibility and control by centrally managing identities and user access to applications, whether on-premises or cloud-based.
Features
- Streamlined Access: Enhanced remote application accessibility.
- Unified Control: Total Environment Visibility and Control
- Authorization: access control through governance
What is good?
- Efficient Single Sign-On (SSO) mechanism.
- Intelligent access governance with automation.
- Strengthen and streamline identity infrastructure using Entra.
Disadvantages
- The group size limit hampers large organizations.
- Limited flexibility for specific needs.
- Limited accessibility to advanced features.
Azure Sentinel

Employ advanced security analytics to optimize operations and support scalable business expansion.
Use an advanced SIEM to monitor the system for sophisticated threats and proactively identify, investigate, and mitigate them.
Eliminate legacy SIEM setup and maintenance to achieve a cost reduction of up to 48% while utilizing elastic scaling to meet changing security requirements.
Use the integrated connector to collect data from Azure, on-premises systems, and multiple clouds quickly and easily, improving accessibility and analysis.
Features
- Threat Analytics: Intelligent threat detection for proactive security.
- Rapid Incident Response: Automated task orchestration enables swift response through streamlined workflows.
- Integrated Log Analysis: Seamless log import and correlation for heightened intelligence capabilities.
What is good?
- It uses advanced threat detection to identify unknown threats and anomalous insider behavior.
