Cross-Site Request Forgery (CSRF) is one of the most rampantly occurring online attack. Also notoriously known as XSRF or “Sea-Surf”, it is listed as the 8th most common web application vulnerability in the OWASP Top 10 report of 2017 cyber-attacks.
Understanding CSRF in PHP
Execution of a CSRF attack involves a malicious website sending a request to a web application via another formerly authenticated website. This allows the attacker to dodge authentication procedures by impersonating the victim using his/her credentials and perform malicious activity or financial transactions. Hot targets for such attacks are online banking services, social media applications and web interfaces for network devices.
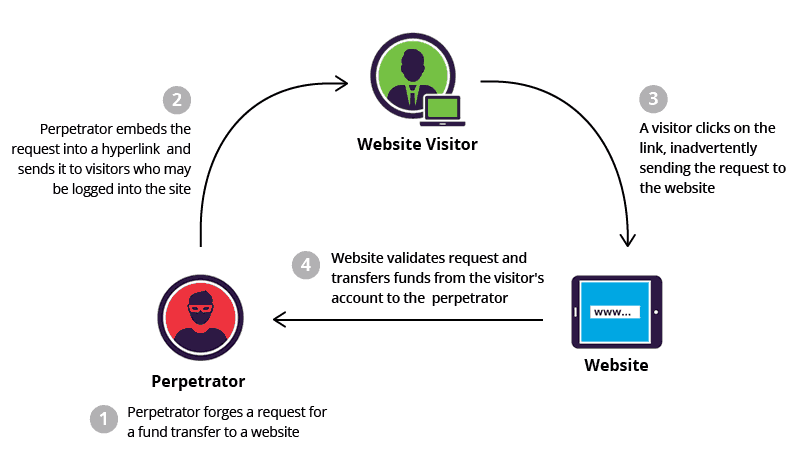
General Workflow of a CSRF attack
To exemplify, a CSRF attack can occur if a victim logs in to their banking website and during an active session, receives an e-mail to click on a link. On clicking the link, a script would execute on the banking website, using the victim’s bank credentials to transfer funds from their account into the attacker’s account. In this case, the attacker posed as the victim by exploiting the victim’s login information, computer and IP address for illegally transferring funds.
Alternatively, instead of emailing a victim while validated into a site, an attacker may inject a code into the site and just when the user clicks on the link, the code would automatically perform the malicious transaction.
There is no way for the victim to claim that someone else performed the malicious transaction since their login credentials and IP information were previously used for legitimate transactions by the victim in the past
Misconceptions about CSRF
Following are some common techniques employed by the developers to boost security of the application but unfortunately none of them proves to be effective against the CSRF.
- SSL Certificate: Just like various other web application vulnerabilities, HTTPS does not offer any significant protection from the CSRF, This is because the vulnerability persists as a result of flaws in application logic.
- POST requests: This is not an effective method for preventing CSRF attacks. An attacker can generate a similar POST request like the main application and change data that is being is saved at the server side.
This is a simple CSRF exploit for the POST requests
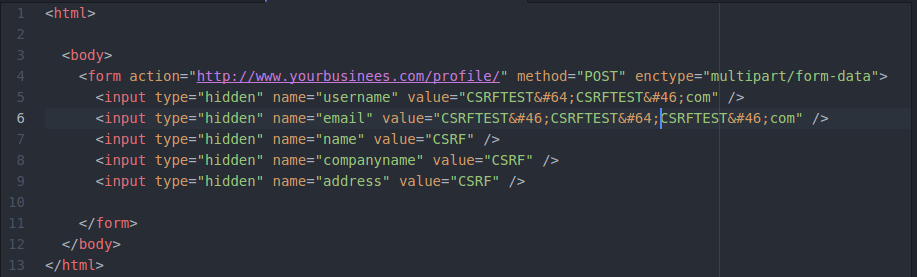
By tailoring this exploit according to specific application attackers can easily compromise the application.
How to defend against CSRF attacks in PHP
It is not difficult to fix this vulnerability. Below are given methods which helps preventing applications from possible attacks:
- Same Origin Policy: This is an important security measure which allows an application to ensure that all the requests are coming from trusted origin (original website) and not from non-trusted origin (malicious websites). This also ensures that the response from the server is also being sent to the intended application and not to any application being controlled by the attacker.
- Synchronizer (CSRF) Tokens: This is an additional surety over the same origin policy where special tokens must be attached to the session tokens and communicated for every update request.
- CAPTCHA: It is a method which involves user interaction, since executing CSRF is based on execution of malicious scripts (payloads) by the attacker, making use of Captcha solves the problem.
Apart from these, a regular audit of your website is critical to ensure detection of any vulnerability. With Astra’s Business Plan, you can get monthly security scans to ensure that your website is well prepared against any hack scenarios.

















[…] CSRF + Stored Cross Site Scripting (customer group) […]