Are you into web development? Or do you own a website? If yes, then chances are that you have used PHP at some point. PHP stands for Hypertext Preprocessor, is one of the most commonly used scripting languages for web development.
Well-known websites such as Facebook, Wikipedia, and WordPress are built using PHP as their back-end script language. However, as reported by Wikipedia, more than half of PHP websites are on discontinued and EOLed versions. Further, over 55% of PHP websites run versions prior to 7.2 and are not supported by The PHP Development Team.
Consequently, more than 55% of websites are susceptible to hacks. Updating to the latest version is always a recommendation, but that’s not all. You need to test your PHP for all the underlying vulnerabilities and loopholes. A careful PHP Penetration Testing is something we vouch for.
Today we will take PHP Penetration testing and break it bit by bit for your understanding. You will also get a close look at the steps involved in a PHP Penetration test and the tools that can come in handy for a manual PHP Penetration Test.
But first, let’s evaluate – How secure is PHP?
How secure is PHP?
PHP is just a scripting language and thus, security depends on the coder. Just like other programming languages, you can make your website insecure by writing insecure codes in PHP. Meanwhile, you can use various security-centric functions to make your web application secure against a multitude of attacks. However, many websites such as WordPress, which is built on PHP, have seen a rise in web attacks. PHP is one of the oldest programming languages used for web applications and not much was done earlier in terms of security.
But in more recent versions of PHP, several security measures have been added as well as the overall security protocols have been revamped. In spite of the security measures already present in PHP, websites can be vulnerable to attacks such as SQL injection attacks, cross-site scripting attacks, session hijacking, to name a few. To prevent such attacks, we need to put the websites through intensive testing and PHP security audits.
Also Read: 7 Top Cyber Security Auditors for SaaS Companies [Reviewed]
Why you need PHP security audit & Penetration Testing?
We have already discussed how websites built using PHP can be vulnerable to a number of attacks. To better protect your website, it’s necessary to conduct regular PHP Security Audit & PHP Penetration Testing.
The purpose of a security audit & penetration test is to detect all vulnerable areas in your website which can be exploited by an attacker. A penetration test also includes exploiting a vulnerability to examine its gravity. Once the test is done, the results help in patching the vulnerabilities and sanitizing the application or website.
These tests are also necessary to ensure that all control measures are active and effective. Sometimes, patches to fix bugs can introduce newer bugs. Hence a regular vulnerability audit is required to find and rectify these bugs. Long story short, it is better to identify your vulnerabilities before hackers do.
Also Read: Cloud Security Audit: Everything You Need to Know | Penetration Testing Quote
How to carry out a PHP Penetration Test?
Penetration testing includes exploits that can test various security features of your application or website. Before PHP penetration testing software became common, most of the testing was done manually. Which could take hours to run.
Things have changed for the better. You can easily find both paid and free penetration testing software that can simplify manual testing for you. In fact, using software alongside manual testing is recommended.
Mentioned below are some of the most popular and effective penetration testing software in the market:
- Zed Attack Proxy:
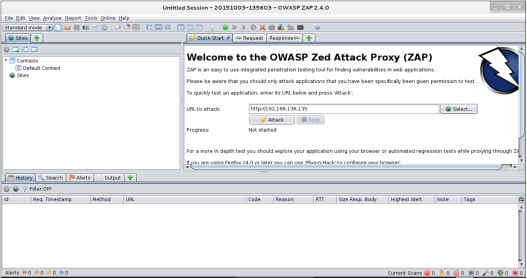
If you are a penetration tester then you must be familiar with OWASP. Developed by OWASP, Zed Attack Proxy is an open-source security tool for testing web applications
It can be easily operated by anyone as it supports an interactive GUI and also has access to the command line. This tool can expose vulnerabilities such as SQL Injection, XSS injection, and application error disclosure, and also exposes missing anti-CSRF tokens, to name a few. It is written in JAVA and is one of the most famous projects by OWASP.
