With the rapid spread of the internet, companies are making their online presence now more than ever. The backbone for their presence on the web is undoubtedly the servers powering websites, APIs, emails, games, etc.
As servers are central to the functioning of an internet company, they are often targeted by hackers.
There have been instances where hackers managed to break into the servers of companies and stole proprietary source code.
There are several threats on the internet that might target your server for a variety of purposes ranging from cryptocurrency mining to data-stealing and much more.
Hence, in the present scenario, performing the server security audit should be done as frequently as possible to eliminate all security vulnerabilities.
As Michael D. Bauer puts it nicely in his book Linux Server Security,
It’s impossible to anticipate all possible or even all likely types of attackers. That’s okay: the point in threat analysis is not to predict the future; it’s to think about and analyze threats with greater depth. You can’t anticipate everything, but you can take reasonable steps to maximize your awareness of risks that are obvious, risks that are less obvious but still significant, and risks that are unlikely to be a problem but are easy to protect against.
This article covers the various issues that can be found during the server security audit and how to fix them.
Server Security Audit at the Physical Level
This is the most basic and often ignored part of the audit. The physical audit can be divided into three basic parts:
- Access Control: To prevent unauthorized access to your server.
- Surveillance: To detect any unauthorized access to your server.
- Testing: To recover from the incident.
For this audit, try to find the answers to the following questions from the three categories. This will give you a fair idea of how robust your physical server security is.
1. Access Control
- Are unauthorized personals allowed in the server room?
- How easily can physical security be bypassed to enter the server room?
- While doing physical server security audit, is the server room easily available through unconventional means like windows, backdoor, etc.?
2. Surveillance
- Is the server being continuously monitored via CCTVs even during a power failure?
- What is the frequency of malfunctioning of the CCTVs and what is the response of security staff when that happens?
- How long does the server room go unmonitored when the staff changes duty?
3. Testing
- How long does it take for the security staff to detect the breach?
- When the breach is detected, how long does it take the security staff to reach the server room and secure it?
- How frequently is the server backed up?
- Where is the backup of the server kept?
Related blog – Penetration testing Company | 10 Best Cyber Security Audit Companies [Features and Services Explained]
What can you do?
- Make sure only authorized personal are allowed in the server room via access cards, etc.
- Block all the extra entrances to the server room except the main entrance.
- Keep the server room cool and inspect frequently for fire hazards.
- Create a comprehensive physical security policy.
- Use multiple CCTVs with a power backup.
- Frequently change the shift of security personnel.
- Keep an emergency room lockdown mechanism ready.
Here it is noteworthy that answers to these questions are the primary and basic steps in physical server security. For detailed server assessment, follow this exhaustive list. Including it is beyond the scope of this article.
Server Security Audit on the Application Level
1. Missing Firewall
Configuring a firewall for your server if not already done is the most basic step to improve the security of your server. It basically acts as a guard between your server and the internet by filtering incoming traffic.
If you have a firewall installed already, you can manually search for it using this tool called WhatWaf. This tool can also identify possible bypasses for your firewall.
Here’s how to use it:
- Install WhatWaf using this link.
- Once everything is set, navigate to the ‘whatwaf’ directory.
- Run the following command to detect your firewall:
./whatwaf -u https://www.example.comDon’t forget to replace www.example.com with your actual website’s URL 🙂
Also Read: Security Audit Services: Importance, Types, Top 3 Companies

What can you do?
If you want to start with a free and basic firewall, ModSecurity is a popular candidate. It is available for installation on Apache, installation on Nginx as well as Microsoft IIS.
However, the limitation with such WAFs is that there exists a variety of tools to bypass them.
For instance, Modsecurityzeroversioned tamper for Sqlmap can be used to exploit SQL injections behind the ModSecurity firewall.
Hence, for reasons like this, it is recommended that instead of using a free firewall solution, try an affordable premium firewall like Astra. With plans catering to small servers to large-scale infrastructure, Astra makes server security a manageable affair.