- Aggregate data from heterogeneous environments.
- AI-driven scalability enhances activity analysis capabilities.
Disadvantages
- Challenges in export, stability, and compatibility.
- On-premises log source limitations.
- Disruptions caused by mobile alerts.
Azure Information Protection
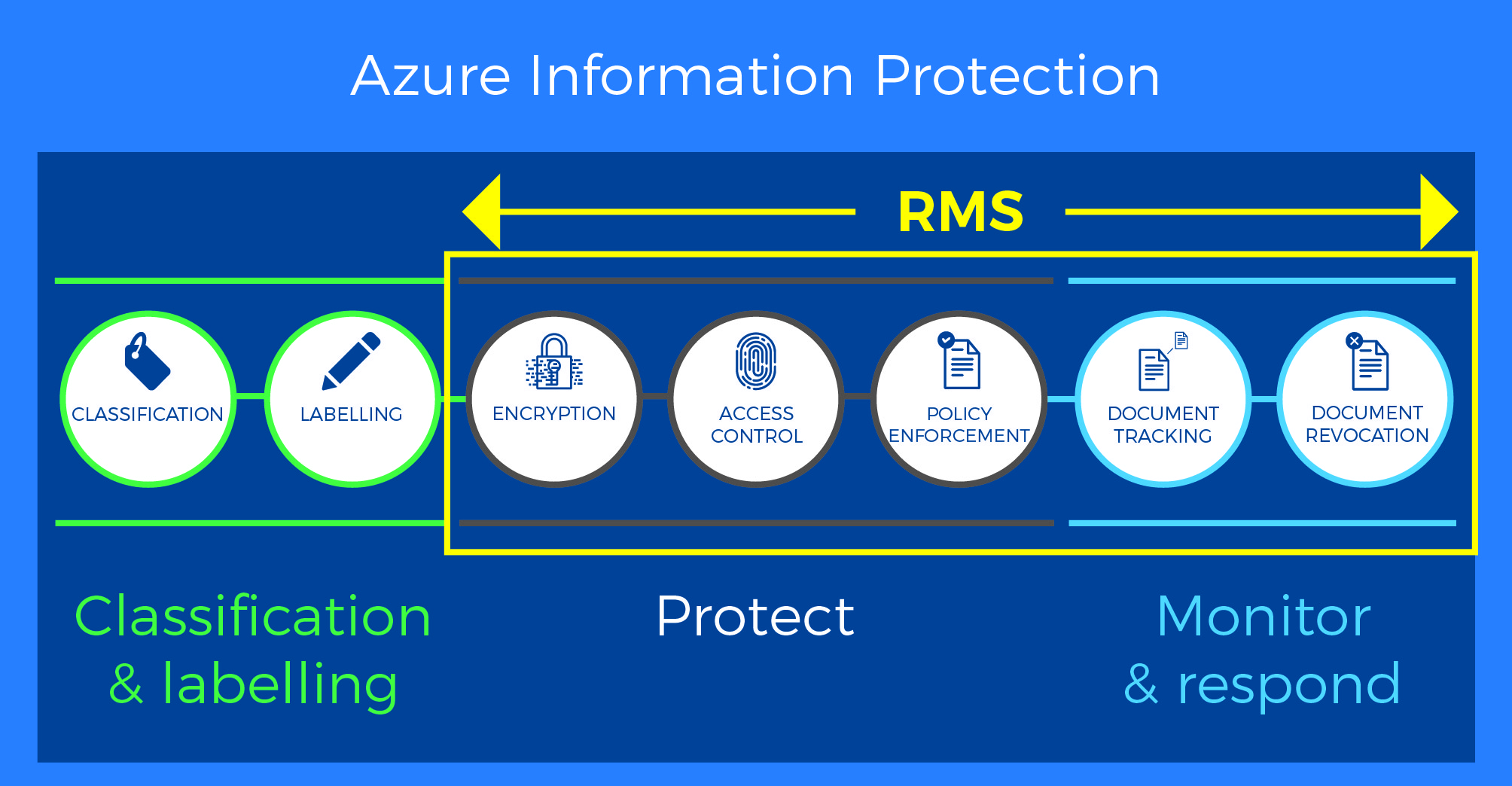
No matter where data is stored or with whom it is shared, Azure Information Protection can improve data protection at all times with features like simple classification, embedded labels, and permissions.
Applications like Microsoft Office and others have built-in data classification and protection controls, so you can quickly secure the data you are working with.
Provides comprehensive external data security for emails, documents, and sensitive information shared beyond the company’s boundaries.
Features
- Data Classification: Automated Protection and Labeling
- Persistent Protection: Continuous data safeguarding
- Activity Monitoring: Track, analyze, and revoke access.
What is good?
- Controlled access and permissions.
- Seamless integration of data protection mechanisms.
- Versatile critical management solutions are available.
Disadvantages
- Windows-only Office support
- Reduced versatility in supported formats.
- Technical complexities in meeting data protection compliance.
Azure Firewall
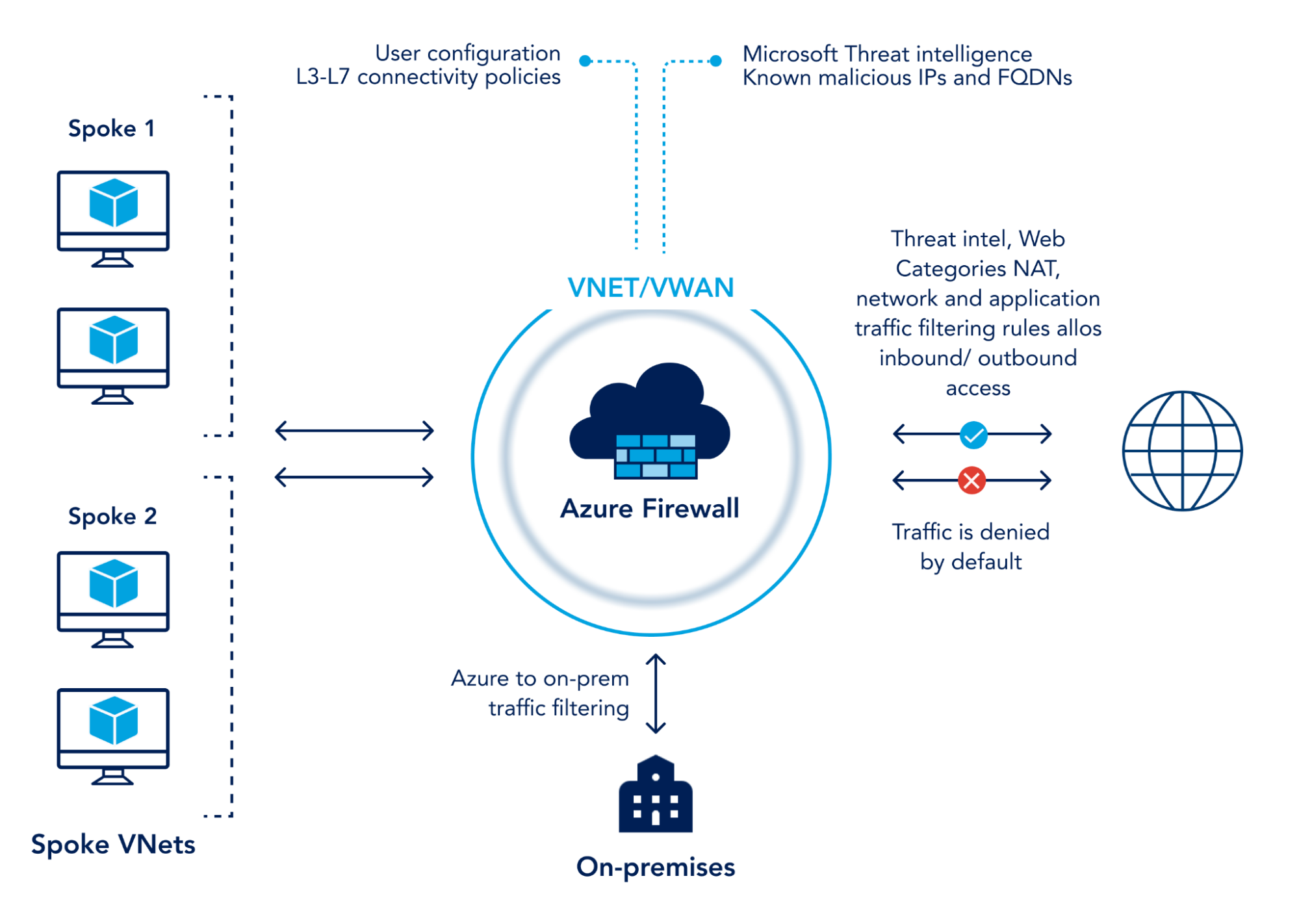
Azure Firewall is a managed cloud-based network security service that safeguards your Azure Virtual Network resources.
You can create, enforce, and log application and network connectivity policies across subscriptions and virtual networks with the help of the stateful firewall service, which comes with built-in high availability and unrestricted cloud scalability.
To protect against evolving threats and zero-day vulnerabilities, Azure Firewall uses real-time security signals from various sources and Microsoft threat intelligence.
Features
- TLS Inspection: Prevent malware transmission in encrypted connections.
- Centralized Management: Manage security rules across virtual networks.
- Secure Outbound Traffic: Decrypt, check, and encrypt outbound traffic with URL filtering and web categories.
What is good?
- Automated alerting and blocking against malicious traffic.
- The firewall system is designed with scalability and high availability features to accommodate growing demands and minimize downtime.
- The firewall system is designed to scale quickly and maintain high availability during operation.
Disadvantages
- Inefficient scaling for larger enterprises.
- Inconsistent service speed between regions.
- It complicated the firewall rule migration process.
Azure Key Vault
Azure Key Vault is a cloud service for safely keeping and accessing secrets.
Anything you want to strictly control who has access to, such as API keys, passwords, certificates, or cryptographic keys, is considered a secret.
Managing hardware security module (HSM) pools and vaults are the two container types that the Key Vault service supports.
Software-based keys, secrets, and certificates can be stored in vaults with HSM backup.
Features
- Key and Password Security: Enhanced control and protection
- Certificate Management: Task automation ensures streamlined efficiency and effectiveness.