Also Read: Top Penetration Testing Software & Tools Pros Use | A Complete Guide to Cloud Penetration Testing
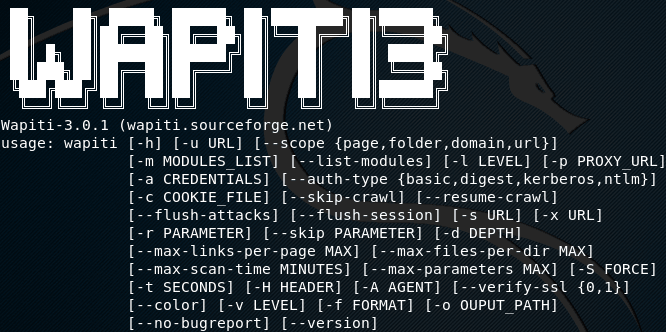
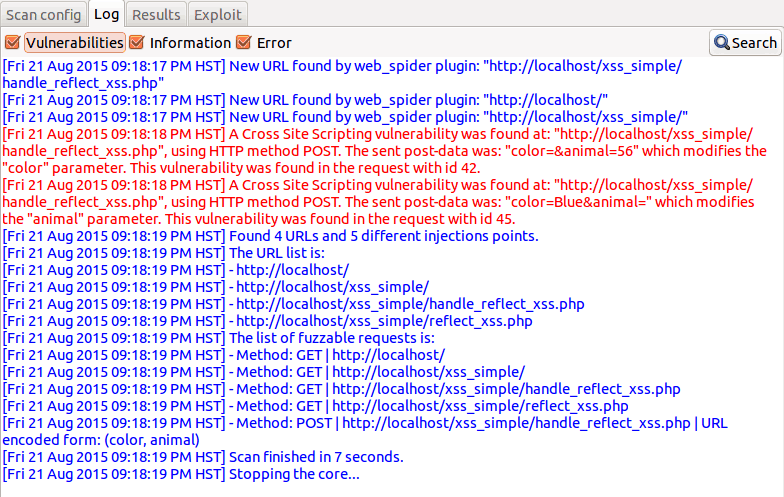
Wapiti:
Wapiti is also an open-source tool for testing built by Devloop and SourceForge. It only supports command line access. So having some knowledge of commands is necessary to use this tool.
This tool supports brute force attacks, using file names and brute force directories. This PHP penetration testing tool can expose XSS as well as XXE injection, command execution detection, database injection, bash or shellshock bug, etc.
W3af:
This is one of the most popular security tools built using python. This PHP penetration testing tool can detect over 200 types of security threats, which makes it an effective PHP security audit tool. It has a user-friendly GUI interface and is easy to get started with. It can detect vulnerabilities such as blind SQL injection, buffer overflow, XSS attacks, etc.
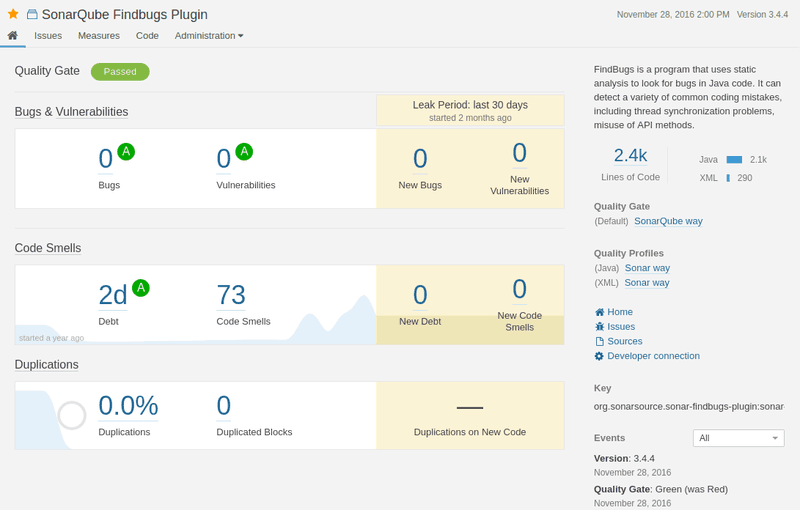
SonarQube:
SonarQube is another PHP penetration testing tool written in Java. Though it is written in Java, this tool can conduct a PHP security audit on over 20 programming languages. It not only exposes security flaws in web applications but also tests the quality of the source code. With an extremely easy to use interface and support for command line for advanced users, this tool can be effectively used for exposing vulnerabilities such as SQL Injection, DDoS attacks, memory corruption, etc.