Here’s how the Astra firewall protects your server from any attack that may come your way:
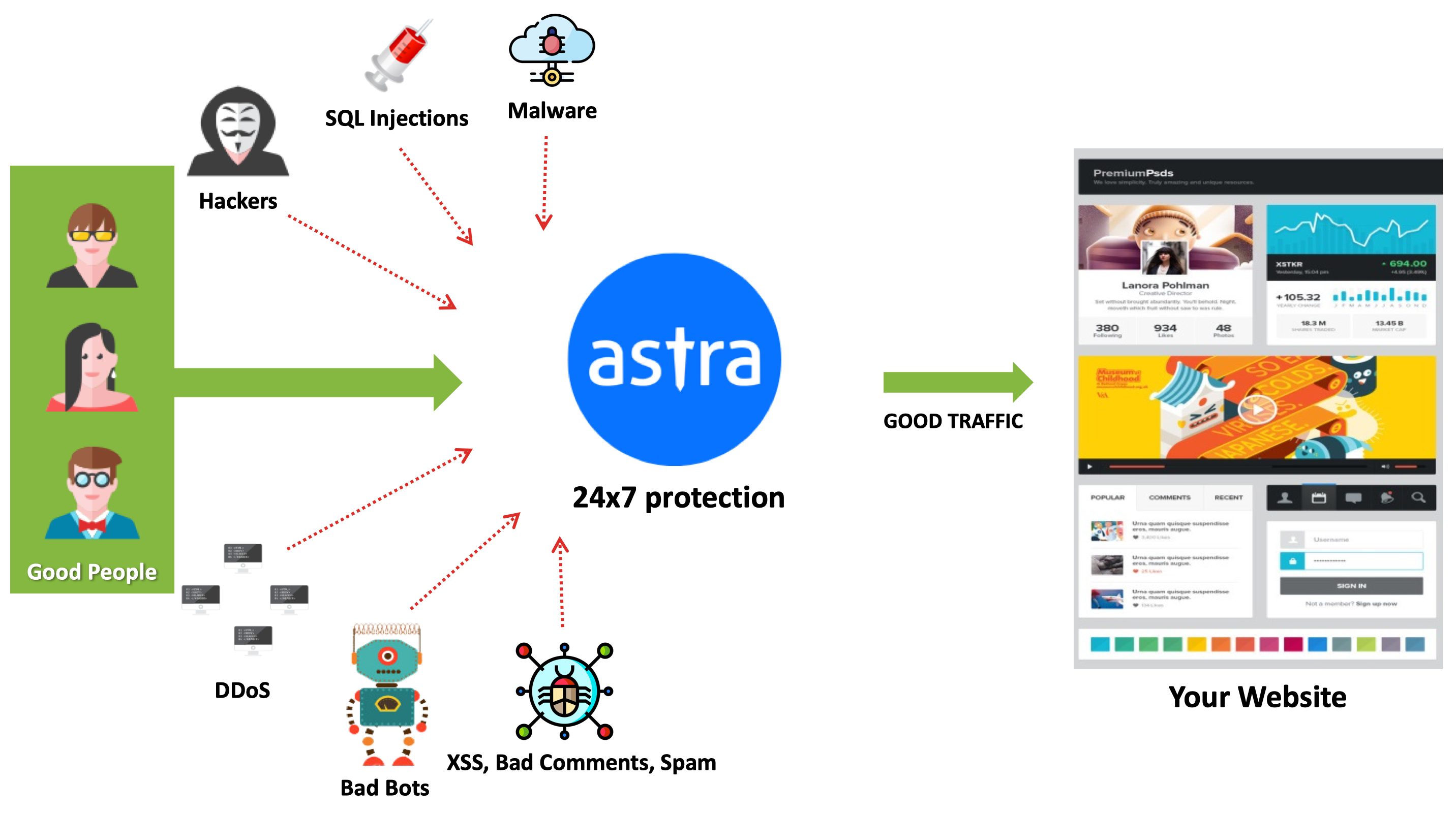
2. Server Not Using SSL
You are probably living under a rock if your server is still not communicating over HTTPS on the internet. Using HTTP over the internet sends that data for communication in plaintext, risking threats like MITM attacks and malware injection.