- Azure resources: VMs, storage, web apps, databases, and networks.
What is good?
- Quick deployment and data importation.
- FIPS 140-2 Level 2 and Level 3 compliance
- Application access with indirect key usage.
Disadvantages
- Limited UI usability.
- There need to be more detailed key expiration notifications.
- Complex retrieval process and certificate authentication.
Azure Advanced Threat Protection (ATP)
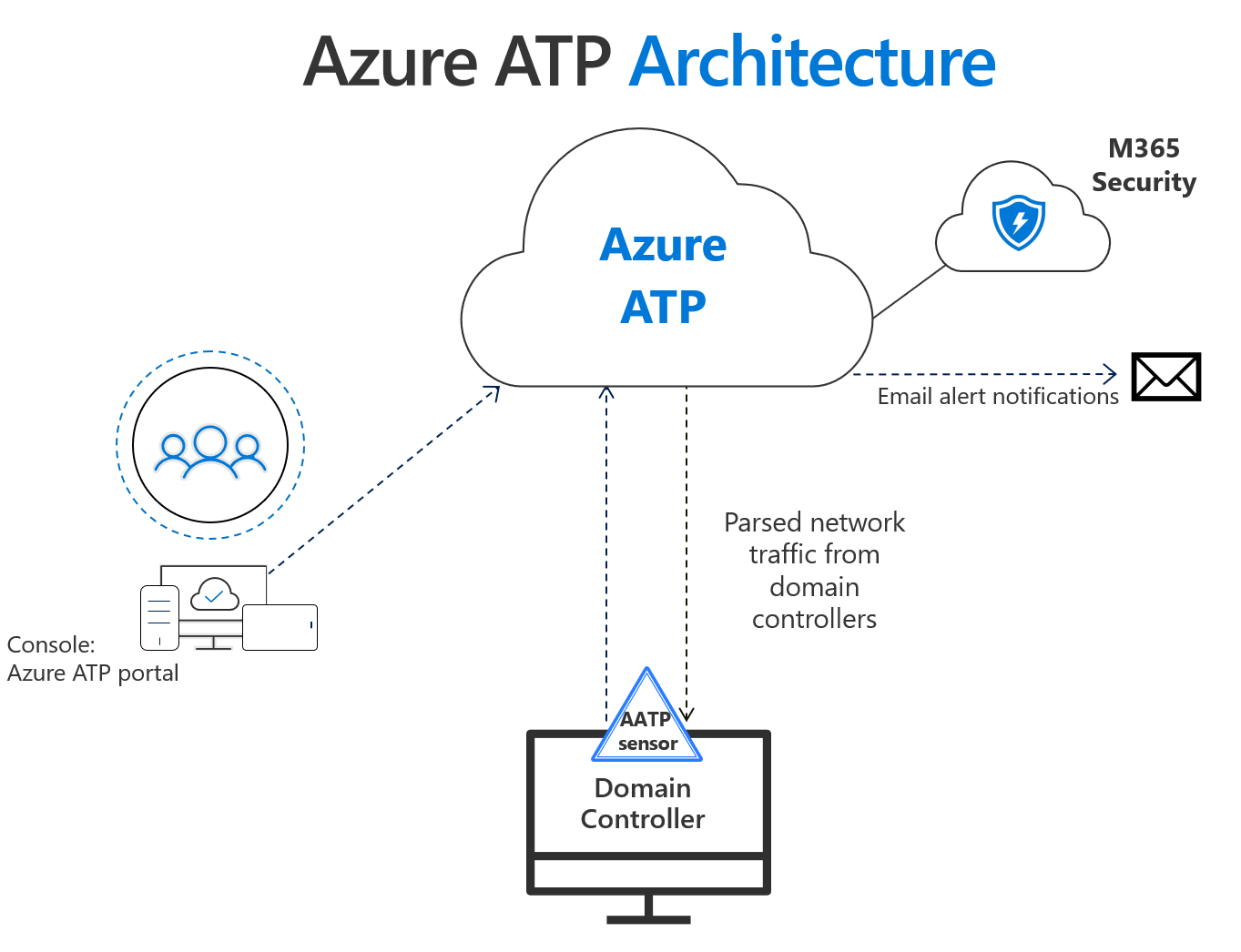
Integrated with Windows Defender ATP, Azure ATP detects advanced attacks using cloud and on-premises signals, reducing false positives and facilitating end-to-end investigations.