Hassle-Free PHP Security Audit & Penetration Testing with Astra
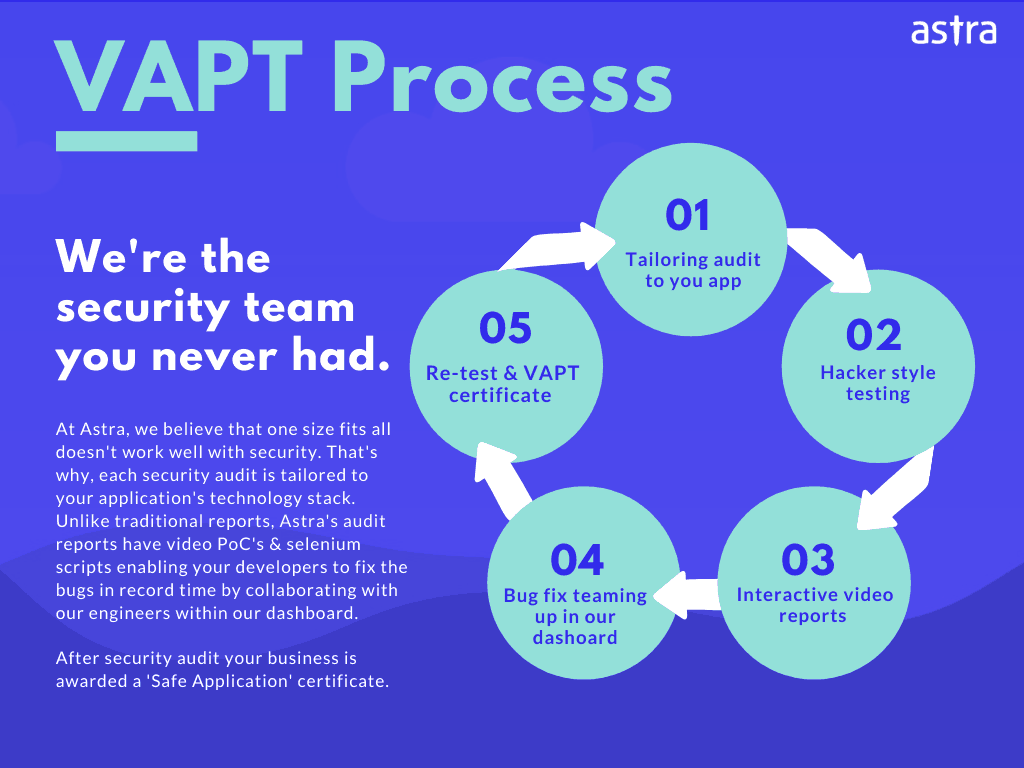
All PHP penetration testing tools are partly automated and always require manual intervention. Also, not all tools are tailor-made to fit your PHP security audits. Based on your needs and to provide a complete arsenal to secure your web application, Astra created the Vulnerability Management Platform.
With custom-made audits for your specific application, you can be sure of a thorough analysis and all-around testing. Automated testing combined with manual audits provides you with the most comprehensive PHP security audit that you will ever need.
Also Read: What are VAPT Tools and which one to choose? | Top 5 Software Security Testing Tools You Should Know About
Post the audit & pentest, Astra provides a detailed VAPT report for your reference.
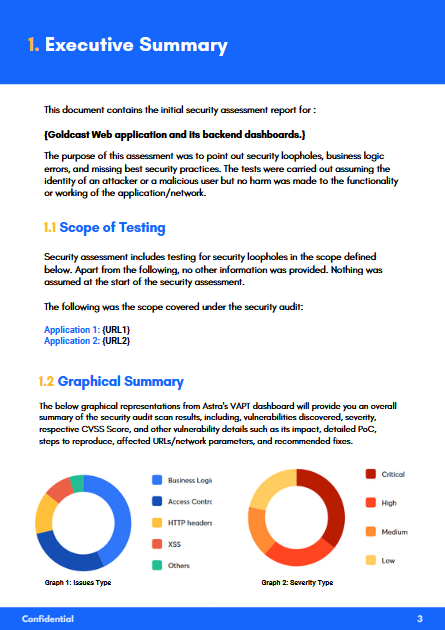
Astra security experts also go out of their way to assist your developers in fixing those vulnerabilities. All this is made seamless by our one-stop Security Scan dashboard.