To check if your server uses SSL or not:
- Go to digicert.com, and
- Enter the URL of your server as shown in the image below.

What can you do?
If no SSL is detected for your server in a server security audit, you should get one. There are plenty of websites like ZeroSSL and Let’s Encrypt that offer free SSL certificates.
Once you purchase the certificate, configure your server to communicate over HTTPS. If you’re faced with any difficulty installing & configuring SSL on your server, watch tutorials by sslforfree.com. It has resources for all major servers (Apache, Nginx, IIS, etc).
Also Read:Security Audit Company and Services [Top rated]: How to Pick
3. Missing Security Headers
Most modern browsers come with a variety of pre-built filters to prevent common attacks like XSS, Cookie stealing, Clickjacking, etc which are disabled by default. So, by sending correct security headers, your server ensures that the browsers of end-users protect them from malicious attacks.
The missing security headers can be checked during the server security audit using a tool called Nikto. Not to mention, this tool can also identify thousands of security issues with more than 270 servers.
To use this tool:
- Firstly, download Nikto from its Github repo.
- Now, navigate to the program directory of Nikto i.e. cd nikto/program
- Run the tool with the following command (you must have Perl installed):
./nikto.pl -h http://www.example.com
As we can see in the image, the website www.example.com has an anti-clickjacking header missing as pointed out by Nikto.
What can you do?
Fix the issue of security headers with this knowledge base. These missing security header vulnerabilities can sometimes be combined with the HTTP Trace method (if enabled) to exploit your server.
This method was basically designed for diagnostic purposes and there is not much utility in keeping it enabled for end-users. If Nikto detects this method, disable it.
- For Apache .3.34, 2.0.55, or 2.2+ release, open the ‘httpd.conf’ file and add this line: TraceEnable Off
- For IIS 7 and higher, open cmd and run the following command:
appcmd.exe set config /section:requestfiltering /+verbs.[verb='TRACE',allowed='false']- For Nginx, open the ‘nginx.conf’ file and add the following code:
if ($request_method !~ ^(GET|HEAD|POST)$ ) { return 405; }Also Read: Cloud Security Audit: Everything You Need to Know
4. Directory Indexing Enabled
Directory indexing allows an attacker to see sensitive files on your server. While it is not a vulnerability in itself and sometimes some servers (like Linux mirrors) even need to enable it. But generally, if you have no such requirement, it is recommended to disable it else there is always a chance of leaking some sensitive file.
You can check the config file if directory indexing is enabled or Nikto will detect it for you as shown in the image below:

What can you do?
- For IIS 7 and above, open the CMD and run the following command:
ppcmd set config /section:directoryBrowse /enabled:false- For Nginx, open the ‘nginx.conf’ file. Now here, look for a line like this, autoindex on; and change the value of this parameter to off so that the line now looks like autoindex off;
- To disable directory indexing in apache, add the following lines to ‘httpd.conf’ file.
<Directory /{YOUR DIRECTORY}>
Options FollowSymLinks
</Directory>Here, replace {YOUR DIRECTORY} with the name of the directory you wish to disable it for.
Server Security Audit on the Operating System Level
1. Open Ports
Different services on your server use various ports for communication on the internet. However, sometimes a vulnerable service may be running behind your open ports which could compromise the server.
To see all the open ports listening on your system, open the terminal in Linux-like systems and run the following command:
sudo netstat -tulpn | grep LISTENIf however for some reason, you wish to check for open ports using an external tool, Nmap is the industry standard.
To download and use Nmap in Debian based Linux OS, run the following command:
sudo apt install nmapThereafter, scan your server using the following command:
sudo nmap -sTU -O IP-to-scan
Here, replace the IP-to-scan with the IP address (internal as well as external) or domain name of the server that you wish to scan. This command will scan both TCP and UDP ports.
What can you do?
In Debian-based Linux systems, service can be stopped using the command:
sudo service service-name stopFor example, sudo service tor stop.