Azure ATP offers threat protection for security teams working in hybrid environments by precisely identifying complex attacks.
Increase threat visibility and detection capabilities by using Windows Defender ATP to track and carefully monitor numerous entry points.
Features
- Robust Security Analytics: Supports demanding enterprise workloads
- Behavioral Analytics: Detects suspicious user and device activity.
- Unified Threat Intelligence: Integrate intelligent capabilities across cloud and on-premises environments.
What is good?
- Enhance Active Directory credential security.
- Clear attack timeline for quick triaging.
- Detects advanced attacks across cloud and on-premises.
Disadvantages
- Potential complexity leads to increased false positives and negatives.
- Possible log collection effectiveness limitations.
- Possible compliance and privacy drawbacks.
How to choose the best Azure security tools?
- Security Requirements
Before selecting Azure security tools, analyze your unique security needs. Evaluate threat detection, vulnerability scanning, and identity management to match an organization’s risk profile.
You can achieve complete cloud resource, data, and application protection by coordinating security requirements with Microsoft Azure tools.
- Integration with Azure Services
A seamless integration of Azure security services is necessary for adequate security in Azure.
To find Azure security tools, look for those that can connect to essential Azure security services like Azure Security Center and Azure Active Directory.
Through this integration, your Azure environment can be monitored and managed centrally, allowing for a unified approach to security.
Analyze whether the tools offer APIs or extensions to simplify integration with current Azure security solutions or workflows.
- Scalability and Performance
As your cloud infrastructure expands, choosing Azure cloud security tools that can scale and perform well is critical.
Scalability, data processing, and resource adaptability should all be considered when choosing Azure security tools.
Assess performance metrics (response times, throughput) to evaluate tool scalability and system impact.
- Compliance and Auditing
Many organizations place a high priority on maintaining compliance with pertinent laws and business standards.
Your organization must follow a compliance framework like GDPR, HIPAA, or ISO 27001, so ensure the Azure security tools you use comply with them.
To help you meet your regulatory obligations, look for features like compliance evaluations, audit logs, and reporting capabilities.
- Vendor Reputation and Support
Consider vendor expertise, reputation, compliance, integration, and updates when choosing Azure security tools.
Analyze their availability of documentation, training resources, community support, and the support channels they provide.
A reliable vendor will provide ongoing product updates, prompt security patches, and attentive customer support to address potential issues or problems.
What is the importance of Azure security tools?
- Data Protection
Sensitive data is well protected by Azure Security Tools like Azure Information Protection (AIP) and Azure Key Vault.
Data classification and encryption by AIP and critical security by Key Vault help prevent unauthorized access and data breaches.
- Threat Detection and Prevention
Through the analysis and guidance of security logs, Azure Security Center offers advanced threat detection.
To reduce successful attacks, Azure Advanced Threat Protection monitors and defends against potential threats and identifies and responds to sophisticated attacks.
- Compliance and Regulatory Requirements
By conducting assessments, keeping track of them, and reporting, Azure Security Tools help with compliance.
Intelligent analytics from Azure Sentinel support regulatory compliance for GDPR, HIPAA, and ISO 27001 standards.
- Security Monitoring and Incident Response
To provide real-time insights, Azure Monitor centralizes security-related data.
Through guided investigations and alert visibility provided by Azure Security Center, businesses can effectively respond to security incidents, minimizing their effects.
- Secure DevOps
Azure DevOps and Azure Security Tools collaborate seamlessly to support secure DevOps procedures.