Get a professional PHP Vulnerability Assessment & Penetration Testing for your website now.
Also Read: Top 6 Web Pentest Tools You Should Not Miss in 2022 | API Penetration Testing: What You Need to Know
FAQs
1. What is the timeline for PHP Security Testing?
PHP security testing takes 7-10 days. The rescan after fixing the vulnerabilities takes 3 more days. The timeline may differ slightly based on the scope of the test.
2. How much does security testing cost?
PHP security testing costs between $99 and $399 per month depending on the number of scans and the plan you are on.
3. Why choose Astra for PHP security Scans?
The security engineers at Astra perform extensive manual pentest on top of machine learning driven automated scans. The vulnerability reports appear on your dashboard with detailed remediation guides. You will have access to a team of 2 to 10 security experts to help you with the fixes.
4. Do I also get rescans after a vulnerability is fixed?
Yes, you get 1-3 rescans based on the type of Pentesting and the plan you opt for. You can avail these rescans within 30 days from the initial scan completion even after the vulnerabilities are fixed.

















I own a website which is php based and I want to know if there are any vulnerabilities that can give access to hackers to hack my site. Is there any way I can do that?
PHP is the backbone of almost every popular CMS today. Thanks to its simplicity and license-free nature, PHP is the preferred choice for dynamic website development. However, due to poor coding standards, compromising PHP sites has become relatively easy. The internet is full of help threads where users complain about custom PHP website hacked or PHP website redirects hack. This has led to a lot of negative publicity for PHP itself which is nowhere to be blamed for this. For more information on how to secure, visit here: https://www.getastra.com/blog/911/php-website-hacked/
What kind of security issues that we can face running a php website? Just curious to know cause I want to build a site based on php.
PHP is dramatically the most criticized languages when we talk of security, yet the oldest in its usage. Despite being old it is far from being outdated. On the contrary, it is still in high demand. Thus, it is important that it remains as protected as possible for it is basic to many growing businesses. PHP coders, understand the fact that it is highly expected of them to take care of all the PHP security issues that come along way. For more information , visit here: https://www.getastra.com/blog/php-security/fixing-php-security-issues/
What is the duration of if I opt for php audit?
Thanks for responding to the article. The security audit is started within 24-hours of your signing-up on a working day. You start seeing vulnerabilities on your dashboard once the audit begins & a final report can be expected within 4-7 days. The turnaround time can be a function of how big the website is.
Is csrf is also a part of hacking? What can be done here to secure from happening this?
Thanks for responding to the article. A CSRF attack involves a malicious website sending a request to a web application via another formerly authenticated website. This allows the attacker to dodge authentication procedures by impersonating the victim using his/her credentials and perform malicious activity or financial transactions. Hot targets for such attacks are online banking services, social media applications and web interfaces for network devices. For more info, visit here: https://www.getastra.com/blog/knowledge-base/cross-site-request-forgery-csrf-attacks-all-you-need-to-know/
Is there anyway I can update my PHP version? Btw I am using wordpress.
Thanks for responding to the article. Having the latest version of PHP on your website can give you a significant edge over the people who run outdated versions. There are many reasons why you should update to the latest version of PHP. For importance of updating, visit here: https://www.getastra.com/blog/php-security/how-to-update-php-version-in-wordpress/
What is sql injection in php website? How can I secure my custom based site from this?
Thanks for responding to the article. SQL Injection is an approach where hackers change the SQL statement running at the backend through falsification of executed SQL commands. Such form of injections is carried out through input fields of the form and cause awful aftermath on the database. It eventually leads to the disclosure of highly sensitive information from the database. For more info, visit here: https://www.getastra.com/blog/911/php-sql-injection-all-you-need-to-know/
I would like to know more information and more about features before opting a php audit. Can you tell me more on this?
Thanks for responding to the article. Sure, you can visit here to know all the information and how Astra helps in finding loopholes of your website: https://www.getastra.com/php-vapt