Moreover, to stop a process running on a particular port, use the command fuser port-no/protocol. For example, if you wish to stop a process on TCP port 1234, the command will be fuser 1234/tcp.
2. Improper File Permissions
For every file on the server, people are allowed to do 3 basic operations that are read, write and execute. Now, permissions can be assigned to perform these operations to 3 types of entities, owner (you), group (other people on the server), and the world (everyone else).
Having incorrect file permissions can allow an attacker to edit your files. The dangers of this can be malware injections, defacement, ransomware attacks, and so on.
Thus it is important to have correct file permissions for the 3 entities mentioned above. To check file permissions of all the files of a directory on UNIX and LINUX systems, open the terminal and run the following command:
ls -la DIRHere replace DIR with the directory name for which you wish to check. For example, to check file permissions for the ‘/var/www/html/’ directory, the command will be:
ls -la /var/www/html/What can you do?
To see what correct file permissions should be and how to change them using a CPanel or FTP. You can also change file permissions using the ‘chmod’ command.
For example, to change the permission of a file such that only the owner can write, everyone else can only read and execute, open the terminal, and type:
chmod 755 my-file3. Missing Software Updates
Software updates play a key role in the security of your server. Often with updates, a new patch for some existing vulnerability is introduced.
Using outdated server software can make your server vulnerable to attacks. Scanners like Nikto can detect the server software version and tell if it is outdated as shown in the image below.

What can you do?
Firstly, avoid using unnecessary software on the server as they add to operational complexity. Secondly, enable automatic updates for your system.
If for some reason, you cannot do that, subscribe to the update newsletter service of the software if that is available. Make a policy to manually check for updates frequently. In systems using the apt package manager, the server can be updated using the ‘install’ command of apt.
For example, sudo apt install apache2. To update the entire OS and its packages, run the following two commands:
sudo apt updatesudo apt upgrade4. Weak Passwords
During a server security audit always check for multiple endpoints that are protected via a password. Using a weak password can leave the services running on the server vulnerable to brute force attacks.
A weak password is one that uses common phrases and is short. Tools like Hydra can be used by attackers to brute force the passwords of services. Ony the weak passwords are vulnerable to such attacks. This tool can brute force passwords for multiple services like FPT, SSH, LDAP, etc.
You can check for weak passwords as follows:
- To download and install Hydra, read this README file.
- Once installed, run the command hydra -help for more info.
For example, in the image given below, hydra has cracked the password of SSH on a test server by setting the username ‘demo’ and taking passwords from a dictionary file.

What can you do?
- Enable 2-factor authentication on the endpoints where possible.
- Make a comprehensive password policy.
- Enable modules to block multiple tries on whichever endpoint is possible.
- Frequently keep changing your passwords.
Conclusion
To conclude it can be said that businesses should avoid cutting corners when it comes to server security. Some of the server security measures mentioned above should be followed initially while setting up the server. Whereas others can be gradually added over time.
However, it is worth mentioning here that this article touches only on the basics of a server security audit. So, in order to make yourself sufficiently secure, it is always recommended to hire experts for the server security audit.
Astra provides server security services at a very affordable and flexible rate. With plans starting as low as $349 per scan, Astra is definitely worth a go. Still, got a query?
FAQs
What is the timeline for Server Security Audit?
The security audit by Astra takes 7-10 days for websites and apps, and 4-5 days for cloud infrastructures.
How much does security testing cost?
The cost for security testing ranges between $99 and $399 per scan for websites.
Why choose Astra for Security Audit?
8000+ tests, adherence to global security standards, intuitive dashboard with dynamic visualization of vulnerabilities and their severity, security audit with simultaneous remediation assistance, multiple rescans, these are the features that give Astra an edge over all competitors.
Do I also get rescans after a vulnerability is fixed?
Yes, you get 1-3 rescans based on the type of Pentesting and the plan you opt for. You can avail these rescans within 30 days from the initial scan completion even after the vulnerabilities are fixed.
