Azure DevTest Labs provide secure environments for development and testing, and the integration makes continuous security testing, code scanning, and vulnerability assessments possible.
Why is Astra Vulnerability Scanner the Best Scanner?
- Runs 8000+ tests with weekly updated scanner rules
- Scans behind the login page
- Scan results are vetted by security experts to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities from one place.
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Integrates with Slack and Jira for better workflow management
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

What are the features of Azure security tools
- Identity and Access Management (IAM)
- Conditional access policies provide granular access control based on the user, device, location, and risk.
- Using JIT access and auditing by PIM helps reduce the risk of unauthorized access for privileged roles.
- Network Security
- Managed network firewall services are available for Azure resources through Azure Firewall.
- As Azure DDoS Protection reduces DDoS attacks, it is possible to define and enforce network security policies while ensuring resource availability and uptime.
- Security Analytics
- The cloud-native SIEM tool Azure Sentinel gathers and correlates security logs from various sources, using advanced analytics and AI to identify threats, carry out investigations, and enable proactive threat response for businesses.
- Incident Response and Forensics
- Azure resources provide ongoing threat detection and security monitoring with AI-powered alerts.
- As well as supporting forensics and preventative security measures, Azure Monitor analyzes telemetry data for anomaly detection.
- Secure Development
- Secure artifact management, code scanning, and CI/CD pipelines with built-in security checks are all provided by Azure DevOps.
- The Azure Security Development Lifecycle (SDL) guides the development of secure applications, decreasing the likelihood of deploying insecure software.
How do Microsoft Azure security tools protect your cloud?
- Microsoft Defender for Cloud secures cloud-native apps, defends against contemporary threats, and mitigates risk in multi-cloud and hybrid environments.
- Azure Security Center provides threat intelligence, vulnerability scanning, and security policy management to monitor your environment continuously.
- Integrated security posture visibility across Azure, AWS, Google Cloud, and hybrid clouds
- You can detect and react to attacks in real-time, and it offers suggestions to strengthen your security posture.
- Context-aware cloud security allows for real-time security access and prioritization of the most critical risks.
- With MFA, conditional access, and privileged identity management, Azure AD provides secure identity and access management.
- An integrated extended detection and response (XDR) solution is used for multi-cloud workloads to prevent, detect, and respond to attacks.
- Azure Key Vault provides secure key and secret storage, and Azure Firewall and Azure DDoS Protection lessen network-level threats.
- Azure Sentinel also offers intelligent security analytics and automated response to quickly identify and address security incidents.
- Improved application development security through centralized insights across multiple pipelines and clouds
Cloud solutions like Microsoft Azure are rapidly used by organizations, making security a priority. Azure security tools provide full protection for data and applications. Every kind of business can make use of its many features, including its scalability, adaptability, privacy, and hybrid support. Proactive cloud penetration testing, clear allocation of responsibilities, stringent Identity and Access Management (IAM), and constant monitoring are all examples of best practices. Azure security tools enable Azure customers to confidently use the cloud, protecting their digital assets.
Frequently Asked Questions
What is the use of Azure?
Microsoft’s Azure is a cloud computing platform. It offers tools and services for creating, deploying, and maintaining infrastructure and applications. Users may create, host, and expand apps on Azure, store and analyze data, put security measures in place, and use cutting-edge technologies like AI and machine learning.
What is zero trust in Azure security tools?
A security system called Zero Trust in Azure makes no assumptions about the reliability of people, devices, or networks. Every access request is verified, activity is continuously watched, and the least privileged access controls are applied. Regardless of resources’ location or network limits, it focuses on identity verification, authentication, and continuous monitoring.
How can I begin using Azure Security Tools?
1. Create an Azure account.
2. Become familiar with the security tools that are accessible.
3. Determine your security requirements and choose the right technologies.
4. Go to the Azure manuals and tutorials for advice on deployment and configuration.
5. To safeguard your Azure environment, implement security procedures and continually monitor them.